A look at HiJackThis Fork
Remember HiJackThis? The program was designed to scan a Windows PC thoroughly for any signs of malicious software, spyware, and other unwanted bits.
Trend Micro acquired the software program in 2007 and turned it into an open source program in 2012.
The last version of the application was released in 2013; it was a beta version and the project was abandoned shortly thereafter. HiJackThis is still downloaded more than 4000 times per week from Sourceforge alone and that is not counting other download repositories the program is offered on.
The lack of updates reduced the effectiveness of the program. Developer Polshyn Stanislav from the Ukraine created a fork of HiJackThis that brings the application to the modern age. The fork is compatible with all modern versions of the Windows operating system -- the last version of HiJackThis was published two years before the release of Windows 10 -- and introduces new functionality.
HiJackThis Fork
HiJackThis Fork is offered as a portable program for Windows; just download the latest version from the project's GitHub page and run it after the download completes. A test on the virus scanning site Virustotal returned zero hits.
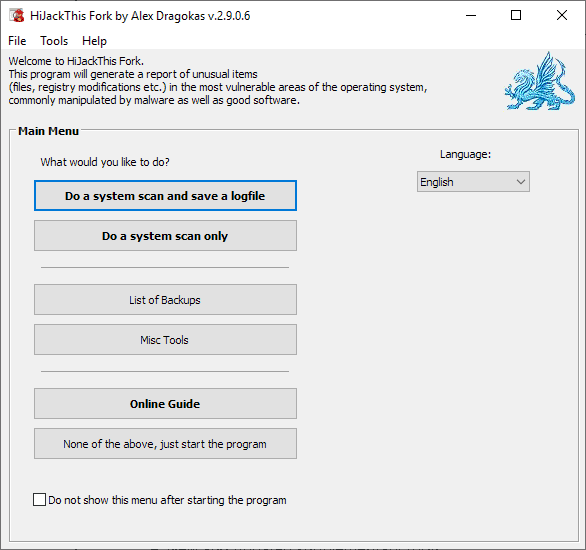
You need to accept the terms on the first run. The main window displays all available options right away. You can change the interface language -- default is English -- and run a system scan with or without the generation of a log file on the local system.
New users may click on online guide to access a short English tutorial that explains some of the basics.
HiJackThis Fork analyzes different areas of the operating system and displays its findings in the program interface and if you selected the log option as a log file as well. The option to save a log is available on the scan results page as well.
HiJackThis Fork detects potential hijacking issues primarily. It is necessary to go through the list of items one by one to determine whether an item is dangerous or harmless.
The button "info on selected item" provides a basic explanation of the general nature of an item but it won't help you make a decision in regards to the malicious or problematic nature of the item.
The program does not rate items that it finds and removing any may have unforeseen consequences on system functionality or stability.
Check any items that you want removed and select "fix checked" to delete them on the system. Inexperienced users may select "analyze this" to find out how they can have someone else look at the results to provide advice.
HiJackThis Fork includes numerous improvements over its discontinued predecessor. The developer added detection support for new hijacking methods and new tools to the program's arsenal.
You may run tools to generate an extensive list of startup items, check the digital signature of files, unlock locked Registry keys, or check LNK elements.
Closing words
HiJackThis is certainly not as important as the program was ten years ago but it is still a good tool to analyze certain areas of the operating system. The fork of the original application ensures that it can be run on modern versions of Windows and that items that the program detects are updated to reflect these changes as well.
Now You: What is your take on HiJackThis (Fork)?



























I used to really like HJT. But I always needed an analyser tool to help me sort through it all. I’m IT savvy but it is just too much info to sort through without that assistance. But all the best HJT analyser databases have shut down, so I’m afraid I will surely have to move on to other tools.
The possibility that *maybe* the analyser database can be messed with is not a good enough reason not to have them.
@Martin Brinkmann, thank you for overview.
I like it :) I found it by chance through Google.
The only misunderstanding that “The last version of HiJackThis was published two years before the release of Windows 10”.
All my versions are published in devel branch: https://github.com/dragokas/hijackthis
and can be downloaded via binary folder https://github.com/dragokas/hijackthis/tree/devel/binary
or via link in description.
Only the final v3.0 will be included in the release.
Although, the current version is absolutely stable.
The version I just got (2.9.0.6, which was committed four days ago) seems not to work on X64 systems. :(
HJT Fork v2.9.0.6 (in general, all versions) work on x64.
Your problem can be due to:
1. Malware infection.
2. System problems
3. Antivirus block
4. Some pre-installed restrictions, like policies, AppLocker etc.
You can register on GitHub and create issue about your case if you want to find out what’s happen: https://github.com/dragokas/hijackthis/issues
Has anyone done a security audit on the fork?
Is the author from the western or eastern Ukraine? Can anyone tell me if his name is more likely to indicate a western Ukrainian heritage or an eastern Ukrainian heritage?
