NoSuchApp for Android highlights apps secretly connecting to tracking sites
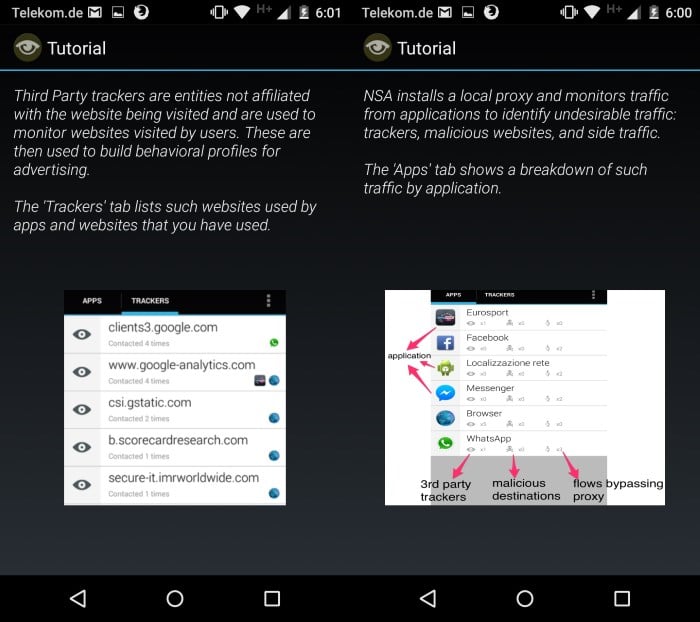
When it comes to knowing what apps do and don't do on Android, there is little that average users can find out in advance or after installation.
While the requested permissions may provide information about data the app may access or modify, and also about network or Internet connections it may establish, nothing is provide in detail.
For instance, you may know that an app connects to the Internet based on its permission requests but you don't know to which sites and often why.
A recently published research paper suggests that many free applications offered on Google Play connect to urls in the background.
The team analyzed 2146 free applications in all 25 categories on Google Play based on popularity and recency and discovered that these applications connected to "almost 250,000 unique URLs across 1985 top level domains".
The methodology used to analyze these apps was the following:
- All apps were downloaded and executed on a Samsung Galaxy SIII Mini smartphone running Android 4.1.2.
- The phone was configured to use a local VPN which the researchers monitored for traffic activity using tcpdump to create a package for each individual application.
- A series of 10000 automated user interactions with each application simulated use while the app was running.
- Each packet capture was processed with tshark to extract urls which the team compared against EasyList and EasyPrivacy, two popular lists used by Adblock Plus and other adblocking and anti-tracking extensions and programs.
- Last but not least, all urls are checked on Virustotal as well.
The conclusion is devastating. About 10% of all tested apps connect to more than 500 distinct URLs with the top applications all connecting to more than 1000 distinct URLs each and about 100 top level domains.
About 33% of apps don't connect to ad-related sites while the remaining applications connect to an average number of 40 ad urls (some to more than 1000) with Google owned sites at the top.
About one quarter of apps communicate with tracking servers. Some connect to more than 800 different trackers.
As far as Virustotal ratings are concerned, 94.4% of all urls tested had a suspicion score of 0 with the worst case for the rest being that hits were recorded by three of 52 different engines used by the service.
NoSuchApp
The developers have created an application that introduces reporting functionality on Android similar to what they have done.
The app is not available on Google Play currently but plans have been made to publish it on the site in the future. For now, it is only available directly on this address.
Update: The download is no longer available due to traffic. We have set up a mirror here on Ghacks. Download the file with a tap or click on the following link. Please note that we don't support it in any way and cannot be held responsible for issues that may occur. (Download Removed)
Note: It installed fine on My Motorola G running Android 5 but crashed after the introduction.
The app installs a local proxy and monitors traffic from applications run on the system to identify 3rd party trackers and malicious destinations.





















since this app always crashed on my lollipop 5.0.2 I found an alternative which works great: https://code.google.com/p/iptableslog/ you can fidn it via F-Droid, its called Network Log – not sure if this NSA app does anything else?
Installed on Sprint Samsung Galaxy Note 2, Android 4.4.2, unrooted. App issues SandroProxy certificate, i accept. The associated icon in the notification bar and the entry in the notification tray blink occassionally, but no suspicious apps are ever specified, nothing is found. The in-app utility “Test Configuration” claims “error: proxies–not–configured”. I’m guessing that the proxy server is down, perhaps intentionally as this proof-of-concept has been proven doable.
