Time to update Chrome again: latest update patches two 0-day vulnerabilities
Google released a new security update for the company's Chrome browser on October 28, 2021. The new update patches eight security vulnerabilities in the web browser, two of which are exploited in the wild according to Google.
As is the case with all Chrome releases, these are rolled out over time to the entire browser population. Chrome users should consider updating as soon as possible to fix the vulnerabilities to block any attempt at exploiting the vulnerabilities.
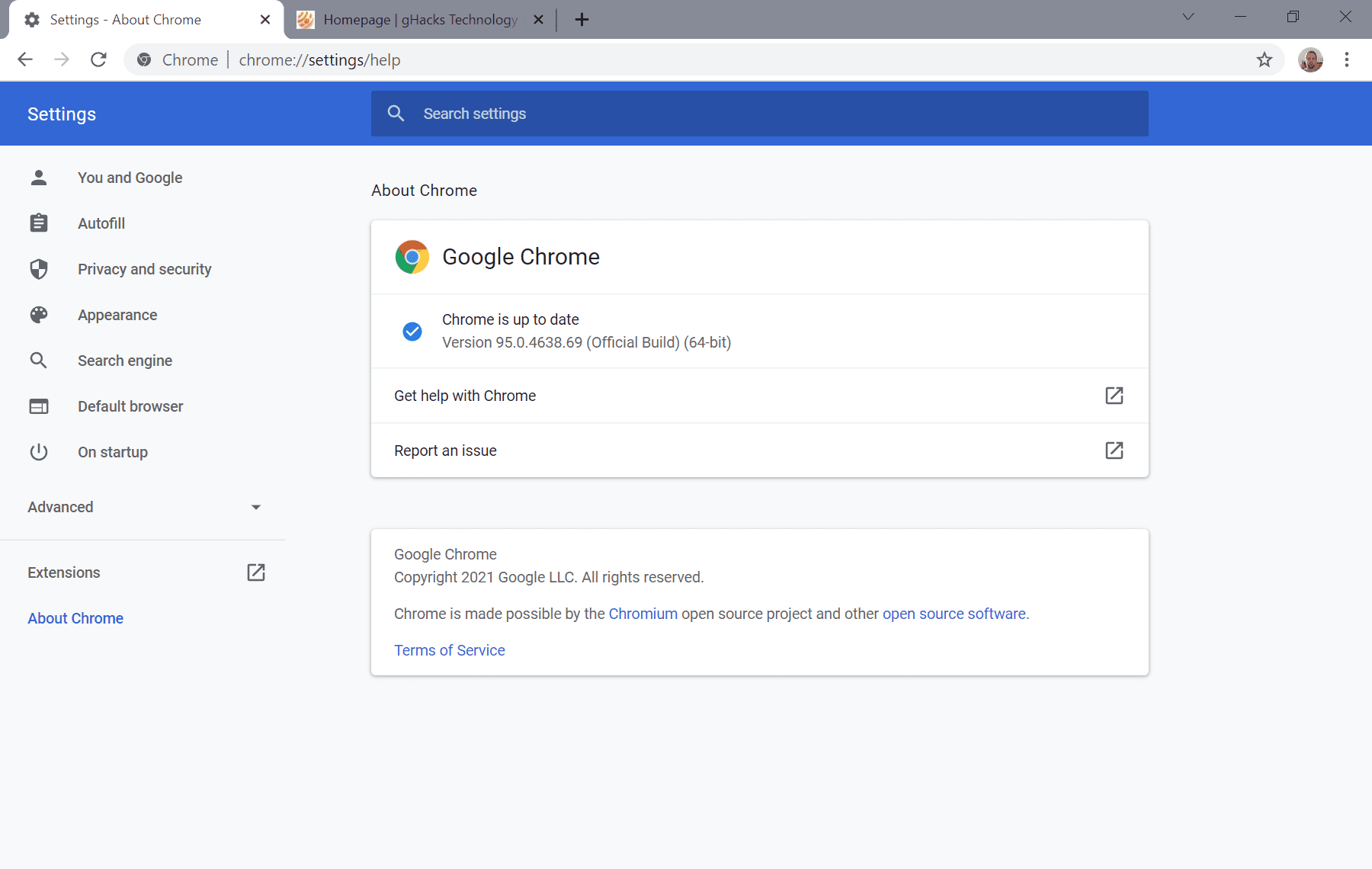
Desktop Chrome users should point their browser toc hrome://settings/help to initiate the update check. The same page is opened by navigating to Chrome Menu > Help > About Google Chrome.
