Malwarebytes Hijack.Securityrun hits explained
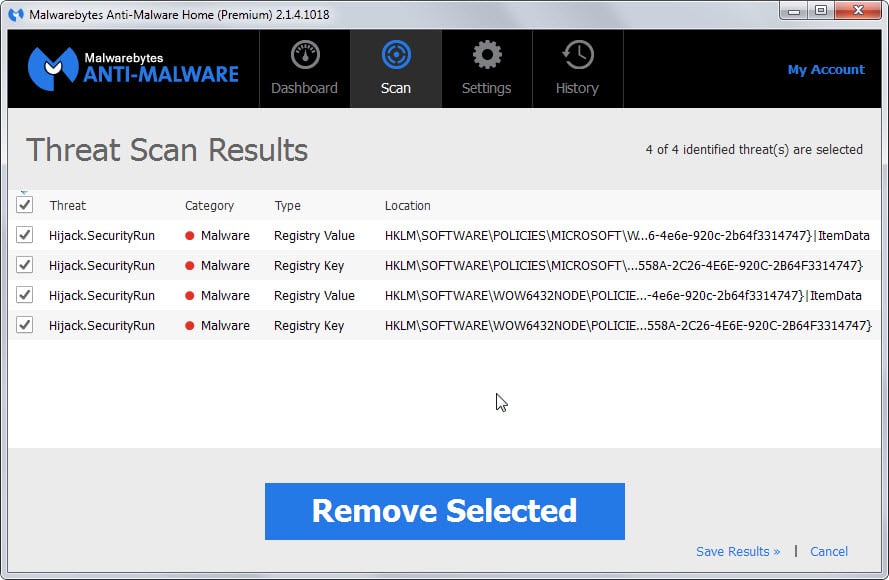
When I ran the usual Malwarebytes Anti-Malware Pro scan today I noticed that the program detected a set of threats it called Hijack.Securityrun.
The threats it detected during the scan were rated as high and malware, and pointed all to the Windows Registry. A quick search for the used threat descriptor Hijack.Securityrun would only return one result on a support forum where users of the software reported the same issue in the past couple of days.
First problem that you will experience is that you cannot display the full Registry path in Malwarebytes itself because the interface is not flexible enough to display multiple lines if one line is not enough to display the whole string.
That's a usability issue that you can overcome by selecting save results in the interface to export the data to a text file on your local system.
That text file displays the full string so that you know where you find it in the Registry.
The two strings found on the system were the following ones:
Hijack.SecurityRun, HKLM\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SAFER\CODEIDENTIFIERS\0\PATHS\{3A25558A-2C26-4E6E-920C-2B64F3314747}, , [76d151fa63275ed8e442a7a722e31de3],
Hijack.SecurityRun, HKLM\SOFTWARE\WOW6432NODE\POLICIES\MICROSOFT\WINDOWS\SAFER\CODEIDENTIFIERS\0\PATHS\{3A25558A-2C26-4E6E-920C-2B64F3314747}, , [e3643615fc8e999dac7a1c32a85d45bb],Hijack.SecurityRun, HKLM\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SAFER\CODEIDENTIFIERS\0\PATHS\{3a25558a-2c26-4e6e-920c-2b64f3314747}|ItemData, C:\Program Files (x86)\Avira\AntiVir Desktop\avnotify.exe, , [76d151fa63275ed8e442a7a722e31de3]
Hijack.SecurityRun, HKLM\SOFTWARE\WOW6432NODE\POLICIES\MICROSOFT\WINDOWS\SAFER\CODEIDENTIFIERS\0\PATHS\{3a25558a-2c26-4e6e-920c-2b64f3314747}|ItemData, C:\Program Files (x86)\Avira\AntiVir Desktop\avnotify.exe, , [e3643615fc8e999dac7a1c32a85d45bb]
The second string lists Avira's avnotify.exe program while the first does not provide any information what it is about.
The program suggests to remove the selected entries and classifies them as malware.
But what are they?
If you worked with software restrictions on Windows before, you may know that it is possible to author software restriction policies using the Group Policy Editor or the Windows Registry directly.
You find detailed information about that on Microsoft's Technet.
The entries that Malwarebytes found are software restrictions that someone or a program have added to the system. They can be malicious in nature as they may prevent security software or other important software from running on the system.
A malicious file could use this for example to prevent the antivirus solution to run properly on the system or notify the user about the threat.
Each rule has a security level associated with it which determines its rights on the system.
- Disallowed blocks the program from execution on the system regardless of the rights of the user account trying to run the application.
- Basic User allows the program to be executed with basic user privileges only but not with elevated privileges.
- Unrestricted will run the program with the same rights as the user executing the program (which can be with administrative privileges)
What you should do
The course of action depends on whether you have set those restrictions or not. If you are not the system administrator, an admin may have set them as well.
