Java Update Addresses Critical Security Vulnerability
It feels like I'm patching computer systems all day long in the last two days. First the monthly Windows Update, then Adobe with its patches and now Oracle and Java. This is madness and unfortunately a necessary evil. Oracle has just released a security advisory that details a critical security vulnerability in the JDK and JRE 6 Update 23 and earlier for Windows, Solaris and Linux. Oracle has not released an update for the Java SDK or JRE but another Java based command line tool that fixes the security vulnerability.
The vulnerability is triggered when 2.2250738585072012e-308 is converted to a binary floating number. It can be exploited to allow unauthenticated network attacks which can "cause a hang or frequently repeatable crash (complete Denial of Service) of the Java Runtime Environment". Oracle notes that "Java based application and web servers are especially at risk from this vulnerability".
The Java SE Floating Point Updater Tool has been created to "address the hang that occurs when parsing strings like "2.2250738585072012e-308" to a binary floating point number". The file is offered for download at this page. It is best to unpack the file directly into the /bin/ directory of the Java installation since it is necessary to run a command from the command prompt that references that file.
Windows users need to open an elevated command prompt and switch to the directory of their Java installation. The directory is located in the program files directory, in the case of a 64-bit operating system in the program files (x86) directory. The full path on my Windows 7 64-bit test system is C:\Program Files (x86)\Java\jre6\bin.
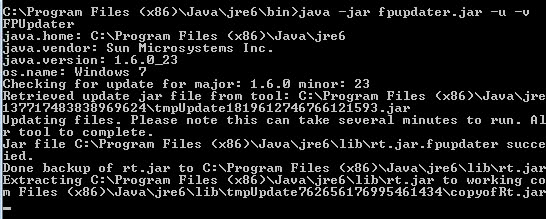
The command that needs to be entered is java -jar fpupdater.jar -u -v. The path of fpupdater.jar needs to be added if the file is not in the same directory as the java executable. The command assumes that the user is in the bin directory mentioned above. The path needs to be added to the command as well if that is not the case.
It can take up to two minutes before the patch is fully applied to the JRE or JDK. It is necessary to run the patch against any instance of JAVA on the system, for instance if the JDK with JRE and a standalone JRE are installed on the system.
The program should display that the patch was applied successfully in the end. Another indication are two files that are placed inside the lib folder by the application.
/lib/rt.jar.fpupdater Copy of rt.jar before the fix.
/lib/.fpupdater.log Zero-length file indicating that the update has taken
Users who have Java installed should patch the vulnerability as soon as possible. (thanks Dante for the tip, via)
Advertisement
















Please note the following from: http://www.oracle.com/technetwork/java/javase/fpupdater-tool-readme-305936.html
“The FPUpdater tool is not intended for use on systems managed through auto-update as this will disable future auto-updates. We recommend that you wait until the next Critical Patch Update (CPU) when you can update your installation by going to http://java.com/latest.”
I saw that but since it means leaving the system vulnerable I’d say the majority of users prefer running the tool.
I’ll be waiting for next JRE update, this patch deployment frightens me a bit, I admit.
You are authorized to laugh ;)