What Is paypal.112.2o7.net
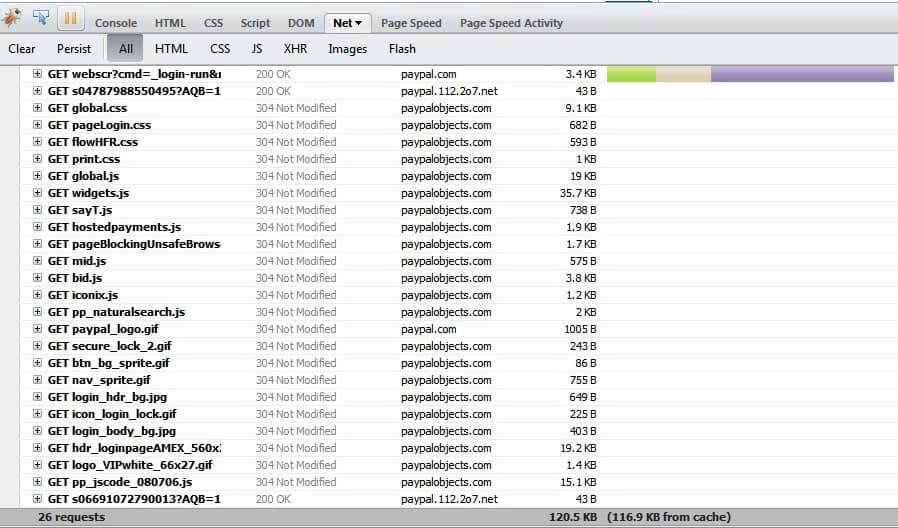
If you are a very observant - or cautious - PayPal user you may have noticed that several connection requests are made whenever you connect to the main PayPal website that you may not link to PayPal necessarily.
Some of the requests are made to third-party domains instead of paypal.com which you would not necessarily expect from a financial service.
This can be extremely worrying to users considering that malicious software and attackers also use these kinds of connections for their evil doings.
If you analyze the connections that PayPal makes you notice that the site makes two connections to load objects from the domain paypal.112.2o7.net.
What Is paypal.112.2o7.net
This looks on first glance like one of those phishing websites that add the name of the service that they attack to the url to make users believe that they are on the right website.
The two elements are the smallest in size (both are 43 Bytes) but seem to take the longest to transfer.
The very long url of these requests seems to transfer data about the computer system. It contains the screen resolution and browser plugins among other data which might be even more cause for concern.
If you open paypal.112.2o7.net directly you are greeted with a page that is more or less blank.
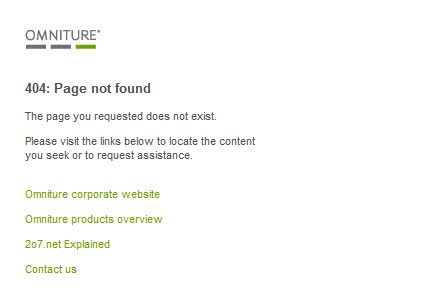
Not found does not sound good as well. Omniture on the other hand will give many webmasters a clue. It is a service that analyses traffic and it seems that PayPal is one of the company's customers.
This has been confirmed by a press release on the Omniture website which states that PayPal is indeed one of the company's customers. Omniture is part of Adobe Systems.
The way the data is handled, especially the cryptic url paypal.112.2o7.net can cause concern by users who don't know about Omniture or discover the connection for the first time.
PayPal should consider changing that url so that the request will come from a PayPal server and not that url.
Update 2: PayPal.com connects to different third-party servers now. It seems to have dropped connections to paypal.112.2o7.net completely. It appears that PayPal switched to Google Analytics for web stats instead.
Connections may also be established to secure.adnxs.com, paypal.d1.sc.omtrdc.net, and paypalobjects.com.
Check for third-party Connections
You can check the connections that PayPal -- and any other site for that matter -- make in the following way:
In your browser of choice, tap on the F12 key to display the Developer Tools. Locate the network tab in the interface, and load the PayPal page. The browser lists all connections made during page load time.
Simply go through them to discover all third-party connections made.


















Adobe now owns Omniture Marketing out of Utah… Adobe SiteCatalyst
I picked it out when using yp.com(Yellow Pages)
If your business fake obfuscates IP like that, it tells me something about your failed mindset.
[https://en.wikipedia.org/wiki/Omniture]
Reference:
Name: paypal.112.2o7.net
IP: 66.235.138.194, 66.235.139.19, 192.243.250.88, 66.235.138.193,
66.235.139.18, 66.235.139.206, 66.235.138.195, 192.243.250.72,
66.235.139.17, 66.235.139.207, 66.235.139.205
Domain: 2o7.net
Registrar: CSC CORPORATE DOMAINS, INC.