If you are the only user on the system and have not set them, you may want to consider removing them from the system.
If you are using Malwarebytes, you could have them quarantined which provides you with an option to restore the rules should the need arise.
You can use the Group Policy Editor or the Registry directly as well to remove those entries.
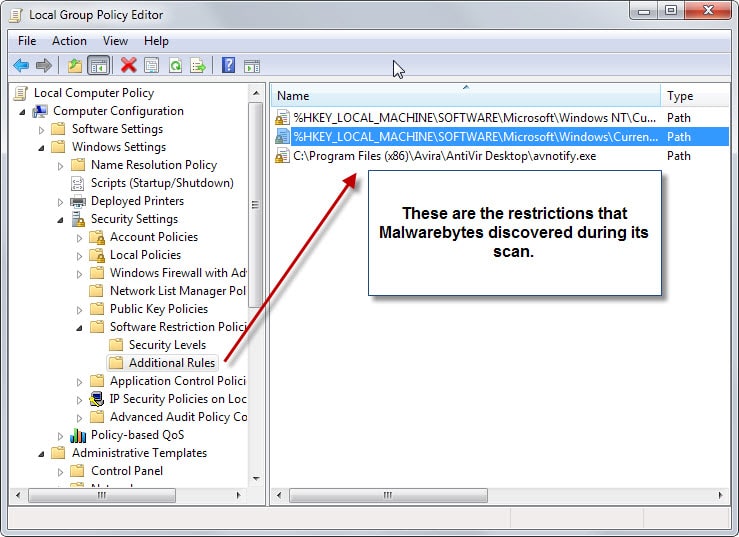
In the Group Policy Editor, you find them under Local Computer Policy > Windows Settings > Security Settings > Software Restriction Policies > Additional Rules.
To remove an entry select it and hit the delete key on the keyboard. Alternatively, right-click on a rule and select delete from the context menu.


















MBAM just found similar entries for me, which also were for disabling the avira popup!
I guess they just added this to their signatures.
@Nebulus
Your first response to me did not mention anything specific about those entries. I ask specific questions, you answered with generalities. You never hinted as to the particular origin of those entries, their function, their safety, etc. Indeed, re-read your response and tell me if it does not apply to any other registry entry. All registry entries are created by an administrative action (including initial installation) or program (malicious or not). See what I mean? No specificity, only generality.
I’ll expand on Martin’s excellent explanation by saying that security programs such as AVs and MBAM are unable to discern between malicious intent and benign intent so they tend to err on the side of safety and flag anything with the potential to be used for malicious purposes.
That’s why some of NirSoft’s freeware, such as password extraction tools, are being flagged. The security program has no way of knowing if it’s the user looking for his or her own passwords or some third party with evil intent, so it flags the potential.
Similarly, software restrictions can be utilized for both malicious and benign purposes. MBAM has no way of knowing which is which so flags the potential.
As Martin said; in these cases it’s up to the user to make the final determination.
Also a reminder, those of us running Windows 7 Home Premium edition do not have access to Local Group Policy Editors, some Advanced Admin privileges, and definitely no remote access which is disabled by default. Only the Pro, Enterprise and Ultimate editions have those available to them. Though we can download and install “gpedt.msc” which will unlock and enable access to the Local Group Policy Editor.
http://www.askvg.com/how-to-enable-group-policy-editor-gpedit-msc-in-windows-7-home-premium-home-basic-and-starter-editions/
Martin, your gpedit screenshot doesn’t show the column “Security Level”. I assume it shows Disallowed?
Because Disallowed rules are stored under
CODEIDENTIFIERS\0\PATHSand are known to be added by malware to block security programs from running.I use Software Restriction Policies myself and have no problem with Malwarebytes. I have Disallowed set as the default security level. Then in Addition Rules I have a few entries as Unrestricted. The first two are the same as yours I assume: the Windows and Program files folder. These rules are stored under
CODEIDENTIFIERS\0\PATHS.You can run this in a command prompt to see all entries for SRP, if you have any
0\PATHS:reg query HKLM\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SAFER\CODEIDENTIFIERS /s
Roomi they are both set to unrestricted.
So, now I have a question about this.
For users who are long-time users of Nir Sofer’s wonderful programs and utilities (NirSoft), we have become accustomed to seeing “False Positive” warnings when trying to run some of his programs. I have had Malwarebytes, SuperAntispyware and MSE all quarrantine some of his programs at various times — and I believe he even addresses the issue on his website.
So – What is the difference between the normal “False Positive” we all experience from time to time – and this “Hijack.Securityrun” – which seems a lot more ominous ? Any further explanation would be greatly appreciated.
