Microsoft Security Updates June 2010
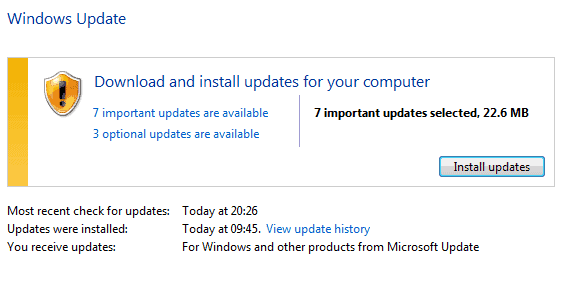
Microsoft has released security updates for their operating systems and applications. The June 2010 patch day consists of 10 security bulletins that fix a total of 34 30 different security vulnerabilities.
The updates are already available via Windows Update but can also be downloaded from the Microsoft website in case they need to be deployed on computer systems without Internet connection.
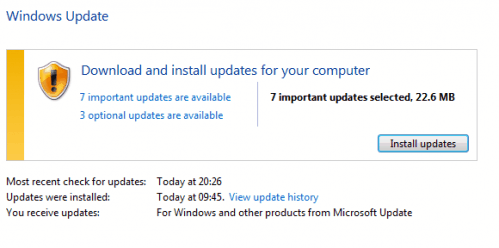
The severity rating differs depending on the operating system and software version installed. Three security bulletins have a maximum security rating of critical, the most severe one, while the remaining seven are all rated as important.
Vulnerabilities affect various Windows operating systems from Windows 2000 to Windows 7, Microsoft Office, Internet Explorer, Microsoft Server and the Microsoft .net Framework.
- MS10-033 - Vulnerabilities in Media Decompression Could Allow Remote Code Execution (979902) - This security update resolves two privately reported vulnerabilities in Microsoft Windows. These vulnerabilities could allow remote code execution if a user opens a specially crafted media file or receives specially crafted streaming content from a Web site or any application that delivers Web content. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-034 - Cumulative Security Update of ActiveX Kill Bits (980195) - This security update addresses two privately reported vulnerabilities for Microsoft software. This security update is rated Critical for all supported editions of Microsoft Windows 2000, Windows XP, Windows Vista, and Windows 7, and Moderate for all supported editions of Windows Server 2003, Windows Server2008, and Windows Server 2008 R2.The vulnerabilities could allow remote code execution if a user views a specially crafted Web page that instantiates a specific ActiveX control with Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. This update also includes kill bits for four third-party ActiveX controls.
- MS10-035 - Cumulative Security Update for Internet Explorer (982381) - This security update resolves five privately reported vulnerabilities and one publicly disclosed vulnerability in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-032 - Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (979559) -
This security update resolves two publicly disclosed vulnerabilities and one privately reported vulnerability in the Windows kernel-mode drivers. The vulnerabilities could allow elevation of privilege if a user views content rendered in a specially crafted TrueType font. - MS10-036 - Vulnerability in COM Validation in Microsoft Office Could Allow Remote Code Execution (983235) - This security update resolves a privately reported vulnerability in COM validation in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Excel, Word, Visio, Publisher, or PowerPoint file with an affected version of Microsoft Office. The vulnerability cannot be exploited automatically through e-mail. For an attack to be successful a user must open an attachment that is sent in an e-mail message.
- MS10-037 - Vulnerability in the OpenType Compact Font Format (CFF) Driver Could Allow Elevation of Privilege (980218) - This security update resolves a privately reported vulnerability in the Windows OpenType Compact Font Format (CFF) driver. The vulnerability could allow elevation of privilege if a user views content rendered in a specially crafted CFF font. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS10-038 - Vulnerabilities in Microsoft Office Excel Could Allow Remote Code Execution (2027452) - This security update resolves fourteen privately reported vulnerabilities in Microsoft Office. The more severe vulnerabilities could allow remote code execution if a user opens a specially crafted Excel file. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS10-039 - Vulnerabilities in Microsoft SharePoint Could Allow Elevation of Privilege (2028554) - This security update resolves one publicly disclosed and two privately reported vulnerabilities in Microsoft SharePoint. The most severe vulnerability could allow elevation of privilege if an attacker convinced a user of a targeted SharePoint site to click on a specially crafted link.
- MS10-040 - Vulnerability in Internet Information Services Could Allow Remote Code Execution (982666) - This security update resolves a privately reported vulnerability in Internet Information Services (IIS). The vulnerability could allow remote code execution if a user received a specially crafted HTTP request. An attacker who successfully exploited this vulnerability could take complete control of an affected system.
- MS10-041 - Vulnerability in Microsoft .NET Framework Could Allow Tampering (981343) - This security update resolves a publicly disclosed vulnerability in Microsoft .NET Framework. The vulnerability could allow data tampering in signed XML content without being detected. In custom applications, the security impact depends on how the signed content is used in the specific application. Scenarios in which signed XML messages are transmitted over a secure channel (such as SSL) are not affected by this vulnerability.
It is advised to install the security patches immediately to protect the PC from exploits that are targeting unpatched computer systems. Additional information are provided by the Security Research & Defense team which offers additional information that are helpful for system administrators and advanced users.
Lastly there is the security bulletin overview which lists all relevant information.
Advertisement

















Again thanks a million for this fairy handy explanation
Thanks for this. I never use automatic updates. Prefer to do it manually.