Chrome displays the installed version on the page and runs a check for updates when it is opened. Any new version found is downloaded and installed automatically. All that the user has to do then is to click the relaunch button to complete the installation.
A check on the same page after the update should return the Version 95.0.4638.69 (Official Build).

Chrome users on Android can't enforce the update in the same way. It's distribution is managed by Google Play.
The latest Chrome release for the stable channel patches eight security vulnerabilities in total. All issues reported by external security researches have a severity rating of high, the second-highest rating after critical.
The two vulnerabilities that are exploited in the wild are the following ones:
[$N/A][1249962] High CVE-2021-38000 : Insufficient validation of untrusted input in Intents. Reported by Clement Lecigne, Neel Mehta, and Maddie Stone of Google Threat Analysis Group on 2021-09-15
[$TBD][1263462] High CVE-2021-38003 : Inappropriate implementation in V8. Reported by Clément Lecigne from Google TAG and Samuel Groß from Google Project Zero on 2021-10-26
Google revealed no additional details. It is unclear how widespread the attacks are and how they are carried out.
Google patched a total of 15 0-day vulnerabilities in Chrome in 2021 already.
Now You: do you use Google Chrome?




















I wonder what Martin thinks of these useless comments :)
Martin does this issue affect other chromium browsers
yes, Brave is as insecure as chrome
@fake-madaidan
Nice try, troll.
@Newer
Yes, it does. All relevant Chromium-based browsers have released the related security update already though.
I use both Firefox and Chrome with no problem. Each one has its benefits for some purposes. :]
@Anonymous
Take your degeneracy elsewhere.
Other than that, in your head, rent free apparently.
0-dayz and in goolium? wtf?
Thank god they responed so fast.
There is no 0-day. It is sold to highest bidder, exploited and then labelled as 0-day.
btw Iron Heart would you lick my balls if I choose to use brave? These balls needs some love;)
no comment
Vunerabilities that will affect 0.00000001%? that’s what people worry… complain about, I am not even a Chrome user or like Google but it is stupid to complain about something like this when in reality none of the complainers will get affected by this “vulnerability”
I was an avid fan and user of Firefox because of the philosophy behind it. But I discarded it 4-5 years ago because it just doesn’t work! Firefox is a memory hog and the sad fact is that it still is the same after all these years.
Now I’m quite satisfied to have Chromium-based Microsoft Edge and Brave. Both are fast and work well.
And internet is a dangerous and frustrating place without uBlock Origin! Man, you can block ANY element on a web page with uBO! It’s a really powerful content/ad blocker.
Good job by Edge and Brave!
Long live uBO ;)
Chrome, the gift that keeps on giving.
Really, Ad companies doing something respectable? Can’t wait for the upcoming MetaBrowser to start World War III.
“If it is not broken do not fix it” is an ostrich head in the sand approach to PC maintenance IMO. For example, I’m glad to see Chrome, Windows Defender, and Oracle Java spend the time and money to keep their products safer than they otherwise would be. Dell Support Assist has updated drivers and firmware 13 times for me in less than 3 months. So far I have had no problems with this approach. If I am not so lucky in the future, that is what backups are for.
