Microsoft Security Bulletin Overview January 2011
The second Tuesday of a month is Microsoft's patch day where the software company releases security patches and fixes for its products. The first patch day of the year 2011 brings two security bulletins that patch vulnerabilities in the Windows operating system. MS11-002 patches vulnerabilities in Microsoft Data Access Components that could allow remote code execution. The maximum severity rating of the vulnerability is critical, the highest possible rating.
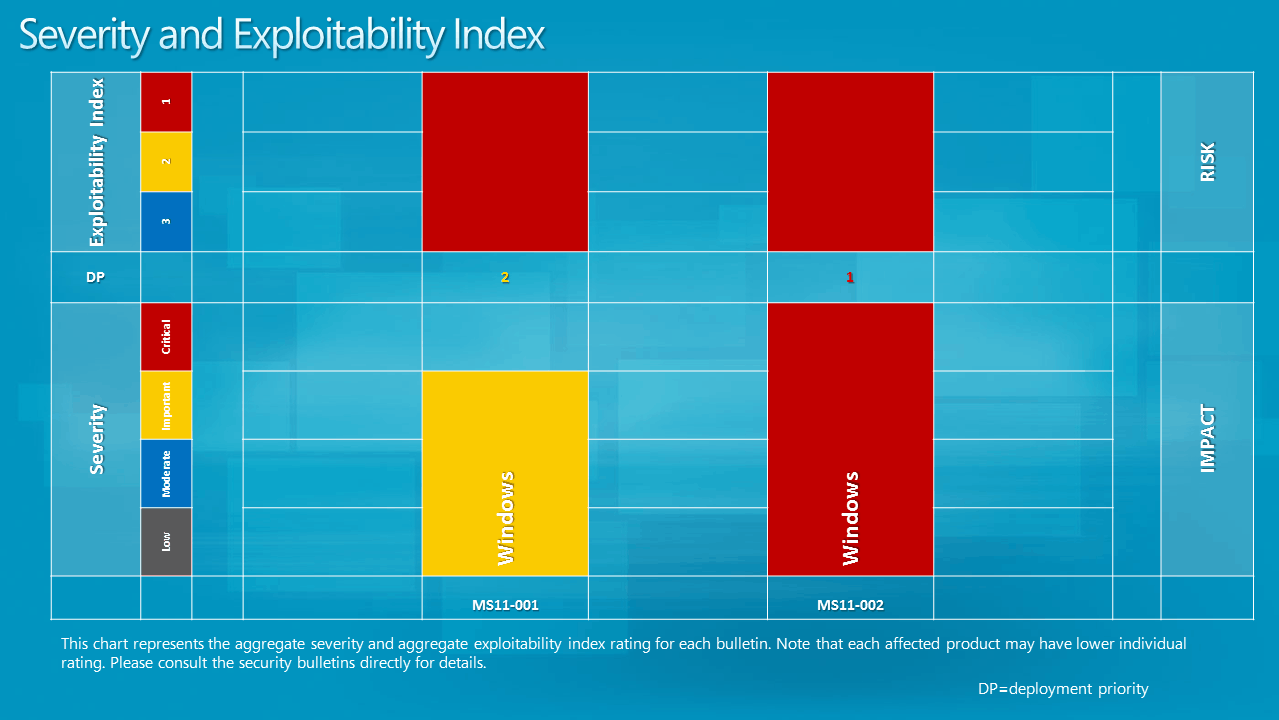
A closer look at the security vulnerability reveals that is is rated critical for all 32-bit and 64-bit Windows client operating systems from Windows XP to Windows 7. The same vulnerability is rated as important for all server based operating systems.
The second vulnerability, MS11-001, has a maximum severity rating of important. It fixes a vulnerability in the Windows Backup Manager that could allow remote code execution. The vulnerability affects only the Windows Vista operating system.
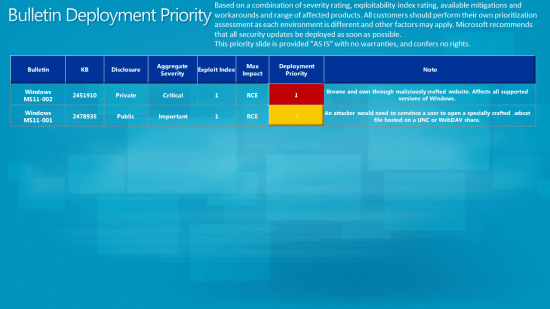
- MS11-002 - Vulnerabilities in Microsoft Data Access Components Could Allow Remote Code Execution (2451910) - This security update resolves two privately reported vulnerabilities in Microsoft Data Access Components. The vulnerabilities could allow remote code execution if a user views a specially crafted Web page. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-001 - Vulnerability in Windows Backup Manager Could Allow Remote Code Execution (2478935) - This security update resolves a publicly disclosed vulnerability in Windows Backup Manager. The vulnerability could allow remote code execution if a user opens a legitimate Windows Backup Manager file that is located in the same network directory as a specially crafted library file. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open the legitimate file from that location, which in turn could cause Windows Backup Manager to load the specially crafted library file.
Severity and Exploitability Index
Bulletin Deployment Priority
The images have been taken from the Technet announcement which offers further information about the vulnerabilities and patch deployment.
Windows users are advised to apply the patches as soon as possible to protect their system from possible exploits. The patches can be applied directly via Windows Update or directly from Microsoft Download.
Advertisement




















Good to see security patch before service pack release..
No fixing the hole in all version of IE.
It time to fix 20 years old (win 95) holes.
Thanks again Martin, for this month ferry illuminating piece about this mouths Microsoft security updates.