You can block WebRTC from leaking your IP now in uBlock Origin
Ublock is without doubt a popular extension for Firefox and Chrome that blocks network requests and popups, and modifies DOM requests on sites you visit to block advertisement, malicious content and other -- often -- undesirable content on the web.
While there is some confusion involved when it comes to picking the right release, there is uBlock and uBlock Origin for instance, it is clear that the two extensions are not identical.
I prefer uBlock Origin as it gives per-site controls which uBlock does not anymore. It seems as well that development is progressing at a faster pace when it comes to new releases.
If you have installed the most recent developer build of uBlock Origin which was released a couple of hours ago, you may have noticed a new privacy feature that Gorhill, the lead developer of the project, added to the extension.
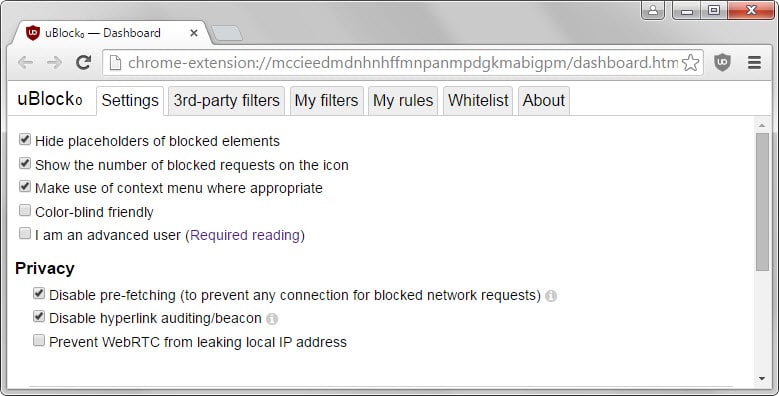
You find the following three privacy settings listed under the main settings tab in the uBlock Origin options (which you access with a right-click on the icon and the selection of options).
- Disable pre-fetching (to prevent any connection for blocked network requests).
- Disable hyperlink auditing/beacon.
- Prevent WebRTC from leaking local IP address
The new setting provides you with a toggle to enable or disable WebRTC from leaking your local IP address.
Please note that it won't prevent the leaking of your public IP address (which other Chrome extensions referenced here support).
Once you enable the preference in uBlock Origin you will notice that only the public IP is displayed on this test site.
The latest version is only available as a developer release. This means that it is not available yet on the Chrome and Firefox add-on stores. While you can install it, it is slightly more difficult if you are using a Chrome-based browsers.
- Download the Chromium zip package on the uBlock Origin releases page and extract it to a directory on your computer.
- Open chrome://extensions/ in the web browser and check the "developer mode" box at the top.
- Click on "load unpacked extension", browse to the directory you unpacked the extension to and select it.
- This runs the installation process to install uBlock Origin in Chrome.
Firefox users can install the xpi file directly in the browser. This may change for Stable and Beta users when version 40/41 of the web browser hits those channels due to the introduction of mandatory add-on signing.
It is unclear when the dev build will be pushed to the release channel.
Closing Words
The introduction of privacy-related settings and features in uBlock Origin make sense as they relate closely to the overall nature and purpose of the extension.





















It doesn’t work anymore in Google Chrome after version x which released in middle 2020. Though it still works in firefox.
Look at the red tags this is just a trick to get you to comment. They are in every country. Some work for Google, big phone & cell companies. I have their data list.
You can truly hide your IP address and securely encrypt your data on Macs (and possibly PC’s) by using these guidelines:
1.) Enable Google Chrome as your browser.
2.) Enable the WebRTC extension.
3.) Enable the WebRTC Leak Prevent extension (I have always successfully used both this and the WebRTC extensions simultaneously, but in theory that could leave your connection vulnerable at times.) For maximum security, when using the former, you may enable this option: Prevent WebRTC from using non-proxied UDP, as well as choosing “Disable non-proxied UDP” as the “IP handling policy”. But keep in mind that you will be drawing extra attention to yourself by blocking even the VPN’s IP address, so you may want to just use the default setting.
4.) Enable Hotspotshield’s free version (not the less effective extension, but the full software.) The encryption is 256-bit (military/bank grade.) You can still use the extension to unblock websites, but your true IP address will not be hidden. Contrary to popular legend, Hotspotshield does not log your activities.
4.) Alternatively, to block WebRTC you can disable JavaScript on Chrome, but that will block many online features like watching videos.