Ah, I see we continue with the browser wars. This comment section always becomes amusing when a browser battle begins. :-)) I will agree with the adblock comments though. Don’t hit the interwebs without one. Thanks for the info, Martin.
fuckrome!
Thank you! You took the words right out of my mouth.
This comment section is being ridiculous again. The default browser of both Windows AND Android are based on Chromium, and there is a wide selection of Electron apps (Chromium inside of there as well). Furthermore, Chromium has 80% market share in the browser market. This should give you some idea of how much scrutiny it is getting – A LOT. As a consequence, more security issues are being discovered as more eyes are on the code, both benevolent and malevolent. Chromium has the best security practices compared to irrelevant competitors that get far less scrutiny (due to irrelevance):
https://madaidans-insecurities.github.io/firefox-chromium.html
Just because your irrelevant browser is getting less scrutiny does not mean that it is more secure – the contrary is the case, Firefox is years behind. Chromium is far ahead in terms of security and the above link should give you the complete picture.
Counting security issues is the method of cretins because it fails to account for the overall relevance / attractiveness to hackers of a software. This comment section is a lost cause because it, as always, fails to account for this.
how many times are you going to spam this shit – you are literally a shit spam bot and serial whinger at this point
@gorhill has spoken
Says the guy who spammed the same article over and over again in past articles. LOL, look in the mirror and then get lost.
You know very well that Chromium and Chrome are different beasts.
Something I found while looking for alternatives to Googledroid, has a decent explanation of the differences between FF and Chromium security. Yes, Chromium wins, under Web Browsing here:
https://grapheneos.org/usage
Somewhat easier to understand explanation, although phones still have to connect to a cell tower and they’re regulated differently than computers so privacy beyond a little bit is kind of pointless.
@ULBoom
Yeah, Chrome and Chromium are technically different, but as far as I know, Chrome is really just Chromium + rebrand + some proprietary binary blobs from Google. The issues discussed here are Chromium issues as well. I am not aware of any one security issue that was Chrome-specific and not a Chromium issue.
Install uBlock Origin and take care of most “zero days” yourself. Also, if you must use a chromium BASED browser, use CHROMIUM instead. You know, like in the shower you use soap and not a soap based advertising-lotion that makes you dirty and smelly. You lose nothing. Your computer will thank you.
https://chromium.woolyss.com/
uBlock Origin works best on Firefox – https://github.com/gorhill/uBlock/wiki/uBlock-Origin-works-best-on-Firefox
@gorhill’s drone
How often do you want to post that crap here? Some browser don’t even need uBO, it’s a bandaid fix for browsers that have no native adblocker.
You mean Librefox. Firefox in 2021 is a sad joke. If you must use a relic from 20 years ago, go ahead.
15 Zero days just this year? And that is what we know of. At this point Chromium based browsers are many things, but secure it isn’t.
Supposed to be the most secure browser……?
Seems rather leaky to me.
“exploited in the wild”
About all those browser security vulnerabilities, I suspect that actually visiting infected sites is not the main attack vector but that malvertising is much more efficient to reach people on any site. Which would make any browser with a built-in ad blocker, even without getting any security updates at all, a lot more secure against such attacks than the ad friendly browsers which do not bundle one. Another nail in the coffin of the “Google may be malicious against you all the time, but at least it will protect you from the rare competing malware that it does not approve” lie.
Martin, Microsoft Edge has also been updated to 95.0.1020.40 to plug CVE-2021-38000 and CVE-2021-38003 released 29th Oct 21.
Blog title edit to reflect this perhaps?
Edge is now available for Linux Ubuntu based systems, Might give it a peek on Mint maybe.
Also Edge is Chromium based, exploits probably affect all browsers based on that.
I use Chromium with a sandbox called Firejail and a custom security profile. Home directory is blocked with the exception of .config & template folders. Those seem to be necessary for loading and themes. Similar to a Windows app called Sandboxie. Might help to alleviate some security issues.
