Less CloudFlare captchas with Privacy Pass
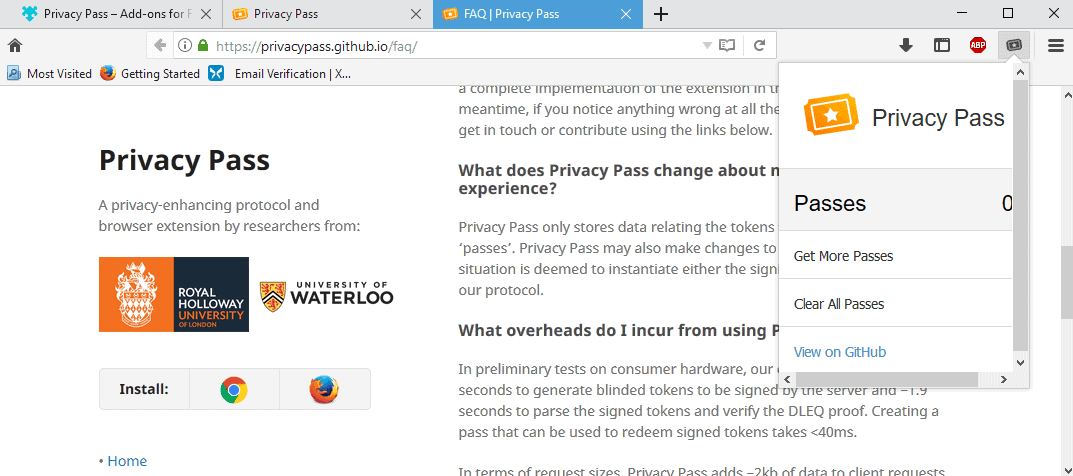
Privacy Pass is a new browser extension for Mozilla Firefox and Google Chrome to reduce the number of captchas that legitimate users get when they access CloudFlare protected properties on the Web.
CloudFlare protects a large part of the Internet, and that is why the company's captcha solutions designed to determine whether a visitor is a human or a bot are found on many different sites.
The current system throws a captcha at users regularly when they visit different sites. It is not a "prove once that you are human and you are done" kind of system.
Privacy Pass is not the first browser extension of its kind. The browser extension CloudHole came out in 2016, and while it is still available for Firefox, it has not been updated for nearly a year.
A more recent extension is Cloudflare Privacy Pass. It was based on the challenge bypass specification, and while it has been pulled, Privacy Pass appears to use the same interface and icon.
Challenge Bypass Extension
Challenge Bypass Extension is available for Firefox and Google Chrome. The extension works on websites using a "blind signature" protocol, and reduces the number of captchas that are shown to users by gaining tokens when completing captchas that are spent to pass future challenges.
The "blinding" procedure means that signed and redeemed tokens are cryptographically unlinkable from the server perspective and, as such, are suitable for usage in conjunction with external privacy measures (such as VPNs).
Privacy Pass has been developed by members of the Royal Holloway University of London, and the University of Waterloo.
Cloudflare supports Privacy Pass currently, and clients get 30 signed tokens for each captcha that is solved in the browser while the extension is enabled.
This reduces the number of captchas displayed to users significantly, and is probably most appealing to users who connect to VPN networks, Tor, or are assigned IP addresses with bad track records.
Privacy Pass stores data locally that relates to the created tokens. The extension adds an icon to the browser's toolbar that lists a -- somewhat broken -- interface right now listing the number of available passes (before another captcha needs to be solved). The "get more passes" link opens the project's site on GitHub, and the only other option is to clear the available passes.
Check out the FAQ for additional details.
Closing words
Privacy Pass improves web browsing for Internet users who run into CloudFlare captchas regularly. Tor users are probably prime candidates for the extension, but certain VPN IP addresses and regular IP addresses may throw captchas fairly regularly as well.


























The extension was working just fine, then stopped working abruptly. You get the tokens but still have to put in the captchas every time…
I still get captchas with this, but less without it, just as advertised: “reduce the number of captchas”
I guess some folks can’t read, and likewise can’t do captchas well.
it doesn’t work, i still get the captchas and not only that, but it’s not like u can click on the extension and you don’t have to do the captchas.
worthless
Here’s Tor dev response.
https://trac.torproject.org/projects/tor/ticket/24321
Nice read.
Well, that was shortlived: https://imgbox.com/Qy4LQvpk
hasn’t been updated for a yer but we def need to publish an article about it to encourage ppl use it.. Go Germany!
Don’t like the sound of that sentence, “Privacy Pass stores data locally that relates to the created tokens”. Presumably the data will have to be retained which implies a forthcoming privacy issue if it can be used to track users.
https://privacypass.github.io/protocol/
> Scenario 7: “This is basically our scheme”
So they have worked around the following problems
– scenario 1 – Linkability
– scenario 2 – Malleability
– scenario 3 – Redemption hijacking
– scenario 4 – Tagging
– scenario 5 – only one redemption per issuance
– scenario 6 – Bandwidth
Although this is not finished, the DLEQ needs more work from the quick scan I did. I am also not an expert :)
I did however, find absolutely no privacy policy on github nor AMO
Well, that’s good news at least. I don’t come across that many captchas, but I installed the extension anyway to see how it performs.