Microsoft Security Bulletins For May 2013 overview
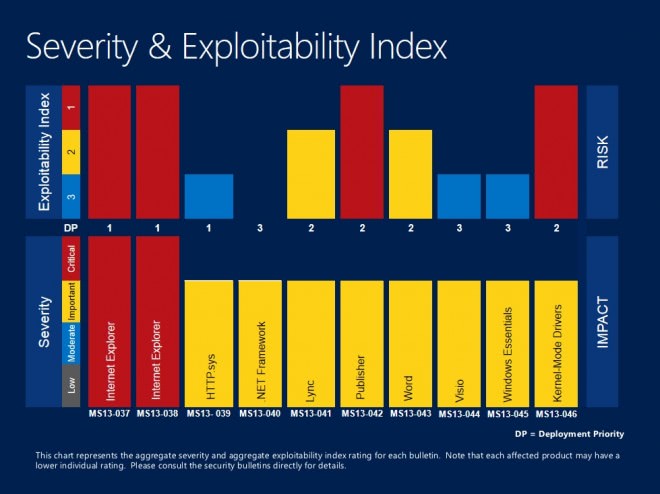
It is the second Tuesday of the month and we all know what that means: Microsoft Patch Day. Microsoft has released a total of ten security bulletins this month that address security related issues in products such as Microsoft Windows, Internet Explorer, Microsoft Office or Windows Essentials. The ten bulletins address a total of 33 different vulnerabilities.
Two bulletins have received the highest severity rating of critical while the remaining eight received important ratings. What this means is that at least one product received the rating while other affected versions of the product may have received the same or a lower rating.
Security update MS13-038 resolves a 0-day security vulnerability that affects Microsoft's Internet Explorer 8 on all supported operating systems. Microsoft has released a fix-it patch recently to address the issue.
The second critical bulletin of the month is a cumulative update for Microsoft's web browser that resolves 11 different security related vulnerabilities.
Operating system distribution
It is often the case that desktop and also server operating system versions are affected in different ways by the vulnerabilities. Here we look at the distribution of severity ratings across all desktop and server operating systems.
As you can see, all desktop versions of Windows share the same severity rating with the exception of Windows 8 and Windows RT. As far as servers go, the picture is a little bit different. Here it is Windows Server 2012 that is affected more severely than previous versions of the server operating system.
- Windows XP: 2 critical, 2 important
- Windows Vista: 2 critical, 2 important
- Windows 7:Â 2 critical, 2 important
- Windows 8:Â 1 critical, 3 important
- Windows RT: 1 critical, 2 important, 1 moderate
- Windows Server 2003: 1 important, 2 moderate
- Windows Server 2008: 2 important, 2 moderate
- Windows server 2008 R2: 2 important, 2 moderate
- Windows Server 2012: 3 important, 1 moderate
Deployment Guide
Microsoft recommends to deploy the bulletins in the following order:
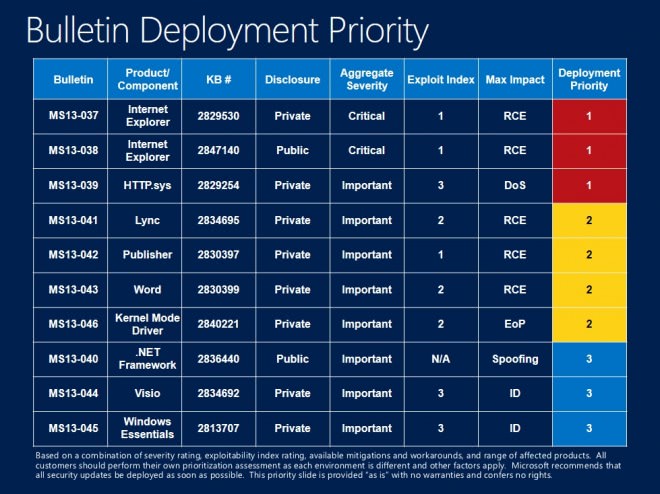
- First MS13-037, MS13-038 and MS13-039. The first two bulletins are the only ones with a critical severity rating. The third bulletin addresses an issue that could allow a denial of service attack against Windows systems.
