Firefox to get option to verify all binaries to protect against compromise
Mozilla is working on a new security project for Firefox, called Binary Transparency, currently to allow all Firefox users to verify the binary files of the web browser to ensure that the files are safe and have not been tampered with.
Firefox is an open source project. This means that anyone may build the browser from source, and even change code before that.
Most Firefox users however don't do that. They download pre-compiled versions of the web browser that they download from Mozilla's own website, third-party sites, or even -- once installed -- using the automatic update feature of the web browser.
Binary versions of Firefox don't come with any assurance that they correspond to the Firefox source code of that particular version of the browser. While users could in theory build Firefox from source to compare the downloaded binary version of Firefox with the version compiled from source, it is not really something that is very practical.
Also, if you have the tools and knowledge to build Firefox from source, there is really no need to download the binary of the browser in first place.
Firefox: Binary Transparency

Mozilla plans to change that by adding a feature to the Firefox web browser that allows anyone to verify that the binary files are genuine and not compromised.
The main idea is to log all Firefox binaries in a publicly verifiable log. Anyone may look it up, and compare the binary files of the local Firefox installation with the log data to make sure that the files are the same that any other user of the web browser got during download.
While that is already helpful, plans are underway to implement that functionality in the Firefox updater as well. This means that Firefox's automatic update feature will verify any new update that it discovers before it is downloaded or installed on the user system.
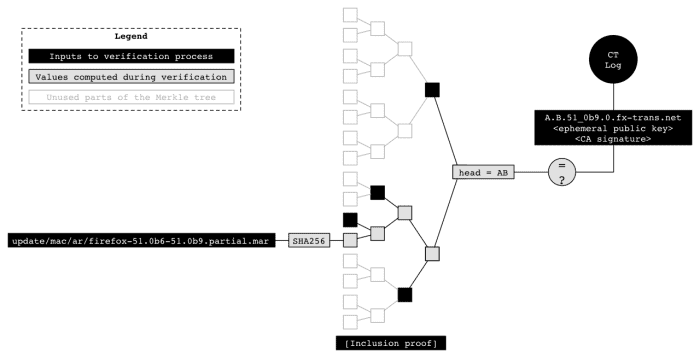
Mozilla details the logging and verification steps on the official Wiki entry of Binary Transparency. The process is technical, but it uses certificates, SHA256 hashes, a Merkle tree and unique domain names for each release. You can check out the details on the wiki page if you are interested in additional details.
The verification process at its core requires that you verify one, some or all binary files of the release against the hash values of the public log file of that release. Again, there is more to the process than just described, so head over to the wiki for details on that as well.
You may be interested in the meta tracking bug over on Bugzilla, as it highlights the progress made to implement the feature. A target milestone has not been announced yet.
While you can use the feature to check Firefox binaries before download or updates, the feature may prove useful as well to check existing installations of the web browser.
Now You: What's your take on Binary Transparency?






















Martin,
When would this “Binary Transparency” feature be released?
But, the figure says it is Firefox 51 .mar file.
This was used by Mozilla internally, it has not been released yet.
Mozilla has yet to announce a Firefox release version for the new feature. You can follow development here: https://bugzilla.mozilla.org/show_bug.cgi?id=1341396
The process is technical, but it uses certificates, SHA256 hashes, a Merkle tree and unique domain names for each release.
How can we be sure NSA won’t hack the Merkle tree again? (I’ll get my coat. And yes, I know it’s spelled Angela Merkel.)
I fully expect this “browser self-check, self-protection” will be turned and used against us ~~ in the same vein as “removing one’s freedom to privately craft and use one’s own extension xpi” (rejected by browser’s SELF protection checks because the xpi is considered “unsigned”, unblessed, untrusted).
Why, exactly, does this “solution” involve a happyshit proprietary signed .mar file and contacting remote auth servers and…? Seriously, I would feel MORE confident using a manifest + list of hashums provided by a 3rd party (NOT mozilla), e.g. the Electronic Frontier Foundation.
Mark my words, eh. On the horizon I envision “We have detected that one or more of your browser files is tainted. FOR YOUR PROTECTION, functionality shall be limited — you will be unable to use this tainted {non-blessed} browser to conduct ecommerce, nor to submit login/signon webforms, period… nor will you be able to use PriVaTeBroWsing mode”.
Yeah. All your base are belong to THEM.
the files are save=the files are safe
“While that is already helpful, plans are underway to implement that functionality in the Firefox updater as well. This means that Firefox’s automatic update feature will verify any new update that it discovers before it is downloaded or installed on the user system.”
They haven’t been doing that already?!!! SCARY…
Outside of Linux, what software does this? Not much. Users just trust the magical internet to provide software without questioning how this software is coming to them, or from whom.
I’d like to know when Firefox *extensions* will get some PGP signatures, because right now they are the weakest link in the Firefox security chain.
If this method works well for Firefox, I hope it turns into an industry standard.
Ordinary users should have some reassurance that they are getting genuine compiled versions of any program in widespread circulation.