The issue here is that you cannot determine — usually — why the Registry key exists. It could have been added by an admin for instance. Malwarebytes does not know that and it is up to the user to determine whether the keys have been created with malicious intent or not.
If you are the sole user of the computer and you find keys like this, you may want to quarantine them and see what happens. It won’t hurt usually if you have not set them as it just changes execution rights of the programs if you do.
The main difference between the two “false positive” findings is that one is software, the other is a Registry key. The former reveals immediately what has been blocked while the latter may require more research to find out about it.
Thank you very much Martin for that clear explanation. I am the sole user of my computer and probably do not receive more than three or four “warnings” in a year from my security programs regarding suspicious programs – and most of the time I know what it’s about.
I do appreciate your taking the time to answer my question; it’s very helpful.
Thank you!
In this case, it seems Malwarebytes is warning that a software path restriction has disabled Avira’s notification popup. I’d definitely want to fix that.
I’d be really careful changing that part of the registry otherwise. Although Martin detected path restrictions, the ..\Policies\Microsoft\Windows\safer\codeidentifiers section can also be used to enforce that the given program(s) have a signed certificate.
If you were to delete a software certificate restriction, it would allow malware to replace the program at the given location with an unsigned program with the same pathname. That would be … ironic.
I’d forgotten that Avira Free uses avnotify to serve up nag popups. A side effect of disabling it is that it also gets used in “browsing virus information” according to http://alexborisov.org/disable-avira-splash-screen-and-nag-on-windows-7-64bit
I’d bet that the restrictions above were more due to irritation than to malware.
Ah thanks for the tip, that was exactly the problem I was having. I installed Avira on this PC maybe 3 years ago, and disabled the popup via Software Restriction Policy, subsequently uninstalled Avira for a better replacement and forgot all about the SRP.
As an aside, the reason that I blocked the Avira popup wasn’t because I just didn’t want the “Buy Avira” nag popups – I can deal with that on free software – but they popup and take over window focus for ALL windows inluding movies or games you may be playing fullscreen.. that’s a useability issue I refused to put up with.
Dan, those registry can be created by the user as a part of an administrative action (i.e. allowing or restricting some software by using Software Restriction Policy) or by another program (malicious or not). MalwareBytes has no way of knowing how the keys were created, but unfortunately it assumes they were created by malware. In this case, the only way to be sure is to follow Martin’s advice to inspect the keys yourself and to use common sense or a search engine to see what is their nature.
As for why they weren’t prevented by an AV, the answer is simple: creating and modifying them is a perfectly legitimate action.
I am not asking for generalizations, I am asking for those specific registry entries. How were these entries created? Are they the same registry entries that also trip up CCleaner? What do they do? Are they really malicious or just benign?
You seem to have an axe to grind with Malwarebytes, but I am not interested in your crusade. I myself only used MBAM, and only as a backup to an antivirus.
Dan, I think what you misunderstood me… I WAS talking about those specific registry entries that Martin mentioned in the article when I said that they were created either by the user for SRP purposes or by another program (malicious or not). Look at CJ Earner’s reply below: his first impression was they they were created to disable a component of Avira by a nefarious program and he suggested to fix it, but afterwards he remembered that the user can also add the rule in order to stop Avira’s nag popups. So it is hard to evaluate their purpose unless you do a research.
It is unclear to me how the registry entries were created. Did a program, virus, spyware, PUP, or a website script create it? What does it do? How come it was not prevented by your real-time antivirus (what AV are you using)? I remember that Avira creates a registry entry that CCleaner hates and tries to remove whenever you scan the registry. And it keeps being re-created.
This is the reason why I think that Malware Bytes is a bad product and why I will never use it. They make decisions about what is malicious or not without any context whatsoever. In this case, for instance, an entry in the Software Restriction Policies cannot be considered malware by itself; only if there are other signs of infection you can say for certain that a computer is infected, but Malware Bytes list just this registry entry as “Malware” (as you can see in the screenshot). IMO, this kind of behavior is not desirable for a security product, which should detect a real infection not something that their developers thought that it might be an infection.
I also use MBAM Pro version which differs in protection level over their freebie version. MBAM flagging suspicious items does not make it bad as there are many programming styles and avenues. Some use legit programming that runs like any normal MS certified program but it has malintentions. While others use obvious Trojan type coding and are easily caught. How do you tell the difference between what is good and what is bad. To the program it is just coding so it looks for known patterns.
Just because the police pulled you over because you were driving erratically doesn’t mean you’re going to lock-up. He just noticed it and issues a warning. Nothing wrong with flagging a warning, and under MBAM Pro we can exclude items, directories and web links we don’t want it to go looking in. Even Norton’s and McAfee’s sometimes flags such files/directories/links as possible undesirable. Are we to suddenly dismiss their credibility because they flagged something they deem suspicious?