Script Safe for Firefox: better privacy and security controls
Script Safe, a popular extension for the Google Chrome web browser, has been ported to the Firefox web browser by its author.
Tip: check out our review of Script Safe for Chrome if you use the browser, or another Chromium-based browser.
Script Safe is a privacy and security extension that gives Firefox users better control over what gets loaded when web pages are opened in the browser, and what web pages may do or access.
Script Safe for Firefox
The extension is configured to block many elements that sites may load by default. This includes scripts, iframes, embedded objects, and audio or video content. In fact, the only elements that websites are allowed to load, besides the actual HTML page and stylesheet are images, Noscript elements, and Data URLs.
You can change this default behavior in the program settings. There you may switch from block to allow mode if you prefer that for instance, and customize the default behavior in detail.
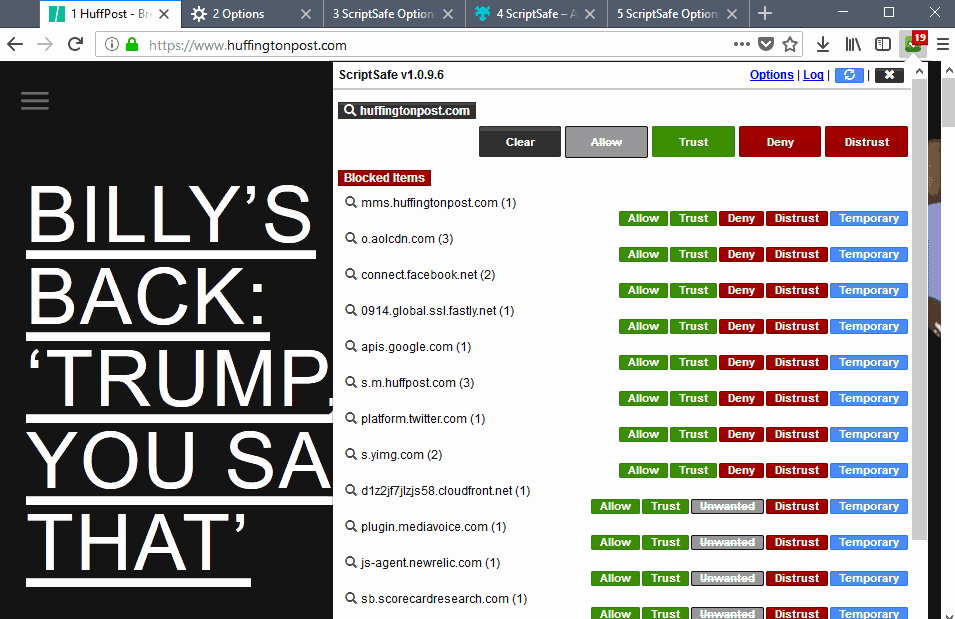
The extension adds an icon to the main Firefox toolbar. A click on it displays either nothing at all, if you use the default block mode, or the connections that the site makes.
This default behavior, of not showing any connections, is a bit problematic from a usability point of view. While this may not be an issue if the site works as expected, you cannot control individual connections unless you set the main domain to "allow".
You may need to do a hard refresh of the page afterwards (using Ctrl-F5) as the list of connections is not displayed otherwise.
You control each connection a site makes individually, so that you may allow or block individual connections, trust or distrust them.
Script Safe supports whitelisting and blacklisting which automates the functionality. Use it to whitelist trusted sites or connections that are required for functionality that you need, or to blacklist sites that you distrust.
Script Safe uses several hosts file lists to block unwanted content regardless of the mode the extension is run in. This means basically that it will block many advertisement, malware or tracking domains even if you set the program to allow mode, or allow connections on a particular site temporarily. You can still whitelist these domains manually, but there is a setting that prevents these from being loaded even if whitelist.
What more? Script Safe blocks unwanted cookies from the same range of domains as well, protects the local IP address from leaking when WebRTC is used, and blocks so called web bugs on top of that.
You can add the following blocking options on top of all that:
- Block social widgets, e.g. Facebook like buttons.
- Remove Google Analytics tracking.
- Block click-through referrer information.
- Spoof the user-agent, referrer, or timezone (does not work in Firefox properly it seems).
