DLLHijackAuditor, Check Programs For DLL Hijack Vulnerability
A new Windows vulnerability was made public at the end of August which can result in remote code execution on a computer system if the issue is exploited successfully.
The issue is caused by programs and applications that use insecure programming practices. According to various researchers at least 40 popular applications are affected by the issue.
New users who want to read up on it can open our coverage of the issue, or Microsoft's Security Advisory. Both offer a deeper explanation and manual workarounds for the issue.
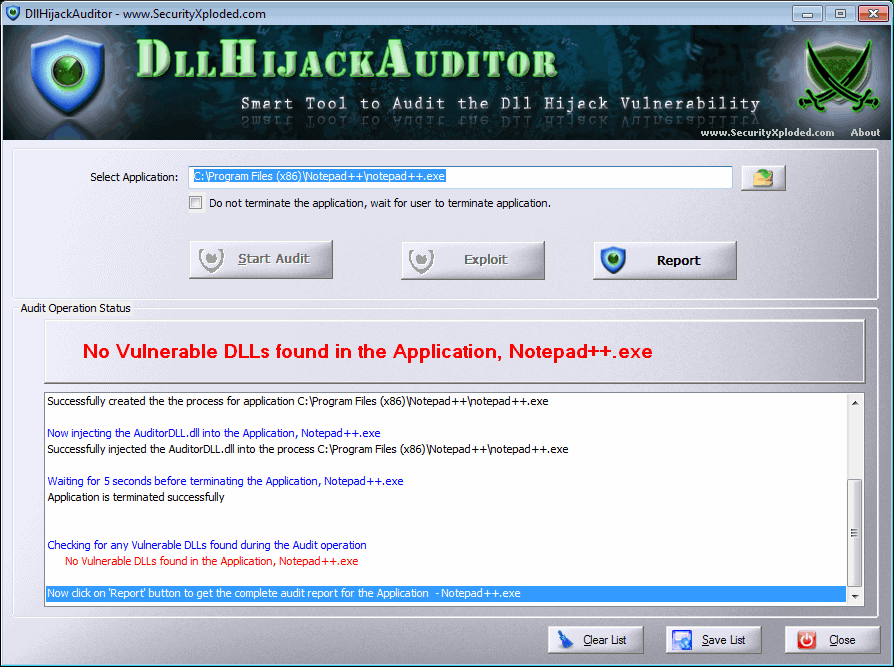
The free software DLLHiJackAuditor has been designed to test software for the vulnerability. The portable program can audit any 32-bit Windows application.
The program is dead easy to use. Users need to select an application from the computer system first before they click on the start audit button to test the application for the vulnerability.

The portable software will automatically load the application and terminate it. It will uncover any vulnerable DLLs that are found during the audit, and report those back to the user of the system.
The Exploit button becomes active if a vulnerable DLL has been found in the selected software.
Finally, it is possible to create a HTML report of the findings which contains detailed technical information that the developer of the vulnerable application can use to fix the issue.
DLL Hijack Audit does not require any third party tools to function properly. It has in addition been designed in a way that it does not trigger antivirus or security software on the system. Finally, the program require no special privileges for auditing applications, with the exception if the target executable does).
The software program is available for download at the developer website over at SecurityXploded. The tool can be useful for software developers, and users who want to make sure that the programs they run on their system are not affected by the security issue.
Advertisement















