Advanced Microsoft Enhanced Mitigation Experience Toolkit (EMET) Tips
The Microsoft Enhanced Mitigation Experience Toolkit, short EMET, is an optional download for all supported client and server versions of Microsoft's Windows operating system that adds exploit mitigation to the system's defenses.
Basically, it has been designed to prevent attacks from being carried out successfully if they have breached system defenses such as antivirus solutions already.
EMET is easy to install and runs out of the box, but to get the most out of the program, you need to spend time getting to know it and configuring it.
This article provides you with tips on how to make the most out of EMET.
1. Protecting important processes
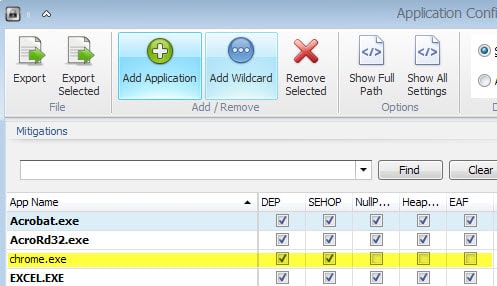
EMET protects core Microsoft and a handful of third-party processes only after installation. While that takes care of programs like Java, Adobe Acrobat, Internet Explorer or Excel, it won't protect programs that you have installed manually such as Firefox, Skype or Chrome.
While it is theoretically possible to add all your programs to EMET, you may want to consider adding only high-risk programs to the application instead.
High-risk programs? A short definition of a high-risk program is that it is either exploited regularly (e.g. Internet Explorer), capable of executing files downloaded from the Internet (web browser, email client), or stores valuable data for you (e.g. encryption software).
This would make Firefox, Chrome and Thunderbird high-value targets and Notepad, Minesweeper and Paint not.
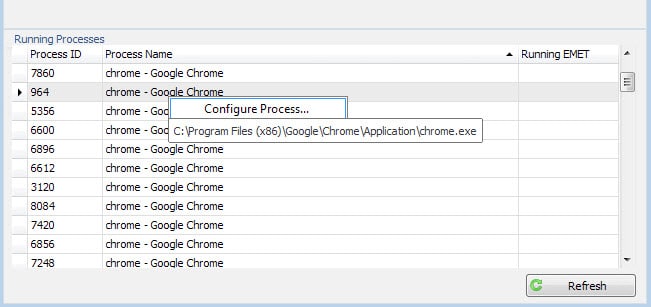
To add applications to EMET's protection list
- Open EMET on the system.
- You find a list of running processes in the interface. If the program that you want to protect is not running, start it on the PC.
- Right-click on its process afterwards and select "configure process" from the context menu.
- This adds the selected process to EMET's application list.
- Select okay afterwards to save the selection and restart the program you have just added to EMET.
Tip: It is highly suggested to test each application individually before you start to add more processes to EMET. A program may not be compatible with all exploit mitigation techniques that EMET offers.
2. Debugging misbehaving processes
The chance is rather high that you will encounter issues after adding programs to EMET. Some programs may refuse to start entirely while others may open and close immediately after they have been started.
This is usually the case when one or multiple mitigations are not compatible with the process. The main issue here is that you won't receive information which mitigation caused the problem.
Verify that there is a problem
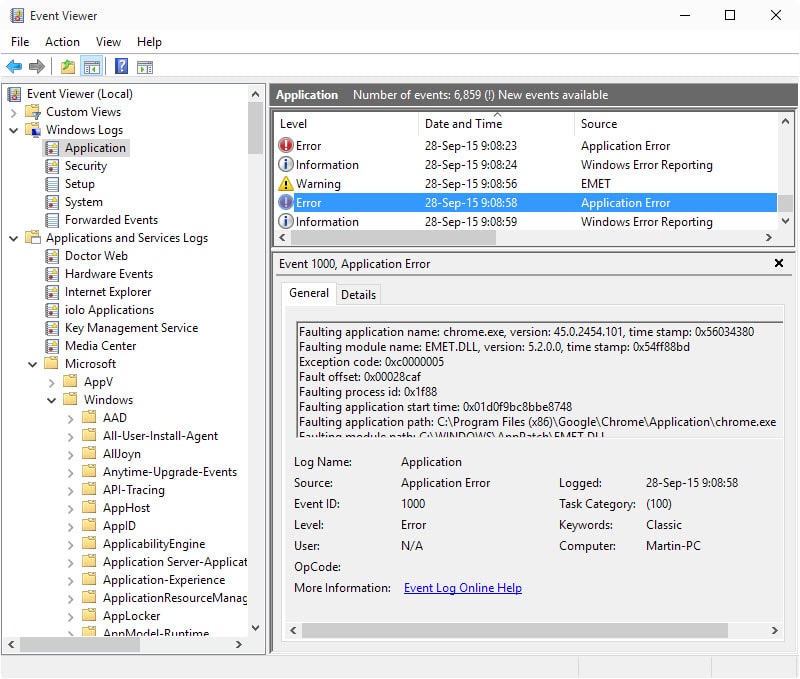
One of the easier ways to verify that something is not working right is to check for EMET entries in the Windows Event log.
