Firefox 67 with anti-fingerprinting technique letterboxing
Mozilla Firefox 67 will feature a new anti-fingerprinting technique that protects against certain window-size related fingerprinting methods.
Mozilla plans to integrate the new feature in Firefox 67 but delays may postpone the release. Firefox 67 will be released on May 14, 2019 according to the official release schedule.
The technique comes from experiments that the developers of the Tor browser conducted and is part of the Tor Uplift project that introduces improvements in the Tor browser to Firefox (Tor browser is based on Firefox code).
Window dimensions, especially in maximized state and when windows are resized, may be used for fingerprinting.
Fingerprinting refers to using data provided by the browser, e.g. automatically or by running certain scripts, to profile users. One of the appeals that fingerprinting has is that it does not require access to local storage and that some techniques work across browsers.
Tip: A study analyzed the effectiveness of fingerprinting countermeasures recently.
Maximized or fullscreen windows provide screen width and height information. Fullscreen reveals the actual screen with and height, a maximized window the width and height minus toolbars.
Resized windows on the other hand reveal exact dimensions of the browser window, e.g. 1003x744.
Letterboxing protects better against window size related fingerprinting techniques. It is a method that rounds the content view dynamically using 128x100 pixel steps.
Letterboxing adds margins around the content view of the window and calculates the margin dynamically to ensure that it is applied to resize scenarios as well (and not only when a new window is created).
Setting this up in Firefox

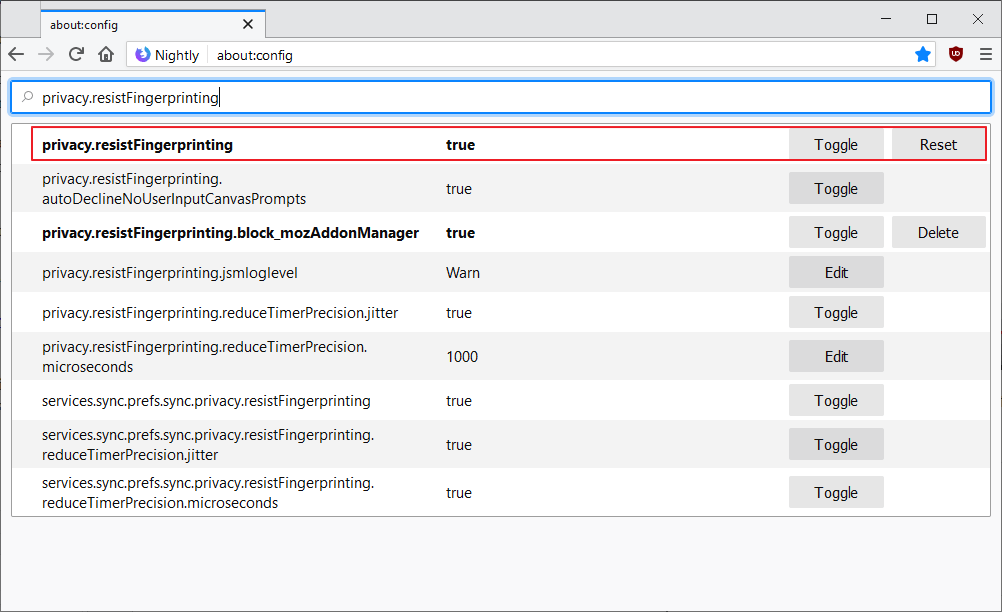
The Firefox preference privacy.resistFingerprinting determines whether anti-fingerprinting is enabled in Firefox. Note that it may render some sites and services unusable or less functional.
- Make sure you run at least Firefox 67 (check about:support for the version. Note that this does not appear to have landed in Firefox Nightly atm)
- Load about:config in the Firefox address bar.
- Confirm that you will be careful.
- Search for privacy.resistFingerprinting.
- True: Fingerprinting protection is enabled including Letterboxing (as of Firefox 67).
- False: Fingerprinting protection is disabled.
You can verify that the protection is in place by visiting Browserleaks or any other site that returns the screen resolution and viewport. Just change the window size a couple of times and reload the page to find out if it rounds the resolution and viewport (it should return a multiple of 128x100 pixels).
You may also notice the margins that Firefox uses when the feature is enabled.
Now You: Have you enabled anti-fingerprinting in your browser?























If I’m reading this correctly, does this mean I could go back to using a toolbar on the bottom part of my browser without it disclosing a smaller window size? :thinking:
GTM (GoogleTagManager) is easily the most insidious tracking platform, not inherently, but nothing is done to prevent or audit what site admins are deploying (in real time) with it.
It comes pre-packed with the full GA (Google Analytics) platform as a default ‘tag’ but you can then add as many 3rd party/custom ‘tags’ as you wish. It is literally meant to act as a black box container with the Google branding that allows for the creation of a dataLayer object that blankets the website and proceeds to then asynchronously deploy every ‘tag’ added to it by the admin. If one were inclined, they could have GTM packed to deploy malicious payloads/viruses/malware limited only by what the HTML5 spec and JavaScript make possible – which is close to anything one could imagine. Very scary as 1 admin’s GTM login grants acess to every GTM instance that they implemented or have publish permissions to, which could consist of dozens or hundreds of domains.
