A Closer Look at KeePass: Why Its Reputation as a Safe Password Manager is Being Questioned

With the recent security breaches involving LastPass and Norton Password Manager, it's understandable that people are wary about keeping their passwords in the cloud. That's why there's been a rise in the popularity of password management solutions that store passwords locally, like KeePass, which is free and open-source.
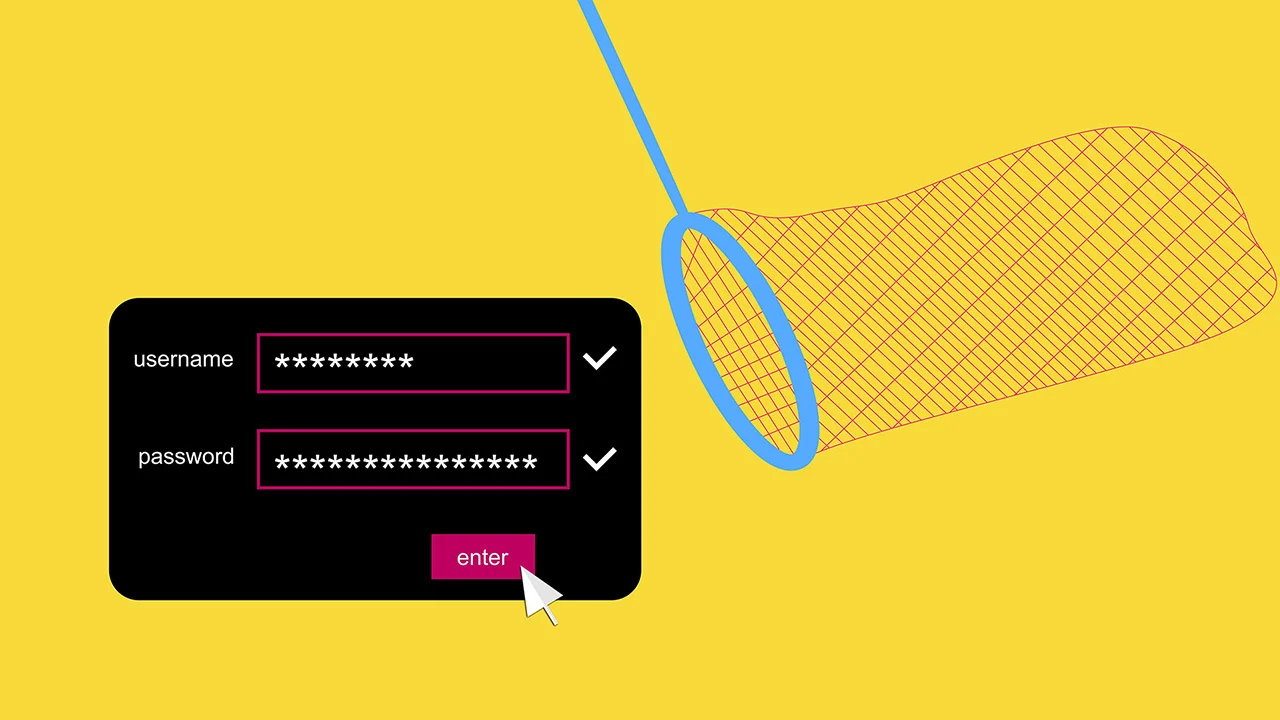
However, there's a potential flaw in KeePass that's recently been uncovered, which could allow an attacker to get their hands on all your locally stored passwords using a basic tool like Notepad. Although the creator of KeePass hasn't commented directly on this issue, it's still a concern for those who place a high value on the security of their password information.
gHacks Deals -> NordPass: Securely Store, Manage & Autofill Passwords

How KeePass works
KeePass is highly customizable, surpassing all other password managers. The customization is done through a system of triggers, conditions, and actions. Triggers can be simple events like launching the program, opening a database, or shutting down the program, or more advanced events like time-based triggers or custom button triggers. Triggers can also be set to activate only when specific conditions are met, such as the presence of a particular file or the availability of a remote host.