- Then the four bulletins MS13-041, MS13-042, MS13-043 and MS13-046. The first three address vulnerabilities in Office programs, the fourth one in the Kernel Mode Driver.
- Last but not least bulletins MS13-040, MS13-044 and MS13-045 which address security issues in the .Net Framework, Visio and Windows Essentials.
Security Bulletins
- MS13-037 - Cumulative Security Update for Internet Explorer (2829530)
- MS13-038 - Security Update for Internet Explorer (2847204)
- MS13-039 - Vulnerability in HTTP.sys Could Allow Denial of Service (2829254)
- MS13-040 - Vulnerabilities in .NET Framework Could Allow Spoofing (2836440)
- MS13-041 - Vulnerability in Lync Could Allow Remote Code Execution (2834695)
- MS13-042- Vulnerabilities in Microsoft Publisher Could Allow Remote Code Execution (2830397)
- MS13-043 - Vulnerability in Microsoft Word Could Allow Remote Code Execution (2830399)
- MS13-044 - Vulnerability in Microsoft Visio Could Allow Information Disclosure (2834692)
- MS13-045 - Vulnerability in Windows Essentials Could Allow Information Disclosure (2813707)
- MS13-046 - Vulnerabilities in Kernel-Mode Drivers Could Allow Elevation Of Privilege (2840221)
Non-security related updates
Non-security related updates have been released since the last patch Tuesday as well. The following list provides you with an overview of the updates that Microsoft has released in that time.
- Update for Windows 8, Windows RT, Windows Server 2012, Windows 7, Windows Server 2008 R2, and Windows Server 2008 (KB2798162)
- Update for Microsoft .NET Framework 4.5 on Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB2805221)
- Update for Microsoft .NET Framework 4.5 on Windows 8, Windows RT, and Windows Server 2012 (KB2805222)
- Update for Microsoft .NET Framework 4.5 on Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB2805226)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2805227)
- Update for Windows 8 and Windows Server 2012 (KB2805966)
- Update for Windows 7 (KB2813956)
- Update for Windows 8, Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2 (KB2818604)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2820330)
- Update for Windows 7 and Windows Server 2008 R2 (KB2820331)
- Dynamic Update for Windows 8 and Windows Server 2012 (KB2820332)
- Dynamic Update for Windows 8 and Windows Server 2012 (KB2820333)
- Update for Windows 7 and Windows Server 2008 R2 (KB2835174)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2836988)
- Windows Malicious Software Removal Tool - May 2013 (KB890830)/Windows Malicious Software Removal - May 2013 (KB890830) - Internet Explorer Version
- Update for Root Certificates for Windows 8, Windows 7, Windows Vista, and Windows XP (KB931125)
- Update for Windows 8 for x64-based Systems (KB2818604)
How to download and install the May 2013 security updates
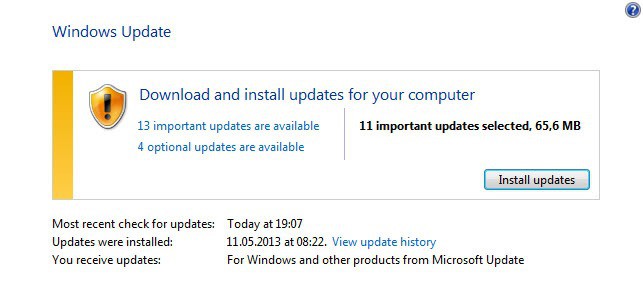
The easiest way to obtain all security updates is to use Windows Update. Windows XP to Windows 7 users can use the search menu to load Windows Update on their system while Windows 8 users need to search for it on the start screen instead.
You may need to click on the check for updates button on the page as the updates may not have been picked up automatically by the operating system.
If you want more control over the process head over to Microsoft's Download Center. I recommend you enter the name of the bulletin into the search on the page as Microsoft seems to have modified the download page so that you cannot sort security updates by date anymore.
