Riot Isolator: privacy and security tool for Windows
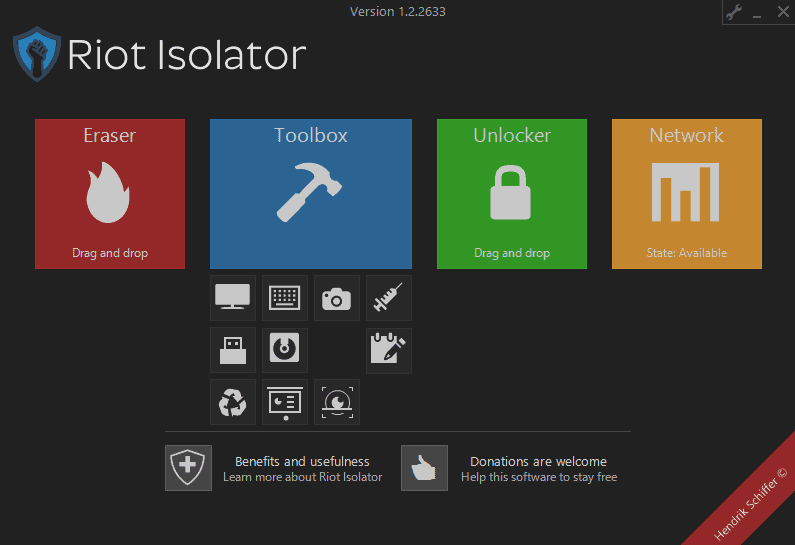
Riot Isolator is a free multi-purpose security and privacy tool for devices running Microsoft's Windows operating system.
You may install the program on a Windows machine, or run it without installation. Please note that Riot Isolator requires the Microsoft .NET Framework 4.x or higher.
The program interface itself lists the four main options Eraser, Toolbox, Unlocker and Network. Three of those, Eraser, Unlocker and Network, are single purpose tools.
Toolbox on the other hand lists ten additional tools that you may make use of.
Riot Isolator review
Eraser and Unlocker work exactly as you'd expect them to. Drag and drop files or folders on to the target icon, and either have them deleted securely from the computer system (Eraser), or unlocked so that you can process them.
The Eraser feature overwrites the data that you dragged and dropped on to the icon twice, but does not differentiate between platter-based hard drives and Solid State Drives. It is up to you to make sure that you only drag files from platter-based hard drives, as files from SSDs won't be erased securely due to the nature of how data is stored and processed.
Network logs the TCP connections within the last eleven minutes when activated. It is not a network on/off switch, but displays a graph when selected that shows the number of TCP connections instead.
Toolbox is the heart of the application. It includes the following ten tools:
- Anti-screenshot tool.
- Anti-keylogger tool.
- Anti-webcam tool.
- Anti-exploit functionality.
- Volume protection.
- Drive Eraser.
- Live report.
- Recycle Bin cleaner.
- Presentation mode.
- Realtime recognize.
Some tools, like the anti-keylogger tool, let you toggle their functionality with two clicks. Others require explanation to understand what they are designed for.
Anti-exploit for instance may prevent the spoofing of file extensions, and detect process executions in memory. The spoofing protection detects two commonly used methods of spoofing file extensions on Windows, and will kill processes that make use of it.
The detection of process executions in memory rates the risk level of these executions.
Volume protection may be used to block new USB volumes on the device, and to make all USB volumes read only.
Live Report enables limited report functionality online. I could not get this to work on the device I tested the program on. It supposedly lets you access information such as an activity monitor, module overview, or screenshots, online.
Presentation mode locks down the computer by focusing on a single process / program window.
Realtime recognize finally provides you with information on runtime about the packing tools that executable files use on the system.
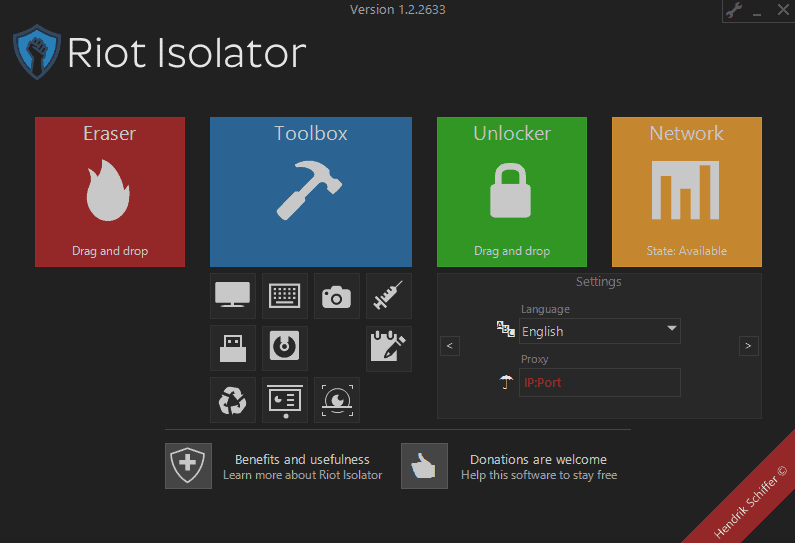
The interface of Riot Isolator can best be described as messy and compact. Settings are for instance displayed on multiple pages with no option to manage them all on a single page.
