Microsoft Security Bulletin December 2010
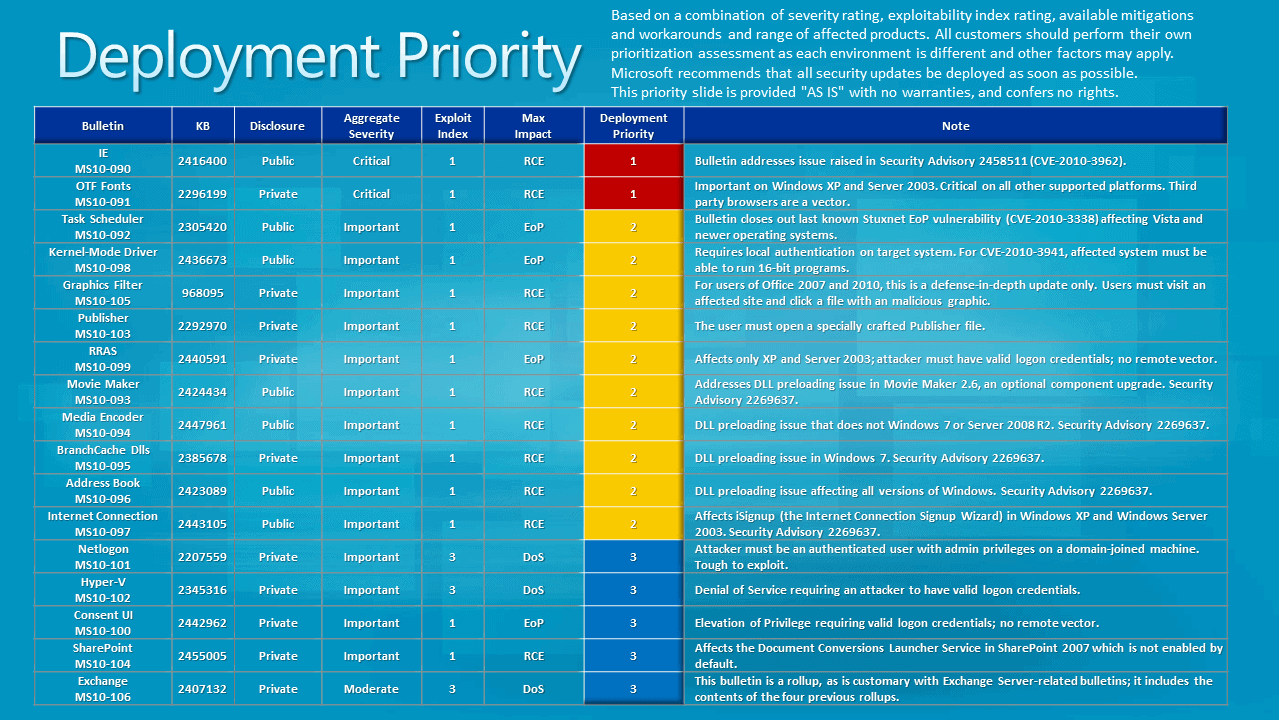
Microsoft has released the last set of planned security bulletins for the year 2010 yesterday. A total of 17 security bulletins have been released that patch vulnerabilities in Microsoft products like the Windows operating system, Microsoft Office or Internet Explorer.
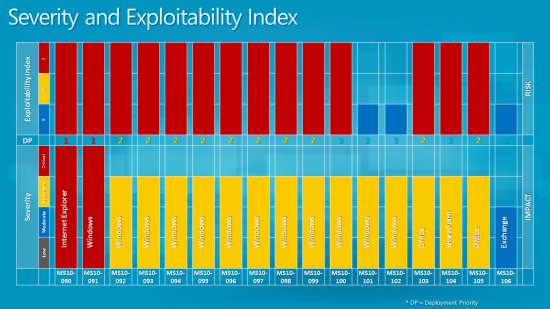
When we look at the severity rating of those vulnerabilities we notice that two of the bulletins have a maximum severity rating of critical while the remaining ones a rating of important with the exception of one that has been rated as moderate.
Maximum severity rating means that at least one Microsoft product is affect this way by the vulnerability. The critical vulnerability MS10-090 affects Internet Explorer 6 to Internet Explorer 8 and is critical on all Microsoft operating systems. Vulnerability MS10-091 on the other hand is critical on Windows Vista and Windows 7 but not on Windows XP, something that we do not see very often thanks to improved security of the two operating systems.
The updates are already available via Windows Update and the Microsoft Download Center.
- MS10-090 - Cumulative Security Update for Internet Explorer (2416400) - This security update resolves four privately reported vulnerabilities and three publicly disclosed vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-091 - Vulnerabilities in the OpenType Font (OTF) Driver Could Allow Remote Code Execution (2296199) - This security update resolves several privately reported vulnerabilities in the Windows Open Type Font (OTF) driver that could allow remote code execution. An attacker could host a specially crafted OpenType font on a network share. The affected control path is then triggered when the user navigates to the share in Windows Explorer, allowing the specially crafted font to take complete control over an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
- MS10-092 - Vulnerability in Task Scheduler Could Allow Elevation of Privilege (2305420) - This security update resolves a publicly disclosed vulnerability in Windows Task Scheduler. The vulnerability could allow elevation of privilege if an attacker logged on to an affected system and ran a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS10-093 - Vulnerability in Windows Movie Maker Could Allow Remote Code Execution (2424434) - This security update resolves a publicly disclosed vulnerability in Windows Movie Maker. The vulnerability could allow remote code execution if an attacker convinces a user to open a legitimate Windows Movie Maker file that is located in the same network directory as a specially crafted library file. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a document from this location that is then loaded by a vulnerable application.