Advertisement




















I have let the system (Windows 8 Pro x64) update itself and after installing these Patches, I can’t no longer use Windows anymore…! After the blue flag, the screen goes black and flash repeatedly, like it’s stuck in a loop of being turned on and turned off And strangely there’s no restore point (I have turned it on). Luckily, I install Windows 7 on a seperate drive in case such as this, and now seems like I got to do a Refresh. By far, there seems to be no report of this problem
As always, Martin and Ilev, thank you very much for the Microsoft updates list: quick, easy and useful :) Even with a link for troubleshooting that update problems in Ilev’s comment… :)
This month may be even more important, as Microsoft appears to have messed up their Download Center, and I can just get any product downloads list ordered by “popular downloads”, but not by date to get the most recent ones…
Again, thank you very much :)
I got an error :
Update for Microsoft .NET Framework 4 on Windows XP, Windows Server 2003, Windows Vista, Windows 7, Windows Server 2008, Windows Server 2008 R2 for x64-based Systems (KB2468871)
Installation status: Failed
Error details: Code 643
Solved it here : http://answers.microsoft.com/en-us/windows/forum/windows_7-windows_update/kb2468871-system-update-install-error-error-643/62e33560-eb46-4b82-95f3-00d7c56709da
Microsoft Patch Tuesday: May 2013
MS13-037/KB2829530 – Cumulative Security Update for Internet Explorer (IE 6, 7, 8, 9 and 10 on Windows XP, Vista, 7, 8, RT, Server 2003, 2008, 2008 R2 and 2012). This critical update addresses eleven different vulnerabilities in Microsoft’s web browser running on all currently supported editions and versions of Windows except the Server Core installations. The way IE authorizes script access to data and handles objects in memory can allow remote code execution. A restart is required after installation.
MS13-038/KB2847204 – Critical Security Update for Internet Explorer (IE 8 and 9 on Windows XP, Vista, 7, Server 2003, 2008, and 2008 R2). This is another update for the listed versions of IE, which addresses a single vulnerability that could allow remote code execution if a user visits a specially crafted web page that contains malicious code. It’s rated critical for the client operating systems and moderate for servers, and does not affect IE 6, 7 or 10 nor Server Core installations. A restart may be required after installation.
MS13-039/KB2829254 – Vulnerability in HTTP.sys (Windows 8 and RT, Server 2012, including Server Core installation). This update addresses a single vulnerability in the way HTTP.sys handles some HTTP headers that could allow an attacker to send a specially crafted malicious HTTP packet to a system that results in a denial of service attack. It is rated “important.†Only the listed operating systems are affected. A restart is required after installation.
MS13-040/KB2836440 – Vulnerabilities in .NET Framework (Windows XP, Vista, 7, 8, RT, Server 2003, 2008, 2008 R2, and 2012, including Server Core installations). This update addresses two vulnerabilities in the .NET Framework versions 2.0 through 4.5, which could allow spoofing of a .NET application that would allow the attacker to modify the contents of an XML file and gain access to endpoint functions. It’s rated “important.†A restart may be required after installation.
MS13-041/KB2834695 – Vulnerability in Lync and Communicator (Microsoft Communicator 2007 R2, Lync 2010 and Lync Server 2013). This update addresses a vulnerability in Lync and Communicator that could allow an attack to remotely execute code by sharing a specially crafted malicious file or program through the communications application. It’s only rated “important,†as the recipient would have to take action to view or share the content by accepting the invitation. Only the listed version of Communicator and the listed versions of Lync are affected. Lync 2013 and Lync for Mac 2011 are not affected. A restart may be required after installation.
MS13-042/KB2830397 – Vulnerabilities in Microsoft Publisher (Microsoft Office 2003, 2007 and 2010). This update addresses eleven vulnerabilities in Microsoft Office that can be exploited by getting a user to open a specially crafted malicious file with Microsoft Publisher. The attacker would then gain the same rights as the currently logged-on user. It’s rated “important†but note that Office 2013 is not affected. A restart may be required after installation.
