Create, sign, and publish your PGP key with Seahorse
I have espoused encryption on Ghacks plenty of times. I find most users do not employ encryption, of any kind, which is somewhat surprising given the constant rate at which data is stolen. With the help of encryption your data is much safer than it would be in plain text. To deal with encryption you have to use encryption keys.
This means you will giving and getting keys to/from various people (or within a business, different departments). If the amount of keys you manage gets too large, key management can become rather challenging. Fortunately there are tools out there to aid you in this task.
Once such tool is Seahorse. Seahorse is the default keyring manager for the GNOME desktop and it makes the task of key management quite simple. In this article you will see how easily Seahorse handles creation, signing, and publishing of your PGP key to a PGP keyserver.
Of course this does assume you want to publish your key on a public keyserver. There are benefits to publishing your PGP key. For instance it makes for easy access to your key so that those who need it, can get it. In some cases you would want to publish these keys to a non-public keyserver. For the simplicty of this article we will be publishing to the Ubuntu keyserver.
Features
Seahorse contains a number of outstanding features:
- Create/manage both PGP and ssh keys.
- Publish/retrieve keys from keyserver.
- Key backup.
- Passphrase caching.
But the feature that makes Seahorse stand out the most is it's user-friendly interface. A task which other applications can make new users shy away from, Seahorse makes simple. You can create, sign, and publish your own keys to a keyserver quickly and easily.
Installing Seahorse
More than likely Seahorse is already installed on your machine. If you are using the GNOME desktop, chances are it is there. To check to see if Seahorse is installed go to the GNOME Applications menu and look in the Accessories sub-menu. If it's there you're good to go. If not, you don't have much to do.
To install Seahorse all you need to do is follow these steps:
- Fire up your Add/Remove Software tool.
- Search for "Seahorse" (no quotes).
- Mark the entry for installation.
- Click Apply.
That's it. Once Seahorse is installed you are ready to create, sign, and publish.
Creating your PGP key

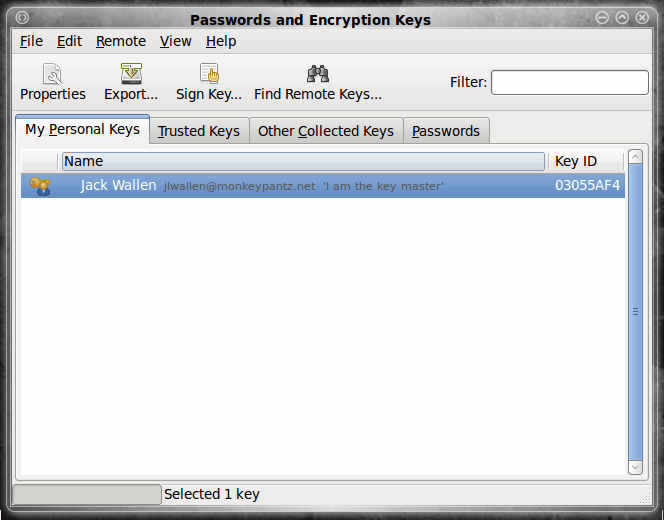
When the main Seahorse window opens (see Figure 1) the first thing you need to do is click the File menu and then select the New entry. This will open up another window where you can select from one of three keys to create:
- Password Keyring
- Secure Shell Key
- PGP Key
Since we are creating a PGP key, the choice should be obvious. Select PGP and then click the Continue button. The next window is where you fill out your information for your PGP key. All you need to fill out is:
- Full Name
- Email Address
- Comment
You also have the option of configuring some advanced options such as:
- Encryption type
- Key strength
- Expiration date
I recommend sticking with the defaults unless you have reason to alter one of the above options. You can up the strength of the Key to 4096 bits if you need. Naturally the higher the key strength the longer the creation time as well as the larger the file size. But if strength is important, take it to the max.
Once you have filled out this information, click the Create button. The next window will ask you to set a passphrase for this key. Remember, this key is going on a keyserver so make sure the passphrase is strong. And if you are creating a key with strength in mind, that passphrase should reflect this.
When the key is created it will be listed in your main window. In order to sign this key you simply have to select the key and click the Sign button. If you are going to distribute this key you should certainly sign the key. Why? When you sign (even self-sign) your key, if someone tries to tamper with your key PGP will notify you of the tampering. If you do not sign the key, someone could fairly easily modify your key without you being the wiser. Now with that said, all you need to do to self-sign your key is select the key you want to sign and click the Sign Key button.