- Various fingerprinting protections: plugin enumeration, canvas fingerprinting, audio fingerprinting, WebGL fingerprinting, battery fingerprinting, device enumeration, gamepad enumeration, WebVR enumeration, Bluetooth enumeration, Canvas font access, client rectangles, clipboard interference, reduce keyboard fingerprinting
You are probably wondering how Script Safe compares to NoScript or uMatrix. Script Safe has a couple of usability issues, but the WebExtensions version of NoScript has them also. The main issue with ScriptSafe is that while it comes with an auto-reload feature that is enabled by default, that it does not work properly (at least not on the system I tested it on as I had to force refresh the page to get the changes to apply).
Script Safe adds fingerprinting and other privacy protections and enhancements to the browser however, more than many anti-fingerprinting extensions offer.
Closing Words
The first version of Script Safe for Firefox is up to a promising start. The developer needs to sort out some features of the extension, and work on the usability part as well. I can see this become a very popular extension though in the long run.
Now You: Which privacy / security extensions do you run?


























Another very promising extension that hasn’t seen an update in a very long time. Last update: v.1.0.9.3 (Dec 12, 2017) on both Firefox and Chrome stores. It’s a one-man side-project (according to the home page) so sometimes it easy for us end-users to forget the sacrifices involved in something like this.
Looks like a great alternative to uMatrix and RequestPolicy Continued.
As long as the author doesn’t make it compatible with Firefox 52 ESR it’s a useless addon.
Live Linux OS
Close the browser every X minutes. Close the browser before logging into any site. Close the browser after logging out of any site. Keep it open when cookies and JS are not needed. Tor, VPN are snake oils, unpolished turds that cannot be polished at all.
Proxies, local proxy, externally-owned proxy.
I tried it but then uninstalled it because it was causing problems on certain websites
You can make it work by whitelisting some components. It is a boring issue – I know – but it is needed ONE time only. Backup the settings, also.
Back in the day, Giorgio Maone (developer on NoScript) evaluated the possibility of porting NoScript to Chrome. He concluded that it was not possible and that add-ons that claimed to provide script blocking functionality weren’t secure somehow (I don’t remember the details), because of Chrome APIs.
So I am rather wary about such a recent port to Firefox. It would be nice if someone was able to see what I’m talking about and provide insight on it.
See for yourself. Visit “hackademix.net” (Giorgio Maone’s blog site) and read.
Even Gorhill has an added repository for Chromium, it is uBO-Extra:
The extension is useful only for Chromium-based browsers. There is no need for such an extension so far on Firefox, and thus there is no version for Firefox.
Visit “forums.informaction.com” and read 7 years old threads, I’m sure you’ll find some info stuck between two unrelated posts after reading for 10 hours. Probably the info will apply to 2017, crossing fingers.
—
As expected, this isn’t what I was talking about; way too old and not related to Script Safe and other Chrome add-ons: https://hackademix.net/2009/12/10/why-chrome-has-no-noscript/
The right info is located on “forums.informaction.com” and should still be about 5 years old.
@BM try Blokada
You can run 100 extension/addons, several isolated VM’s with several different operatings systems and you’re same secure as running none of them – the reason is that using programs making you not more secure, this is a myth. It might lower the attack scenario but that’s all, it not prevents someone to MITM your internet connection, manipulating your DNS, faking emails or login fields and more. In the past every deep web guy made stupid mistakes and they all got busted and none of them used 100 extension/addons. They get busted by stupid little mistakes which is difficult to see for you or any of these so called security addons.
What difference it make if you use noscript but you need to allow javascript + cookies + dom and other crap when you’re forced to login into the page? Right nothing cause you can’t use them without breaking several things, of course now several people gonna say, okay I not login into any page. Right, but there are other ways to get you, especially while writing eMails, using Amazon and more. I never heard someone use the internet without leaving traces behind – it’s a matter of time.
The thing is that none of such suites, AV’s or so called ‘security’ tools are helpful if the user has no control over it or if he is unable to use it properly. I’m not sure that people got that part. But when you never visit e.g. page xyz you not need to block it at all because your pc not makes magical connections on it’s on to this domain, there of course cross references e.g. if your daily visited page adds a e.g. like button on it which might ping back to facebook & co. but then you simply could work in general with a whitelist instead, because if you visit a lot of pages it’s almost impossible to track all website changes and merge it with your programs – however then you have less work with working with a whitelist because you take then control over the dns/domain requests – at this point you not need any tools except your router.
The rest of the attack levels are browser related which needs to be fixed within the code not with a addon.
