Simplewall 3.0 Beta First Look
Simplewall 3.0 is the next major release of the free open source firewall and security software for Microsoft's Windows operating system. We reviewed Simplewall back in 2017 for the first time.
A beta version was released on May 7, 2019 for 32-bit and 64-bit versions of Windows. While it is possible that things may change until the final release, it is more or less ready for release already.
Simplewall 3.0 is fully compatible with previous versions. It is not suggested to install the beta version on a production system, but if you do, all settings and preferences should remain available in the new version. The same will be true for the final release.
The new version drops support for Windows Vista. Simplewall 3.0 is compatible with Windows 7 or newer versions of the Windows operating system only.
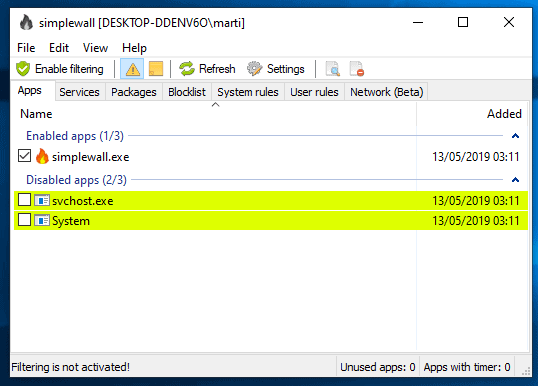
Simplewall 3.0
Simplewall 3.0 works for the most part just like previous versions. Enable filtering to block applications from making outbound connections unless you permit it. First enabling filtering leads to a large number of prompts but once those are dealt with, e.g. by blocking some and allowing others, it becomes less of an annoyance to deal with new prompts as the number decreases significantly.
The Simplewall interface features new options: you find new services and UWP application tabs, access to the rules list in the main window, and a new network connections monitor.
The Network Connections monitor is labeled as beta right now. It displays all open connections of the system when you access it or hit the refresh button.
It is not a real-time monitor as the listing is not updated automatically but only on user request. Just hit the refresh button to refresh the listing.
The monitor lists all application names, ports, destinations, protocols, and other information in its interface.
From there, it is relatively easy to create new rules for individual processes. Just right-click a process and select "create rule" to get started. Doing so opens the rules creation wizard to allow or block connections based on selected parameters. You may also open the folder the file is stored in to investigate the process further.
The Services tab lists Windows Services and you may create rules for individual services there. UWP apps are only available on Windows 10, but the apps listing displays these applications again with options to allow or deny them access to the Internet or network.
Windows users who use high DPI monitors benefit from improved DPI support next to all that. Simplewall 3.0 includes several fixes, listview resizing and sorting improvements, and some cosmetic fixes. Blacklist mode is removed in the new version.
Closing Words
My verdict from 2017 still stands: Simplewall is a great free firewall program for Windows. It still has some rough edges and requires a bit of knowledge when it comes to the creation of rules.
The future of my favorite Windows firewall app Windows Firewall Control is unclear as the program has been acquired by Malwarebytes in 2018. The program is free and version 6.0 of Windows Firewall Control was released in early 2019.
Simplewall is a great alternative, some say it is even better.
Now You: do you use a firewall app?























After the 3.01 update I lost an hour to try to find the blocklist which has disapeared without any explanation. At each major update definitely too much disturbing radical changes for me, too often I do not understand why the changes, why ever more opacity?? I will try to find a software with a dev less capricious and more respectful about non geeks users.
The program is very good but I doubt it would fare well in a code review or security audit. Take a look at the code yourself. That should be a big focus from now on.
It is unable to block many applications from accessing the net and i don’t know why.
For example to test it for yourself, it cant block uTorrents Helper file (helper.exe)
Awesome news !
I have been using it since the first release and I love it !!!
Comodo Firewall.
Comes with extra stuff like HIPS and sandbox.
@SimonAlberta
You’re right about FW Software being behind MS Botnet Development.
