Five Tips for the disk encryption software DiskCryptor
With all the TrueCrypt drama, I made the decision to switch my secondary hard drive to the disk encryption software DiskCryptor.
It is not clear if TrueCrypt development will continue after the audit finishes, and while it is likely that the devs have posted the message that the software is insecure on the official project website, it has not been confirmed until now.
I have been using DiskCryptor on my system drive for a while and it worked really well for that purpose. While I had to purchase a new hard drive to migrate my second hard drive encrypted with TrueCrypt to the new software -- something which I wanted to do anyway because it is an old drive -- I decided that it was worth the trouble.
TrueCrypt as you may know does not offer options to decrypt none system drives which meant that I had to connect both drives at the same time to the computer to transfer all files from the old to the new drive.
Once done, I started the encryption process which tool several days to complete. I'm not sure why it took this long -- I only got transfer speeds up to 20 Mbit/s during the process regardless of whether the PC was busy or idle.
The following list is a selection of tips that you may find useful if you have never worked with DiskCryptor before and are considering using it.
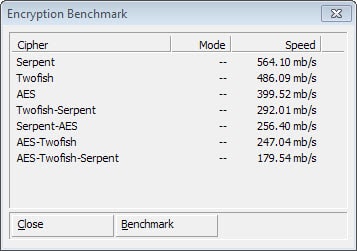
1. Before you encrypt, benchmark
DiskCryptor supports several encryption algorithms. While you may be inclined to pick the first one, AES usually, and stick with it, you may want to benchmark the drive using different algorithms to find one that is best working for you.
To do so, select Tools > Benchmark from the menu. The program will test all encryption algorithms and display the speed of each in its interface.
While you should not expect the advertised transfer rates, it may be in your best interest to select a fast algorithm as opposed to one that finishes in the bottom half.
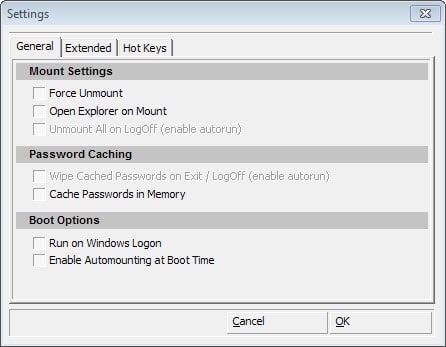
2. Disable Auto-Mounting
Auto-Mounting may be a comfortable feature as it mounts the disk in question automatically when you start your system. This may work well under certain circumstances, say, you have encrypted your system partition as well so that it is still necessary to enter a password before it becomes available on boot.
If that is not the case, or if you prefer to mount the disks of the system manually instead, then it is advised to disable the feature.
You do so with a click on Tools > Settings > General > Enable Automounting on Boot Time.
3. Backup headers after the encryption process
The headers of the disk are important to determine whether a disk is encrypted or not. If headers get corrupt or modified in any way, you may no longer be able to decrypt the disk which in turn means that you won't be able to access your data on the drive anymore.
To avoid this, it is highly recommended to backup the disk header of each drive that you have encrypted and store it in a safe location.
Make sure you do not store it on one of the encrypted drives. Good options are to store it on a Flash drive or even your smartphone. Header files have a size of about 2 Kilobyte.
Select Tools > Backup Header to do so. The header of the selected disk drive will be backed up. Repeat the process for each drive.
4. Create a Windows Live CD and integrate DiskCryptor
A Live CD may be the only option to recover a system that won't boot anymore. This is especially the case if it is your only PC. While you can try to use recovery options built-in to the Windows operating system, you won't be able to restore the disk header which may be necessary.
That's why it is recommended to create a Live CD and integrate DiskCryptor on it so that you can run it and recover the encrypted hard drive.
This works only if you have backed up headers before so make sure that is the case before you continue.
Check out the wiki that details how you can create Live CDs (BartPE or WinBuilder) and add DiskCryptor to it.
5. Using the same password will auto-mount all drives
If you have encrypted a system partition and secondary hard drive with the same password, you only need to enter it once during start of the PC.
The secondary drive will be automatically mounted using the password as well so that you do not have to do so manually.
Now Read: How to encrypt partitions using DiskCryptor



















Thanks Martin great info.
It took 6 hours to encrypt 1 terabytes USB 3.0 on AES with AMD FX-8350 16 gigs ram. It was doing about 40 megs a sec.
Hello.
What is more secure and faster Veracrypt or Diskcriptor?
Veracrypt is based on Truecrypt, which was independently audited and found to be generally secure. Neither Veracrypt itself or Diskcryptor have been independently audited. I am using Veracrypt because it’s the spiritual successor to TC, it is very similar to use, and it can mount my older external drives encrypted with TC.
Try both and choose which one is best for you.
If you have Core i 3-5-7 CPU , using AES encryption will be 7 times faster then any other….. You just have to be sure in settings you have ON the option Hardware encryption…..
Useful article, thanks. I’ve recently migrated to DiskCryptor from TrueCrypt. One question: Is tip 4 in your article only applicable if I’ve encrypted a system drive? I only have non-system drives and partitions encrypted.
Well it is not limited to that but you can as well format the partition that is not encrypted, install a new Os on it and DriveCryptor afterwards to regain access to the encrypted partitions.
Hi,
If the previous comment goes through – fail.
I see that Martin has already discussed VeraCrypt.
Have a great day.
Gus
I Totally AGREE with all the above-stated comments.
I am Holding on to TrueCrypt until the verdict is in!
Thank You,
i
i’m still sticking with truecrypt until there’s 100% verifiable proof to change my mind.
There is a lot of hype and speculation but see Gibson Research’s article– https://www.grc.com/misc/truecrypt/truecrypt.htm
I have used TrueCrypt for years and plan on continuing unless something bad turns up in the current ongoing audit.
I’ve tried Diskcryptor on my old system partition and it worked quite well. But after upgrading to a new laptop recently, I’ve decided to return to Truecrypt. I have countless external HDDs and thumb drives with Truecrypt encryption and I’ve always found it very reliable and trustworthy.
I take the recent announcement as a eccentric farewell and “f*ck it” by the developers of TC. There is still no good reason to distrust the security of TC encryption and I will stick with it. I look forward to the fork of TC and wish them well.