- Tap on the Windows-key, type event viewer and hit enter.
- You find EMET entries under Event Viewer (local) > Windows Logs > Application.
I suggest you sort by Date and Time, and look for "Application Error" as the source. You should find EMET.DLL listed as the source of the issue under General when you select one of the log entries.
Obviously, you could also remove all protections for the application in EMET and run it again to see if it resolves the issue.
Correcting the issue
The only surefire way of enforcing compatibility with Microsoft EMET is trial and error. Open the protected applications listing again in EMET, turn off all protections, and start turning them on again one by one.
Try to run the program after each switch to see if it works. If it does, repeat the process by switching on the next mitigation in line until you come to one that prevents the program from starting up.
Disable that mitigation again and continue the process until you have enabled all mitigations that are compatible with the selected software.
Google Chrome for instance failed to start using the default mitigations selected for new processes. I discovered that the only mitigation the browser was not compatible with was EAF which I disabled as a consequence.
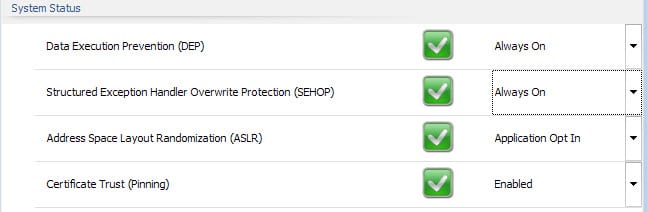
3. System-wide rules
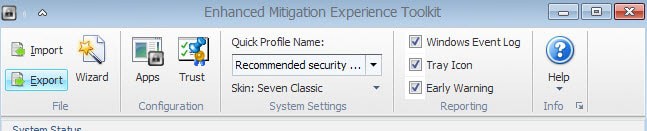
EMET ships with four system-wide rules that you can configure in the main interface. Certificate Pinning, Data Execution Prevention and Structured Exception Handler Overwrite Protection are enabled as system-wide rules while Address Space Layout Randomization is set to opt-in instead.
This means that you need to enable the rule for each application you want protected by it. You may change the status of these system wide rules, for instance by enforcing the opt-in rule system-wide as well.
This may however cause issues with programs running on the system. Since it is enforced for all programs when enabled, you may want to monitor the system closely and switch back to opt-in if you notice issues starting or running applications on the machine.
4. Rule importing and exporting
Configuring programs in EMET so that they are protected by the application takes a while because of the issues outlined above.
Good news is that you don't need to repeat the process on other PCs that you manage as you can use EMET's import and export feature for that.
Tip: EMET ships with a set of extra rules that users can add to the program. To access those select import in EMET and then one of the following:
- CertTrust - EMET default config of Certificate Trust Pinning for MS and 3rd party online services
- Popular Software - Enables protections for common software such as Internet Explorer, Microsoft Office, Windows Media Player, Adobe Acrobat Reader, Java, WinZip, VLC, RealPlayer, QuickTime, Opera
- Recommended Software - Enables protections for minimal recommended software such as Internet Explorer, Microsof Office, Adobe Acrobat Reader and Java
Option 3 is the default option that gets loaded automatically. You can add other popular programs to EMET automatically by importing the Popular Software rules.
Rule migration and policies
To export rules select the export button in EMET's main interface. Pick a name for the xml file in the save dialog and a location.
This set of rules can then be imported on other systems, or kept as a safeguard on the current machine.
Since rules are saved as XML files, you may edit them manually as well.
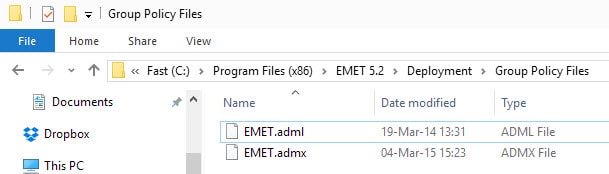
Administrators can deploy Group Policy directives on systems as well. The adml/admx files are part of the EMET installation and can be found under Deployment/Group Policy Files after installation.

