How about the code itself? Is he just using English (Where regular languages are called for) because that’s what the language of the original coding may have been in? If not, which language is it in, Ukrainian or Russian?
I hate to give this added scrutiny just because of the country of origin, especially since western Ukraine is our ally, but since a great deal of the east is under the control of a Russian puppet government, not even counting Crimea, which Russia has officially annexed (Although the annexation is not recognized by international bodies), I doubt I’d consider using it without additional data.
Russia launches cyberattacks against the United States and other western governments, including the legitimate Ukraine government in the west, on a regular basis. I wouldn’t trust a program coming out of the eastern portion of the Ukraine for that reason. From the western part by someone not speaking Russian? Maybe I would.
To be clear, it’s the current Russian government and it’s puppet governments that I don’t trust. It’s nothing personal against Russians in general. I know people of Russian descent who I like very much- but I don’t trust Putin’s regime (In the same way that many Russians probably don’t- they just can’t say so because they live under a repression regime).
None done security audit, as far as I know. But I will not refuse if someone offers such help.
Yes, I’m using mostly English in code (as every normal developer), because it is a standard in programming. Although, several comments I made in Russian, and some in Netherlandish (by Merijn Bellecom).
I hate people make findings based on code language, spell language and origin. I call such people – racists and paranoid. If you are not, you should not care where I come from.
But if you interested I’m speaking Russian and Ukraining both good as well as most people in Ukraine. And I’m from the city near the region where fighting takes place.
If you want to see my extended opinion, look in my commentary at mg: https://www.majorgeeks.com/files/details/hijackthis_fork.html#comment-3453521586
LOL…
Wikileaks released CIA’s Vault 7 showing that everything including your Samsung Smart TV is bugged and you are worried about Russa.
https://our.wikileaks.org/Vault_7
Amusing.
LOL that was the funniest comment I have ever seen on this site. don’t worry, this app is pretty useless since it is superseded by Autoruns and the whole toolbox of Sysinternals and NirSoft, etc …
@Martin Brinkmann idea for a post: useful tools for troubleshooting malware infections.
HJT has some common detection areas with Autoruns. And HJT has areas that none of Sysinternals or NirSoft tools can see.
HJT is used every day by our specialists on several forums (e.g. KasperskyClub forum) as part of set of tools to cure PC infection. You can see details on GutHub main page of HJT Fork.
WARNING
WARNING
WARNING
Virus Total results are very poor. https://www.virustotal.com/en/file/4edd90785d2e47749f6005b16c3e1f20cc935cc9c1cfa8ff1969d6a0d4950980/analysis/1542041029/
Thank you Steve. I will see what cause VT reaction in src files. I bet on IC.exe, the program used to patch icon resource. Anyway, it has source code, supported by me and not included in program.
Fork release version is fine.
The release version is clean: https://www.virustotal.com/#/file/fe4d4192b933dd7cdad2a9e14ee66ce911637cf39cd94defee0a3dc986c3e7b7/detection
Thank you.
Presumably the github main page download link version was (is) yet to be updated.
Autoruns is a modern and more user friendly alternative.
The same as HJT. Users should not delete anything in Autoruns if they not absolutely sure what is it. It can cause system malfunction.
And you cannot rely only on digital signature or VT result when you are decide whether item is malicious. Both can be hijacked. Signature stolen. VT detection decreased by special methods.
As about HJT, it has common areas with Autoruns. It has areas that Autoruns see, and HJT do not, and vise versa.
Presumably same as before: dangerous if you don’t know how to use it.
@Bill Blagger
Agree Bill.
If one is not familiar with how to create restore points, then one probably should not use this program.
It not require RP. HJT creates full registry backup using ABR (from UVs author). It’s analogue of ERUNT. Registry can be restored by executing c:\windows\ABR\\restore.exe
Also, fork has powerful backups system. Each item you fixed can be restored (registry, files, access, date stamps etc.).
However, users should fix items if only absolutely sure what they mean.
last update 2016. yeah it is still dead.
Look into /binary/ folder: https://github.com/dragokas/hijackthis/tree/devel/binary
v2.9.0.6 updated 4 days ago, but this belongs into releases area imo.
@asd, that is not correct. Even if it were true, it doesn’t matter, because HJT doesn’t need constant updates to databases since his detection core based mostly on hajacker methods, not a database.
Also, don’t download it, please, using “release” tab (it is old original HJT). I don’t want to public release until I finish v3.0.
Meanwhile, you can use devel version, that is fully stable: https://github.com/dragokas/hijackthis/tree/devel/binary or build project yourself.
Did you look at the GitHub page, It looks to me like he updates often.
Looks like the last release is 2.0.6 published two years ago. But the program was updated 4 days ago at version 2.9.0.6. Get the file at hijackthis/binary/hijackthis.exe