But I let you guys believe that more tools help more —> it’s exactly the opposite. Snake oil FTW! We had it years with antivirus programs, I wonder how long it takes it’s the same with extensions… Maybe also 25 years…..
Reducing exposure and closing most security issues helps tremendously. Using a condom and taking the pill doesn’t prevent a girl from getting infected or pregnant, but that helps tremendously.
For Firefox: Canvas Defender + Cookie AutoDelete + Decentraleyes + Don’t touch my tabs (rel=noopener) + eCleaner (Forget Button) + Google search link fix + Neat URL + Privacy Badger + Referer Control + Smart HTTPS + uBlock Origin + about:config changes.
Chrome is similar, but with these substitutes: No Openers, No Phishers + Pure URL
StartPage for search
Dashlane + Authy for logins
Windows Defender + Malwarebytes Premium
A few websites won’t work with this setup, but not many.
Privacy Badger + uBlock Origin. The latter totally outplays the former.
Thank you Martin
I use Script Safe on Chrome
and now also on Firefox
Random Agent Spoofer, anyone?
Yeah, I know it’s abandoned (it can’t be ported to WebExt), but it still works.
I don’t actually use it to spoof the user agent periodically (it makes you stand out from the crowd). What’s actually useful about the add-on are all the other options – spoofing headers (ETags, Via, X-Forwarded-For, language), script injection (which allows screen size spoofing; I’m not aware of any other way to do that), and using the add-on’s UI to quickly toggle some settings (like local dom storage, which some sites require).
Secret Agent is another gem: https://www.dephormation.org.uk/
It only works with FF57+ according to the AMO site which is a pity: I wanted to give it a go, but it’s a “no-go” instead.
As to my own privacy related extensions, I have ABP + Element Hiding Helper, Canvas Blocker, Decentraleyes, No Resource URI Leak, Self-Destructing Cookies, Privacy Badger, I Don’t Care About Cookies, No Coin (anti-coin miner) and Smart Referer plus most of the “about:config” privacy-related recommendations Martin recommended.
I also run Malwarebytes Premium which blocks exploits, malware and ransomware.
A hosts file + uBlockOrigin + uMatrix. Both for Fx and Chromium.
Hey, speaking of hosts, MVPS hosts file has been updated on 30.11.2017 (I just noticed) and a search for “coin-hive” returns eleven blocked addresses! A real kick in the teeth for all those people who want to make the internet a worse place for everybody else (:
Thanks Yuliya, I’ve been looking out for an update for ages! I must have gone back and checked 10 times!!
I’ll go and get it now :)
UBO medium blocking mode .
Q: Which privacy / security extensions do you run?
XP with trick POSREADY2009
Firefox ESR – Noscript + U.B.O. + Canvas Defender + No Resource URI Leak
____________________________________
W.10 1709
Chrome – ScriptSafe + UBO + Ublock Protector + HTTPS Everywhere
Ciao Sampei, I enjoy some of your threads @ Wilders
@Sampei – interesting ideas there!
@Everyone – a question:
For the desktop is seems we have a plethora of tools available to secure our privacy to a significant degree.
What are the equivalent tools for the Android smartphone platform?
I confess some ignorance on that platform, but find that it is an increasing necessity to use well beyond just email and phone/text. Our “portal” to the web from the desktop is mainly through a browser. Android (and iPhone) does have a browser, but a great deal is via apps as well.
Don’t want to derail the topic here with long discussion, so maybe people can provide links to pages where this is more broadly discussed.
You know, the fewer the apps, the better; also use good VPN (always on) on phone. I never take OTA updates from ISP, either — the older the build, the more likely you’ll be able to use unlock bootloader/root method (go to xda to learn ins and outs of your phone, preferably before buying, but even now, just to see if there’s bootloader unlock method. If so, there will be instructions how to unlock bootloader and root). Often there are privacy-focused ROMs you can download and install.
You never had to login to goolag, ever: most playstore apps AND MORE at aptoide, and often apks of same app are available on developer’s site or xda. Get browser that supports decent privacy (not stock or Chrome), just be sure to have a VPN client running (NordVPN is my favorite; pick servers to install, choose always on, delete app).
I tend to stay away from goolag services entirely, but alternate no-login youtube apps are out there, OR a decent privacy browser, plus bookmarks of account pages you would normally subscribe to, is just as good. And you don’t have to log in to google/youtube.
@ BM You have 0 privacy on mobile, look for security at least:
https://github.com/CHEF-KOCH/Android-Vulnerabilities-Overview
try Blokada
TH.