Virustotal launches Android Sandbox Droidy
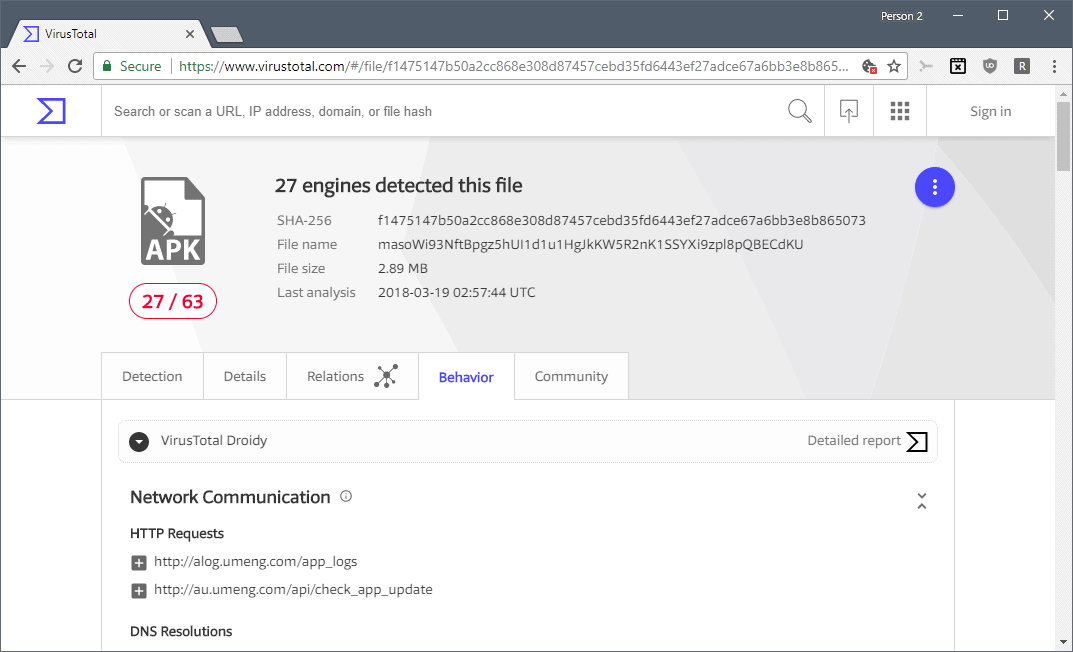
Google owned Virustotal announced the launch of the Android sandbox Droidy today which replaced the Android sandbox environment that the service used since 2013. Google acquired Virustotal in 2012 and the service launched its first Android sandbox a year later in 2013.
Virustotal Droidy reveals details about an application's activity that the previous sandbox did not reveal including HTTP requests, DNS resolutions, IP traffic, system file activity, permissions, process and service actions, database use, crypto-related events and more.
Interested users can check out a sample report on the Virustotal website. Use it to switch between Virustotal Droidy and the classic Virustotal Sandbox to see the differences.
The information that the new sandbox accumulates is used by other Virustotal services, Intelligence and Graph, to provide a clearer picture of an Android application's activity.
Using Virustotal Droidy

All you need to do is head over to the Virustotal website and drag & drop an Android APK on the field on the site, or use the upload button to pick an APK from the local system instead.
Virustotal computes the hash and displays scan results right away if the hash is already in the service's database; the APK is scanned if it is not.
Switch to behavior to see the list of actions that the sandbox detected during its analysis of the application.
Tip: you can click on detailed report to get additional details about hooked calls and screenshots that the sandbox captured during analysis.
Virustotal Droidy requires no Virustotal account. You still need an account to use some functionality such as Virustotal Graph on the site.
Closing Words
While security researchers may get the most out of Virustotal Droidy, it is clear that home users can benefit from the new Android sandbox as well.
If you download APKs from third-party sources or marketplaces, or even Google Play, you may want to run them through Droidy to find out more about their behavior before you install them on your Android device.
You could check out the network connections the app makes, take a look at captured screenshots, or take a closer look at file actions and service actions.
Related articles
- Scan files and apps with Virustotal Uplink for Android
- Virustotal Redesign and new tools Sneak Peek
- Virustotal: Scan firmware for signs of manipulation




















Trust Google ? Tsssss…….
I love VirusTotal.com, I always upload shady .apk files to catbox.moe then scan them with VirusTotal, it gives me such a peace of mind :)