Microsoft Security Bulletins For December 2012 Released
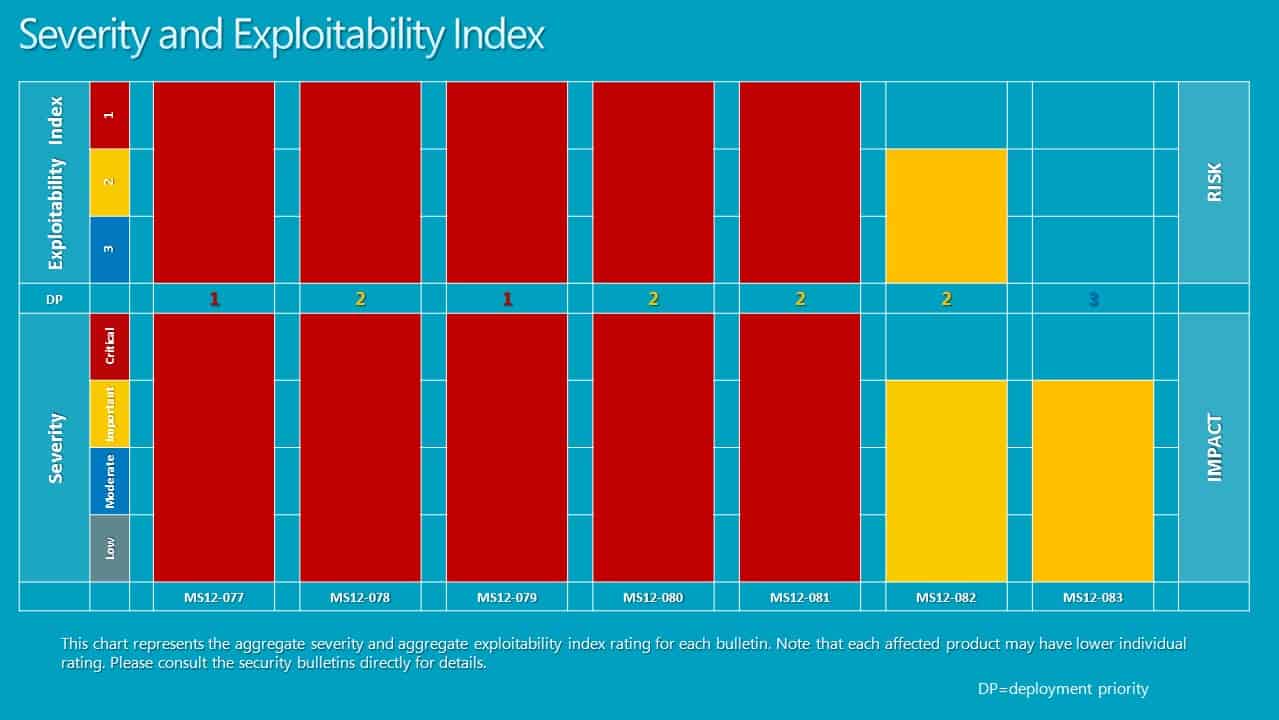
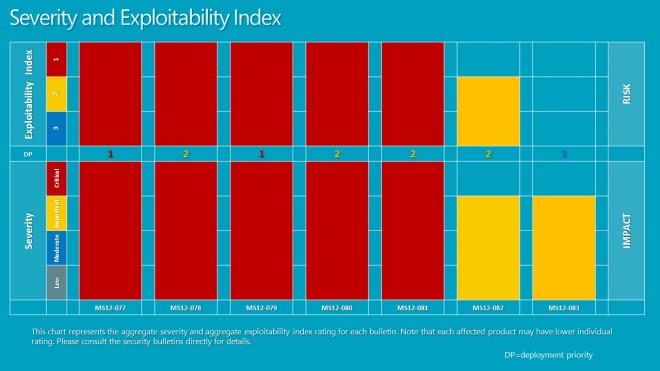
The last Patch Tuesday of the year has arrived and it brings along seven security bulletins that fix vulnerabilities in Microsoft products. Five of the seven bulletins have a maximum severity rating of critical which means that there is at least one Microsoft product that is affected critically by them.