Thankfully, I’ve yet to discover a single website in the wild that managed to implement GTM in a fashion that hinges the site functionality on allowing GTM to run. So you can and SHOULD blacklist all the GTM Command and Control Servers. It won’t break or impact negatively any web services or sites. It’s stricly for ad, tracking, fingerprinting, and custom script deployment.
Another hard pass for my tastes, thanks very much.
Its ironic that google-analytics is performing extensive data-mining by running in the background at browserleakers.com. They pay web-sites to become part of their www dragnet.
In uBlock Origin I added explicit rules to block these devious bast*rds:
* google-analytics.com * block
* google.com * block
* googleads.g.doubleclick.net * block
* googleadservices.com * block
* googlecommerce.com * block
* googlesyndication.com * block
* googletagmanager.com * block
* googletagservices.com * block
* googleusercontent.com * block
For those using legacy add-ons the Random Agent Spoofer 0.9.5.6 has an option to Disable Canvas Support. Browserleakers confirmed it does indeed disable Canvas support in both the latest Waterfox and Palemoon. It also spoofs screen-size (random or fixed) and MANY other attributes used for fingerprinting
Note: google-analytics is contained within googletagmanager
How is blocking canvas better than spoofing with things like CanvasBlocker? (It doesn’t block it, it spoofs it by default.)
Doesn’t the privacy.resistFingerprinting spoof the timezone to UTC?
Is there a way around that?
I use websites like email that I would like to show in my timezone and not UTC.
Yeah, that’s problematic. Because unless all your devices spoof the same time TZ, you will end up with emails sent from the future, or replied to in the past. I’m not an email server expert, but why doesn’t gmail just always use their own server time (for date/time stamping), and this is simply converted to your local time zone settings for display?
RFP doesn’t have a switch for just TZ, but they are thinking about it: https://bugzilla.mozilla.org/show_bug.cgi?id=1426232 – a per site exception like canvas
Since the TZ can be spoofed by extensions, and extensions will be the last to modify the data, then you could use a extension: but you’ll have to find one that would allow only applying it to a whitelist – so all other domains stick with the RFP value.
Mozilla has improved the RFP pref to an incredible degree. In versions of FF < 66 or so it caused SOME breakage, captcha triggering, etc. Maybe 1 in 40 sites would have a tiny issue. But currently, its becoming very polished and the measures added to it several versions ago have been perfected. I use it alongside the ghacks-user.js in a semi-relaxed profile and never run into captchas, have no issues on sites like Netflix/Amazon/YouTube and other fingerprint flood sites (I look at the toolbar visiting wired.com or similar and umatrix has blocked 50+ 3rd party call attempts, 60 cookies have been denied, and Nano Adblock's badge is steadily passing 100 blocked connections. Utterly absurd.) which would otherwise have been allowed to gather all that telemetry to track you. To actually track a user via fingerprinting, a site needs to use dozens of vectors and combine them into a profile unique enough to pick you up out of the whole internet. It's why you're so viciously attacked when visiting sites like Google's and the rest.
Point is, the FF RFP pref counters like 25+ of the most critical fingerprinting vectors returning inaccurate telemetry which is enough to make any attempts to uniquely trace you result in failure. Without a certain number of reliably accurate printing measurements, you're a needle in a stack of needles. The more users that enact RFP, the bigger the needle pile gets. Keep in mind as well that allowing say 300 3rd party server calls, 95% of which are for ads/tracking/malconduct on a websites leads to an ugly, slower, exposed, and FAR less safe/secure browsing experience… which only accumulates from site to site if you do nothing. For me, that's a hard pass. Businesses built on a data collection and sale model offer your info to WAY sketchier parties than you may think. Gross.
@Anonymous: “Businesses built on a data collection and sale model offer your info to WAY sketchier parties than you may think.”
I don’t disagree, but I just wanted to comment that businesses built on data collection and sale without getting informed consent from those whose data they’re collecting are incredibly sketchy in the first place. I’m not so sure that that downstream customers could be any sketchier.
CORRECTION !!!
THIS IS OFFICIAL GOOGLE ANALYTICS Opt-Out:
https://tools.google.com/dlpage/gaoptout/thankyou.html?hl=en
I somehow got confused where I got it… It selects the correct version after Fingerprinting your browser..
it probably installs a unique ID…”Well ..We’re not fingerprinting you anymore.”
@supergirl:
I think the GA opt-out is very likely to be worthless. I prefer to just block GA scripts, then I don’t have to wonder.
Aww, it’s so cute when you try to talk about things you don’t understand.
@supergirl:
I think the GA opt-out is very likely to be worthless. I prefer to just block GA scripts, then I don’t have to wonder.
True dat!