- MS10-094 - Vulnerability in Windows Media Encoder Could Allow Remote Code Execution (2447961) - This security update resolves a publicly disclosed vulnerability in Windows Media Encoder. The vulnerability could allow remote code execution if an attacker convinces a user to open a legitimate Windows Media Profile (.prx) file that is located in the same network directory as a specially crafted library file. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a document from this location that is then loaded by a vulnerable application.
- MS10-095 - Vulnerability in Microsoft Windows Could Allow Remote Code Execution (2385678) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a file type such as .eml and .rss (Windows Live Mail) or .wpost (Microsoft Live Writer) located in the same network folder as a specially crafted library file. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a document from this location that is then loaded by a vulnerable application.
- MS10-096 - Vulnerability in Windows Address Book Could Allow Remote Code Execution (2423089) - This security update resolves a publicly disclosed vulnerability in Windows Address Book. The vulnerability could allow remote code execution if a user opens a Windows Address Book file located in the same network folder as a specially crafted library file. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a document from this location that is then loaded by a vulnerable application.
- MS10-097 - Insecure Library Loading in Internet Connection Signup Wizard Could Allow Remote Code Execution (2443105) - This security update resolves a publicly disclosed vulnerability in the Internet Connection Signup Wizard of Microsoft Windows. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. All supported editions of Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.The vulnerability could allow remote code execution if a user opens an .ins or .isp file located in the same network folder as a specially crafted library file. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a document from this location that is then loaded by a vulnerable application.
- MS10-098 - Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2436673) - This security update resolves one publicly disclosed vulnerability and several privately reported vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logged on locally and ran a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit these vulnerabilities. The vulnerabilities could not be exploited remotely or by anonymous users.
- MS10-099 - Vulnerability in Routing and Remote Access Could Allow Elevation of Privilege (2440591) - This security update addresses a privately reported vulnerability in the Routing and Remote Access NDProxy component of Microsoft Windows. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. All supported editions of Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS10-100 - Vulnerability in Consent User Interface Could Allow Elevation of Privilege (2442962) - This security update resolves a privately reported vulnerability in the Consent User Interface (UI). The vulnerability could allow elevation of privilege if an attacker runs a specially crafted application on an affected system. An attacker must have valid logon credentials and the SeImpersonatePrivilege and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS10-101 - Vulnerability in Windows Netlogon Service Could Allow Denial of Service (2207559) - This security update resolves a privately reported vulnerability in the Netlogon RPC Service on affected versions of Windows Server that are configured to serve as domain controllers. The vulnerability could allow denial of service if an attacker sends a specially crafted RPC packet to the Netlogon RPC Service interface on an affected system. An attacker requires administrator privileges on a machine that is joined to the same domain as the affected domain controller in order to exploit this vulnerability.
- MS10-102 - Vulnerability in Hyper-V Could Allow Denial of Service (2345316) - This security update resolves a privately reported vulnerability in Windows Server 2008 Hyper-V and Windows Server 2008 R2 Hyper-V. The vulnerability could allow denial of service if a specially crafted packet is sent to the VMBus by an authenticated user in one of the guest virtual machines hosted by the Hyper-V server. An attacker must have valid logon credentials and be able to send specially crafted content from a guest virtual machine to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS10-103 - Vulnerabilities in Microsoft Publisher Could Allow Remote Code Execution (2292970) - This security update resolves five privately reported vulnerabilities in Microsoft Publisher that could allow remote code execution if a user opens a specially crafted Publisher file. An attacker who successfully exploited any of these vulnerabilities could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-104 - Vulnerability in Microsoft SharePoint Could Allow Remote Code Execution (2455005) - This security update resolves a privately reported vulnerability in Microsoft SharePoint. The vulnerability could allow remote code execution in the security context of a guest user if an attacker sent a specially crafted SOAP request to the Document Conversions Launcher Service in a SharePoint server environment that is using the Document Conversions Load Balancer Service. By default, the Document Conversions Load Balancer Service and Document Conversions Launcher Service are not enabled in Microsoft Office SharePoint Server 2007.
- MS10-105 - Vulnerabilities in Microsoft Office Graphics Filters Could Allow for Remote Code Execution (968095) - This security update resolves seven privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user viewed a specially crafted image file using Microsoft Office. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-106 - Vulnerability in Microsoft Exchange Server Could Allow Denial of Service (2407132) - This security update resolves a privately reported vulnerability in Microsoft Exchange Server. The vulnerability could allow denial of service if an authenticated attacker sent a specially crafted network message to a computer running the Exchange service. Firewall best practices and standard default firewall configurations can help protect networks from attacks that originate outside the enterprise perimeter. Best practices recommend that systems that are connected to the Internet have a minimal number of ports exposed.
Additional information are available at the security bulletin summary and the Microsoft Security Response Center.
Advertisement

















Make sure to also check out the monthly security update videos on TechNet Edge: http://bit.ly/ec8CFc
Thanks again Martin for this fairy explicit (great those pictures) Microsoft update notification. Over the decennium every month i stay astound how much updates are needed.