The same is true for the toolbox. You only see if you have enabled one of the "anti" options when you select that option in the toolbox.
The tools work well on the other hand, at least the ones that I ran tests for. The anti-screenshot tool blackens the screen when it is enabled. This is true not only for Windows' own copy to clipboard option, but also third-party screenshot tools.
Closing Words
Riot Isolator is a powerful program with a messy interface. While you will find your way around in the program after clicking through all the options, the fact that the state of the tools is not shown is a serious usability issue.
All in all though, this is a handy tool to have at your disposal.
Now You: Do you find a multi-purpose program like Riot Isolator useful?




























good program for setting usb to read only permanently /new drive blocking (the second one is good idea), has portable option and doesn’t conflict too much apart some CTDs with few softwares, didn’t see it doing anything malicious and the author made many other software for free. It works on the screenshot level, but other stuff is forgettable unfortunately (failed tests). Program will spot forking techniques though. The author has received alot of hate also on Wilders. Not nice since if developed further would make for some spy shelter competitor.
This is simply an other fake security product. I don’t know why we should trust software behaving suspiciously like this? And I can’t understand why use this program when it is considered by a lot of security compagnies as malware. In my test it don’t do a well job and it’s classified as malware in V.T. So it’s safe to stay away from this kind of programs and don’t trust malwares developers when they instruct you to disable your A.V or your AdBlock to install something, because the moment you disable it, you will be vulnerabe and you will be infected. That’s all what can say for now. Thank you.
IMHO it’s a pointless tool. The anti-keylogger module doesn’t work at all (tried with a basic keylogger). The anti-screenshot module looks like the only working feature as it adds an effective black overlay.
And yes, it conflicts with many well-known anti-malware software without being really useful.
“the state of the tools is now shown”
Now shown? What does it mean?
I guest the author meant “not shown”
I guess you mean guess in place of guest. :)
For god sake, no AV or ‘pseudo’ security tools. Even GUI is copy & paste from HitManPro.Alert.
Even the name seems inappropriate!
If it is not open source, how are you supposed to trust an unknown program with such important tasks?
I strongly object to a program such a this one. Apparently, it’s a secure eraser and file unlocker, to which have been added a few anti-malware functions.
First of all, you’re not supposed to use two different anti-malware at the same time, because the risk of incompatibility is too high (some well-known exceptions may exist). This program compels you to do so, since it’s not a comprehensive “anti-virus” by any stretch. Therefore the concept is flawed from the start.
Second, security is serious business, and incredibly difficult to get right. In other words, it’s for the big boys only. You can’t come out of nowhere, slap together a few anti-malware functions, not even try to offer comprehensive protection and pretend to be credible.
Finally, anti-malware programs are legitimate targets for suspicion, since they can have themselves quite malwary behaviour. Many of the reputable, well-know brands of anti-malware engage in such questionable tactics. It’s enough that we have to put up with them while prevailing ourselves, presumably, from an enhanced level of global protection. We certainly don’t need to worry, on top of that, from possible added sources of spying, data mining or adware-type behaviour.
As F-Secure themselves say :
“The very software that is supposed to protect your security is an under-appreciated threat to privacy because of the massive amount of data many products secretly gather on customers, according to F-Secure’s Jarno Niemelä.”
https://www.theregister.co.uk/2017/03/17/security_software_is_a_threat_to_your_privacy_too/
Riot Isolator will not work if Windows Aero is not enabled.
Is it another false alarm, as most security tool falsely detected its as malware? https://virustotal.com/en/file/3b10f905a69eb284ad729c3fb04853f588ccbf5218c47bf55133fdb10bc5ab30/analysis/ SHA256: 3b10f905a69eb284ad729c3fb04853f588ccbf5218c47bf55133fdb10bc5ab30
I believe you did not understand the comment I posted. When I clink on the setup file, I get an error message “you require Windows Aero to be enabled!,” which I have disabled on my system.