Registry Registrant ID:
Registrant Name: Domain Administrator
Registrant Organization: Adobe Systems Incorporated
Registrant Street: 345 Park Avenue
Registrant City: San Jose
Registrant State/Province: CA
Registrant Postal Code: 95110
Registrant Country: US
Apparently paypal is not the only site concerned : I’ve noticed the address oracle.112.2o7.net appearing quickly in Firefox status bar while connecting to Oracle support website
Ironically: Ghacks (who host this blog) are apparently using kontera.com for their analytics! I refused to accept the kontera cookies, of course! I have strong feelings about experimental ethics and privacy. It’s generally accepted, in modern scientific practice, that the informed consent of the subject is required for any experimentation. If an experiment might cause harm to the subject (e.g. an identity theft in this instance) then it is generally considered unethical to run the experiment unless all reasonable mitigations have been taken to minimise the harm, and unless there’s some counterbalancing “good” that will accrue to the class of fully-informed, consenting subjects.
I found this blog after I got annoyed with repeated requests, from a Wiley InterScience website, to accept a cookie from 112.2o7.net. At that time I was retrieving an article from Wiley InterScience. Librarians generally abide by a professional code of ethics, e.g. in the ALA: “We protect each library user’s right to privacy and confidentiality with respect to information sought or received and resources consulted, borrowed, acquired or transmitted.”
The usual argument in favour of tracking-cookies is that they don’t contain any personally-identifiable information. This may well be a sufficient legal defense in jurisdictions with weak or non-existent privacy laws, however it doesn’t take too many bits of “npn-personally identifiable” information about a person’s activities, interests, IP addresses, etc to get a pretty good “fix” on who they are… should you be interested in identifying someone. So… lusers must rely on the ethics of the market researchers themselves, unless they’re lucky/wealthy enough to have access to a legal recourse against the marketing research firm, or unless they appeal to the “court of public opinion”.
http://uneasysilence.com/archive/2008/01/12827/ is an amusing blog entry describing Adobe’s response to a similar concern about 112.2o7.net, a couple of years ago. Amusingly (I’m really not paranoid about this stuff — even though it *is* rather a worry) Adobe purchased Omniture a year later. See http://www.omniture.com/en/privacy/2o7.
I use PC Tools for my AntiVirus/Spyware.
It pops up to the 112.2o7.net and I hit Perm-Block.
End of story.
I agree, they should remove objectspaypal.com and 2o7.net
Had to google it out,
On my Last Post, its “Adblock Plus” a Firefox Plugin.
Internet Explorer 8 doesnt have the same problem, it seems like IE8 is filtering it automatic.
(Sorry for my bad english :O )
~211^
hey brother can some one tel me which software is this please
http://cdn.ghacks.net/wp-content/uploads/2010/02/paypal1-500×381.jpg
That is the firefox add-on firebug
to block paypal.112.2o7.net, u can use this filter:
|https://paypal.112.2o7.net/*
since i added this filter, there is no upcoming phishing warning from AntiVir.
If u turned Javascript off then its loaded as Gif-Image.
(Sorry for my bad english :O )
~211^
Also it isn’t that hard to notice since this considerably slows the transaction down… it took me like 5mn … while the status bar showed “transferrin’ data from paypal.112.2o7.net” … which made me look & find this good explanation u hav here.
Not being an informatic pro, i wonder what “analytics” this Omniture company collects about me…
What tool is required too analyse a website like that Martin?
You can for instance use Firebug which is what I have used. It is mainly used for web development but excellent for this purpose as well as it shows all connections and elements that are loaded by the website.
You should also notice that the script is embedded into another script. Bypassing any protection you have against it, like adblock. Sneaky sneaky. There is no legit reason for that element to be there. It doesn’t enhance privacy or functionality. Avoid ebay-Paypal. They are not a trustworthy company.
If I see a URL like that I would think phishing definitely and would cancel the site immediately.
Is Paypal really this STUPID?
Good eye!
First off, this is a lack of innovation on PayPal’s part to write their own analytics… Pretty sad if you ask me.. sombody’s god knows they have enough money.
And then to integrate with the 3rd party vendor in this manor (sending end-user to initiate the tracking code…), is amateur at best…
tisk tisk pay pal.
They aren’t getting things secured.
Think about Omniture get down by someone and they replace the scripts called by Paypal’s server with anything else :)
What would happen?