Microsoft: 44 million Microsoft accounts use leaked passwords
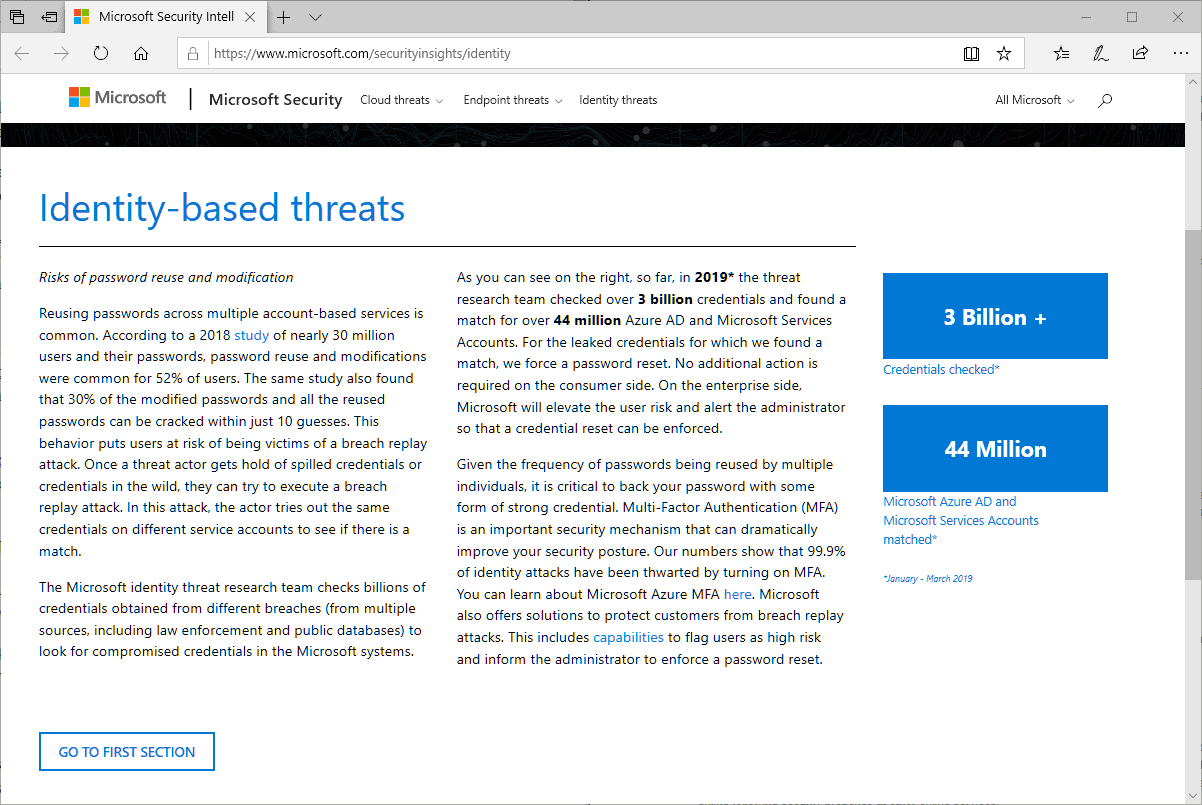
Microsoft ran a password-reuse analysis on over three billion company accounts in 2019 to find out how many of the used password were in use by Microsoft customers.
The company collected password hash information from public sources and received additional data from law enforcement agencies, and used the data as a base for the comparison.
An analysis of password use in 2016 revealed that about 20% of Internet users were reusing passwords, and that an additional 27% were using passwords that were "nearly identical" to other account passwords. In 2018, it was revealed that a large part of Internet users were still favoring weak passwords over secure ones.
Companies like Mozilla or Google introduced functionality to improve password use. Google published its Password Checkup extension in February 2019 and started to integrate it in August 2019 natively in the browser. The company launched a new Password Checkup feature for Google Accounts on its site in 2019 as well.
Mozilla integrated Firefox Monitor into the Firefox web browser designed to check for weak passwords and monitor passwords for leaks.
Computer users who use standalone password managers may also be able to check passwords against leak databases; I have published a tutorial on how that is done in the password manager KeePass.
Microsoft has been pushing for password-less logins for a while now, and the company's password reuse study provides a reason why.