“phoning home†grows after every update, with URLs hardcoded into .DLL Files and other ways that prevent any internal FW to completely work. You need and external FW for blocking everything MS.
Everytime you update the hogged system, MS retrieves most of your actions – well, its METADATA.
>How do I know that Windows isn’t taking advantage of its’ sudden access to my PC to upload all the telemetry it wants?
PROTIP: YOU CAN’T
You should have another box that filters the connections going out of MS Botnet… but wait you should have it!
It’s the router! Set it up properly and you can block telemetry etc.
>Further, how do I know that Windows can’t upload telemetry via my browser access to the web any time it pleases?
Winblows doesn’t even need the browser (Application Layer). MS botnet COMMS happen at a lower System Level that neither a normally logged User, nor an Admin can touch. SYSTEM LEVEL IS UNSTOPPABLE !!
>All the “knowledge†out there talks about specific ports and servers but I am getting suspicious that this is all nonsense.
Yep, MS owns many IP ranges or, better say, many AS (Autonomous Systems).
>If Windows has just one port open to the internet then surely it can just do what it wants?
Positive, Sir/Missus.
>Frankly I am tempted to just give up on all efforts…
FOSS, FLOSS. Libre… BDS, *Nix-Like, systemd-Free Distros…
>So, what is the verdict?
:+1:
0. OpenBSD PF: http://www.openbsd.org/faq/pf
1. Outpost Firewall by Agnitum (RIP)
2. Comodo FW with CRUELSISTER preset
For now at least Malwarebytes is letting WFC continue pretty much as before. Can see the author’s posts here:
https://www.wilderssecurity.com/threads/windows-firewall-control-wfc-by-binisoft-org.347370/
Oddly enough, I still use an old PC Tools firewall, which I’ve used since something like 2005. It works, perfectly and the settings are an absolute doddle. I occasionally check things, at Shield’s up https://www.grc.com/x/ne.dll?rh1dkyd2 and it seems to be doing it’s job.
Of course it is transmitting when able. I don’t know why one would assume that windows wouldn’t transmit the information it had queued as soon as it was able. Its clear that they enabled many redundant channels to releasing information to their servers.
@daveb; you said: “I don’t know why one would assume that windows wouldn’t transmit the information it had queued as soon as it was able”
I am just an ordinary end-user who has many things I find more interesting than computers and Windows and Microsoft and so I tend to just hope that things I am told are true until I find out otherwise.
In this specific case I based my “assumption” on the witterings of many self-appointed experts on blogs and forums, including this one, telling me to block “this port or that server” etc. and all would be well.
Your condescending tone NOT appreciated.
I use Windows Firewall Control but did not know it had been acquired by Malwarebytes so thank you for that information. I will now be more alert to any negative changes in it.
I previously used Simplewall. I can’t recall exactly why I switched to WFC but I think it had something to do with my not being entirely convinced it was blocking all the Windows processes that I wanted it to. I am not stating that was the case, just my own suspicion.
Which brings me to the point of my comment; I am rapidly losing faith that ANY piece of software or action on the part of a user can prevent Windows from “phoning home”.
The following may well be nonsense, and I would be glad to hear alternative ideas, but this is my current thinking;
Using WFC and several “privacy” apps to shut down telemetry and Windows Update and only “opening the firewall” briefly a few times a month to run Windows Update Manager to get security updates etc.. I had been blithely thinking that I had outwitted Microsoft, but now I am less sure.
When I run WUM I am often amazed at how long it takes to download and install tiny little Defender updates, often 10, 15 minutes or even longer.
How do I know that Windows isn’t taking advantage of its’ sudden access to my PC to upload all the telemetry it wants?
Further, how do I know that Windows can’t upload telemetry via my browser access to the web any time it pleases? All the “knowledge” out there talks about specific ports and servers but I am getting suspicious that this is all nonsense. If Windows has just one port open to the internet then surely it can just do what it wants?
