Microsoft Updates Windows To Block Fraudulent Digital Certificates
If you follow this blog closely you may have noticed that several browser developers have pushed security updates in the past week (see Mozilla Releases Firefox 3 Security Updates for instance) that block several invalid digital certificates to protect users from attacks exploiting those certificates.
Microsoft is currently pushing out a Windows Update that addresses the situation on Windows. Lets take a closer look at what actually happened before we go into details about that.
Comodo, a certification authority, notified Microsoft and other companies on March 16 that "nine certificates had been signed on behalf of a third party without sufficiently validating its identity".
The following domains are affected by the certificates:
- login.live.com
- mail.google.com
- www.google.com
- login.yahoo.com
- login.skype.com
- addons.mozilla.org
- Global Trustee
These domains are some of the most visited domains on the Internet.
Microsoft notes that "these certificates may be used to spoof content, perform phishing attacks, or perform man-in-the-middle attacks against all Web browser users including users of Internet Explorer".
Comodo has revoked the certificates in the meantime. Microsoft has released a security update for all versions of Windows that moves the fraudulent certificates into the untrusted certificate store of Microsoft Windows.
The update is provided via Windows Update and Microsoft Download. Users with automatic updating enabled will receive the update automatically, a restart of the system is not required after the update has been installed.
- Microsoft Security Advisory: Fraudulent Digital Certificates could allow spoofing at Microsoft Download [link] for direct downloading.
- Security Advisory [link]
Here is how you can verify that the certificates are blocked after you have installed the update. Open an elevated command prompt. Windows 7 users click on Start, select All Programs > Accessories, right-click the Command Prompt program link and select Run as Administrator.
Enter mmc in the command prompt window to launch the Microsoft Management Console. Now follow these steps:
- Press Ctrl-m or select File > Add / Remove Snap In
- Find Certificates in the listing, select it with a left-click and click on Add.
- Select Computer Account on the next window and press Finish
- Click the ok button to leave the Add or Remove Snap-ins configuration window.
- Expand the certificates listing under Console Root and then the Untrusted Certificates sub-listing. Click on the Certificates folder there.
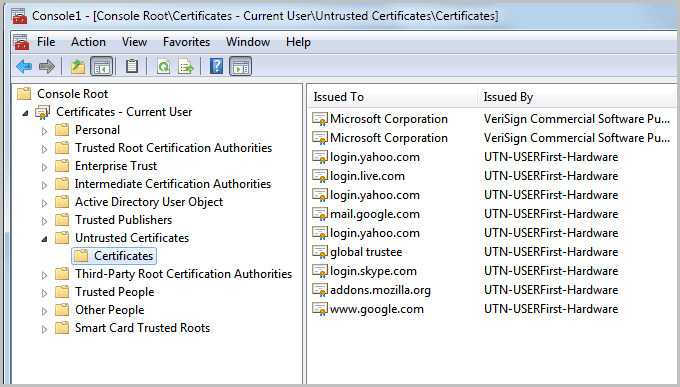
You should now see the affected domain names in the listing. Issued by should read UTN-USERFirst-Hardware.



















I wanted to thank you for this excellent read!! I definitely loved every little bit of it.Cheers for the info!!!! & This is the perfect blog for anyone who wants to know about this topic. You know so much its almost hard to argue with you
I actually do not understand well. why these certificates are in Untrusted list? what does it mean? could u pls explain more. coz i always want to make sure to get secure connection. thanks.
One thing for sure is I would never trust anything associated with Comodo, the sell certs to many malware vendors. Comodo should somehow be a banned subject ever making it to my PC