Quick Crypt creates self-expiring encrypted files
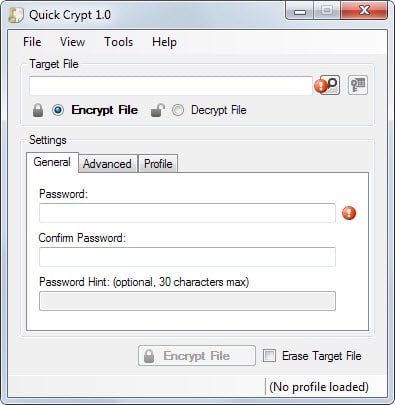
Quick Crypt looks on first glance just like many of the other file encryption tools for Windows. You can use it to encrypt files using 256-bit AES encryption, and also decrypt those files again at a later point in time.
It does however make available features that are not that common or available at all in other programs of its kind including an option to set expiration dates for encrypted files.
Note: Quick Crypt requires the Microsoft .NET Framework 4.5.
When you first start the program the main tab is displayed to you. Here you can select the file that you want to encrypt or decrypt, set a password, and add a password hint if you want. Files can be added via drag and drop, or the built-in file browser.
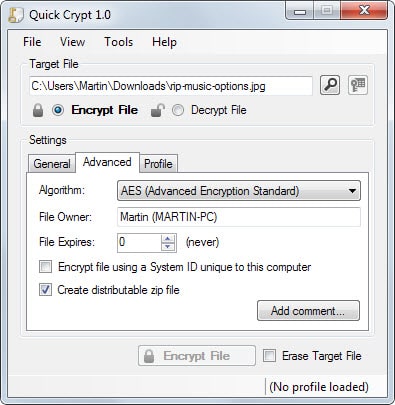
You can then hit the encrypt file button right away to start the process, or switch to the advanced tab first to make additional modifications first.
Here you find several interesting options:
- Encrypt file using a system ID unique to the PC. Attempts to decrypt the file on other computer systems will result in errors even if the correct password is entered.
- Set a file expiration date. The file cannot be decrypted anymore once the expiration date is reached.
- Create a distributable zip file. This adds the Quick Crypt program and the encrypted file to a zip file for easy distribution since Quick Crypt is required to decrypt an archive.
Both file expiration and unique ID systems worked well during tests. The program stops the decryption process if either the system ID does not match and the option has been set, or if the file has expired due to its expiration date.
You can save configurations as profiles so that you can load them again at a later point in time without having to make configuration changes in the program directly each time.
The program runs a file verification check automatically to make sure files have not been modified after they have been encrypted. There is also an option to securely erase the target file -- that is the file that you encrypt -- to remove it from the computer's hard drive in a way that it cannot be recovered anymore.
Verdict
Quick Crypt is a new encryption program that introduces several interesting features. It is new on the other hand and since there has not been any audit yet, you may not want to use it in a business environment or for important files yet because of that.



























If a send a file say Jpeg to any person on Facebook and want it that it should destroy with in a minute or 30 seconds of opening then would it happen? I am sending the file to the other person and want it to be destroyed within some time…
Hi
Is there a similar program for Mac? Can you recommend anything for storing files con memory drive with an expiration date??
thanks in advance
>Encrypt file using a system ID unique to the PC. Attempts to decrypt the file on other computer systems will result in errors even if the correct password is entered.
Tip to the unwary, don’t use this for files you can’t afford to lose because if your computer dies then so does any file encrypted with this option.
With all the mention of encryption lately, I wonder what high level security jobs all of the readers have that would make it a necessity to encrypt anything considered “top secret.” Or maybe this is one of those sites that appears to be a legitimate technology site, but, in reality, it exists to exploit the regime of German Chancellor Angela Merkel and her distaste for “economic espionage.” Or maybe there is some cryptic communication already occurring without readers knowing–every fourth letter is meaningless; therefore, to enable communication, I will need a program that auto deletes every fourth letter of the article! I think I’ll stick with the Navajo tongue. NizhónÃgo Nee Ado’ááł .
I think it has something to do with privacy more than security.
Or maybe one wishes to copy/synchronize a file to the Cloud without the file being visited on its journey and/or at its arrival, or maybe a computer is shared and one has his little secrets, or maybe…, or maybe … Privacy is a right, and it does not mean there is a confidential-top-secret-for-your-eyes-only information behind. Period.
How does it check the date? Via system clock? If so, then how can prevent a malicious attacker pegs the system clock to the file’s creation/modification date?
I was thinking the same thing (assuming Quick Crypt in blocked from the internet via firewall/rooter). I assume we keep a copy of the encypted file as a master copy. Any attempt to open the file, if the current system date > expiration date = zap. Set date back, restore test copy from master copy. Rinse and repeat.
However, and I used this once in some trial software I developed over 15 years ago. When opened, the current system date is harvested, and is stored in the container as the latest date, but only if it exceeds the date already stored there. If the current system date harvested is more than a day older (to allow for time zones) than the stored date, then clearly someone is trying to fiddle with system dates and get a work-around – continue but use the lastest date ever harvested as the current date. <<< not 100% foolproof, but the logic works.
As for Quick Crypt – I might try this expiry later to see what happens.
Okay I ran a quick test. You cannot just go back in time to decrypt an expired file. I encrypted a file using 1 day as the expiration timeframe. Changed the system date then to two days in the future and tried to extract. Did not work. I then set it back to today’s date, and I could not extract the file as well.
So, there is another barrier besides the system date that is being used by the program to determine the expiration date.
This is interesting. Besides the two innovative functions — file expiration and unique ID — I’m interested in the distributable zip file containing the encrypted file together with the Quick Crypt program. Thanks, Martin, for pointing this out, especially that on the developer’s page I found no information relevant to this feature. – How does this proceed?
– Does the end-user who receives such a file need to have NET Framework 4.5 on his system?
– Does the included Quick Crypt program unfold only for decrypting the included file or must it be installed by the receiver?
It seems to me — I’m complaining again — that developers provide less and less information, be it an application, software, script, whatever: have they lost their tongues and/or fingertips? If it weren’t for sites like gHacks more than a user would miss quality sometimes due to the simple fact that he cannot find in-for-ma-tion.
Tom, I can answer some of those questions.
1. Yes, the .Net Framework is required to run Quick Crypt.
2. No, a full version of the program is added to the zip file. It has a size of 123 Kilobyte.
3. No, it does not need to be installed, only extracted and run.
OK, Martin, thanks for the information.
Proceeds in the same way as AxCrypt except that it requires the destination user to have .net Framework 4.5 installed. Most users have the latter installed, but not everyone.
Nota : I understand .net Framework is required for Quick Crypt install, I was wondering if it was required as well for a destination user receiving a self-extracting Quick Crypt file …
The two innovative functions — file expiration and unique ID — make this app, nevertheless, worth being considered.
No haste here of .net Framework, simply I’m not fond of it and always prefer apps that don’t require it. It’s heavy.
I prefer AxCrypt