According to Microsoft, 44 million Azure AD and Microsoft Services Accounts use passwords that are also found in leaked password databases. That is about 1.5% of all credentials the company checked in its study.
Microsoft cites a study in which password use of nearly 30 million users was analyzed. The conclusion was that password reuse and modifications were common for 52% of users, and that "30% of the modified passwords and all the reused passwords can be cracked within just 10 guesses".
Microsoft will enforce resets of passwords which were leaked. Microsoft account customers will be asked to change the account password. It is unclear how the information will be communicated to affected users or when the passwords will be reset.
IT administrators will be contacted on the Enterprise side.
On the enterprise side, Microsoft will elevate the user risk and alert the administrator so that a credential reset can be enforced.
Microsoft recommends that customers enable a form of multi-factor authentication to better protect their accounts against attacks and leaks. According to Microsoft, 99.9% of identity attacks are unsuccessful if multi-factor authentication is used.
Closing Words
It is surprising that only 1.5% of all analyzed credentials were found in leaks; the study that Microsoft linked to saw password reuse and password modifications in over 50% of all analyzed passwords.
Now You: Do you reuse passwords? What is your take on the study?
And people say Windows 7 is now insecure…
The compession function (of a hashing algorithm) is designed to always resolve to the same length of hash, how could they possible know when someone makes minor changes to a password when it is designed to avoid this? Also, they must have somehow had the data before salting, then compared it with Rainbow Tables.
I would prefer they spend their time imporving Win 10 instead they spend their resources on this!
More disturbed about how Microsoft is able to obtain this data then the whole password situation.
I still don’t understand why Microsoft needs one email account or password to run properly. Currently there are more better ways to protect a whole hard disk like HD password or complete disk encryption with other third party powerful software like TrueCrypt or DiskCryptor. Anyway, the use of junk email should bypass this useless requirement if needed. 😑
A critical security update will follow so MS can install even more spyware on our devices and reset privacy settings to improve password experience enjoyment.
I wonder how many of these 44 million are inactive or “junk” accounts. Microsoft finally, just a few months ago, got around to announcing a policy of closing unused accounts, after a two year period of no logins. Anyway, the accounts in question are about 1.4 percent of all MS accounts, which is a lot better than I would have expected.
The problem is education, incorrect education that is.
People are constantly misinformed about what exactly a strong password and this is causing them to avoid best practices for convenience.
The longer the password the stronger it is. It’s that simple, it’s math.
Instead of short 8 or 16 character passwords that are impossible to remember people should be taught to start using “pass phrases” that are 16 characters or more.
“Mydogsleeps1dayaweek!” is far stronger and easier to remember than “sv<k-0si46/AC".
@Dave: ““Mydogsleeps1dayaweek!†is far stronger and easier to remember than “sv<k-0si46/AC"."
If your password consists dictionary words like that, it needs to be a lot longer than that to match the strength of a 16 character random password. Don't underestimate the power of very large rainbow tables.
So MS know’s your passwords. Is there anything they don’t spy on?
They don’t know the passwords, they simply compared password hashes.
Comparing hashes is essentially an attempted login,
and regardless of motive, it’s a serious breach of user security.
What Microsoft should have done is notify affected users,
and either obtain consent or require them to change their passwords.
Suspecting that users might have been compromised
is not sufficient to justify password hacking.
Remember when Windows 10 was first released Microsoft would steal your wifi password to “help” you?
https://www.pcworld.com/article/3068659/microsofts-killing-windows-10s-controversial-wi-fi-sense-password-sharing-feature.html
Avoid Microsoft, Google, and Apple services if you value your private data.
So, Microsoft doesn’t use salt?
Since these are leaked passwords, Microsoft can salt them before a compare.
It’s essentially an attempted login, otherwise known as password cracking.
Regardless of motive, it should not be done without user consent.
Multi factor? What do they mean? Giving my Mobile, it’s no-no for me. Fingerprint on my PC don’t have. A cheap USB device would be acceptable. Camera also don’t have. So what?
Same here.. I’d make my own email server before giving out any of my phone numbers.
Also note that Yandex is well known to lock user accounts, where they require a phone number to re-open it.
Sure, you can open a new Yandex account without a phone number, but there’s a chance they will tell you that your email got hacked and lock your account. Then they require a phone number, which is silly if you think about it, as that only helps if i gave them the a phone number when I opened the account, not after some so-called hack. And they actually said that when I went to log on:
“Your account has been hacked”
Also, the account was only a few days old and i hadn’t even used it yet. Ha..
