Do you know which data breaches you have fallen victim to?

In today's digital landscape, the security of personal information is an ever-present concern. The ubiquity of data breaches raises questions about the extent to which identities are exposed and vulnerable. While high-profile incidents involving companies like Optus and Medibank may be familiar, the broader landscape of data breaches remains largely hidden from public view, perpetuating a sense of uncertainty and potential danger.
Fortunately, the diligent work of online security expert Troy Hunt has yielded a valuable resource: "Have I Been Pwned?". This powerful platform, utilized by governments, security services, and law enforcement agencies, enables individuals to assess the impact of data breaches on their personal information. By leveraging Hunt's extensive database, they invite you to explore the depths of your digital vulnerabilities and gain a clearer understanding of the risks involved.
When I tried to see if the site was working, I realized that I had fallen victim to this type of breach twice when I queried my own e-mail address. In digital security, it's hard to know who you can trust. Therefore, if you want to use the site, I recommend that you test with an e-mail address that you no longer use.
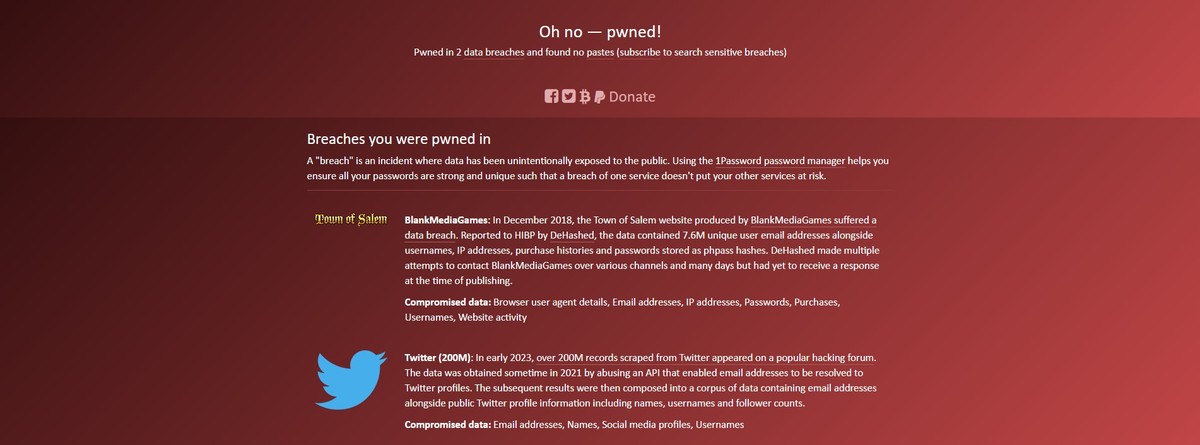
Have you been involved in data breaches?
In a world where data breaches occur with alarming frequency, it is crucial to comprehend the consequences of these incidents on personal lives. By utilizing the comprehensive "Have I Been Pwned?" database, they offer you the opportunity to unveil the breaches that have compromised personal information.
This repository, developed through collaborations with various organizations, sheds light on the hidden breaches that have implicated you, often without your knowledge. By exploring the breached data connected to your identity, you can gain insights into the potential risks and take proactive steps to protect yourself.
Understanding the reach of leaked information
To grasp the magnitude of leaked information circulating online, a visual summary is presented that illustrates the scope of data breaches. Through this visualization, you can gain a clearer understanding of the vast amount of compromised data that threatens privacy. Each breach represents a piece of the puzzle, interconnected with others, and collectively forming a mosaic of compromised information.
This visualization provides a sobering glimpse into the sheer scale of stolen data and underscores the importance of implementing robust security measures to safeguard personal information.
The mosaic effect
Beyond individual breaches, there exists a concerning phenomenon known as "the mosaic effect." Cybercriminals can combine fragments of stolen data from multiple breaches to create a more comprehensive and detailed profile of your identity. This process allows them to piece together various aspects of personal information, which can lead to identity theft, financial fraud, and other forms of malicious activity.
Recognizing the mosaic effect emphasizes the need for heightened vigilance in protecting data and underscores the importance of employing strong security practices to mitigate the risks posed by data breaches. So think twice before entering your e-mail account on a site that has not proven to be secure.
Advertisement
















This is just more hyperbole and harem-scarem from the OP.
Back in the day, ‘Mr. Martin’s – ghacks’ led a concerted effort, through his many professional associates to teach folks how to secure ones system.
We ol’tymers can see through this ‘click-bait-nonsense’
11r20 From TX
Quoting the article, “In digital security, it’s hard to know who you can trust. Therefore, if you want to use the site, I recommend that you test with an e-mail address that you no longer use.”
I don’t quite understand. Either you trust ‘Have I been pwned?’ either you don’t, “testing” will provide no information in terms of trust, maybe will it in terms of reliability if the analysis turns out to be positive, but not otherwise. The statement seems to me as conducted by upside-down logic.