Microsoft's Password Recommendations
Robyn Hicock of the Microsoft Identity Protection Team published a Password Guidance paper recently in which recommendations are made to IT administrators and users in regards to password security and management.
Passwords are widely used on today's Internet, local networks and even individual devices, and while companies have started to develop alternatives, none will replace the need for passwords for authentication in the near future.
Microsoft Password Recommendations to IT Admins

The company's advice to IT administrators is to a degree quite different from common practices used in many company networks.
- Set a minimum length of 8 characters for passwords (but not necessarily more).
- Remove character composition requirements.
- Don't require periodic password resets.
- Ban commonly used passwords.
- Educate users in regards to password re-use.
- Enforce multi-factor authentication registration.
- Enable risk-based multi-factor authentication challenges.
The first three points address so called anti-patterns, the remaining four successful or beneficial patterns. These are widely used while research suggests that enforcement has negative consequences that may outweigh their benefits.
Anti-Patterns
Requiring long passwords
Microsoft suggests to require passwords to be at least eight characters, but not to enforce longer passwords (16 characters for instance) as users may choose repeating patterns to meet the length requirement.
Another point worth noting according to Microsoft is that the majority of long passwords that users are required to pick are within a few characters of the minimum length which in turn helps attackers in their attacks.
Longer passwords, at least those that don't use repeated passwords, may lead to insecure practices such as writing down the password, storing it in documents, or re-using it.
Microsoft acknowledges that longer passwords are harder to crack but that truly strong passwords ! inevitably lead to poor behaviors".
Multiple character sets
Many sites and services require that passwords include certain character types, for instance at least one uppercase and lowercase letter, and one number.
These requirements lead to bad user practices as well according to Microsoft research. Many users start passwords with a capital letter and end it with a number of those are two of the requirements.
Certain substitutes, $ for S, ! for 1 or @ for a, are also fairly common, and attackers configure attacks to take advantage of that knowledge.
Password expiry
The third and final anti-pattern addresses periodic resets of passwords forcing users to pick a new password in the process.
Microsoft notes that research has shown that users tend to pick predictable passwords when passwords expire, usually based on the previous password.
There is evidence to suggest that users who are required to change their passwords frequently select weaker passwords to begin with and then change them in predictable ways that attackers can guess easily.
Successful Patterns
Banning common passwords
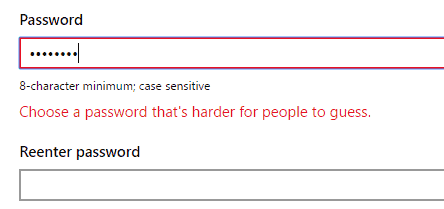
This is the most important restriction when it comes to the creation of passwords as it reduces the impact of brute force attacks.
Microsoft's Account system uses the best practice already. When you try to pick a common passwords during account creation, or password reset, you will receive the message "choose a password that's harder for people to guess".
Password Re-use education
Company employees need to be aware that reusing passwords can have serious implications for security. If an employee uses the same password that he/she uses on company computers elsewhere, attackers may be able to use successful attacks against other accounts of that employee to attack the company network as well.
Multi-Factor authentication
The last two points go hand in hand. Microsoft suggests that companies maintain security information such as an alternate email address or phone number. This can be used to inform users about issues but also to authenticate users should the need arise.
Microsoft noted the following stats changes for account customers with security information on their account:
- Password reset success jumps from 67% to 93%
- Compromise recovery improves from 57% to 81%
- User attrition rate actually drops from 7% to 3%, month over month
Guidance to users
Apart from providing guidance to system and IT administrators, Microsoft's password guidance paper provides guidance for users as well.
- Never use a (Microsoft) password on another site.
- Make sure your security information (alternate email address, phone number) are up to date.
- Verify your identity whenever the need arises with the Microsoft account application for Android.
- Consider enabling two-factor authentication whenever possible.
- Don't use common passwords, words or phrases, or personal information when selecting passwords.
- Keep the operating system, the browser, and software up to date.
- Be careful of suspicious emails and websites.
- Install an antivirus program.
- Make use of Microsoft Password and Windows Hello.
- Use trusted identity providers.
Closing Words
Microsoft's guidelines are written for the average user base. It is somewhat surprising that the company fails to mention password managers in the paper as they address several of the negatives mentioned in the IT administrator guidelines.
Now You: What's your take on Microsoft's password recommendations?






















If Microsoft are concerned about password crackability, why do they always give default passwords in 365 in the same format:
[A-Z][a-z][a-z]xxxxx
?
This is fine in most cases, as admins should change them before handing to the new user, but we all know, in self-managed tenancies, the admin will hand the password to the user as is, and the user will write it down, and the hackers will try the above pattern first in their brute force attempts. Every time I see a phishing attack, it originates from a compromised Office365 account.
Personally, I don’t enforce frequent password changes when the domain as MFA, but I always change the first password because the password pattern is always the same.
do these ***** still limit password length to 16 chars and do not allow many special characters, as they still did at least half a year ago?
I think MS is looking at the majority out there who don’t use password managers, or use work systems where they aren’t allowed to use personal software…. but I think microsoft should have flagged password managers as an option to consider.
Password Managers are always tampered by 3V1L H4CK3RS. Changing daily/weekly a paassword is a thing that comes from WWII. Obviously nowadays, when a Client/Server has an undetected rootkit and the password is changed, it is likely stolen by some 3V1L H4CK3R.
Now we know part of what MS is gathering with all the telemetry data they are pulling in with 10….
A good password manager will stop all the writing down and forgetting. I didn’t use one for years but after I started using one I don’t know how I got by without it.