Excellent white paper–thanx for that and the heads up. The app developers cite “The lack of oversight in Android Play Store…” and “envision a crowd sourced app reputation system…” that “…would enable easy blacklisting of applications (and their traffic)…”
In other words, instead of trying to reform Google, or to do what Google should be doing and constantly maintain NoSuchApp via a complex database with algorythms designed to detect tracking, overly aggressive advertising, etc, and prone to become outdated, inaccurate, and potentially problematic…instead of giving us the fish, the developers want to enable us to fish for ourselves! Amen to that. Please, Martin, keep us posted about their progress.
Hey Brian, I have had the exact same issue for a while now. I don’t know if it’s the proxy that’s down or if it’s an issue with the device. I’m thinking your device needs to be rooted in order for it to snoop on your traffic. Just a thought, but I couldn’t get it to work ever. I will get a rooted device and test.
It crashes only on wifi, works fine with mobile data. HTC One M7 android 5.0.2
Crashes immediately after tutorial on my Galaxy Note 4 android 5.0.1
> I don’t understand the first sentence. Seems to me “it DOES matter”. Possible BIND attacks and possible certificate spoofing are “maybe, might happen someday” cases. Proxying the traffic does provide benefit in handling the “happening right here, right now” cases.
Maybe it was a bit unclear but a proxy can easily bypassed, FREAK attacks are not “might someday cases” – even such big company’s like Kaspersky, Eset and others are affected by this, and they update there signatures/programs daily to stay up-2-date. On Android that story is a lof of complicated because it takes usually more time to get updates (STOCK).
As I said tcpdump does the same – or in case you want really a firewall just use AFWall+ (but that also not protects against all). So a tool that promise something should be well documented and not on any dropbox. This app is more like a proof as concept and not for daily use or beginners.
Hello,
Do you have to be rooted for the app to work? I have installed it, but it finds no traffic at all and tells me my proxy needs to be configured.
Thanks and May the 4th be with you,
Vinny
Don’t work with Android 5+
@Thomanphan, ahhhhh thank you, that’s gotta be my issue. I’m on 5.0.2.
Thanks for update link but you share a zip file not easy to install from my phone, I search and founded a link for easy to install
http://apkdot.com/apk/martin-brinkmann/nosuchapp/nosuchapp-0-6-00/
@martin:
where did your comment and the link go?
The link is in the article.
Sorry, the notifications came 5 minutes before your site had actually updated :-(
This account’s public links are generating too much traffic and have been temporarily disabled!
can yo put up a mirror please? I’m getting:
Error (429)
This account’s public links are generating too much traffic and have been temporarily disabled!
I have added the program as a download mirror here on Ghacks.
The app seems to work on my (rooted) Samsung Galaxy S5 (SM-G900F) running still Android 4.4.2 Kitkat.
It detects for example the non malicious tracker analytics.appmonsta.com in the Gravity Screen app or the Google IP 216.58.208.46 in the system app BluetoothTest.
But see the confusing NVISO ApkScan malware analysis report on a test device running Android 4.1 Jelly Bean:
http://apkscan.nviso.be/report/show/b7a6a6fcd74cc3b4d89e1c24534fa3f6
nevermind, I figured it out, you can delete this post. I think the page wasn’t updating for me for some reason.
Much needed, but, why is it asking for privacy permissions including ‘read phone status/identity’ & ‘read, modify, delete contents of SD card’ at install?
The only permissions is actually needs to function as it should are device access facilities associated with network and internet connectivity.
This totally goes against what they are setting out to demonstrate: the invasiveness of many android apps.
Also, the paper is from Eurecom, a research centre with strong telecoms industry ties, so on the whole, I find it all little dubious.
Crashes immediately after tutorial on my one plus one (running cm12s, 5.0.2, stock Cm kernel). Right as I selected “do it now”. No such app did manage to place a notification in the tray which appears to be counting tracklers/malicious, but it’s count had remained at 0/0 for nearly am hour already, leading me to conclude it isnt working
Good topic, badly needed app, sloppy article. Doesn’t name the researchers or the organization or even the title of the paper . Yes those are available after a link, but what happens when the link breaks?