The bulletins address a total of 12 vulnerabilities in Microsoft Windows, Microsoft Office and Microsoft Server software. Microsoft recommends to focus deployment on the MS12-077 and MS12-079 vulnerabilities first affecting Internet Explorer and Microsoft Word before deployment of the other patches on affected systems.
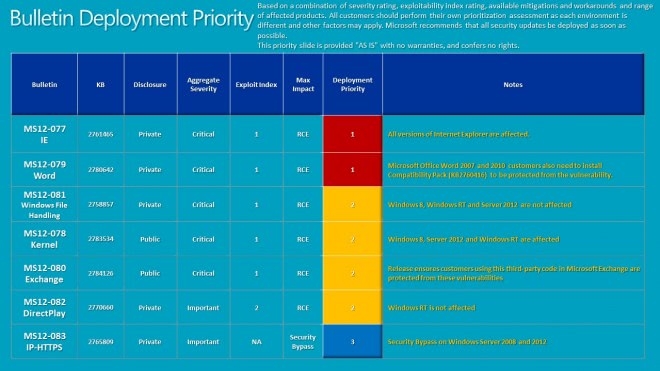
Check out the bulletin deployment priority guide below for suggestions on how to deploy the bulletins on affected computer systems.
- MS12-077 - All versions of Internet Explorer are affected
- MS12-079 - Microsoft Office Word 2007 and 2010 customers need to install Compatibility Pack KB2760416 to be protected from the vulnerability
- MS12-081 - Windows 8, Windows RT and Server 2012 are not affected
- MS12-078 - Windows 8, Server 2012 and Windows RT are affected
- MS12-080 - Protects Microsoft Exchange customers from the vulnerability
- MS12-082 - Windows Rt is not affected
- Ms12-083 - Security bypass on Server 2008 and 2012.
- MS12-077 Cumulative Security Update for Internet Explorer (2761465) - This security update resolves three privately reported vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-078 Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution - (2783534) - This security update resolves one publicly disclosed vulnerability and one privately reported vulnerability in Microsoft Windows. The more severe of these vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a malicious webpage that embeds TrueType or OpenType font files. An attacker would have to convince users to visit the website, typically by getting them to click a link in an email message that takes them to the attacker's website.
- MS12-079 Vulnerability in Microsoft Word Could Allow Remote Code Execution (2780642) - This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted RTF file using an affected version of Microsoft Office software, or previews or opens a specially crafted RTF email message in Outlook while using Microsoft Word as the email viewer. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-080 Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution (2784126) - This security update resolves publicly disclosed vulnerabilities and one privately reported vulnerability in Microsoft Exchange Server. The most severe vulnerabilities are in Microsoft Exchange Server WebReady Document Viewing and could allow remote code execution in the security context of the transcoding service on the Exchange server if a user previews a specially crafted file using Outlook Web App (OWA). The transcoding service in Exchange that is used for WebReady Document Viewing is running in the LocalService account. The LocalService account has minimum privileges on the local computer and presents anonymous credentials on the network.
- MS12-081 Vulnerability in Windows File Handling Component Could Allow Remote Code Execution (2758857) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user browses to a folder that contains a file or subfolder with a specially crafted name. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-082 Vulnerability in DirectPlay Could Allow Remote Code Execution (2770660) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker convinces a user to view a specially crafted Office document with embedded content. An attacker who successfully exploits this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-083 Vulnerability in IP-HTTPS Component Could Allow Security Feature Bypass (2765809) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow security feature bypass if an attacker presents a revoked certificate to an IP-HTTPS server commonly used in Microsoft DirectAccess deployments. To exploit the vulnerability, an attacker must use a certificate issued from the domain for IP-HTTPS server authentication. Logging on to a system inside the organization would still require system or domain credentials.
Microsoft Surface users may also notice improvements after the update. It increases the Wi-Fi reliability of Surface, improved connectivity and performance including support for access point names that use non standard ASCII characters and reduction in scenarios resulting in limited WiFi connectivity.
