Setting up CSF Firewall front end for IPTables
Firewalls, commonly underused by home users yet probably one of the most important aspects of securing your machine; ever.
Windows users have a HUGE array of options in front of them, but GNU/Linux isn’t quite as flexible in terms of giving you a thousand and one options.
Thankfully, there is the powerful IPTables firewall built into most systems. However, IPTables can be a daunting task for people to configure and learn how to use, thankfully there are front ends and other tools that can make setting up a very powerful firewall MUCH easier for the end-user.
CSF, or ConfigServer and Firewall, is one such IPTables frontend, and is an absolute powerhouse in itself while still maintaining a much easier setup.
MANY Distros come with firewall GUI frontends included in the system, but for the odd one that doesn’t, or if you are setting up a firewall on a text only system such as a VPS, or you just have decided to do away with graphical environments as a whole; this is for you.
For this, I am setting up CSF on one of my VPS, through a text only environment via SSH, so it’s absolutely required that you have some basic proficiency and understanding of how to use a terminal environment on your system if you wish to follow the exact steps I will be taking.
Note: You could do the vast majority of this if not all of it using a graphical environment, but I personally still would prefer to do it via command-line because I find it much faster to do simple things like extractions, copy pasting, text editing etc via terminal; but the choice is ultimately up to you. Just know that this tutorial is strictly text.
The Installation of CSF
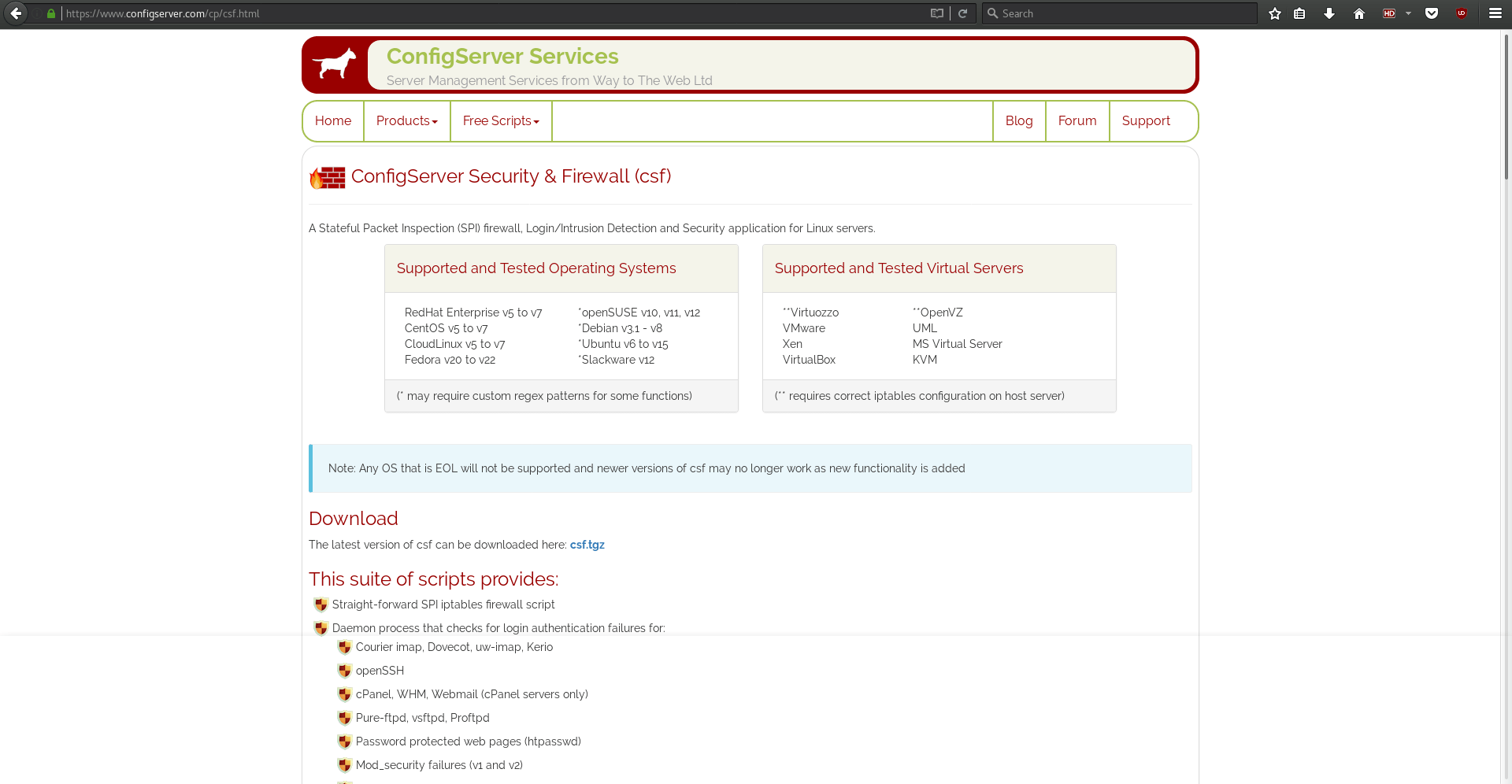
The first step is to download the tarball from the CSF website https://configserver.com/cp/csf.html
The first thing you’ll want to do is navigate to whatever folder you intend to download CSF to as root.
- su
- cd /usr/src
Then download the tarball
- wget https://download.configserver.com/csf.tgz
And then we need to extract the tarball
- tar -xzf csf.tgz
Move into the new directory
- cd csf
And run the installation script
- sh install.sh
Next, we need to check if our system has all of the required IPTables modules installed. Some of these may not be installed but so long as the following script does not give a -Fatal Error- then you are good to go.
