Microsoft Releases September Security Patches
Microsoft has released this month's security patches for their operating systems and applications.
The patches and updates are already available via Windows Update and Microsoft Download, and it is recommended to update the operating system as soon as possible to protect it from exploits targeting those vulnerabilities.
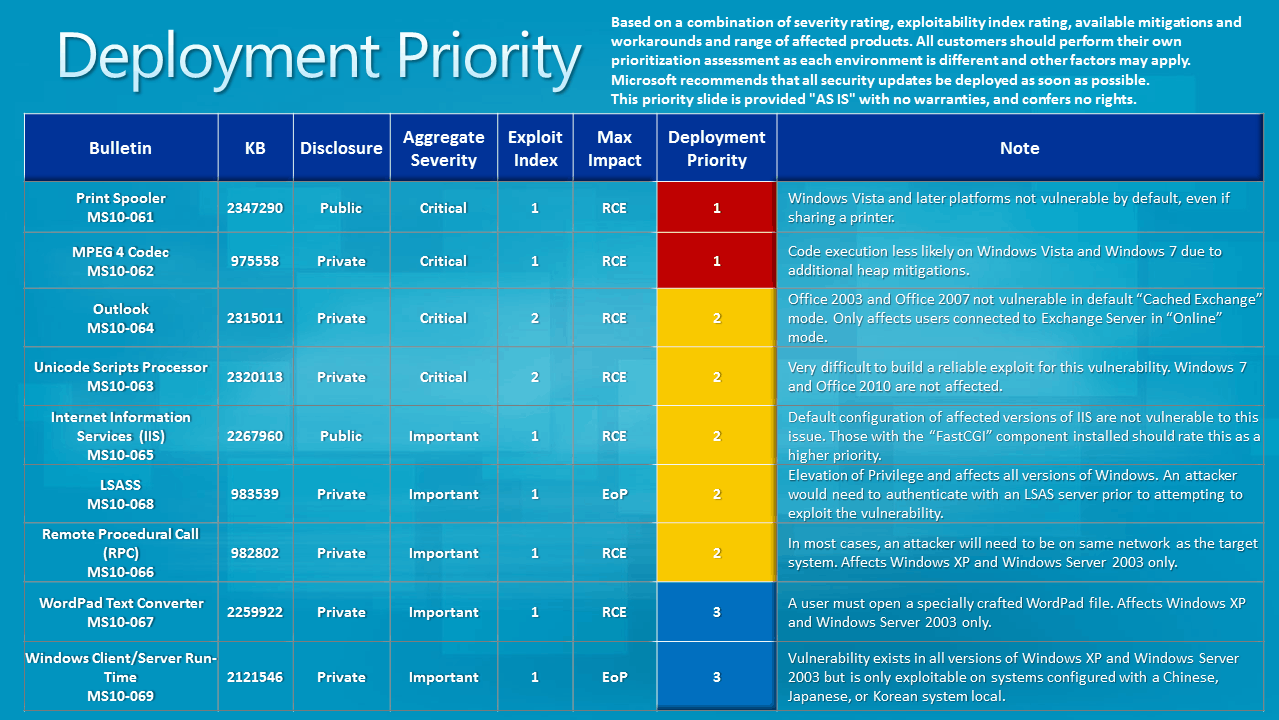
A total of nine bulletins have been released by Microsoft of which four have received a maximum vulnerability impact rating of critical, the highest possible rating.
As usual, not all operating systems and applications are affected with the same severity. Microsoft's latest desktop operating system Windows 7 for instance is either not affected by the critical vulnerabilities, or with a lower severity of important.