Updating
Updates are as usual available via Windows Update or Microsoft's Download Center. The download center is ideal for deployment on multiple systems, Windows Update if you only need to patch a single system to protect if from exploits targeting the vulnerabilities.
You can download the December 2012 Security Release ISO image from the Download Center which includes all the bulletins released by Microsoft.
Advertisement
















The full list of updates from last updates :
MS12-077/KB2761465 – Cumulative Security Update for Internet Explorer (Microsoft Windows, Internet Explorer). This critical update for IE 9 and 10 resolves three privately reported vulnerabilities in Internet Explorer. There is no severity rating for IE 6, 7 and 8. It affects all versions of Windows except the Server Core installation of Windows Server 2008, 2008 R2 and 2012.The most severe vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. Actual impact ranges from moderate for Windows Server 2008, 2008 R2 and 2012 to critical for Windows Vista, Windows 7, Windows 8 and Windows RT. There is no severity rating for systems running Windows XP.
MS12-078/KB2783534 – Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (Windows XP SP3, Server 2003 SP2, Vista SP2, Server 2008 SP2, Windows 7/Windows 7 SP1, Server 2008 R2/Server 2008 R2 SP1, Windows 8, Windows RT, Server 2012. Includes Server Core installations). This update is rated critical for all versions of Windows except Server Core installations, where it is rated important. It addresses one publicly reported and one privately reported vulnerability, both of which have to do with font parsing (OpenType and TrueType) and the way kernel-mode drivers handle objects in memory. The vulnerabilities can allow remote code execution in all versions of Windows except Server Core installations, where they can allow elevation of privilege.
MS12079/KB2780642 – Vulnerability in Microsoft Word Could Allow Remote Code Execution (Microsoft Office 2003 SP3, Office 2007 SP2 and SP3, Office 2010 SP1, Microsoft Word Viewer, Microsoft Office Compatibility Pack SP 2 and SP3, SharePoint Server 2010 SP1, Office Web Apps 2010 SP1). This critical update resolves a privately reported vulnerability in Microsoft Office that could allow remote code execution if a user opens a specially crafted RTF file using an affected version of Microsoft Office software, or previews or opens a specially crafted RTF email message in Outlook while using Microsoft Word as the email viewer. This vulnerability is in Word, not Outlook, but Outlook is affected when Word is the email reader (which is the default in Outlook 2007 and 2010). This vulnerability does not affect Office for Mac (2008/2011), Word 2013/2013 RT or Office Web Apps 2013.
MS12-080/KB2784126 – Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution (Exchange 2007 SP3, Exchange 2010 SP1 and SP2). This security update resolves publicly disclosed vulnerabilities and one privately reported vulnerability in Microsoft Exchange Server. The vulnerabilities are actually in Oracle Outside In libraries (third party code). The most severe vulnerabilities occur in Microsoft Exchange Server WebReady Document Viewing and could allow remote code execution. It is rated critical for all affected software. This update also contains non-security related functionalities. This does not affect Exchange Server 2003 SP2.
MS12-081/KB2758857 – Vulnerability in Windows File Handling Component Could Allow Remote Code Execution (Windows XP SP3, Server 2003 SP2, Vista SP2, Server 2008, SP2, Windows 7, Server 2008 R2 and Server 2008 R2 SP1, including Server Core installation). This security update resolves a privately reported file name parsing vulnerability in Microsoft Windows that could allow remote code execution if a user browses to a folder that contains a file or subfolder with a specially crafted name. The attacker can gain the same rights as the currently logged on user. This is rated critical for all affected versions of Windows. It does not affect the final release versions of Windows 8, Windows RT or Server 2012; however, it does affect the release preview and release candidate versions of Windows 8 and Server 2012.
MS12-082/KB2770660 – Vulnerability in DirectPlay Could Allow Remote Code Execution (Windows XP SP3, Server 2003 SP2, Vista SP2, Server 2008 SP2, Windows 7 and Windows 7 SP1, Server 2008 R2 and Server 2008 R2 SP1, Windows 8, Server 2012 except Server Core installations). This security update resolves a privately reported vulnerability in Microsoft Windows that stems from the way the DirectPlay component handles specially crafted content. The vulnerability could allow remote code execution if an attacker convinces a user to view a specially crafted Office document with embedded content. The attacker could gain the same rights as the currently logged on user. This does not affect Windows RT nor the Server Core installation of Server 2008, 2008 R2 and 2012.