Firefox has become road kill, a rotting carcass from it’s glory days long ago. It’s so SLOW and some site do not render correctly. Chromium’s a lot more polished and from a basic user perspective, is what really matters most.
No, we’re not interested in Edge being pushed & this article has nowt to do with Edge anyway..
That snide comment by Vaccini Assassini was totally unnecessary.
Chrome is an un-safe browser, proven by the last found bugs.
Therefore a better title for this article would be;
Time to change Chrome permanently
It’s unsafe even without bugs. Google is unsafe.
If it looks relevant to what I have chosen to be interested in I read and sign up for more. If it is
simply commercial advertising or I do not trust it I ignore it as wasting my time.
and the hits just keep on coming
– https://docs.google.com/spreadsheets/d/1lkNJ0uQwbeC1ZTRrxdtuPLCIl7mlUreoKfSIgajnSyY/edit#gid=2129022708
These are all used-in-the-wild zero-days found in chrome in 2021 so far
CVE-2021-21148 2021-01-24 Memory Corruption Heap buffer overflow in V8
CVE-2021-21166 2021-02-11 Memory Corruption Object lifecycle issue in audio
CVE-2021-21193 2021-03-09 Memory Corruption Use-after-free in Blink
CVE-2021-21206 2021-04-07 Memory Corruption Use-after-free in Blink
CVE-2021-30551 2021-06-03 Memory Corruption Type confusion in v8
CVE-2021-30554 2021-06-15 Memory Corruption Use-after-free in WebGL
CVE-2021-30563 2021-07-12 Memory Corruption Type confusion in v8
CVE-2021-30632 2021-09-08 Memory Corruption Out of bounds write in V8
CVE-2021-30633 2021-09-08 Memory Corruption Use-after-free in Indexed DB
CVE-2021-37973 2021-09-21 Memory Corruption Use-after-free in Portals
CVE-2021-37975 2021-09-24 Memory Corruption Use-after-free in V8
CVE-2021-37976 2021-09-21 Memory Corruption Information leak in Core
CVE-2021-38000 2021-09-15 Logic/Design Flaw Insufficient validation of untrusted input in Intents
CVE-2021-38003 2021-10-26 Memory Corruption Inappropriate implementation in V8
2021 stats: chrome 14, firefox 0
2020 stats: chrome 8, firefox 3
Expect the carnage to continue
– https://www.schneier.com/blog/archives/2021/09/the-proliferation-of-zero-days.html
chromium is becoming a major liability: it is more targeted (fact) because it has more users (fact), and gets more exploits against it including in the wild (fact), which leads to more exploits discovered (fact) and therefore is a bigger liability (fact: because exploits in the wild are patched after the fact) as not all exploits are found (fact)
blink may have 10-20x more users than webkit or gecko, but that does not mean they have 10-20x more security engineers, or 10-20x more safe practices, or 10-20x more powerful and efficient linters and fuzzers, or that they uses a language 10-20x safer.
Did you know almost 10% of Firefox’s code uses a memory safe language called Rust?
also, before someone posts that madaidan link, here is a mozilla security engineer explaining some security basics
– https://old.reddit.com/r/firefox/comments/lbu6q2/why_do_people_say_chromiums_sandbox_is_better/glxjrjg/
“before someone post that madainwhatever link”
Eureka, it worked well.
@Yash
I was immersed in TTS alternatives, so with a small delay (and another OT, sorry) thanks for the last tip. Always thank who’s helping you! Unfortunately, until a collaboration between Vosk and Kõnele will see the light no Google vocal service right now. Well, at least I’m done with all apps, let us hope I made the right choices. Big headache, I have awoken to a world of s…
PS: better not to talk about the browser choice as an app in this topic after reading comments :-)
Yep understood :-)
@Yash
> Eureka, it worked well.
Eureka, when this guy writes nonsense (but still nowhere close to your laughable comments, mind you), I link to the factual refutation. It’s inevitable, and was already anticipated beforehand by him – because this guy knows perfectly well that his own comments are complete BS.