Below are the vulnerability summaries for all nine bulletins that have been released by Microsoft in September 2010:
- MS10-061 - Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - This security update resolves a publicly disclosed vulnerability in the Print Spooler service. The vulnerability could allow remote code execution if an attacker sends a specially crafted print request to a vulnerable system that has a print spooler interface exposed over RPC. By default, printers are not shared on any currently supported Windows operating system.
- MS10-062 - Vulnerability in MPEG-4 Codec Could Allow Remote Code Execution (975558) - This security update resolves a privately reported vulnerability in MPEG-4 codec. The vulnerability could allow remote code execution if a user opens a specially crafted media file or receives specially crafted streaming content from a Web site or any application that delivers Web content. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-063 - Vulnerability in Unicode Scripts Processor Could Allow Remote Code Execution (2320113) - This security update resolves a privately reported vulnerability in the Unicode Scripts Processor. The vulnerability could allow remote code execution if a user viewed a specially crafted document or Web page with an application that supports embedded OpenType fonts. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-064 - Vulnerability in Microsoft Outlook Could Allow Remote Code Execution (2315011) - This security update resolves a privately reported vulnerability. The vulnerability could allow remote code execution if a user opened or previewed a specially crafted e-mail message using an affected version of Microsoft Outlook that is connected to an Exchange server with Online Mode. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-065 - Vulnerabilities in Microsoft Internet Information Services (IIS) Could Allow Remote Code Execution (2267960) - This security update resolves two privately reported vulnerabilities and one publicly disclosed vulnerability in Internet Information Services (IIS). The most severe of these vulnerabilities could allow remote code execution if a client sends a specially crafted HTTP request to the server. An attacker who successfully exploited this vulnerability could take complete control of an affected system.
- MS10-066 - Vulnerability in Remote Procedure Call Could Allow Remote Code Execution (982802) - This security update resolves a privately reported vulnerability in Microsoft Windows. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. All supported editions of Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.The vulnerability could allow remote code execution if an attacker sent a specially crafted RPC response to a client-initiated RPC request. An attacker who successfully exploited this vulnerability could execute arbitrary code and take complete control of an affected system. An attacker must convince the user to initiate an RPC connection to a malicious server under the attacker's control. An attacker could not remotely exploit this vulnerability without user interaction.
- MS10-067 - Vulnerability in WordPad Text Converters Could Allow Remote Code Execution (2259922) - This security update resolves a privately reported vulnerability in Microsoft Windows. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. All supported editions of Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.The vulnerability could allow remote code execution if a user opened a specially crafted file using WordPad. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-068 - Vulnerability in Local Security Authority Subsystem Service Could Allow Elevation of Privilege (983539) - This security update resolves a privately reported vulnerability in Active Directory, Active Directory Application Mode (ADAM), and Active Directory Lightweight Directory Service (AD LDS). The vulnerability could allow elevation of privilege if an authenticated attacker sent specially crafted Lightweight Directory Access Protocol (LDAP) messages to a listening LSASS server. In order to successfully exploit this vulnerability, an attacker must have a member account within the target Windows domain. However, the attacker does not need to have a workstation joined to the Windows domain.
- MS10-069 - Vulnerability in Windows Client/Server Runtime Subsystem Could Allow Elevation of Privilege (2121546) - This security update resolves a privately reported vulnerability in Microsoft Windows. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. All supported editions of Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.The vulnerability could allow elevation of privilege if an attacker logged on to an affected system that is configured with a Chinese, Japanese, or Korean system locale. An attacker who successfully exploited this vulnerability could then install programs; view, change, or delete data; or create new accounts with full user rights.
Microsoft's Jerry Bryant has posted graphs for the deployment priority and severity exportability index in a blog post.

Happy patching everyone.
Advertisement
















I can’t access one of my two user profiles after these patches rebooted my system. I haven’t had time yet to roll back the patches one by one until it’s resolved. Anyone else having these problems?
No, I have not experienced that. Which OS are you using? If I were you, I would thoroughly scan my system with several security programs to make sure that no rootkit or other malware is causing this.
Thanks again Martin i am writhing to you like every month for this fairy elaborated explanation of this month path Microsoft day. Ferry handy indeed this detailed information and with the pictures it becomes even more easy to understand.
I think that Microsoft has secretly “fixed” some DLL Injection problems as well as on myIBM Thinkpad + Win XP SP3 the update has broken 2 Thinkpad applications TP4SERV (trackpoint application) and TPKmapAP (keyboard configuration). In both cases a DLL file has vanished.
Thanks for the detailed info Martin, I’m using your MS patching articles at work on a monthly basis as I’m responsible for the release management (including patches), which includes monthly communication on our intranet for 3000 employees. So thanks for these summaries, they are really useful !
You are welcome. I always find it handy to have an overview at hand as well. Great that I’m not the only one ;)