Critical vulnerability in Gigabyte Motherboards discovered
Millions of PC devices with Gigabyte motherboards are in danger. Researchers at Eclypsium have discovered backdoor-like tools in hundreds of Gigabyte motherboard models. The legitimate tools are used by Gigabyte for updating purposes, but they may be abused by threat-actors to attack systems and install persistent malware.
The implementation by Gigabyte is designed to download updates. Eclypsium explains that Gigabyte has embedded a Windows executable file in the motherboard's UEFI firmware. This file is written to disk as part of the boot process and loaded into memory.
Later on, it is loaded during Windows startup, contacts an Internet server operated by Gigabyte, to check for and download updates. The researchers discovered that one of the servers was still using HTTP and that the HTTPS implementation of the other servers was not validating remote server certificates correctly.
This allows third-parties to attack systems using Machine-in-the-middle attacks. Furthermore, the researchers note, there is no cryptographic digital signature verification or other validation in place regarding the firmware. While Gigabyte's executable that is embedded in the firmware and downloaded tools from the manufacturer are cryptographically signed, threat actors may nevertheless use the backdoor to attack systems and infect them with persistent malware.
Mitigations
Eclypsium published a list of affected motherboard models here. It is a PDF document that lists motherboards and revisions. Programs such as the free Speccy reveal the make and model of the motherboard, and you may also find out how much RAM the motherboard supports.
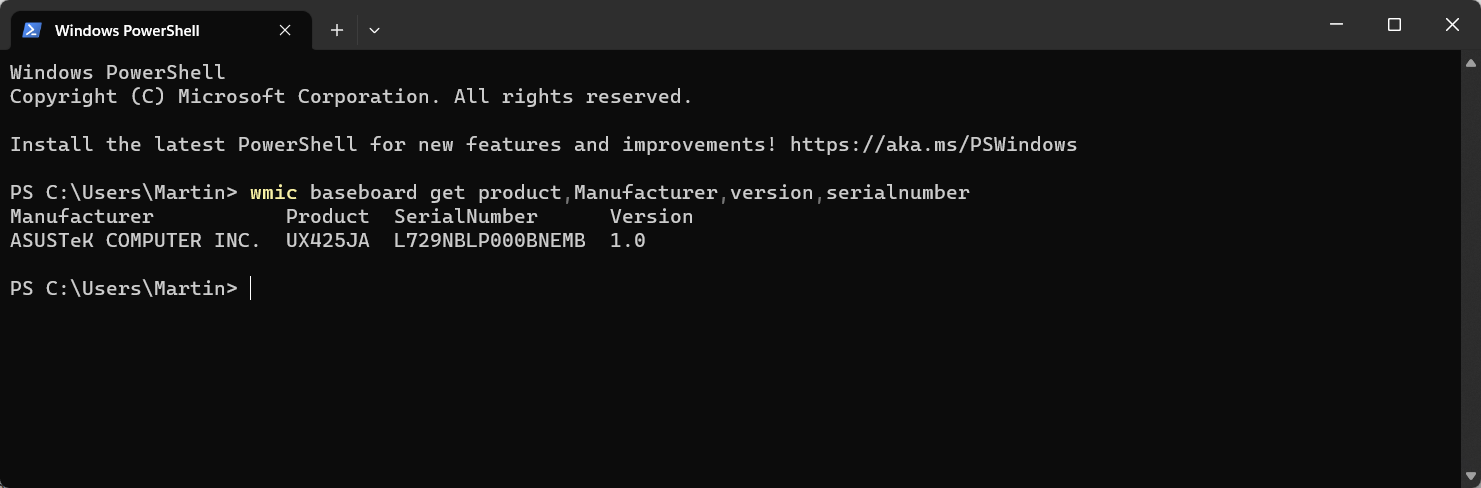
Windows includes options to look up the information without using third-party tools. Here is how that works:
- Use Windows-X to open the admin menu.
- Select Terminal.
- Run the following command wmic baseboard get product,Manufacturer,version,serialnumber
The command returns the information required.
The researchers recommend that administrators disable the "App Center Download & Install" feature in the system's UEFI/BIOS. Doing so blocks the process, so that it can't be exploited. They also recommend setting BIOS passwords to protect the setting from manipulation by third-parties.
Other options include checking for firmware updates released recently by Gigabyte that address the issue, and to block the server addresses that Gigabyte's tool uses for its downloads.
The firmware of Gigabyte motherboards can still be updated manually. This requires downloading the latest version of the BIOS from Gigabyte's website and then using the company's BIOS flash tool to apply the update.
Closing Words
While the risk appears relatively low for Home systems, administrators of these systems may still want to make sure that the functionality is disabled in the BIOS. Organizations are the more likely target, and system administrators should also ensure that the functionality is turned off.
Installation of new firmware updates for Gigabyte motherboards, if released by the manufacturer, may address the vulnerability. Gigabyte has not published an official response and it is unclear if and when firmware updates will become available.
Now You: do you check for firmware updates regularly?



















Now THIS is the type of story I’m interested in! Thanks Martin.
I miss the old days when there was an actual physical jumper on the motherboard that had to be shifted in position manually by hand before the BIOS could get updated.
This is why I – who routinely disable any phone-home capabilities in anything I can – don’t pay attention to people who accuse me of being paranoid.
I’m capeable of managing my own updates, thanks.
be it that or the root-kit like armory crate from ausus or any other pro comfort / convenience / lazyness user soft-wash option that comes at cost of security. its time companies put more load on users brains instead of trying to do the thinking for them (in a sloppy way) what will alwas fail horribly at the end.
Teach users tech – if they want to deal with tech. everything else will not work OR put some real efford into your solution.
Yep. I can’t remember if I mentioned gigabyte in the ASUS article but they have been a problem for a while too.
So lately MSI, ASUS and now Gigabyte are receiving bad press for one reason or another. One of my last mainboards was Gigabyte, the hardware side was generally good but the software side was another thing. Terrible!
This is another one dumb and useless functionallity that can cause a threat to end users. Especially in this type of hardware where manufacturer will stop supporting and releasing security update after a few years of product unveiled
Giga-backdoor-like. I wonder how many other motherboard brands are affected with similar danger.
I’ve seen many HP computers that install spyware (telemetry) drivers into the OS from BIOS. Clean install the OS all you want and it comes back. I had to jump through a lot of hoops to block that mess.
@Tony, and I think that HP printers have some kind of telemetry also. I know that it’s a nonsense idea, however a friend of mine has talked about this some days ago, making some fun jokes about where the scanned documents are really going. Or perhaps not a joke? :S