Microsoft might be error prone but it still employs some of the best coders on the planet so they may well be capable of evading all the tricks and dodges that we all use to block them, and why wouldn’t they?
Frankly I am tempted to just give up on all efforts at maintaining privacy as it consumes too much of my time and effort and seems ultimately futile. (Example, I added dozens of “privacy” settings to Firefox only to have to remove most of them to fix broken websites…waste of time and extremely frustrating!)
So, what is the verdict? Am I onto something or should I discard my tin hat?
You have more control over incoming or outgoing traffic inside your network, when you put a firewall device such as pfSense or OPNSense between your modem and the rest of your network.
That can be any old Pentium class computer, as long as it has 2 (or more) NICs (network cards) if your internal network isn’t too large. If your network is large, you have to use more powerful hardware.
Although not that difficult to setup initially, very specific rules and regulations you want in your network could make things difficult.
Anyway, the firewall portion of either pfSense or OPNSense is relatively easy to manage and you can block access to Microsoft servers on there, not your Windows machine.
Even if Microsoft found a way around the firewall settings of your system, they do not have such capabilities on the OPNSense of pfSense server. This software is based on FreeBSD operating system, which has a very good safety/privacy track record and you manage can the server through a browser, so there is no need for a mouse, keyboard or monitor after the initial setup.
A solution, not for the faint of heart, but not too difficult to manage your network traffic more extensively. The default settings in either are already pretty solid regarding security and privacy.
Once you have a grasp of the network related terminology being used in both products, you can experiment (as long as you save a working copy of the configuration you already have, preferably on a portable device such as a pen drive).
OPNSense I have been using for years in this way and happily recommend it to anyone willing to learn about computer networking.
In a way it is shame to have to resort to such measures when you have concerns about your security and/or privacy.
Of course, none of this is useful when you are a (medium/heavy) user of social media on your computer, tablet or phone. The traces you leave on the internet with those are too extensive for any security/privacy protecting tool.
Martin, you included links for
This is one of the best programs I’ve ever come across, it’s lightweight, it works right out of the box, non-existing learning curve and easy to use, allows custom traffic rules, comes with pre-defined blocklists for Windows telemetry (quadruple check ) and is open-source. Definitely recommended.
Glasswire is also very nice for monitoring as it provides a nicer real time interface, but it’s more restrictive when it comes to create your own traffic control rules (at least on free tier).
Haven’t tried Windows Firewall Control but I don’t like it’s now part of Malwarebytes. I’ll give it a try one of these days just for testing it anyway.
By the way Martin I don’t see the links for simplewall in this article or the previous review so I’ll leave them here:
https://www.henrypp.org/product/simplewall
https://github.com/henrypp/simplewall
Links are always in the summary box below the article if it is a software review.
Tried firefox and chrome, no link there for me and i have been staring for ages. thanks to previous poster for posting the links.
So, i assume “network connections monitor” is the same as “Connections Log” from WFC?
Also “Blacklist mode is removed in the new version.” Does this mean it’s not possible to block all connections by default and only enable those we want?
No that is different. Blacklist mode allowed all connections but from processes that were blacklisted. You can still block all.
I use Windows 10 Firewall Control by Sphinx-Soft. I’d love to see you review it.
Do you use a firewall app?
Yes (it’s indispensable IMO)… Glasswire Elite !
Hmm. Will have to check this out. I see their Android firewall is really highly rated.
I use this program a long time now and can’t wait for 3.0 final
For me, it’s the best firewall program which also works with Windows firewall
Never seen marked “final” version. Each time I have a look at the about it always says “beta”.
@Anon You installed the beta version, so it keeps being updated in the beta channel. To make it simpler for you, imagine you’re using Firefox beta. If you’re opening it’s about page, it will always says beta. And it won’t automagically updated to stable releases.
@Kalandria. I have disabled auto-update, I always download the last release from there: https://github.com/henrypp/simplewall/releases. No version marked as beta, but it will always says beta. Something not clear.