Someone does not mention Firefaux and you go full retard mode
> “Nobody uses Firefox”.
You preach to the wrong crowd, but as it seems noone likes your crap, here is your last resort, making fool of yourself in benefit of this site.
Sad and funny.
@anonymous
> You preach to the wrong crowd
“Dear Iron Heart, you are talking to a bunch of fanboys!” Yeah, that changes the facts… Oh wait, it doesn’t.
> but as it seems noone likes your crap, here is your last resort, making fool of yourself in benefit of this site.
Has to be a new kind of making a fool of oneself, refuting misleading numerical comparisons, wrong claims about Rust etc. The fools are those posting this crap, not the one refuting it.
And that no one likes “my crap”… Well, you’ve already established that I am talking to a bunch of fanboys, and what’s more, liking / disliking the facts is not a criterion for their truthfulness.
I have already highlighted shortcomings of madainwhatever website. Also I have asked for evidence to support his nonsense claims about Firefox vulnerabilities exploited in real world. You didn’t provided any evidence, and more importantly couldn’t back up your point. So yeah I’m saving you the trouble of writing another nonsense comment by instead just chirping along and having some fun. But you didn’t like that. So here’s one more time – Can you point any Firefox vulnerabilities exploited in real world as mentioned by madainwhatever?
Funny enough article clearly states how these zero days vulnerabilities are surfacing in Chromium at worrying pace, but hey issue is with Firefox, very smart eh.
@Yash
> So here’s one more time – Can you point any Firefox vulnerabilities exploited in real world as mentioned by madainwhatever?
Dude, of course I can. It adds nothing to the debate though:
https://www.theverge.com/2019/6/18/18684272/firefox-zero-day-flaw-browser-attacks-crypto-patch
https://www.wordfence.com/blog/2016/11/emergency-bulletin-firefox-0-day-wild/
https://arstechnica.com/information-technology/2020/01/firefox-gets-patch-for-critical-zeroday-thats-being-actively-exploited/
https://www.zdnet.com/article/firefox-gets-fixes-for-two-zero-days-exploited-in-the-wild/
https://blog.mozilla.org/security/2015/08/06/firefox-exploit-found-in-the-wild/
https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-mozilla-firefox-could-allow-for-arbitrary-code-execution-17/
There’s is even more cases but that should suffice here. Why does it add nothing to the debate though? It adds nothing because “exploited in the wild” is not an actual criterion differentiating one security exploit from another. It just increases the urgency for an update, nothing more, nothing less. Per se, any security issue has to be taken seriously once reported by a human being who has found it(!). Whether or not it is already getting exploited adds nothing on top of that, it has to be fixed no matter what. Most security issues fixed in Chromium, despite the sensationalist gHacks articles, were not exploited in the wild either. That’s the minority of cases.
> Funny enough article clearly states how these zero days vulnerabilities are surfacing in Chromium at worrying pace, but hey issue is with Firefox, very smart eh.
Issue is with misleading numerical comparisons failing to account for the popularity / attractiveness as a target of each software.
The Chromium user base is 25 times as big as the one of Firefox, don’t you think that more eyes are on that code, both benevolent and malevolent? Yeah? OK. Then you should conclude that it makes no sense to say “Oh, so much more issues are discovered for Chromium! Means Firefox is more secure! Look at the numbers!” – This is idiotic, just because hardly anyone cares about Firefox, doesn’t mean it is more secure. As per the madaidan articles, it is materially less secure and there are years of engineering to do until it catches up.
First thanks for sharing these links, credit where credit’s due.
‘Oh, so much more issues are discovered for Chromium! Means Firefox is more secure! Look at the numbers.’
No one is saying this. Not a single software is invincible. That’s why patches are released, but the main point is Why on earth is Chromium having all these zero days vulnerabilities at such worrying pace?
And what does it say about those so called security experts who advise to not use a particular product aka Firefox because it is insecure?
