Windows Firewall Notifier
Microsoft has improved the built-in Windows Firewall ever since it was included in Windows XP and Windows Server 2003.
The majority of usability and security issues have been dealt with. Outbound Packet Filtering was for instance introduced under Windows Vista. There are still some issues left that Microsoft has not yet addressed. Especially the firewall's configuration interface and notifications need improvement.
Windows Firewall Notifier is a third party program for Windows 7 and Vista that improves the handling of the firewall in this regard. When you first start the firewall notifier it performs a series of actions.
The program enables the Windows Firewall if it is not enabled on the system. Once enabled, it will block all inbound and outbound connections for which no firewall rules exist. It then enables Windows firewall inbound connection notifications and outbound connections logging if disabled.
A task is then created in the Windows Task Scheduler that is linked to Windows firewall event log entries. This will basically launch Windows Firewall Notifier whenever an inbound or outbound connection for which no rule exist is blocked.
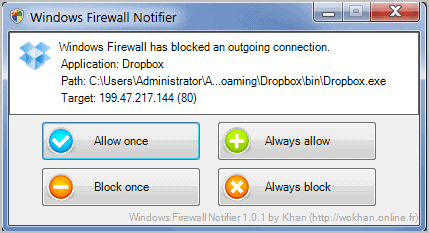
Configuring the program to run as a task means that it will not run in the background all the time. The Task Scheduler will launch the firewall notifier whenever the system tries to make a connection that is not listed under allowed or blocked connections. The following dialog is then displayed on the screen giving the Windows user options to allow or block the connection.
The notification lists the application's name, system path and target IP or hostname. Buttons are available to allow or block the connection once, or to allow or block it always.
The program will make the selected changes to the firewall configuration before it closes down again. Users who want to uninstall the firewall software again need to run it again. A dialog to disable it is then presented on screen.
Windows Firewall Notifier is a handy program for Windows Vista and Windows 7 users who make use of the built-in firewall. The program, compatible with both 32-bit and 64-bit editions of supported Windows operating systems, is available for download at the developer website.
Thanks a lot, WFN is AWESOME !!!
So this program works pretty decently for me, doesn’t kill my system memory or anything, just APN updater, always asks for the connection, and it seems no matter how many times i block it, it comes up again. I thought the rule was supposed to stop it from asking over and over.
Handy? Hardly. As soon as I ran it my system (Windows 7 Pro) started slowing down. I ran task manager and saw dozens of copies of notifier.exe running with many more being added by the second. I started up a shell and started entering
pskill notifier.exe
It killed 87 instances. They kept spawning as fast as I could delete them. I had to boot into safe mode so I could delete the executables before I got a working system again.
Two thumbs down.
Khan,
There are a few bugs in this new version. For any application that has its own service, WFN 1.7 will generate a two rules, one for the aplication with the service and one w/o the service. That is not normal WIN 7 FW behavior.
Also the problem with cryptograhic service persists. The dial out to validate CAs is not being recognized resulting in those being blocked or a global rule to allow all svchost.exe activity defeating the whole purpose of creating individual svchost.exe service rules.
Good work, but when I stopped it IE could connect to the Internet no more.
Waterfox (I’m on 7 x64) could. Nor could programs like PeerBlock etc.
Ping, tracert also came with no results. When I resetted Windows Firewall to the defaults everything worked again. Some how outgoing connections were (at least partially) being blocked. Also my utorrent asked again and again for authorization for the same connections on the same ports – should do it once.
For the rest ok.
Works great when running in administrator account!
Any way to to get the program running in Win7 SUA?
Maybe at least giving blocked notifications?
Thanks in advance for any reply
Khan,
At least it appears my original suspicions are correct.
The unnamed svchost.exe alerts are coming from the crypto service. Looks like the command WFN is having problems with is per Process Explorer:
cryptsvc.dll SvchostPush Service Global Svc approximately
I checked it’s permissions and they are all OK:
SeChangeNotify
SeCreateGlobal
SeImpersonate
Khan,
Correction. Forget about my previous comment about localhost. After a reboot, that connection disappeared. I always forget to reboot after I install a new ver. of WFN.
HI Khan,
I am now running the 1.6.2 version.
Does the WSH rules you created maintain a constant localhost connection? TCPView shows a connection to localhost port 5xxxx that is always present.