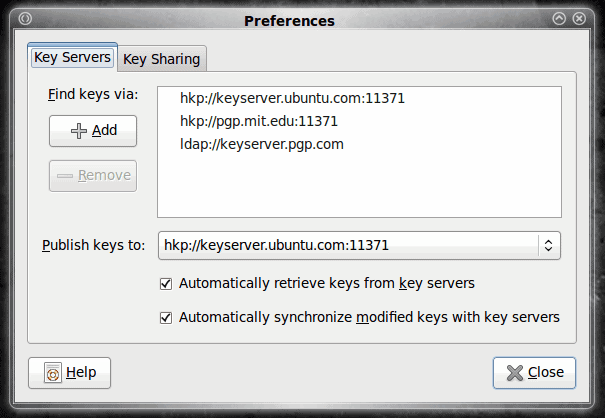
Once the key is signed you can then publish your key. To do this click the Remote menu and then selec the "Sync and Publish Keys" entry. A new window will open asking what you want to do. The button you want to click is the "Key Server" button. When you click this a new window will open (see Figure 2) where you can select the keyserver you want to use for publishing your keys.
If you are using an internal keyserver (or one that is not listed) click the Add button and enter the appropriate information. Once you select your keyserver click the Close button and you will be back at the window where you selected "Key Servers". Now you want to click the Sync button which will sync your new key.
You can check to make sure your key was uploaded by clicking the Find Remote Keys button, enter the name you used for the key, and click search. If your sync was successful your key will be listed. Now when users need your key you can tell them to grab it from the specific keyserver.
Final thoughts
I hope you can see that using PGP doesn't have to be difficult. In fact, Seahorse makes PGP so simple there is little to no reason not to take advantage of this security tool.





















Ubuntu Jaunty
If you want a GUI vs CLI, I recommend you to use GPA to manage your PGPKeys on Jaunty http://www.gnupg.org/related_software/gpa/screenshots.en.html (it is in the rep.)
The is a bug in seahorse 2.26.n You can import your private keys (e.g. from your desk to your notebook) but you cannot set the owner trust. The bug is corrected on v. 2.28.n
Seahorse (Gnome dependent) holds your pass shell keys and pass keyring (e.g. evolution password). So in doubt, do not attempt to remove/replace it with GPA if you are not sure what you are doing or if you are a beginner.
Thanks Jack for your answers. These questions were bugging me for a long time.
On point # 3. Could u please explain me “if you do not sign a key” — What is sign a key.
Is this what are u talking
1. Make a key trusted ( say mypublic key)
2. Encrypt the doc for that trusted key ( say mypublic key)
3. only me who has the myprivate key for mypublickey can see the data
Thanks
Ramesh
Ramesh: Good questions.
1. No, GPG and PGP are not the same. Seahorse uses GnuGPG. GnuGPG can read PGP so long as the versions are compatible. PGP versions 2 or earlier will not be compatible.
2. If you’re going to encrypt, say, a bank username/id and place it in your gmail account you should definately make your key as strong as possible with a complicated passphrase. and do NOT put those keys on a key server. I personally wouldn’t put my bank information anywhere – encryption or not.
3. Sure there have been hacks of encrypted data. As I mentioned – if you do not sign a key it can be hacked without your knowing it. Now a well encrypted key will take a long time to break into.
4. so long as the versions are compatible, you shouldn’t need to convert.
5. one simple way around this – don’t keep your keys on a network accessible computer. keep them on a usb flash drive or something like that. but if you do get both private and public keys you would have a fairly easy time decrypting data. but you would probably find any private key i use for critical data does not have a public key lying around anywhere near.
Hi I have few questions
1. is gpg and pgp keys are same
2. How safe are the content when we encrypt with pgp/gpg. for .e.g. can I encrypt my bank userid and passwd and put it in my gmail account. ( for argument sake FAS)
3. are they any claims saying that pgp/gpg encrypted contents are hacked
4. if gpg and pgp are not same .. how do we convert gpg encrypted document to pgp encrypted document
5. ok important one FAS ..in your sysem you have both private and public key. I hacked into system through net and I got both private and public key by exporting both keys on cmd line. Can I say your data are compromised..
FYI i: I use gpg2 on my mac book