MS12=083/KB2765809 – Vulnerability in IP-HTTPS Component Could Allow Security Feature Bypass (Windows Server 2008 R2 and Server 2012, including Server Core installations). This security update resolves a privately reported vulnerability in Microsoft Windows that could allow security features to be bypassed if an attacker presents a revoked certificate to an IP-HTTPS server commonly used in Microsoft DirectAccess deployments. The problem is with the way some versions of Windows check the validity of certificates. The attacker must use a certificate issued from the domain for IP-HTTPS server authentication. This is rated important for the affected software. It does not affect any Windows client operating systems and also does not affect Server 2003 with SP2 or Server 2008 with SP2 (including Server Core installation).
Other Updates/Releases
When it comes to non-security updates, this is a heavy month. There are eighteen updates in addition to the usual update to the MSRT.
KB2506143 – Windows Management Framework 3.0 for Windows 7 and Windows Server 2008 R2. This update provides updated management functionality for Windows 7 and Windows Server 2008 R2. Windows Management Framework 3.0 includes Windows PowerShell 3.0, WMI, and WinRM 3.0, along with other management features.
KB2506146 – Windows Management Framework 3.0 for Windows Server 2008. This update provides updated management functionality for Windows Server 2008. Windows Management Framework 3.0 includes Windows PowerShell 3.0, WMI, and WinRM 3.0, along with other management features.
KB2607607 – Language Packs for Windows 8. This language pack adds support for over forty languages to Windows 8. It includes updates for both x86 and x64 systems, and individual languages can be installed separately. After you install this language pack, you can change the display language to the one you just installed, by swiping in from the right edge of the screen (if you’re using a touchscreen) or pointing to the upper-right corner of the screen and moving the mouse pointer down(if you’re using a mouse) and tapping or clicking “Search.†Enter “languageâ€, choose “Settings†and then tap or click “Language.†Select the installed language pack, and then tap or click “Move up†until it’s at the top of the list. Sign out and then sign back in to finish.
KB2607607 – Language Packs for Windows RT. This language pack adds support for 10 languages to Windows RT. It’s installed in the same way as the one described above for Windows 8.
KB2748349 – Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP. This update addresses various issues in many versions of Windows, and may require a restart of the computer.
KB2757007 – Update Rollup for Windows Small Business Server 2011 Essentials. This update resolves issues in Windows Small Business Server (SBS) 2011. It may require that you restart your computer.
KB2757011 – Update Rollup for Windows Home Server 2011. This update resolves issues in Windows Home Server 2011. It may require that you restart your computer.
KB2757013 – Update Rollup for Windows Storage Server 2008 R2 Essentials.
This update resolves issues in Windows Storage Server 2008 R2 Essentials. It may require that you restart your computer.
KB2760730 – Update for Windows 7, Windows Server 2008 R2, and Windows Server 2008. This update resolves issues in Windows 7 and Windows Server 2008/2008 R2. It may require that you restart your computer.
KB2761494 – Update for Windows Server 2008 and Windows Vista. This update resolves issues in Windows Server 2008 and Windows Vista. It may require that you restart your computer.
KB2771431 – Update for Windows RT. This update resolves issues in Windows RT. It may require that you restart your computer.
KB2774195 – Update for Windows 8, Windows RT, and Windows Server 2012. This update resolves issues in the latest versions of Windows. It may require that you restart your computer.
KB2769166 – Update for Microsoft .NET Framework 3.5 on Windows 8 and Windows Server 2012. This update enables Windows 8 to repair a damaged Windows 8 machine or enable a feature that has had its payload removed.
KB2779444 – Update for Microsoft Camera Codec Pack for Windows 8 and Windows RT. This update enables the viewing of a variety of device-specific file formats and will allow supported RAW camera files to be viewable in applications in Windows 8 and Windows RT. It may require that you restart your computer.