The majority of actions in KeePass relate to internal operations like importing/exporting the password database or syncing it with a backup file. But triggers can also execute command lines or launch URLs, which is highly desirable for hackers. The KeePass website provides examples of useful triggers, such as backing up the database, exporting it to a secondary format, and syncing it with cloud storage.
How to abuse the trigger system
In January 2023, security expert Alex Hernandez revealed a potential attack on KeePass, where the trigger system could be abused to extract a plain text version of all passwords stored in the database. The National Institute of Standards and Technology took the report seriously and added it to their vulnerability database under the identifier CVE-2023-24055. However, KeePass disputes these findings.
Hernandez shared the code for this attack on Github, which can be reviewed by those with technical knowledge. In short, the attack involves editing the KeePass configuration file to create an action that triggers when the database is saved. This causes KeePass to export the password database to a plain text file without requiring the master password. Another trigger then uploads this exported file to a server waiting to receive it. All that is required to carry out this attack is the ability to edit the KeePass configuration file, which can be done either by accessing an unlocked computer and using a text editor or by using a remote access Trojan to do it remotely.
Security devs should assume that a system is compromised
Despite the report from Hernandez about a potential attack on KeePass, the creator and founder of KeePass, Dominik Reichl, brushed off the supposed vulnerability. He argued that anyone with enough privilege to edit the configuration file can cause even more damage and dismissed the need for a change in KeePass. He stated that KeePass cannot guarantee security in an insecure environment.
However, in today's security landscape, the idea is to assume that the system is already compromised and find ways to maintain security. This approach, known as Zero Trust, is central to many modern security practices, including cloud-based password managers that authenticate users without actually knowing their passwords.
Trusting KeePass means trusting third-party plug-ins
Local-only storage has been a popular feature of KeePass, but it comes with some trade-offs. While it's great that KeePass stores your passwords solely on your PC, manual syncing with another installation can be tedious. However, KeePass does have plug-ins that make syncing easier, but using them means trusting a third party to handle your data securely. This puts your passwords at risk, just like with cloud-based password managers. Although basic cloud storage services have security features, they're not as robust as dedicated password storage in the cloud.
Keep in mind, local storage doesn't mean you can't sync securely. For example, the now-defunct MyKi used to store passwords on mobile devices and sync them through relay servers without storing them on the servers. Unfortunately, MyKi shut down after being acquired by JumpCloud. To sum it up, KeePass does offer local storage, but if you want easy syncing, you're exposing yourself to more security risks.

Should you still trust KeePass?
So nothing really happened in January with KeePass. There was no attack or data breach. The researcher just pointed out an existing vulnerability that has been around for years. The cool customization options in KeePass that people love can also make it vulnerable if not used carefully.
If you still want to use KeePass, be sure to take some precautions, like keeping good antivirus software and a strong password for your Windows account. If you need to step away from your desk, lock your computer to protect your passwords. However, if you want to sync your passwords automatically, you'll have to trust the author of the sync plugin and rely on the security of your cloud storage provider. This means your passwords could be exposed if either the plugin or the cloud storage provider is not secure.
Advertisement
















Yes, Myki was acquired by JumpCloud but the technology still lives, now under JumpCloud Password Manager — JumpCloud Password Manager is built on a decentralized architecture, where the password vaults are stored locally on user devices and are synced in an end-to-end encrypted manner between multiple devices through the use of cloud servers. Passwords are stored locally and synced in an end-to-end encrypted manner between the devices users choose, with no master password needed to access the vault. This modern approach to password management architecture allows users to remain productive with an enjoyable, seamless experience, while promoting secure credential management practices.
How much did you get paid to run this?
Shouldn’t trust the best password manager? Go do a research on what this vulnerability really means..
Sorry to see ghacks net slipping into a third rate tech site. The old ghacks net has gone. It is no longer the first tech site I visit. Seeing the amounts of comments has drastically declined, I am not the only one. It is not even a true tech site anymore.