“The Chromium user base is 25 times as big as the one of Firefox, don’t you think that more eyes are on that code, both benevolent and malevolent? Yeah?”
Dump this point in your backyard. Software security doesn’t work this way, and you know that. Coz if it is then GrapheneOS is not secure as you know less eyes on that code.
@Yash
Dude, the guy above, @jack, clearly posted a misleading comparison between Firefox and Chromium or Chrome, which fails to take into account the popularity / attractiveness as a target of each software, in the end this was meant to invoke the wrong impression that Firefox has stronger security practices at the code level, which it hasn’t in reality.
As you said, nobody claims invincibility, yet it is a fact that some browsers have stronger security practices than others and if you have to counter this with misleading comparisons, then I don’t know what to say.
> That’s why patches are released, but the main point is Why on earth is Chromium having all these zero days vulnerabilities at such worrying pace?
The reason for the last fixes was the Tianfu hacking contest in China: https://therecord.media/windows-10-ios-15-ubuntu-chrome-fall-at-chinas-tianfu-hacking-contest/
Google fixed the issues recently discovered there, this just happened to be shortly after the last security update due to how the hacking contest was scheduled.
> And what does it say about those so called security experts who advise to not use a particular product aka Firefox because it is insecure?
Uhm, it says nothing about them? Again, just because Chromium is getting way more scrutiny and thus has more issues discovered, doesn’t mean that its security practices are worse than those of Firefox. The contrary is the case, Firefox has years of engineering ahead of it in order to reach the level of exploit resistance Chromium already features today.
> Software security doesn’t work this way, and you know that.
If you think that the amount of malware attacking a system is not correlated to the popularity of said system, then I don’t know what to say. LOL. Why is there much more malware for Windows compared to e.g. Linux? Guess what, popularity is the answer, again despite Windows having stronger exploit mitigations than Linux.
> Coz if it is then GrapheneOS is not secure as you know less eyes on that code.
Again, you are asking the wrong questions. Correct question: What is GrapheneOS based on? Answer: Android. How many people use Android? Guess what, Android issues usually affect GrapheneOS at the code level even though it mitigates many issues a regular Android build would face. Those issues still have to be fixed even if mitigated in some cases. And Android is pretty popular, so issues will be found. D. Micay merges the upstream fixes.
@jack
> 2021 stats: chrome 14, firefox 0
> 2020 stats: chrome 8, firefox 3
Completely irrelevant, just like Firefox. Nobody uses Firefox, it has much less eyes on the code in 2021. Its security practices are a decade behind as you can read under that link you fear. Also, in the pwn2own hacking contest, so far, Firefox always got pwned and owned first. When you challenge a hacker to actually find security issues in some kind of contest, Firefox is revealed to be the security failure it is. In the real world, due to its non-existing user base (compared to Chromium) it is just an unattractive target.
Also, how long do you want to repeat your misleading arguments? Like, seriously?
> blink may have 10-20x more users than webkit or gecko, but that does not mean they have 10-20x more security engineers
Don’t worry, at this time the security engineers are fully able to cope with whatever threat arises, they fix issues very quickly. And yep, Chromium has many times the number of individual contributors compared to Gecko.
> Did you know almost 10% of Firefox’s code uses a memory safe language called Rust?
Misleading point of yours, once again:
“Firefox does have some parts written in Rust, a memory safe language, but the majority of the browser is still written in memory unsafe languages and the parts that are memory safe do not include important attack surfaces so this isn’t anything substantial and Chromium is working on switching to memory safe languages too.”
source: https://madaidans-insecurities.github.io/firefox-chromium.html#miscellaneous
> also, before someone posts that madaidan link
The moment you repeat dumb, misleading arguments, you just know that this link is inevitable. LOL.
> here is a mozilla security engineer explaining some security basics
Hm… Quoting from that link you’ve posted:
“It is true that, as of this writing, Chromium’s content process sandbox is more restrictive than Firefox’s sandbox (this is continually changing though as the Gecko hardening team continues to make improvements).”