Screw Yandex!
This has happened to me any many others. The one thing in common is we all use good VPNs, and Yandex hates that, as it cuts into their advertising revenue.
That said, that Yandex search engine sure is good though.
@pcelitist:
I agree. Any authentication scheme that requires me to provide personal information such as a phone number, or requires me to identify myself to a third party, is an authentication scheme that I am not using.
MFA can be a good thing, and it doesn’t have to require those things. It’s just a shame that so many implementations do.
Note that “passwords which were leaked” can mean that they could have been strong and only used for one site, but due to an exploit/hack they got out there.
Regardless, there are cryptographic methods to use strong yet rather memorable pass phrases, where for example you can use the same phrase for all accounts + include letters from the service/company it’s for + add a few coded numbers + repeat it three times, like this:
Google: (1)w3rsh!ngt0N”go”715(2)w3rsh!ngt0N”go”715(3)w3rsh!ngt0N”go”715
Yandex: (1)w3rsh!ngt0N”ya”251(2)w3rsh!ngt0N”ya”251(3)w3rsh!ngt0N”ya”251
Furthermore, in that example, “go” = 715 as “g” is the 7th letter in the alphabet and “o” is the 15th letter. Same method goes with that 251 for Yandex.
So in this case, all you need to remember is “w3rsh!ngt0N” and the method, for every site you use.
Obviously other methods can be used, that are even better, but that can be your secret.
@Gerhard Bohne:
Your method is a compromise between security and convenience. I encourage people to do similar things when they aren’t willing to adopt a truly strong password scheme. Ideally, though, you want a different completely random password, at least 16 characters long, for each thing that requires a password.
@John Fenderson
Your method is a compromise between security and convenience?
Actually, it’s called using your brain. Depending on software to make and store your passwords is likely more of a convenience for most folks.
Regardless, that wasn’t my specific method. That was a basic “example” of how to use “cryptographic methods”, which is a wide and deep topic.
https://en.wikipedia.org/wiki/Cryptography
Furthermore, I said that it can “obviously” be “even better”, and as such the secret methods I use are VERY secure.
The only limit is how smart one is.
That said, even if you use a “random” pass phrase, I recommend making it look like it’s coded. That way, if some hacker gets it, they may spend weeks trying to crack it, but there’s nothing there, ha.
lhaznelleW18eid17adbmal\/16ip\2=k}15adbmal\/14ip\2=k13elytsyalpsid\{12,dnatsbatlapSred11a}a10elytsyalpsid\{9,etierbtlapS eid b}b8elytsyalpsid\{7,lekniwsgnuthcaboeB6red5ahpla\}4ahpla\3elytsyalpsid\{2tsi1iebaD
“you want a different completely random password, at least 16 characters long, for each thing that requires a password”
Why?
I originally used a similar method, but the “paranoid” me came to a conclusion:
If someone is pinpointing me, with 2 or 3 leaks they will probably find my method and access every account I have.
The “normal” me was highlighting that there were no chances for that to happen.
…the paranoid me won and I now use keepass…
@normalvsparanoid
Ha, well said..
Well, if your method was similar to that sample, then it likely wasn’t good enough.
The key is, use something way out there to link the site/service to your pass code method.
And it need not all be memorable, but at least accessible, such as content found on the web.
For example, you could use the colors of the company’s logo in your code, and then even code that further.
There are endless ways to do this, and you can use somewhat different methods on different sites/services, based on yet another method related to that site/service.
But in the end using software is likely best, as telepaths can uncover most any cryptographic method.
Out of curiosity, my original method involved md5 the url, it was few years ago, so I don’t remember exactly but it was something similar to:
– example for https://www.ghacks.net:
1. md5 site url: 57c78e97c7786eaf36b117593e7747e3
2. Upper case first letter = 57C78e97c7786eaf36b117593e7747e3
3. switch position first 2 characters = 75C78e97c7786eaf36b117593e7747e3
4. brackets at the beginning and end = (75C78e97c7786eaf36b117593e7747e3)
5. dot at the end = (75C78e97c7786eaf36b117593e7747e3).
6. add the total amount of characters of the domain name = (75C78e97c7786eaf36b117593e7747e3).6
that would have been my password (or a similar one, as commented it was few years ago, I do not remember the exact rule.