This is why we need a native permission controller plus a firewall for android. But I don’t think they will come anytime soon. I use AFWall+ on my Lenvo k900.
So this app tracks connections, but doesn’t prevent them?
If it prevents track connections, it will become another Adblocker. Then it will need to create its own tracking/ad list because EasyList is too big for mobile. Than it will need whitelist, because many apps will not work without tracking connections. Thats the whole mess. And how you monetize adblocker without betrayals and lawsuits?
At least this app will give estimation which apps should be avoided for tracking way too much. For example, paid apps should not have multiple tracking services attached to them.
Sounds like an app with excellent “freemium” potential. Free version raises awareness; paid version enables selective blocking.
Hmm, although they might create a “starter” mini-EasyList, I don’t expect they’d need to update/maintain the list. User can see/choose which domain destinations the app will be able to contact.
I would absolutely choose to purchase the paid version of an app like this.
I’m curious to understand what/why the “flows bypassing proxy” (annotated in the screenshot) represents.
These ‘flows’ are traffic by apps which refuse to have their traffic proxied? Traffic from apps which are somehow immune to (are autowhitelisted?) having their traffic proxied?
Never mind…reset my wireless and now back to normal. Sorry!
I installed this on my kindle fire, noticed it blocked some of my apps from connecting to the network, and uninstalled it. apps were still blocked so I purged the certificate, but no help. shows I am connected to wifi but no vpn connections or anything. any ideas how to get m.y settings back to where they were before installing this?
Very informative article Martin! I really appreciate your efforts that you find such apps for us.
Anyone have any idea why Google apparently DOESN’T WANT want to make more detailed permission control and information available to its users?
I’m certain they have the technical ability to do better. So why don’t they want to? What are they afraid of?
They want app developers to be able to access sensitive data, so they can then sell it, because there is a market for it. If they allowed to block access to that information, it would be less profitable for app developers, plus, advertising companies depend on Google keeping Android full of privacy vulnerabilities in order to mine the data.
Mr. Brinkmann:
I value your opinion on all things relevant to the Computer and Internet.
On a scale from 1 to 10 (10=Excellent) how would you rate the performance of your Motorola G.
I ask this as I am SERIOUSLY considering ordering one of the MOTO phones through http://www.republicwireless.com and had a special eye on the Moto G and Moto E.
Thanking you in advance for your (usual) Brutally Honest answer!
i
i bought the moto-g on sale for $80 and my service is $35 a month unlimited everything. I haven’t found anything it can’t do. Everything runs solid and fluid. It’s never lagged and the battery lasts all day. If I were to have to buy a new phone (i.e., theft or damage) it would be another moto-g. Don’t waste $600 on a phone that does exactly the same thing a $150 phone does.
Consider the Coolpad Arise on Scratch Wireless. The phone is $100 and after that the phone service is WiFi first with free txting away from WiFi. Monthly voice pass is $25 but if you don’t want to pay anything you don’t have to for that month or year … you can select $2/24hr packages as well. It runs on KitKat 4.4 and is quite capable. The network is Sprint 3G which for some people does not have strong coverage. I will try the app to see how well it works
It is a solid device for its price. There are some drawbacks but those depend largely on how you use it. If you don’t want to run taxing apps, e.g. latest games, then you will probably do just fine with it.
It took Motorola a while to push Android 5 out and my next phone will probably not be a Motorola anymore because of that.
Mr. Brinkmann:
I appreciate your feedback.
Thank You,
i
As long the certificates can easily faked in Android or comprimised by DNS attacks such BIND, redirects and others it doesn’t matter much if we using Android Firewalls like AFWall+ (iptables), local/http proxys or VPN’s. Over 22.000 apps or more affected by this even such popular apps like Es Explorer (100+ mio downloads) and others. https://samsclass.info/128/proj/popular-ssl.htm
Tcpdump also logs host names (included in any AOSP as binary).
I don’t understand the first sentence. Seems to me “it DOES matter”. Possible BIND attacks and possible certificate spoofing are “maybe, might happen someday” cases. Proxying the traffic does provide benefit in handling the “happening right here, right now” cases.
No rating, Martin? :)
Did not run on my device, so no ;)
This is a great article, Martin. I have not heard of this research or app before. You have much to add to our collective store of Android technical information and I hope you continue to do research on Android issues like this.