5.) Test IP blocking at these websites:
https://diafygi.github.io/webrtc-ips/
https://www.browserleaks.com/whois
https://www.browserleaks.com/webrtc
6.) If you are committing online felonies, you may already be on the radar of law enforcement authorities, so you may be under surveillance and, thus, no measures will protect your identity. Also, you can still be tracked down through your MAC address (your device’s unique serial number), which is (at least at first) contained in every IP packet, or via any of many other methods. My post only applies to law abiding citizens who legitimately want to protect their privacy.
CORRECTION:
For the most privacy and security with WebRTC Leak Prevent, at least according to my experimentation at browserleaks.com’s WebRTC Leak Test, enable (under “Advanced options”) “Prevent WebRTC from using non-proxied UDP” and set “IP handling policy” to “Use the default public interface only”.
That does not work on Chrome. Check it out with whoer.net and you will find out that your real Ip is beeing leaked.
So far, all chrome extensions to prevent WebRTC leak on Chrome DO NOT WORK
Can confirm – uBlock 1.0.0.1 does not disable WebRTC and WebRTC block extension does not do it either.
There is apparently no option for “Prevent webRTC from leaking local IP address” in the Opera browser extension, last updated 6. July 2015. Any reason for this?
Presumably, this Opera extension is legit.
https://addons.opera.com/en-gb/extensions/details/ublock/
We need a popular adbocker like this to also disable the facilities getting built in to firefox which facilitate data/usage mining by default; now that its obvious Firefox is going the adware/tracking route, and been openly stated this area will evolve.
My tips: To block WebRTC using Greasemonkey:
// ==UserScript==
// @name BlockWebRTC…….
// @namespace BlockWebRTC…
// @version 0.1
// @include *
// @run-at document-start
// ==/UserScript==
function NoWebRTC(e){return 1}window.RTCPeerConnection=NoWebRTC; window.webkitRTCPeerConnection=NoWebRTC; window.mozRTCPeerConnection=NoWebRTC;
I stopped reading at //@include *
Serious… Don’t you guys care about performance?
It will not affect anything, but you can modify this line to // @include http://* and https:// if you want, I personally don’t think * affect anything if it only run on HTML.
So, what did it do in Chrome? As far as I know this is just disable media.peer.connection in Firefox. But how in Chrome?
All this does is toggle “media.peerconnection.enabled” for you. That’s it. Big whoop.
This may be true for Firefox, but not for Chrome.
The significance of this is … to prevent prosecution (of P2P downloads say) where for instance a household of devices exist – so identity of endpoint cannot be established ?
If so does this affect need for VPN ?
(could authorities prove guilt in other ways?)
They go under the name Monorail. I have copies of the templates they use and how they hack in from contributer and one owner dannyb@goole, he describes how to call a home or cell, Plenty of video tapppings 148 names also. Some work for Google and other companies. These hackers cost me thousands and I am a single mother. My autistic daughter cannot even use her IPad, my 15 year old worked after school for a year to save for an iPhone and they have hacked it 2x, still on her computer for homework, had to take 2 bus to library for homework. I am calling the FBI on them. SHERRIFF calls himself security?????
Not only can they do it through WebRTC, fun way is through Flash: http://whoer.net/extended
With VPNs, it’ll show not only the Public IP address but ALL the private IP addresses (including the VPN’s)
Now there is a hack in chrome that will block it from seeing your Private IP address(es) but if you mistype it, it’ll corrupt your preferences for Chrome.
Found here:
https://support.zenmate.com/hc/en-us/articles/201259661-How-can-I-protect-myself-from-IP-leaks-caused-by-Flash-or-WebRTC-
“C:\Users\Your_Profile_Name_Here\AppData\Local\Google\Chrome\User Data\ (personally, I had to add User Data\Default\ )
Before you change something, please make a copy of that file and place it somewhere you will find it again. Just in case you want to undo this workaround in the near future.
Also, make sure that the Chrome browser is closed completely. Once this is done, open the file and scroll down until the bottom end or until you see the “variations_seed†tag. Finally, simply add the following line to the preference file:
,”webrtc”: {“multiple_routes_enabled”: false}
”
Using that Hack will stop it from seeing the Private but public is still visible. Slight compromise if you don’t want to use uBlock.
This feature is very nice, look at how they get our local IPs: https://github.com/diafygi/webrtc-ips/blob/master/index.html
Probably they can send our IP back to their server with Javascript again, that is harmful.
Jimbo, WebRTC can reveal your IP (local and public) even if you are using a VPN.