Create an ssh key with Seahorse
Seahorse is a very powerful tool for the creation and managing of various keys. Seahorse is the default keyring manager for the GNOME desktop. I have covered Seahorse here on Ghacks before (see "Create, sign, and publish your PGP keys with Seahorse"), but one aspect I didn't cover was the use of Seahorse for secure shell keys. As you know, you can create secure shell keys that can be used for an even more secure ssh environment. I have shown how this is done via command line (see my article "Five handy secure shell tips and tricks"), but did you know that this can be taken care of using the Seahorse GUI? Let's take a look and see how this is done.
I will assume you already have Seahorse installed on your desktop. I will also assume you have access to the remote machine via ssh. With that in mind, let's get started.
Step 1: Fire up the GUI
You will find the Seahorse GUI in System > Preferences > Passwords and Encryption Keys. Start it up and you will see the standard Seahorse GUI. In that GUI, the tab you want to work with is the My Personal Keys tab. Click on that tab and you will see any personal keys you have already created. If you do not see any, you have to first create a key.
Step 2: Creating a key

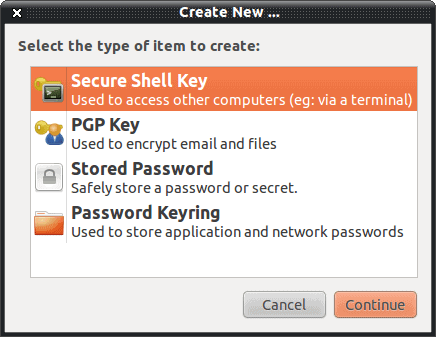
To begin the process of creating a key, click File > New and a small window will open (see Figure 1). From that new window click Secure Shell Key and then click Continue. When you do this you will be prompted for the following:
- Key Description.
- Advanced options: Key type and strength.
You can elect to set up the key or just create they key. Click Just Create and you will be prompted to create a passphrase (and confirm the passphrase). Once you have created your key it will appear in the Personal Keys tab.
Step 3: Set up key for secure shell.
The next step is to set that newly created key up to be used for Secure Shell. You need to have access to the remote machine at this point because the key will be automatically copied for you.
Go back to the personal keys tab and right click the key you want to set up for Secure Shell. When you right click it, select the option for Configure Key for Secure Shell. When you select this a new window will open asking for two pieces of information:
- Computer name.
- Login name
If you do not have the computer name in your /etc/hosts file you can just use the computer's IP address for the Computer Name. For the Login Name you must use a legitimate login on the remote computer. When you have those two pieces entered click Setup and you will be prompted for the remote username's password. Upon successful authentication the key will have been copied and you are ready to go. You can now ssh to that machine with the added security of ssh key authentication.
Advertisement