MS13-043/KB2830399 – Vulnerability in Microsoft Word (Microsoft Office 2003, Microsoft Word Viewer). This update addresses a vulnerability in the Office 2003 SP3 version only of Microsoft Word and the Word Viewer, which could allow an attacker to remotely execute code if a user opens a specially crafted malicious document file or email message. The attacker would then gain the same rights as the currently logged-on user. It’s rated “important.†Other versions of Word, including Word 2013 and Word 2013 RT, are not affected, nor are the Word Web apps or Office for Mac 2011. A restart may be required after installation.
MS13-044/KB2834692 – Vulnerability in Microsoft Visio (Microsoft Visio 2003, 2007, 2010). This update addresses a vulnerability in the listed versions of Microsoft Visio by which an attacker could cause information to be disclosed if the user opens a specially crafted malicious Visio file. It’s rated “important.†Visio Viewer and Visio 2013 are not affected, nor are Microsoft Office 2007 and 2010 Filter Packs. A restart may be required after installation.
MS13-045/KB2813707 – Vulnerability in Windows Essentials (Windows Essentials 2011, 2012). This update addresses a vulnerability in the Windows Writer (formerly called Live Writer) blogging tool that is part of the Windows Essentials package, which could allow information disclosure if the user opens Writer via a specially crafted malicious URL. The attacker would be able to overwrite files on the target system. It’s rated “important.†Note that although Windows Essentials 2011 is affected, there is no update available for it; this update only applies to Windows Essentials 2012, and is available for download only. A restart may be required after installation.
MS13-046/KB2840221 – Vulnerabilities in Kernel-Mode Drivers (Windows XP, Vista, 7, 8, RT, Server 2003, 2008, 2008 R2, 2012, including Server Core installations). This update addresses three vulnerabilities that affect all currently supported versions of Windows. An exploit could result in elevation of privileges if an attacker is able to log onto the system locally with valid logon credentials and run a specially crafted malicious application. It’s rated “important.†A restart is required after installation.
Other Updates/Releases
There were a whopping 15 non-security updates released today, including the regular monthly update for the Malicious Software Removal Tool (MSRT).
KB2798162 – Update to improve messaging of dialog boxes when you run executable files in Windows. Applies to Windows 7, 8 and RT and Server 2008, 2008 R2 and 2012. Changes how some dialog boxes are presented to provide you with more information.
KB2805221 – Update for .NET Framework 4.5. Applies to Windows Vista, 7 and Server 2008 R2. Fixes issues pertaining to DateTime.TryParse, an unhandled exception, a CryptographicException error, and more.
KB2805222 – Update for .NET Framework 4.5. Applies to Windows 8, RT and Server 2012. Fixes the same issues mentioned in KB2805221 above.
KB2805226 – Update for .NET Framework 4.5. Applies to Windows Vista, 7 and Server 2008, 2008 R2. Fixes issues with Windows Workflow Foundation (WF).
KB2805966 – Update to resolve loss of temporary Internet files and history in upgrade. Applies to upgrades from Windows 7 or Server 2008 R2 to Windows 8 or Server 2012. This update resolves the issue of lost temporary Internet files (browser cache), browsing history, cookies, saved passwords.
KB2813956 – Update to resolve mobile broadband issue. Applies to Windows 7. This updates fixes the issue where mobile broadband providers disappear from the list of available networks in the network interface.
KB2818604 – Microcode update for AMD processors. Applies to Windows 8 computers using AMD processors. Updates the microcode for specific models of AMD series C, E, G and Z processors.
KB2820330 – Compatibility update. Applies to Windows 8, RT and Server 2012. Improves the compatibility experience.
KB2820331 – Application compatibility update. Applies to Windows 7 and Server 2008 R2. Improves the compatibility experiences.
KB2820332 – Compatibility update for legacy upgrade experience. Applies to Windows 8 and Server 2012. Improves the experience of upgrading to the latest version of Windows 8 or Windows Server 2012.