KB2779562 – Update for Windows This update resolves issues caused by revised daylight saving time and time zone laws in several countries and enables your computer to automatically adjust the computer clock on the correct date in 2012. It may require that you restart your computer.
KB2779768 – Update for Windows 8, Windows RT, and Windows Server 2012. This is another update to resolve issues in Windows. It may require that you restart your computer.
KB2780541 – Update for Windows 8, Windows RT, and Windows Server 2012. This is another update to resolve issues in Windows. It may require that you restart your computer.
KB931125 – Update for Root Certificates for Windows 8, Windows Server 2012, Windows 7, Windows Server 2008, Windows Vista, and Windows XP. This is an update to the list of root certificates on your computer to conform to the list that is accepted by Microsoft as part of the Microsoft Root Certificate Program. After you install this update, you may have to restart your computer. Note that once you have installed this item, it cannot be removed.
KB890830 – Windows Malicious Software Removal Tool – December 2012 KB890830 – Windows Malicious Software Removal Tool – December 2012 Internet Explorer Version. These are the monthly updates to the Windows MSRT, which will check your computer for infection by specific, prevalent malicious software (including Blaster, Sasser, and Mydoom) and help remove any infection that is found.
Updates since the last Patch Tuesday
Quite a few non-security updates have been issued between the November and December Patch Tuesdays.
KB2771431 – Update for Windows 8 and Windows Server 2012. This update resolves issues in Windows 8 and Server 2012, including an issue with high CPU usage when running a Windows Update applicability scan, duplicate CBS entries when running a Windows Update applicability file, a scenario where updates are not installed, a scenario where drivers are not updated, and other issues pertaining to Windows Update problems. It may require that you restart your computer.
KB2762895 – Update for Windows 7, Windows Server 2008 R2, and Windows Server 2008. This update resolves a set of known application compatibility issues with Windows. It may require that you restart your computer.
KB2764462 – Update for Windows 8 and Windows Server. This update resolves a set of known application compatibility issues with Windows 8 and Windows Server 2012 and improves the user experience. For a complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article for more information. It may require that you restart your computer. (http://support.microsoft.com/kb/2764462)
KB2774223 – Dynamic Update for Windows 8 and Windows Server 2012. This update under Windows 8 Dynamic Update Category is used by Windows 8 and Windows Server 2012 to obtain critical driver, component and setup improvements during initial setup. (http://support.microsoft.com/kb/2774223)
KB2774225 – Dynamic Update for Windows 8 and Windows Server 2012. This update is another in the the Windows 8 Dynamic Update Category that is used by Windows 8 and Windows Server 2012 to obtain critical driver, component and setup improvements during initial setup. (http://support.microsoft.com/kb/2774225)
KB2777294 – Update for Windows 8. This update resolves issues in Windows 8, wherein the Program Compatibility Assistant dialog box appears when you start a desktop app from the Autoplay dialog box. For a complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article for more information. After you install this item, you may have to restart your computer. (http://support.microsoft.com/kb/2777294)
KB2784532 – Update for Windows 8. This update resolves issues in Windows pertaining to licensing terms on an OEM version of Windows 8. It may require that you restart your computer. (http://support.microsoft.com/kb/2784532)
KB947821 – System Update Readiness Tool for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista [November 2012]. This tool is being offered because an inconsistency was found in the Windows servicing store which may prevent the successful installation of future updates, service packs, and software. This tool checks your computer for such inconsistencies and tries to resolve issues if found.
Thank you very much for that list, it will save me *a lot* of time :)
Will you write such a list every month (maybe you’ve done in the past, but it’s the first time I see it…)?, or is there some website I can check for it? Thanks again.
@Miguel
I’ll try to put the full list every month :-)
@ilev
Thanks :)
@Miguel,
Yes, he does it every month. You can find them here :
https://www.ghacks.net/index.php?s=Microsoft+Security+Bulletins
@Sina
I’m sorry… …. I was refering to the list “ilev” posted on a previous comment (Sorry Martin… ;) ), that includes non-security updates and other updates posted before the patch tuesday, because those ones are not as easy to find them all as security updates.