But at least I have a fig-leaf when Imo my ‘Wide Open’ Profile…for Ghacks &
Craigslist so I can click on the reply button there {Yes, Its Google!} to respond to the ‘Great Deals’..LoL
I wouldn’t trust a Google addon to block Google Analytics. No Google software or hardware should be trusted, whatever the stated purpose.
Use this instead to block Google Analytics :
https://addons.mozilla.org/firefox/addon/ublock-origin/
Can we really trust Google on this?
Tried and it messed up too many sites. My browsers in full screen show up in sites such as browserleaks as 1536×864 even though that isn’t even close to the real device resolution, nor the viewport size. Smaller windows are accurately stated.
At some point, I’ve found playing too much with user agents, browser canvas, etc., causes more trouble than not. If I want a higher degree of privacy, I turn on a VPN, use Tor or both.
Does this mean that I when this feature is included and enabled in Firefox release 67 I can disable this feature, in WebExtensions/Add-ons where this feature is enabled?
And remove specific Add-ons like canvas defender?
good question.
“Have you enabled anti-fingerprinting in your browser?”
I have not. So far, effective anti-fingerprinting comes with too far high of a cost on other fronts (such as meaning that you have to leave Javascript enabled, as that’s a strong fingerprint signal) and, of course the issue with window size, etc.
When I balance the wins in terms of increased anonymity against the losses in terms of security and usability, it doesn’t come out in favor of anti-fingerprinting for me.
If you want to avoid fingerprinting, do disable JavaScript, if only for third parties.
One of the big areas of work that went into fingerprinting protection was to make it *also* work with JavaScript enabled.
@Zoulou
The problem is that very few people disable Javascript — so if you do, that alone is a very strong fingerprint signal. Combine that with the other signals websites get that don’t rely on Javascript, and you can be pretty uniquely identified.
*remove entropy
I meant to say that entropy is lower with JavaScript disabled. But a large part of anti-fingerprinting is to make JavaScript produce less entropy. (Less entropy = less unique fingerprint)
The crowd of people who disable JS is small but people are hard to distinguish from one another, especially now with fingerprinting resistance. If you hide your real IP or if you live in a densely populated area with a dynamic IP, it’s interesting.
But the best defence is still to reduce exposure, i.e. not making network requests in the first place. Fingerprinting resistance aims to remove uniqueness so that you don’t *need* to be in the no-JS crowd to hide.
100×128 increments ? They changed it from 100×200. That means more flexibility in selecting window size, but more entropy for easier fingerprintability. However since they’re doing this together with the Tor team, they know the overall entropy of Firefox with fingerprint resistance enabled, and must have figured out that going from 100×200 increments to 100×128 is acceptable.
The current window dimension constraints tend to lead people to disable fingerprint resistance altogether, which is pretty bad.
I wish that the default window width to height ratio was closer to 16:10 though, not to 4:3 as it is right now (e.g. 800×600, 1000×800, …). Most screens nowadays are closer to 16:10 than 4:3, and windows that fit the screen ratio feel more comfortable.
I actually haven’t played with this yet – I’m happy to wait until Dev hits 67. But those are just the “steps”, the actual code should use dimensions which waste the least content area. So if your browser is widescreen, the viewport will be widescreen
This wont last…messing with fingerprinting can make Google captchas fail in an endless loop.
Its been my experience that their purpose is to Fingerprint you.
Google captchas are already a bar that I cannot pass, so personally this wouldn’t affect my decision-making at all.
This. Makes it impossible the browse websites using cloudflare. On ESR52 I only get slow fading captchas which seem to never end. I tried solving them for 15 minutes straight then I gave up and disabled this feature.
Ive had some luck with this in the last few days:
https://addons.mozilla.org/en-US/firefox/addon/google-analytics-opt-out/
This is the Official 1 by Google.
I have No Idea if its Honest…
TI also just threw away my set-up of FFx 65….& installed FFx 60ESR
which helped out also…
I suspect I changed something & now they are trying to figure if its still me.
The Bastards…
We really need to outlaw this sort of behavior.
Stalking/Spying on People is ILLEGAL.
Maybe after Trump destroys the Neo-Cons here we can get a less pro-rich Govt.
And Some real privacy protections.
We NEED to protect FFx as,I believe,Google is very under-handedly targeting it for destruction.
So all of us will HAVE to knuckle under to their surveillance.
What I am doing rite now is using Waterfox as my main browser & then a wide open FFx 60 to get passed ouo.io with its Google captchas then copying the result back into my hardened Waterfox to do my REAL browsing..
1 or 2 Pages thats ALL you get…. Gargle…No more. LoL
I do use fingerprint protection and barely ever have to deal with captchas. I only encounter captchas sometimes with Tor Browser. I’m guessing you are using a VPN for the same effect.
Zoulou,
No VPN. My stance on VPNs is that they are all used to spy on users.
Same problem here with slow fading recaptchas both in Waterfox and Firefox. But perhaps some addon installed interfere too.
This script could be a good place to start, but as a user says in feedback it is too fast and sometimes “cannot contact recaptcha” appears.
https://greasyfork.org/en/scripts/31088-morecaptcha