I set my manager to spit out a 14 character for about everything with numbers, upper, lower, symbols, and human readable.
Difficult enough that if somebody did try to hack me they are going to waste a lot of time trying to crack that password. Long enough it should not be worth it. Weeks to months…
Enpass is my choice, moved to it from Lastpass. Browser plugin for it works well in my experience.
I like Perfect Passwords by Steve Gibson per
https://www.grc.com/passwords.htm
Anyone who is serious about passwords uses a top-notch password manager that can also generate strong unique passwords that you don’t have to remember, since you only have to remember the master password, or the master passphrase which is even better & easier to remember.
I make a print of my passwords & keep that in a safe place. I have had to use that print on a number of occasions.
FINNALY a real recommendation who suggest that forcing pll to change their passwords frequent is BAD.
I’ve been on enough companies where i’ve seen post its on the desktop, or booklets filled with passwords.
ok this is still online secure but still oh so easy to a directed hack.
When I do see this I always give the suggestion to start or end their password with a space as you don’t write it down ;-)
But I do find that people need at least 6 different passwords and even more different email accounts.
* For all informative forums and places where you don’t know why you even should register, take dummy account1
Make a Yahoo email account (not with your onw name but choose a nickname) and a simple password to remember , within the above rules as you want to keep it long time. (you only need that mail if you forgot your password, but you won’t as you”l be using that on different sites.)
* for social accounts do take a google account , then you have G+, hangouts allready checked, use this for facebook and other social stuff, you can set rules and redirect mails to your mail account you really use.
* strong account for the stuff you care about, and rather won’t loose.
* separate account and password for you main mail/ISP account
* another one for your banking
* last one for you home security
write all accounts down in a spreadsheet , just with account name and site/usage.
if you change one of your passwords , you now change it for the whole bunch, so you keep on using it ferequent and wont forget it.
Next the so called secret questions NEVER use real answers, but choose one stupid word and use that everywhere (sometimes you need 3 of them. )
like what was you mothers maiden name ? = PolarisNebula
what was your first pets name ? = PolarisNebula
what is your favourite colour ? = PolarisNebula , if need seperate : SolarisNebula, and so on.
Most of celb account hacks are made by the password forgotten option and social engineering, those answers are found on the net (facebook, ….) so don’t use real data!
As a professional IT consultant,I would need to charge for this advice , but today it’s free ;)
“It is somewhat surprising that the company fails to mention password managers in the paper as they address several of the negatives mentioned in the IT administrator guidelines”
Didn’t it already mentioned?
“Longer passwords, at least those that don’t use repeated passwords, may lead to insecure practices such as writing down the password, storing it in documents, or re-using it.”
If you know the master password of the password manager, you can login no matter how long the password. That’s why I never store my passwords outside my head. What’s worse I know some people write down their master password in paper.
I like that you think for yourself rather than blindly follow conventional wisdom, but I disagree with your point. If the password manager is offline (i.e. not on the “cloud”), then the only way it’s likely to be hacked is if someone has physical access to your computer. Well, if someone has physical access, all bets are off anyway. Any password can be brute-forced eventually if you can just grab the system!
Password managers eliminate a long list of poor user practices (simple passwords, re-used passwords, writing things on paper, etc.). This comes at the price of having everything stored in a single location, yes, but I would argue that the benefits far outweigh the drawbacks.
Not everything needs a “heavy duty” password. Sometimes all you want to do is throw up a lock screen.
Expiring a password after a set period of time was NEVER a good idea. (Just one of the things that executives and security managers decide to do in order to show users who has the real control.) When to do it should be left to the user and “potentially compromising events”.
L33T substitution was always STUPID. (“Oh, I’m so cool!”)
There’s nothing wrong with adding repeating strings to a “good” password to make it less brute-force crackable. Passphrases, though, are still better in most cases.
There’s nothing wrong with writing down password *hints* as long as you don’t make them obvious.
I wonder if they will put in password suggestions in their edge browser, something like Safari on the Mac
Reading MS recommendations makes me puke. As an old time phreaking guy then converted to hacking, debugging and whatever else, I say that… to get a fine SECRET word you should:
– remember a simple one, let’s say ” caesar ”
– convert it by calculating its hash… MD5, CRC32, SHA are common hashes. The SECRET word above in CRC32 is ” e29aed8f ” while in MD5 is ” b712916d8bfc1718a431c7b4fa280ae6 ”
By applying fantasy ( something AI will never have ) you can use more of these hashes in a chain (as done for hiding the keys in software):
For example by using http://www.nirsoft.net/utils/hash_my_files.html on a Grace Kelly image you get an hash value. You do not need any Password Wallet, but you need to remember that GraceKelly.jpg gives you the password for your facebook account.
I was starting to believe that Microsoft really didn’t care at all about Internet users after its Windows 10 behavior but now that I read the company’s commitment to a safer Web for all I feel confident.
OK, finished joking.
Like pointed in the article strange Microsoft doesn’t mention password managers, which is the basis :
“Microsoft acknowledges that longer passwords are harder to crack but that truly strong passwords “inevitably lead to poor behaviors”. Inevitably? … The only thing inevitable is to have a correct password management without a password manager.
When Microsoft doesn’t revolt me, it makes me laugh.
Yeah, the hairs on my arms stood up when I read the word “inevitably” in that quote. I would actually argue exactly the opposite of what Microsoft said: if you force users to have really looooong passwords (100+ characters), they will “inevitably” learn to use a password manager, which in turn will stop them from a whole range of poor password practices.
But in general I applaud Microsoft for setting some good guidelines. I particularly like the point about not forcing users to choose a new password periodically. I know someone who logs into a government site for work and is forced to choose a new password every 90 days. Well guess what? This person has gotten sloppy with the choice.