Although not updated through EMET 5.5 beta, this is useful info that may stop you from spinning your wheels when testing EMET 5.5 beta.
https://support.microsoft.com/en-us/kb/2909257
New EMET 5.5 Beta (includes Windows 10 Support now)
PDF:
http://download.microsoft.com/download/4/3/3/43364390-96B1-4820-9BAD-4A71F9A3221A/EMET%20User%20Guide.pdf
Announcement:
https://social.technet.microsoft.com/Forums/en-US/5cffd220-ec27-4778-b030-40aa88f840e8/emet-55-beta-supports-windows-10?forum=emet
Official link:
http://www.microsoft.com/en-us/download/details.aspx?id=49166
Changelog:
What’s new in Enhanced Mitigation Experience Toolkit 5.5 Beta?
– EMET 5.5 beta release includes new functionality and updates, such as:
– Windows 10 compatibility
– Full GPO support for mitigations and Cert pinning functionality
– EAF/EAF+ perf improvements
– Untrusted font mitigation for Windows 10
– Various bug fixes (UI)
Direct download link:
http://download.microsoft.com/download/0/C/B/0CB2E31A-1CBB-4AE7-B7F7-A96CF142652A/EMET%20Setup.msi
https://support.microsoft.com/en-us/kb/2458544 makes no mention of Windows 10, even though it was last reviewed after Windows 10 was generaly available.
https://social.technet.microsoft.com/Forums/security/en-US/1e70c72b-67b2-43c4-bd36-a0edd1857875/application-compatibility-issues?forum=emet mentions Windows 10 compatibility problems (see next to last entry as an example).
I used EMET 5.2 under Windows 7 and played with it quite a bit. I suggest not doing so under Windows 10.
> I can’t understand why, if EMET, works so well, Microsoft doesn’t offer it as an update, or include it in Windows. I suspect that compatibility issues might be the reason. The average person doesn’t have a clue that it exists.
Because it’s to unstable to use it, especially because people doesn’t want to ‘waste’ there time to try which software works with which configuration. And from what I know only a small range of people looking at the Microsoft Thread to watch which products are incompatible, in fact software also changes from time to time and with each update. To control this coast a lot of time.
In such a case a traditional AV is more efficient because you need to set it up once and run it in the background even if you update or install new software.
EMET was such a PITA that I ended up uninstalling it. Yeah, probably now have MS spyware embedded in my PC. Just like everyone else who runs MS Windows.
^ Not fair. Yes, EMET does require trial and error. This says more about the programs you’re trying to get to play nice with EMET than it does about EMET itself. For example, sloppy/clueless programming practices often make programs require DEP to be disabled for them. There’s no magical way for Microsoft/EMET to know beforehand how competent other programmers are and where they failed to apply due diligence. How could there be?
Do you think Microsoft should establish a central repository of workable settings for every Windows program in existence? Sure, and let’s allow every clueless person in the world to add their $0.00000000002, just to make it even more fun.
Using the windows event logs can make configuring EMET much easier. Often, the reason for an application’s termination (via EMET) is made apparent there.
As far as deinstallation goes, EMET is not a messy install at all. I’m not sure what “traceware” is.
Love it: “The only surefire way of enforcing compatibility with Microsoft EMET is trial and error.” “Trial and error” says something about the technological prowess of a program. “How do I do such and such with EMET?” “Hmmm . . . have you tried this or that? We really don’t know; it’s a ‘trial and error’ program we made for geeky fun. In reality, it doesn’t do anything but leave a bunch of traceware on your machine when attempting to uninstall it.”
…well, it’s wise to be a bit suspicious of Microsoft.
EMET seemed to work well, but would not completely uninstall normally after I tested it this year; its remains appeared suspicious, though could be deleted manually.
It does a lot of communicating with MS servers. What are the full privacy/security risks for users ?
Delivering an intrusive (?) EMET application as a Windows Update might be bad public relations.
I wasn’t able to make EMET work on my Windows 10 upgrade, I could never get internet Explorer working inside Edge. I finally removed it.
It’s nice program that adds another layer to system security :) It works with Malwarebytes Anti-Exploit
I can’t understand why, if EMET, works so well, Microsoft doesn’t offer it as an update, or include it in Windows. I suspect that compatibility issues might be the reason. The average person doesn’t have a clue that it exists.
I’d have to assume because it is too complicated for the average user. Although your suggestion has merit if you mean server editions and not end-user editions.
EMET comes with a pre-generated list, that’s the first thing I would ‘import’. It’s also important to mentioned that some software’s aren’t compatible (see microsoft discussion list for details and report). Also it’s worth to mention that if a pocess spwarns a second process e.g. nvvsvc.exe (for nVIdia driver) you don’t need to protect the sparning processes too, since EMET will also automatically protect the child processes. This is important because I saw a lot of people on the entire www that including all .exe dll’s from the windows/system32 or sysow64 folder which doesn’t need to be manually added.