My dad’s email never touched by other people, but the password ia forbidden to changing or reuse for illegaly. This is scare to me…..
If you think that’s scary, try running around in wolf infested woods at night, nude, with slabs of bloody raw meat tied to your back. Try that, I dare you.
Baloney – they’re only releasing this ‘analysis’ in an attempt to convince the feeble-minded masses to use biometric identification, from which Microsoft will have part of you.
A separate email and different password for each site and service is still the most secure and manageable method of protecting yourself.
Biometric identification is just the opposite – it’s the same password for all sites and services. You can always change one of the passwords for one site if it’s leaked – good luck changing your fingerprint, face, voice, retina, et al.
Just say no to governments and corporations insisting on any form of china-style biometric identification.
We must constantly fight for our freedom, liberty and right to live privately and anonymously in a society.
“Just say no to governments and corporations insisting on any form of china-style biometric identification.”
Here we go again, the world being infested with biometric identification is blamed on the chinese, even when it’s Microsoft doing it.
Being that I’m a criminal in the mafia, I also hate the idea of RFID tags on all our goods, as that would make it near impossible to do the work we do.
But due to our great anti-RFID campaign, we got religious folks into thinking it was the “mark of the beast”, and thus those suckers do most of that work for us for free, and even donate large sums of money to us.
Also I hate the idea of a cashless system, as that will kill our counterfeiting ring.
@Heathcote, I don’t know what Microsoft’s intentions are when publishing this analysis but whatever they be remains that there are two imperative rules regarding passwords,
1- different password for each site, as you state it;
2- strong passwords.
And of course avoiding to provide a plain word when asked for a ‘secret question’ such as the name of our pet, which would be totally absurd when the password itself is strong! When reqired I provide another 32 alpha-numeric+custom ‘word’. Would be a pity someone hijacks my account by providing my pet’s name :=)
How on earth could they know? Do they not salt their hashes?!
Actually, this is a common question when Twitter and Netflix did this. The way they do it is by checking your password (that is leaked and already cracked in breaches (or was never hashed in the first place from another server), and put it through the same input that you use when you enter the password (ie Add the salt (which they know), and hash it, and compare output).
@CKing
Doesn’t that mean they would have to try every leaked password with every salt they have to get these hashes?
Is that computationally feasible?
Isn’t that the point of salt in the first place – to force the cracker (making it too consuming) to do the whole brute-forcing with each password in order to get the password-hash pairs, even if they get hold of the salt too?
Add to that the number of accounts that MS has (thus the number of salts) and you would see how daunting this is, if I understand correctly.
Not quite. They literally just look your email up, and check your password against the leaked password. That’s it. At least that’s how Netflix, Facebook, etc do it. See Brian Krebs article on this practice: https://krebsonsecurity.com/2019/08/forced-password-reset-check-your-assumptions/
Also, the assumption of password hashing is to slow down crackers, since it is fast enough for users to login, etc but you can’t brute force quickly enough. That does not matter when they only have one password to try (from the breach), although feasibly they can try all passwords found in the breach, as they don’t have to do it quickly. They can spread this out if they need to. Though, I am not aware of how Microsoft does this checking
@CKing
This assumes that they checked only for the cases where both username/password (the pair together) have been used across multiple services (or linked with the MS account somehow). In this case, you are right, it would be beyond trivial.
But I notices the summary in the link said: “Given the frequency of passwords being reused by multiple individuals, it is critical to back your password with some form of strong credential.”
This suggests that they considered using a previously hacked password by anyone. If so, I believe the point still stands. They would have to check the 3+ billion passwords multiplied by the number of salts they have (easily in the hundreds of millions IF they use it.)
Microsoft can’t be trusted. Amazon on the other hand is the most trustworthy organization ever. I know.
I love this.
Microsoft: We do research with passwords. We’re a security company now.
People with security know-how: Either your security practices are awful or your security researchers are so incompetent that they did not think of this basic security measure that should make their research impossible.
Microsoft is the biggest threat to security there is for PC users. It wouldn’t be surprising if all this password data gets sent to the government or “accidentally” leaked.
Add me to the list of surprised people. Microsoft shouldn’t be able to do this. Of course I always assumed they *could*, but it’s still rather ugly to see them admit it so casually.
@Anonymous: I was wondering this exact thing as well. That this analysis is possible strongly implies a real problem with how Microsoft is storing passwords.