Even the Mozilla engineer admits that Firefox is behind Chromium at this time. Do you think gHacks readers are too stupid or too lazy to actually read the comment you linked to?
@Iron Heart :
Yes, about 10% of the Firefox is written in Rust – but it is a crucial part of the code. In Chromium the renderers are sandboxed (see https://chromium.googlesource.com/chromium/src/+/refs/heads/main/docs/design/sandbox.md and https://chromium.googlesource.com/chromium/src/+/refs/heads/main/docs/design/sandbox_faq.md).
In Firefox, it’s exactly the rendering engine which is written in Rust. So this makes a big difference considering the both Google and Microsoft acknowledge that about 70 – 80% of all security issues are caused by memory-related issue.
iron heart
– selectively quotes the Mozilla engineer and purposefully misses the entire point of what he is saying
– confirms that 10% is not 100%
– thinks only some code is important for attack vectors
– confirms that Firefox is less of a target
– posts massive rant of nonsense which has continually be copypasted and spammed at ghacks for the last two years
You already made an absolute ass of yourself – https://www.ghacks.net/2021/10/22/google-released-chrome-95-here-is-what-is-new/#comment-4507090 and prior comments
@jack
> selectively quotes the Mozilla engineer and purposefully misses the entire point of what he is saying
He says nowhere in the entire post that Firefox is equal to, or better than, Chromium in terms of security. He confirms the contrary, while saying “We do our best to catch up.”. Why are you afraid of the facts?
> confirms that 10% is not 100%
> thinks only some code is important for attack vectors
You make it sound like, btw misleadingly so, that relevant parts of Firefox are written in a memory-safe language. This is not the case. Why are you afraid of the facts?
> confirms that Firefox is less of a target
Security via irrelevance is not actual security. That’s the whole point of my post.
> posts massive rant of nonsense which has continually be copypasted and spammed at ghacks for the last two years
But still less nonsensical than your POS of a posting, which is, in fact, pure copy and paste:
https://www.ghacks.net/2021/10/22/google-released-chrome-95-here-is-what-is-new/#comment-4507035
> You already made an absolute ass of yourself
Uhm, no? I conclusively refuted your nonsense there and I did it again here. Getting tiresome. Your astroturfing is just annoying, nothing more. Give it a rest for once.
@iron heart.
By engaging in name calling you invalidate your argument.
it is the lowest failure by the rules of debate.
0% name calling, and you are approaching some level of intellectual debate.
@lux
Where did I even “name call”? Seriously? This is getting ridiculous. Just accept that my points are valid, smearing is not doing you any good.
iron heart
– still missing the point and FAILING TO READ what the Mozilla engineer said
https://old.reddit.com/r/firefox/comments/lbu6q2/why_do_people_say_chromiums_sandbox_is_better/glxjrjg/
STOP LYING. No where did he claim Firefox is the equal of or more secure than chromium. And neither did I.
Here’s the full quote
> If you’re comparing across two browsers that both broadly share similar security features, it becomes really difficult to distill into a straightforward comparison between “more” secure and “less” secure.
>
> Hardening a browser is all about “defence in depth”): You have multiple layers of security controls, with each layer intended to catch whatever slipped through the previous one. For example, a sandbox will (hopefully) catch something that broke through the defenses of the JavaScript engine.
>
> When you’re evaluating security, you really need to take a look at the cumulative effect of all layers; just comparing one layer (say for example, Chromium’s sandbox to Firefox’s sandbox) is not going to give you the complete picture.
>
> It is true that, as of this writing, Chromium’s content process sandbox is more restrictive than Firefox’s sandbox (this is continually changing though as the Gecko hardening team continues to make improvements).
>
> On the other hand, Firefox contains significant amounts of code written in Rust. Those components are significantly less vulnerable to specific types of security bugs than if they were still written in C++.