When ghacks net was taken over by Softtonic I knew bad things would eventually be happening.
About KeePass: It is and remains very safe software out of the box. In addition, it has the look and feel of internet 1.0 which is one more reason for me to like it.
This article is a big shame, and it does not undermine KeePass at all, but it does certainly undermine ghacks net again.
The levels of calamity in this article are enough to make a riotous comedy movie.
Remember the days when eejiots thought that open source was the only way to do trustable software … because the code could be reviewed?
By whom?
Certainly not the users.
How often?
Certainly not every release.
Software is hard work. Until accountable entities create laws to validate see against; invest the required resources to develop reliable software for citizens to access services safely; enforce those laws with automated auditing for every release, there will never be a basis for trusting even the most trivial of our credentials to someone else’s computer.
We all need to recognise that digital life is not the exciting, dynamic future we have been ‘sold’.
Digital life is a fraud. Capable of destroying lives yet negligently, incomprehensibly unregulated and therefore unaccountable.
Meanwhile the tail is wagging the dog because the only entities we can even remotely hope may bring some order to the lawlessness – governments – are the same morons forcing us on to the net as the only means of accessing critical services.
Worse still, articles like this one merely jump from one calamity to assuming there an answer to this madness in the form of some generic software development mentality. You know… the likes of which we’ve read about all too often before?
How can you reference this ‘zero trust’ concept as anything more than another buzz phrase designed to delude everyone that there’s an answer also available that will solve the mass fraud that is this form of a digital life we are being fed?
You think there’s really a way to isolate one function from the real password data?
What are they doing …passing a token around instead of the actual password?
So that simple approach unquestionably makes the software ‘secure’ ?
Maybe it’s written in Rust so it’s impervious to buffer overflows as well?
Wow, how solid and simple that sounds! As incontrovertible as the earnestness of a children’s TV host extolling a simplistic morality tale to a puppet.
Reckon I might go and throw together a software security suite. Must be the equivalent of printing money. Some hole found in your software? Nevermind, doesn’t matter how many people and how deeply their lives got screwed by negligence. You can just issue a patch and chalk it up as the nature of software development.
yet another SEO backlink stuffing article to trick search engines into ranking softonic higher huh? Pathetic. This site has zero credibility left.
Security isn’t about handling hackers once they’re in your system, it’s about keeping them out to begin with.
Keepass to me, is one of the most sophisticated and safest ways to store and manage the 79 user accounts that I have generated over the years.
Funny that someone recommended to use KeePass in the LastPass, he didn’t know that it’s also not safe lol.
I rather use KeePass than storing anything in the cloud.
Sooo – this entire article is just a flat-out lie?
Rather awkward ….
Honestly is the last straw, I’m removing Ghacks from my favourites, the amount of misinformation and bias is real.
First with Microsoft, now with KeePass, is getting ridiculous.
Ghacks is no longer a source of trustful and useful information.
I use 1Password app
Expensive and 3rd party cloud-based. No better.
Who is this “we” who thinks storing data in the cloud is safe?
Storing data anywhere is not 100% safe. In the cloud, data are off site and backup is managed professionally. Stored locally, you need SHOULD backup off site in case of natural (or unnatural disaster).
We each choose our own risks, whether knowingly or in blind faith based on what we read that supports our decision while ignoring or rationalizing things that oppose our decisions. Look up ‘cognitive bias’ if you don’t understand the point I make.
Does ghacks seriously like to ruin apps like Keepass that have a long history and now in this time completely are update with latest security and performance issues and are FOSS and are not for some for-the-profit corporations ?
Recently many posts of you has been like this unfortunately.
You even won’t read the previous article in ghacks that Martin wrote that keepass fixed this (although it were not an issue)
About your big words about zero-trust and such.
Those security systems must implemented in OS.
like android and IOS that have completely isolated permission system.
But all our current desktop systems don’t use that sort of system.
