D-Link's digital certificate disclosing could allow spoofing
D-Link Corporation disclosed four digital certificates recently inadvertently that attackers could use to spoof content.
While the certificates cannot be used to issue others or impersonate domains, they can be used to sign code which attackers could use to (better) disguise malware as legitimate software.
Microsoft has released a security advisory and an update to remove the affected digital certificates from supported versions of Windows. D-Link has revoked the certificates in the meantime as well.
The four leaked digital certificates are:
| Certificate | Issued by                   | Thumbprint |
| DLINK CORPORATION | Symantec Corporation | ‎‎3e b4 4e 5f fe 6d c7 2d ed 70 3e 99 90 27 22 db 38 ff d1 cb |
| Alpha Networks | Symantec Corporation | ‎‎73 11 e7 7e c4 00 10 9d 6a 53 26 d8 f6 69 62 04 fd 59 aa 3b |
| KEEBOX | GoDaddy.com, LLC | 91 5a 47 8d b9 39 92 5d a8 d9 ae a1 2d 8b ba 14 0d 26 59 9c |
| TRENDnet | GoDaddy.com, LLC | db 50 42 ed 25 6f f4 26 86 7b 33 28 87 ec ce 2d 95 e7 96 14 |
The issue affects all current Microsoft operating systems that are still supported by the company starting with Windows Vista Service Pack 2 to Windows 10 on the client side, and Windows Server 2008 Service Pack 2 to Windows Server 2012 R2 on the server side.
The update is delivered automatically to all supported operating systems.Windows Vista, Windows 7, Windows Server 2008 and 2008 R2 systems need to have the "automatic updater of revoked certificates" installed. Microsoft customers in disconnected environments need to consult the following Microsoft Knowledgebase article for additional information.
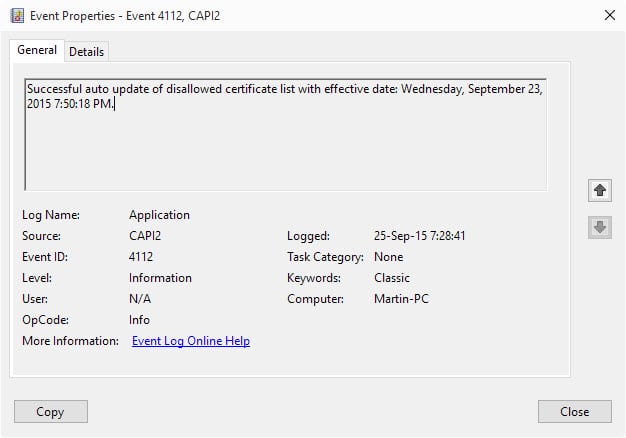
One way to check that it has been applied is to verify this through the Event Viewer.
- Tap on the Windows-key, type Event Viewer and hit enter.
- Select Action > Create Custom View.
- Select "by source" and then the source CAPI2.
- Click ok, and on the next screen ok again.
- Wait until the list of events has been loaded and scroll down to the very bottom.
- You should see an information level event with the Event ID 4112 there.
- Double-click on it. It should have the description: Successful auto update of disallowed certificate list with effective date.
The update has not been applied yet if you don't see it listed yet in the Event Viewer. (via Deskmodder)



















I don’t have this update. So I went to download the “automatic updater of revoked certificates” but when I tried to install it, I got a message saying it’s not applicable to my system. Now what do I do?
Did you check in the Event Viewer?
Well I finally found it under Windows Logs >> Application. I assumed it would be under Windows Logs >> Security.
I checked this morning and missed the log with Nirsoft’s MyEventViewer because I focused on today 2015-09-27.
I just searched for Event Id = 4112 and indeed found two of them dated 23 and 25 September 2015, both stating unauthorized certificates list update (translated from French).
Thanks, Martin, in this way that your question made me check deeper before confirming my first result…
I prefer, I had it in mind like an itching parasite …
Same here on Windows 7SP1… spent half an hour to try to figure out, no way. And don’t count on Microsoft to bother : they conceive the world as composed of admins exclusively the same way we would all be using the Web in an office, from an office, between offices, with office work & standards, all of us, the planet being a gigantic office :)
This procedure worked positively for me on Windows 10 re the subject of interest, but it was a bit disconcerting to note other unrelated failures in the view….