The Phishing Flow Chart
Phishing is a serious problem on today's Internet even with phishing protections in email clients, web browsers and security software in place.
The main reason for that is that the majority of security applications protect against known phishing threats only. Sites of phishing campaigns do get blocked after they have been discovered and that happens fairly quickly nowadays.
The problem is that phishing protection does not necessarily protect against phishing sites that are not in the databases yet. You may not be warned when you open the site and may fall pray to the attack unless you are careful.
There is a window of opportunity for attackers to take advantage of that fact.
The Phishing Flow Chart
Internet users therefore need to know about phishing and how to identify phishing emails so that they don't become a victim of an attack.
While that may sound like an easy thing to do if you are an Internet veteran or simply interested in security, it is not as trivial as it sounds for less tech-savvy users who have little to no experience when it comes to computer systems and security specifically.
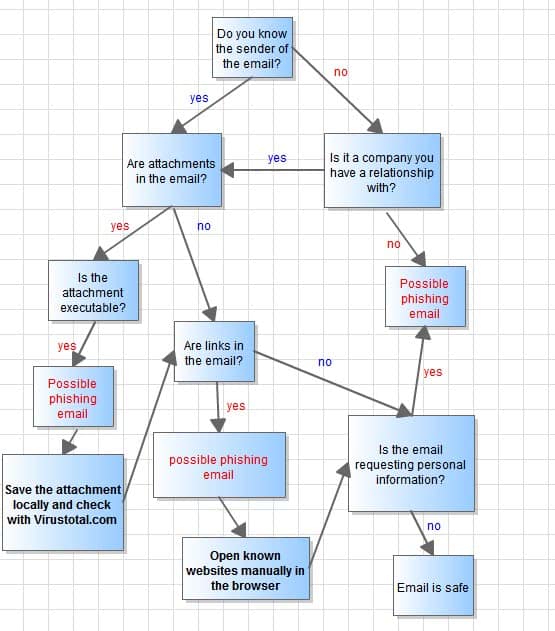
The phishing flow chart outlines the process of analyzing an email to determine if it is a phishing email or not.
The flow chart addresses the three biggest email dangers: Attachments, links and social engineering. The chart has been color coded for easier recognition of safe and dangerous elements in emails. All red elements in the flow chart are considered dangerous while blue elements are considered safe.
The chart furthermore provides basic suggestions on how to react when possible dangerous elements are encountered, for attachments it is to save them locally and check them with a service like Virus total online. That is better than opening them right away and hoping that the resident antivirus solution, if one is installed, catches any attack that gets carried out in the process.
Following the chart leads either to a safe or dangerous rating for the email that you analyze using it.
Here are the core questions that you need to answer when you analyze an email:
- Do you know the sender of the email or is it from a company that you have a business relationship with (e.g. your bank)?
- Does the email have attachments? If yes, is the attachment an executable file?
- Are links in the email? What is the URL the link is pointing to? Does it look legit?
You can print out the chart if you want, or just memorize it. It is really not that complicated to go through. Just follow it from the very top to find out if an email is safe or a possibly malicious.




















Is a reply 9 years later still valid? Coming here from a page Martin published on 2019-09-07 about draw.io. Feels weird to be writing from the future…
Much has changed in the malware world in those 9 years but this chart is still useful. However another breakdown of this chart would give the viewer some more info on how to determine if the attachment is an executable. The miscreants have learned to package them into other forms that some systems (Windows) might execute such as “.scr” or Word documents with VBA. Also there has been a surge in malware propagated through javascript.
this is a good chart, but it needs a “no” connector from the “is the attachment executable” decision box draw to the “are links in the email?” decision box.