Please first use a software then spread false rumours about it.
Syncing Keepass database with an official trusted third party app like Dropbox, Google drive, protondrive, the ftp sync option that is built in keepass itself, mega, one drive, synching, tresorit, spideroak and others are completely safe.
Even it isn’t important that storage be encrypted or not or it is not important it to be secure or not.
Even if you sync your keepass database with your own ftp server, it is perfectly safe as long as your materpassword be long enough, won’t be in a dictionary and you use a high amount of security when you configured the key derivation (argon2 recommended).
All above options also doesn’t need ANY plugins.
Please don’t spread things that you don’t know. Thanks.
regards.
Clarification:
By the word “you” in “many posts of you” I mean Ghacks.com and not only Russell.
Regards.
For those who may want to criticism without thinking.
A secure masterpassword that I talked about must be at least more than 20 characters and have all uppercase, lowercaseand numbers atleast, if these conditions met and you set the argon2 to a very secure configuration
(high amount of memory based on the fact that what is lowest memory of those devices that you use keepass on them, that means if your mobile device has 8GB of memory, you can use 1GB of memory in argon2 and then set Iteration number to a amount that you be okay the database take that long to open (at least more than 12 Iteration),
if all above conditions met then the longer your masterpassword be, it is better. And then what I said is true.
Regards.
Author, wake up!
What am I not getting about this? I have Keepass with no installed plugins (I just installed the Keepass software, that’s it), and use a database file stored on my local computer (no cloud).
Why does the article talk about 3rd party plugins to sync to local storage. As far as I can tell, you don’t need them.
You need them if you want those passwords on another device also.
Well truthfully you don’t need plug-ins. I have my DB synced to my personal vault in OneDrive so it’s behind a password and MFA, then additional MFA. I also use the master pass with the key file.
Speaking of a “potential flaw”, let’s ask why KeePassXC still hasn’t implemented Secure Desktop, which has been asked for years (https://github.com/keepassxreboot/keepassxc/issues/3460).
This is just a small example.
Any of these could be subjected to an info-attack with these “not as secure as we thought” headlines.
Well, if the way to compromise KeePass is via a Trojan installed remotely, most likely the hacker will have installed a keylogger and disabled any antivirus software. So any way to export the KeePass dB is moot, as the master password would be exposed. I can’t think of how you can have security on a totally compromised device – zero trust is just daft.
Anyway, most people don’t use KeePass. You could also use portable KeePass on an encrypted USB stick.
It’s open source. Contribute.
KeePassXC is meant to be cross platform. So to request supporting Secure Desktop would be for a Windows only version. That issues/3460 thread is classic beating a dead horse. Several third party products (some free) deliver protection superior to Secure Desktop, inclusive of the info-attack exploit.
Anyhow, on the topic of that CVE…
Statement on CVE-2023-24055
https://github.com/keepassxreboot/keepassxc/issues/9041
Cheers.
Assuming my system is secure should I store my passwords in a text file?
Configuration trigger is already fixed in new version (requires providing a master password to proceed).
I was using KeePass for years without any plugins. Sync can be done without any plugins by syncing password file via cloud provider like Dropbox (whether it’s safe in general to keep passwords in cloud is another matter).
Sorry but this article looks like a FUD for me, KeePass is really solid piece of software. If one prefers something more condensed – KeePassXC is great – it has more features built in (reasonable ones, no bloat), and it’s multiplatform
You’re too late. This issues has already been fixed. Now to export the data you have to insert the masterpassword. But really it’s a non issue… if you leave your pc knowing someone can acess it, you should at least lock it with an user account pw.
Russell, you’re not up-to-date. On 2023-01-09 Keepass 2.53.1 was released. The “Changes from 2.53 to 2.53.1” mention:
Removed the ‘Export – No Key Repeat’ application policy flag; KeePass now always asks for the current master key when trying to export data.
Martin wrote about this in https://www.ghacks.net/2023/02/10/keepass-2-53-1-password-manager-resolves-vulnerability-controversy/