>
> How does that wash out in the end? It’s really hard to say and pretty much impossible to quantify.
Here’s some key phrases for you
– really difficult to distill into a straightforward comparison
– “defence in depth”): You have multiple layers
– you really need to take a look at the cumulative effect of all layers
– just comparing one layer […] is not going to give you the complete picture
– lists sandboxing in chrome and rust in Firefox as examples of layers
– pretty much impossible to quantify
madaidan’s technical points are good points for discussion, no one disputes that. But it’s also not a very deep analysis – there is a lot missing. Then he claims that chromium is more secure. Sticking to desktop (android is very different), that is just his opinion, not a fact. He has an axe to grind with Mozilla and Tor Project and the blog post was written for that purpose – to cherry pick and fit his narrative. He has an agenda.
Now read what an unbiased security engineer would say … read the link I gave. Spot the difference
So every time I see you post that madaidan link, I’m going to post rebuttals, because you are TALKING OUT OF YOUR ASS
> You make it sound like, btw misleadingly so, that relevant parts of Firefox are written in a memory-safe language
STOP LYING. I said no such thing. I said, FACT, that 10% of Firefox is written in Rust. I did not qualify how much of an impact that has on security, but it certainly isn’t zero. Even the Firefox engineer mentioned Rust.
When you have to stoop so low as to continually make up LIES about what others have posted, you have already lost the argument.
@jack
You: STOP LYING. No where did he claim Firefox is the equal of or more secure than chromium. And neither did I.
Also you: 2021 stats: chrome 14, firefox 0
2020 stats: chrome 8, firefox 3
I rest my case. Your misleading number games amount to that claim.
> Here’s some key phrases for you
Here’s my rebuttal to these key phrases, just for you:
> really difficult to distill into a straightforward comparison
Except when two software packages feature very similar components, as is the case here.
> “defence in depth”): You have multiple layers
madaidan discussed multiple layers.
> you really need to take a look at the cumulative effect of all layers
Yes, I agree. Would make the result even worse for Firefox, as most of its layers either don’t exist or insufficiently so.
> just comparing one layer […] is not going to give you the complete picture
madaidan discussed multiple layers.
> lists sandboxing in chrome and rust in Firefox as examples of layers
Yes, and?
> pretty much impossible to quantify
Nobody quantified, nobody gave any kind of score either.
Quote mining the Mozilla employee is not doing anything for you here, you see.
> But it’s also not a very deep analysis – there is a lot missing.
How about “No.”? He compared all relevant layers afaik.
> Then he claims that chromium is more secure.
Well yeah, that’s the result when it is superior for every single comparable layer and also cumulatively. Sucks for your argument though.
> He has an axe to grind with Mozilla and Tor Project and the blog post was written for that purpose – to cherry pick and fit his narrative. He has an agenda.
Assumptions, ad hominem smearing, and further blah blah… I don’t think so. The article of madaidan is written matter-of-factly and straight to the point. When you lose an argument, it is childish to respond by saying “This guy hates me and has always hated me wah wah!”
> Now read what an unbiased security engineer would say … read the link I gave.
Mozilla engineer? Unbiased? LOL.
Anyhow, what you’ve posted is general purpose blah blah and is not refuting madaidan at all.
> So every time I see you post that madaidan link, I’m going to post rebuttals, because you are TALKING OUT OF YOUR ASS
Feel free to do so, I will do the same when you post your misleading number games again.
> I said no such thing. I said, FACT, that 10% of Firefox is written in Rust.
– You claimed this in a debate related to the security of the browser.
– None of the most attacked components of Firefox are actually written in Rust.
I rest my case. Stop being deliberately misleading and we are good.
> When you have to stoop so low as to continually make up LIES about what others have posted, you have already lost the argument.
LOL, what lies? The facts are 100% on my side and you are coping, having to come up with misleading numerical comparisons and a general purpose post of some Mozilla engineer that says absolutely zilch and is not in any way refuting, or even addressing madaidan.