I already knew about GHacks posts about Microsoft security updates every month, and I read them, instead of the security bulletin on the Microsoft web site, because since some months ago MS Security Bulletins pages just show a blank page if you don’t allow JavaScript to run (any other parts I usually visit on the MS website work well even without JavaScript…).
Thanks ilev.
btw – one of the optional updates I got was was the “Bing Desktop v1..1” which sounds like MSFT spyware/spamware…..what a joke….all the dopes with default auto-updating are in for a surprise.
@ YB –
There’s nothing wrong with Bing search results. But can’t you see the difference between using various search engines (including Bing) and having the “Bing Desktop” pushed onto your installation through auto-updates? Wow.
@Miguel
I agree and just as well I install updates manually. Why on earth are they pushing Bing Desktop through Windows Update?!?
@Tim
Maybe Bing is losing too much “market share” to Google due to the Google products getting installed almost everywhere with “bad tactics” like installing them alonside with 3rd party software. I think that’s bad, most users I do computer support for them (friends, neighbours…) don’t even know how that “Google Toolbar” got installed on their Internet Explorer, or think is part of the standard Search box of Internet Explorer…!
So maybe this is Microsoft “counter-attack”. They’ll get “Bing Desktop” installed on every Windows computer running “Automatic updates” (almost all average home users) :D …. …. Being serious, I don’t really know why they’re installing it without any user notification. In my opinion, it’s wrong to install it in such a way, it should be an “optional update”, just like “Skype” that has been listed on Windows Update web site for a few months now.
@ilev
KB2748349 doesn’t appear to be for Windows XP, but for all others listed on the entry on your list.
Anyway, I must say THANKS again. Since the time of my other comment, I’ve already found and got all the updates of this month!
What’s wrong with Bing? At least it doesn’t display loads of ads like Google does when you search for something
Thanks Martin, For your explanation of this mounts updates. This mouth I got 15 updates. Also i got a update for base certificates KB931125.
After the updates, do you see any problem with Flash? Some times it loads, some times it doesn’t… I still can’t find what change I made and it doesn’t play. I’m talking about Desktop IE, of course. I tried everything, even Reset IE. It must have something to do with rights etc, but I can’t figure what exactly.
Incidentally, truly thanks for Internet Download Manager, guys! I’ve set it nicely, yesterday, and it’s damn perfect!
On which version of Windows and in which browser are you experiencing the issues?
Well, it’s O.K. because I disabled again IE10 due to crappy font rendering. You know, they applied on IE10 desktop the same font rendering of Metro and Metro apps… Which in my understanding, it’s only good if you’re using tablets or small laptops ( I’ve seen in stores and it didn’t look as bad as on my 1920×1080 PC resolution ).
So… No worries.
Just tested it on W8 Pro and it is working fine for me on IE10 desktop. Have you checked the installed add-ons in IE10? It can also be a security setting in the browser. If you do not mind, try resetting the settings or adding the website to the trusted sites.
lol! I forgot vital info… Windows 8 – Desktop IE 10. I’ve problem with the built-in Flash after the updates. As I said, I even tried reset, but nothing works. Just one time I made it work by enabling Smartfilter, but it was a step while I was trying many different ones. I mean, I don’t eventually know what has broken Flash. Any idea what kind of protection can cause this issue?
When I’m on a page, say, Liveleak, I don’t even see the Flash placeholder until I press “combatibility mode”. Then, I just see the placeholder with “blocked” icon or something. I’m saying again, I made it work once. Then I disabled Protected Mode, and now it doesn’t work anymore.
I really don’t understand why can’t I figure it out.
After the updates, do you any problem with Flash? Some times it loads, some times not… I still can’t find what change I made and it doesn’t play. I’m talking about Desktop IE, of course. I tried everything, even Reset IE.
Incidentally, truly thanks for Internet Download Manager, guys! I’ve set it nicely, yesterday, and it’s damn perfect!
MS12-077 – All versions of Internet Explorer are affected
Again those Microsoft monkeys calling themselves programmers copied insecure code
from IE4 through all versions of IE up to IE10.