Windows 10: control Bitlocker during upgrades
When you upgrade a Windows 10 device protected by BitLocker to a new feature update version of Windows 10, for example from Windows 10 version 1703 to Windows 10 version 1803, BitLocker is suspended during the upgrade process.
Suspension does not mean that the entire drive gets decrypted during the process; instead, it makes the encryption key available "in the clear" so that data is "available to everyone".
Data that gets written to the disk is still encrypted. A suspended BitLocker protection on a device does not run validation checks during startup. Administrators could use the Suspend Bitlocker Powershell script in the past to suspend BitLocker protection, for example, before upgrading to a new version of Windows or upgrading device firmware.
A security researcher discovered a bypass option during upgrades to access BitLocker encrypted data.
Windows 10: control Bitlocker during upgrades

Windows suspended BitLocker encryption automatically during feature upgrades to a new version.
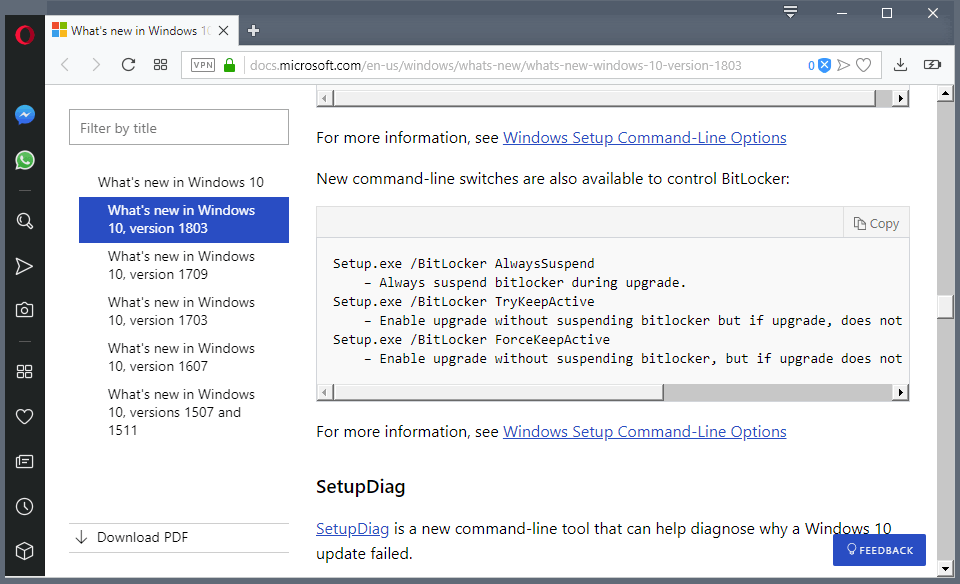
Microsoft added new command line options to Windows 10 version 1803 to control BitLocker behavior during the upgrade:
- Setup.exe /BitLocker AlwaysSuspend – Always suspend bitlocker during upgrade.
- Setup.exe /BitLocker TryKeepActive – Enable upgrade without suspending bitlocker but if upgrade, does not work then suspend bitlocker and complete the upgrade.
- Setup.exe /BitLocker ForceKeepActive – Enable upgrade without suspending bitlocker, but if upgrade does not work, fail the upgrade.
The new setup options work on Windows 10 version 1803 and later, and only on devices running Windows 10 Professional or Enterprise. Other requirements are that Secure Boot needs to be enabled and that TPM is available and that only a TPM protector is being used.
Michael Niehaus reports that you can use the commands on Windows 10 version 1709 machines that get upgraded to version 1803 as well.
The default upgrade option is set to /BitLocker AlwaysSuspend on retail devices. This is no change to the behavior in the past as BitLocker will be suspended during the upgrade if you don't supply another command line parameter.
You can use /BitLocker TryKeepActive to try and keep BitLocker enabled during the upgrade. Windows 10 attempts to keep it enabled but if it does not work will suspend BitLocker to process the upgrade.
The switch /BitLocker ForceKeepActive on the other hand enforces BitLocker encryption during upgrades. The upgrade will fail if errors occur because of BitLocker being enabled.
Microsoft switched the default command to /BitLocker TryKeepActive on Windows 10 Insider Builds. It is likely that Microsoft will switch retail builds to the parameter as well in the future.
Now You: do you use BitLocker or other drive encryption software?
Related articles
- Block "You need to format the disk" message in Windows
- Could VeraCrypt become the next TrueCrypt?
- Forensic tool to decrypt TrueCrypt, Bitlocker and PGP containers and disks released
- Microsoft: Windows 10 Bitlocker is slower, but also better
- Speed up the migration of encrypted drives to another software


















That is interesting.
I do use bitlocker. everyone should encrypt their drives. OSX and Windows 10 installed on surface tablets encrypts the drive implicitly.
Interesting, thanks!
I only have my external harddrive encrypted. Automatically unlocking on my laptop enabled.
Hopefully this will never happen, but in case my harddrive gets lost or stolen, my laptop will most likely be gone as well.
I wonder if I could turn this into BitLocker “forgetting” my laptop if a day not used.
Although, it would probably be easier to figure out if/how to encrypt my OS.