Administrative Templates (admx) for Windows 10 May 2020 Update released
Microsoft has published the administrative templates for Windows 10 version 2004, the new feature update for Windows 10 that Microsoft released last month to the public.
Professional versions of Windows 10 come with a set of policies that administrators may configure using the Group Policy Editor. Administrators may extend the default set of policies by installing the Windows 10 Administrative Templates.
These templates install additional policies on Windows 10 devices. Microsoft updates the optional administrative templates every time it releases a new feature update for the operating system.
The latest at the time of writing, Administrative Templates for Windows 10 version 2004, the May 2020 Update, is now available.
All it requires is to download the 12.9 Megabyte msi file to the local system. The downloaded file may be installed directly on a target system or it may be extracted using a tool such as 7-Zip instead to take a look at the templates that it installs prior to installing them.
The templates (admx) are available for several languages including English, Russian, German, French, Spanish, Chinese, Portuguese and Polish.
Administrators who compare the number of policies against the previous version will notice that the number of included policies has decreased by about 200. The drop is caused by the removal of msedge.admx.
Administrative Templates for Windows 10 version 2004 includes the following new policies:
- Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy > Minimum Password Length Audit
- Determines the minimum password length for which password length audit warning events are issued.
- Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy > Relax minimum password length limits
- Defines if the minimum password length setting can be increased beyond the legacy limit of 14.
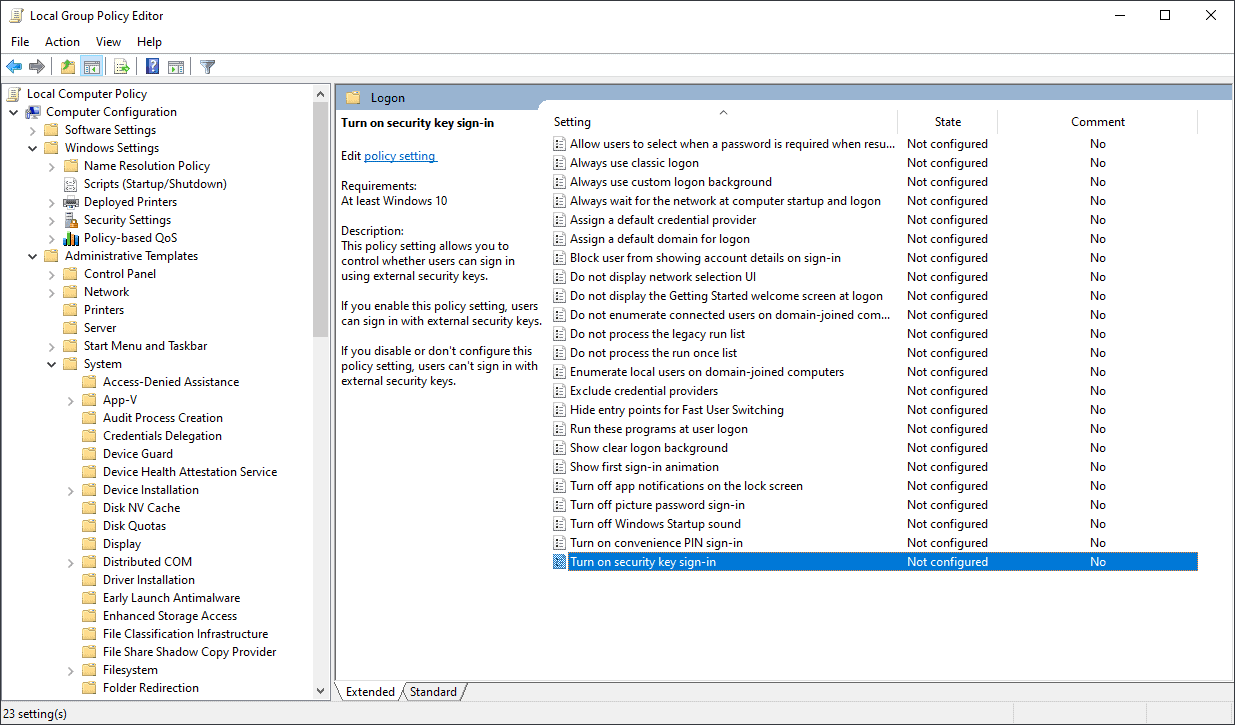
- Local Computer Policy > Computer Configuration > Administrative Templates > System > Logon > Turn on security key sign-in
- This policy setting allows you to control whether users can sign in using external security keys.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Windows Components > App Privacy > Let Windows apps access user movements while running in the background
- Specifies whether applications may access the movement of a user's head, hands, motion controllers, and other tracked objects, while they runs in the background.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Windows Components > App Package Deployment > Prevent non-admin users from installing packaged Windows apps
- Prevent the installation of packaged Windows apps by non-administrators.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Delivery Optimization > Maximum Foreground Download Bandwidth in KB/s
- Set the maximum foreground download bandwidth that the device can use across all concurrent download activities using Delivery Optimization.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Delivery Optimization > Maximum Background Download Bandwidth in KB/s
- Set the maximum background download bandwidth that the device can use across all concurrent download activities using Delivery Optimization.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Delivery Optimization > Cache Server Hostname Source
- Specifies how clients discover Delivery Optimization in Network Cache servers dynamically. Options are 1=DHCP Option 235, 2=DHCP Option 235 Force.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Internet Explorer > Configure which channel of Microsoft Edge to use for opening redirected sites
- Define which version of Chromium Edge is going to used for opening redirected sites.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Windows Components > Microsoft Defender Antivirus > MpEngine > Enable file hash for computation feature
- Microsoft Defender will compute hash values for files it scans if enabled.
- Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Windows Update > Windows Update for Business > Select the target Feature Update version
- Enable this policy to request a specific Feature Update version in future scans.
- Local Computer Policy > User Configuration > Administrative Templates > Windows Components > IME > Configure Japanese IME version
- Local Computer Policy > User Configuration > Administrative Templates > Windows Components > IME > Configure Simplified Chinese IME version
- Local Computer Policy > User Configuration > Administrative Templates > Windows Components > IME > Configure Traditional Chinese IME version
- Defines whether users may control the IME version to use in the selected language.
Microsoft removed five policies in the new administrative templates:
- Delivery Optimization > Max Upload Bandwidth (in KB/s)
- Delivery Optimization > Maximum Download Bandwidth (in KB/s)
- Delivery Optimization > Maximum Download Bandwidth (percentage)
- Windows Defender Application Guard > Allow users to trust files that open in Windows Defender Application Guard
- Windows Defender Application Guard > Configure additional sources for untrusted files in Windows Defender Application Guard
Now You: do you use policies on Windows?
…and yet one more – also on the *User* side:
Local Computer Policy > User Configuration > Administrative Templates > Internet Explorer
“Configure which channel of Microsoft Edge to use for opening redirected sites”
Hi again – I discovered one more new setting in the Windows 10 R2004 templates – it’s on the *User* side:
Local Computer Policy > User Configuration > Administrative Templates > Windows Components > Calculator
“Allow Graphing Calculator”
Thanks for being right on top of it!
Good list, thank you! However, I have a question about this remark:
“Administrators who compare the number of policies against the previous version will notice that the number of included policies has decreased by about 200. The drop is caused by the removal of msedge.admx.”
I have checked every version of the downloadable ADMX templates from Vista through Windows 10 R2004, and I have found no trace of msedge.admx in any of them. There is “MicrosoftEdge.admx”, but not “msedge.admx”. I do see that the latter is available for download separately (here: https://www.microsoft.com/en-us/edge/business/download ), but it was not bundled with the main Windows OS downloadable ADMX template package at any point. The former (MicrosoftEdge.admx) is also still included in the Windows 10 R2004 downloadable templates, so I do not think the “200 policy decrease” is applicable in this context.
Also worthy of note – all settings in the “Windows Settings” section have nothing to do with Administrative Templates, but rather the built-in security template that comes with the OS. Therefore, these new settings:
* Minimum Password Length Audit
* Relax minimum password length limits
…will only be configurable from a Windows 10 R2004 system (or Windows Server, version 2004 system), regardless of whether or not the R2004 Administrative Templates are downloaded and installed in the Central Store in Active Directory.
Please let me know if you concur with the above – I’m doing analysis work on the new R2004 changes, so I’m just trying to clarify for accuracy.
Thanks!
+1, thank you Martin.
Does anyone know or have a link that explains if installing these will overwrite previous Windows 10 policy files – and if so, will they reset them to defaults. If so, that’s painful as it can take literally weeks to carefully fine-tune policies.
The C:\Windows\System32\GroupPolicy\Machine\Registry.pol is not overridden when you install new admx files, but it’s always a good precaution to make a backup of that folder before performing updates.
@SpywareFan
Thanks – it pointed me in the right direction for further info. My PC has three:
C:\Windows\System32\GroupPolicy\Machine
C:\Windows\System32\GroupPolicy\User
C:\Windows\System32\GroupPolicy\DataStore\0\sysvol\domain.local\Policies\{***UUID***}\Machine
So it’s a lot more nuanced than that, but all the same it was a Doh! moment that triggered more digging.
Thanks for this update.