How to analyze a program's Internet connections in a minute
There are times where you want to monitor if a program connects to the Internet. Maybe you have just downloaded it and want to check if it connects to servers on the Internet.
This can be used to check if a program is phoning home for instance, or if it is making connections on its own without being initiated by you.
There are quite a few ways to monitor this, but there is none that is enabled by default on Windows. While you can make sure that no connection slips by, for instance by configuring strict outbound rules in the firewall or running a network monitor 24/7, it is often not helpful if you want to gain a quick overview as analysis and setup are usually complex time consuming processes.
I like to use Nir Sofer's CurrPorts application to check a program's Internet activity fast. While it is not as elegant as a network monitor that grabs every bit of traffic, it is very easy to use.
The program is portable and available as a 32-bit and 64-bit version. All you need to do is download it to your system, extract the archive once done, and run the single executable file that is in the target directory.
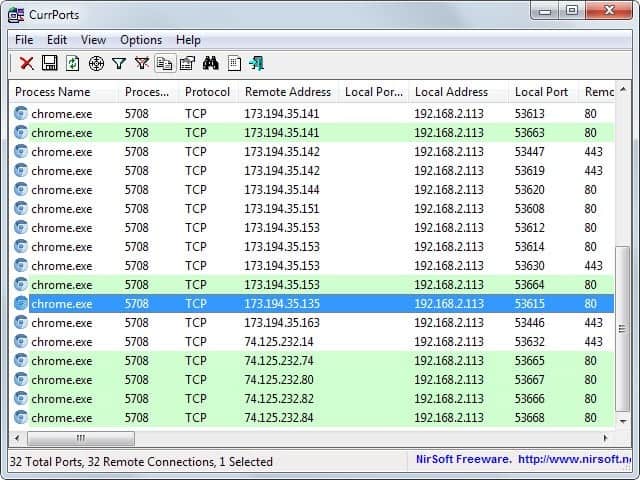
The program displays all established connections in its interface. You can easily sort the display by process name or, and that is better, drag the target icon (fourth from the left) on the application window to limit the data to it.
As you can see on the screenshot above, CurrPorts displays the remote address of every connection. It displays additional information such as the target hostname as well as time and date of the connection.
You can refresh the display manually with a click on the refresh button or hitting F5 on the keyboard, or enable the program's auto-refresh feature to have it update the data automatically in select intervals.
Once the data is displayed to you, you may want to analyze it to find out if it is legit or not. If you monitor Google Chrome for instance, you will notice that it makes many connections to Google servers regularly. In fact, all connections displayed on the screenshot above are to Google servers.
Suggested course of action
If you want to find out more about the connections that the program made, you need to look up IP addresses or hostnames.
- Use View > HTML Report All Items to export all connections to a HTML file.
- The HTML file should be opened automatically after its creation. If not, you find it in CurrPort's program directory.
- Use a service like http://ip-lookup.net/ or http://whatismyipaddress.com/ip-lookup to display ownership information.
- If you use the first service, you need to click on the Whois information link on the results page. The second service displays the relevant information right away.
- Once you have the owner of the IP address, you need to conclude whether the connection is legit or not. You may also conclude whether it is desired or not.
While that is sometimes easy to answer, for instance if a program makes a connection to a company not related to it in any way, it can be difficult at times, for instance when Chrome makes connections to Google.
You cannot use CurrPorts to find out more about those connections. You do have a few options however:
- Configure your firewall to block select IP addresses or limit outbound access of the program, and monitor if functionality is blocked after doing so.
- Use a "real" network monitor such as Wireshark to dig deeper and find out more about the connections.
- Configure the program so that at least some connections are not established anymore. If you block Chrome's Safe Browsing feature for instance, it won't establish connections anymore to test websites or files using it.
Now Read: Take control over all connections with Windows Firewall Notifier
I’m sorry if this information is available, but I couldn’t find it. I have a question though, what does it mean if something is highlighted in green? Thank you!
While I cannot say for sure, I believe that those are displayed after you hit refresh to highlight new entries.
Oh alright. Thanks bud, appreciate it.
type this in command prompt ==> netstat -b
Then use PeerBlock http://www.peerblock.com/ to prevent the application making the undesirable connections.
TCP View is a nice companion to Current Ports. Current Ports must used as an Admin (Run as Administrator), and it does have the function to create filters that will block IPs. I started using it when the ISP claimed my bandwidth was running wild at night. A quick check showed numerous connections to all sorts of crap IPs that have now been blocked. Bandwidth much better.
All though it is a good program there is no way to flag certain application as Approved Apps or DisApproved Apps. This would help me narrow down and display only new apps that I have not seen before and hence track or block them accordingly.
email them with the suggestion – they do implement them.
“If you have any problem, suggestion, comment, or you found a bug in NirSoft utility, you can send a message to nirsofer@yahoo.com“
> email them with the suggestion
It’s a “one man” Company.
I really like NirsSoft tools
Israel software btw :)
Alternate to Wireshark is Fiddler (free web debugging proxy for any browser, system or platform)
http://www.telerik.com/fiddler
Alternate to CurrPorts is TCPView from Microsoft Sysinternals