KB2820333 – Compatibility update for web and media upgrade. Applies to Windows 8 and Server 2012. Improves the web and media upgrade experience when upgrading to the latest version of Windows 8 and Server 2012 and offers the latest compatibility status of installed applications, devices and drivers.
KB2835174 – Update to resolve Product Activation Wizard issue. Applies to Windows 7 and Server 2008 R2. This update fixes an issue where activation fails and an incorrect disclaimer is displayed.
KB2836988 – May Update Rollup. Applies to Windows 8 and Server 2012. This rollup package includes multiple performance and reliability improvements and resolves issues with graphics driver updates, system performance impact of network activity, file copy, crashes and more.
KB931125 – Update for Root Certificates (Windows XP, Vista, 7 and 8). This is an update to the list of root certificates that are accepted by Microsoft for the use of extended validated (EV) certificates on web sites and digital certificates used for email encryption and secure delivery of code. This update requires a restart.
KB890830 – Windows Malicious Software Removal Tool (MSRT). This is the regular monthly update to the MSR for Windows XP, Vista, Windows 7, Windows 8, and Windows Server 2003, 2008/2008 R2, and 2012.
Updates since the last Patch Tuesday
There have been only a couple of new or changed non-security updates or content released since April Patch Tuesday:
KB2840149 – Security Update for Windows Embedded Standard 7, Windows 7, Windows Vista, and Windows Server 2008/2008 R2. This bulletin, originally released on April 9 with the regular Patch Tuesday updates to address vulnerabilities in the kernel-mode driver that could allow elevation of privilege, was updated on April 24.
KB2607607 – Language Packs for Windows RT (Windows RT). On April 23, more new language packs for Windows RT added nine additional languages.
Again thank you ferry much for your extensive explanation this mount like always. This mount I especially like that with the Security Bulletins your linking threw to the technet.microsoft.com website. Also ferry handy is that you now some of the non-security related updates have a link.
I hope that you keep up the linking and maybe if possible if its not to much work will give all them a direct link.
I always linked to the bulletins Paulus. This time, I just cut the description that I took from Microsoft’s website, so it is compact and takes less reading to go through.
I will continue to post the information here as I myself find them useful and from the looks of it, at least some readers as well.
Martin, thank you for your answer. Have as said, just reinstalled Win 7 and getting massive updating, including warning popups about a whole list of the new updates being actually vulnerabilities!!!
i did not pay Microsoft a sh*tload of money to have to spend hours crawling around on the Web trying to find out about their dud “security updates” and how to fix them.
Is why am desperately wanting to go Linux.
Howdy Martin, would like to ask if the latest eruptions of Windows updates (am Windows 7 Home Premium 64-bit) will fix all of the known vulnerabilities. Got an auto-email from Ghacks last week warning about a bad update that was actually creating a dangerous vulnerability (Update 2823324) and that it needed to be manually deleted. Is this still necessary (have just reinstalled the OS and am receiving massive amounts of updates)???
You have got a very good Website here, and very good to know that you are a Linux expert, because am soon intending to try and use “Linux Mint 14 MATE/Nadia” (had a go at installing it prior to reinstalling Windows 7, but the installation of Linux ground to abrupt halt when three icons appeared on the screen, and when each was clicked on, it produced a popup menu of completely incomprehensible “choices” (am not new to Linux either, have installed several platforms to check them out, and have not before encountered any obstructions like this before) and am wondering, Martin, if you could please explain what is the correct way to get through this obstacle???
@ Uhtred
i use only the “Important Update” setting after having lot of trouble when letting “Optional Updates” be included.
Microsoft removed the broken update, fixed it, and it is no longer being delivered, so no need to worry.
Firefox 21.0 just came in on the release channel.
Great to know Firefox is released with Microsoft updates! :p
Thanks for info…
Just a heads up… might just be my win7 system but amongst the other updates I had an optional update included for microsoft mouse and keyboard today which I allowed… and discovered when I had selected restart to take effect, a separate installation window started up for the mouse and keyboard software… it was killed with the restart process, but afterwards I’d lost my intellipoint software for the microsoft 4000 mouse, which I had to download again and install to get working.