- perl /usr/local/csf/bin/csftest.pl
You should hopefully get a message like this: “RESULT: csf should function on this serverâ€
In the scenario where you get fatal errors, this likely means that IPTables is either not installed, or not started / loaded into the kernel; look up the documentation / forums / search engine results for installing or starting IPTables for your distro of choice.
With all that being said, CSF is now installed! However, it’s not actually -DOING- anything yet, so, we need to configure it.
To do this, we simply need to edit one file, albeit a long file, it’s fairly well commented and documented, and relatively straight forward if you have any knowledge of networking or how the internet and your system work together. For those of you who have no idea what ports are for example, this may be a bit above your head and I highly recommend checking out some articles on the topic before you delve in deeper.
Configuring CSF
Let’s get started by opening the CSF configuration file with your favourite text editor, I personally use Nano for things like this.
- nano /etc/csf/csf.conf
The first thing you will see is the following, and it is absolutely essential that you do not play with this setting until we are completely done!
###############################################################################
# SECTION:Initial Settings
###############################################################################
# Testing flag - enables a CRON job that clears iptables incase of
# configuration problems when you start csf. This should be enabled until you
# are sure that the firewall works - i.e. incase you get locked out of your
# server! Then do remember to set it to 0 and restart csf when you're sure
# everything is OK. Stopping csf will remove the line from /etc/crontab
#
# lfd will not start while this is enabled
TESTING = "1"
Basically keeping this on (1=on 0=off) will ensure you don’t lock yourself out of your system by misconfiguring your firewall. Once you are confident everything is working as it’s supposed to, you can disable this.
There are some settings next referring to system logging, I recommend you simply scroll past them as they are set fine for most cases by default, and scroll until you see:
# SECTION:IPv4 Port Settings
CSF by default will be aware of all ports currently being used, and will adjust itself accordingly. For example, on this VPS I host a number of services from VoIP servers to gameservers for a few gaming clan clients of mine, and CSF has sorted that out for me.
# Allow incoming TCP ports
TCP_IN = "10011,20,21,22,25,53,25639,80,110,143,443,465,587,993,995,9987,8080,8181"
# Allow outgoing TCP ports
TCP_OUT = "25639,10011,20,21,22,25,53,80,110,113,443,587,993,995,8080,8081,9987"
# Allow incoming UDP ports
UDP_IN = "20,21,25639,10011,53,9987"
# Allow outgoing UDP ports
# To allow outgoing traceroute add 33434:33523 to this list
UDP_OUT = "20,21,53,25639,113,10011,9987,123"
As you can see, a number of TCP and UDP ports are already being granted passage through the firewall. You may want to double check any games, servers or services you run for what ports they use, and ensure that these ports are all listed accordingly.
If you are unsure of what ports you require open, you can check with the following commands:
- netstat -vatn
- netstat –listen
- netstat -lntu
And look for things such as
- tcp 0 0 0.0.0.0:8081 0.0.0.0:* LISTEN
In this example, port 8081 is being listened on, so I need port 8081 open.
I will add some links at the bottom of this article for more indepth focus on this for those who need it.
After you are all set on setting up the IPv4 ports, you will want to make sure Ipv6 is also taken care of if you utilize it on yout system, much in the same fashion.
After that, you theoretically could simply start CSF and be good to go, however I highly recommend reading through the rest of the configuration file and changing anything you feel needed; ESPECIALLY if you are setting this up on any kind of server environment. CSF has some pretty awesome anti-DDoS protection options in it. I have used CSF on other servers of mine, and attempted to pwn them pretty hard for testing purposes just to have CSF put me down. That said, it's definitely not unbeatable, but it's solid, that's for sure.
Running CSF
Once that is all said and done, we want to test CSF to ensure everything is working properly.
To do this, let's start CSF
- csf -e
You should see a bunch of text scroll through your screen, and a message that reads:
- csf and lfd have been enabled
*WARNING* TESTING mode is enabled - do not forget to disable it in the configuration
At this point, the firewall is running. Now is when you try to connect your usual services, run your games, and do whatever it is that you normally do.
If at this point you have no issues (which you shouldn't if you followed the comments in the config file properly!) you can disable testing mode.
- nano /etc/csf/csf.conf
TESTING = "1" becomes TESTING = "0"
And then
- csf -r
to restart CSF.
You're done!
Anytime you ever need to add ports, you can simply open the CSF config file again, add the port numbers, and then restart csf with
- csf -r
If you ever need to stop CSF, use
- csf -x
Your system is now protected by a firewall!
More resources and information can be found at:
- https://configserver.com/cp/csf.html
- https://forum.configserver.com/
Now You: Do you use the built-in firewall on your system?
















LOL. I knew you’d be using the terminal sooner or later! ;-)
I’m partial to the enterprise ways. I use a shell script (with lots of useful comments) and a systemd service file that starts it before any network interfaces come up (Before=network-pre.target). I can then use this service file as a requirement for other services (protecting me from myself).
I found a lot of great ideas for my firewall script on github and lots of helpful info about rules and modules on sites like stackexchange, the archwiki and of course the man pages.
Does this GUI make use of or suggest to use nf modules where appropriate? Most GUI’s I’ve seen tend to go only so far. Simply sharing a scanner is best with nf_conntrack_sane for example. Unfortunately, nearly all the good info on the web refers to netfilter/iptables and quotes from the man pages. This is the unfortunate reality with Linux, it’s always going to be server first (super geeky). In my experience the more unneeded layers you add the worse things tend to get. And the closer you stay to how things are done in the enterprise world the better.
Although not my cup of tea, it’s nice to see articles that involve Linux and compiling from source. Keep ‘em coming!!
Yes I use my Mint GUFW firewall. Very simple setup incoming-deny and outgoing-allow :)
I don’t game or stream enything:))