Also I am still seeing the same unnamed svchost.exe popup from WFN to alkami and MS servers that occur approximately once an hour. I have been running process explorer and the alerts appear to be related to the Network services container that show Crypto, Dnscache, and Nlasvc running. Interestingly, I have never seen Lanmanworkstation listed as running although this is the container where it resides. I suspect that container is firing off some unnamed service.
wow, taskhost.exe is located at the following path on my machine.
C:\Windows\winsxs\amd64_microsoft-windows-taskhost_31bf3856ad364e35_6.1.7601.17514_none_8664adc870f5633a
Hmm. it’s also in the system32 folder. I wonder why my search didn’t show it there.
Hi Khan,
I went back and reviewed my old firewall rules for Comodo before I uninstalled it a while back.
Comodo created a rule for taskhost.exe tcp port 80. So I duplicated that in the WIN 7 firewall rules.
Whalla – no more blocks when I am now surfing and my web speed is blazing fast.
A bit of research yields this:
TASKHOST is a generic process which acts as a host for processes that run from DLLs rather than EXEs. At startup TASKHOST checks the Services portion of the Registry to construct a list of DLL-based services that it needs to load, and then loads them. There can be many instances of TASKHOST running, as there will be one instance of TASKHOST for every DLL-based service or grouping of services (the grouping of services is determined by the programmers who wrote the services in question).
Appears taskhost is firing off svchost.exe on demand and WFN probably won’t recognize the services i.e. .dlls it is running?
My gut is telling me that Avast is using taskhost.exe to fire off its services dealing with it’s Shields processing.
The bottom line is that I don’t really care how services detection works since I have no intention of using it. I have however tested it with every new version and I was just pointing out, to try and be helpful, that in the original implementation of the services detection, the things that now require a default rule were detected correctly and specific rules just for those services were created by WFN. If there’s some kind of problem now with Windows Update not staying alive long enough or whatever, why was there no such problem before? To me it shows there are still flaws in the implementation of services detection and I thought I should point that out.
I apologize, I know you want to help and I’m really grateful for that :-)
I understand your point of view, but previous behavior was a bit misleading and had a major flaw; I guess I owe you a better explaination than just telling “it’s better now”.
To keep it short: previous version could tell you Windows Update is trying to connect, while it’s actually BITS. Since you believe what WFN tells you, you allow Windows Update instead of BITS. Right after, it’s CryptSvc (or another service hosted by the same svchost instance), but WFN tells it’s BITS. So you allow it as well. As a result: you allowed both Windows Update and BITS, so you think it’s working, but in fact things were messed up! It defeats the main purpose of service detection…
Hope you now understand I could not let it be :-)
What would really help is if I could find a list of services that actually need outgoing connections, so that I can filter out all others during the “late service” detection (which is a complementary step used when the connection owner could not be determined, i.e. when the connection was closed before WFN got it). But I didn’t have the time to do so :-/
Hi Khan,
Sorry, I should have followed up on my missing service detection posting. Appears that if you reboot after installing WFN, there is no issue with services being detected. I also noticed the same behavior in the 1.5 versions.
I think (I know – said this many times ….) I might have found the culprit for my browsing WFN undefined svchost alerts – either Function Discovery Resource Publication and/or Provider Host services. These are used by both Media Center and Home Group and I have both set up, Actually, their primary usage is uPnP, etc. and I really beleive that my unknown svchost firewall activity is port 1900 dial outs to Microsoft. AKA – real or psuedo windows messenger activity although I thought I disabled windows messenger.
I am still concerned at this outbound Workstation service activity. That service is used primarily for LAN activity. Tonight I will experiment with disabling LANManWorkstation service rule and hope the issue was really related to the missing Functional Discovery service rules.
I think the key element for getting a grip on these services is a real-time logging capability of which service was used and what network details were involved. Actually this is a glaring omission to Windows event logging in my opinion. Again another indication that the MS really doesn’t want to give you that information. Or they ran into the same issues as you have in trying to capture which subservice process actually caused the firewall alert.
DCH – I beleive the multiple svchost popup from WFN is when a spawning service like BITS, etc. triggers a bunch of other services and WFN due to timing issues cannot tell which individual service caused the alert. Khan will correct me if I am wrong.
You still can help WFN finding the real service hidden behind a connection by using that command line for all and every svchost hosted services (replacing “service” by the corresponding service name):
sc config service type=own
If you do that for all and every services, it will allow only one service for each svchost instance, meaning that WFN should be able to detect all of them properly, except if the service was stopped before WFN could catch it.
To restore to the (assumed) previous state, use:
sc config service type=share
I haven’t tried to do that (and I certainly don’t ask you to), mainly because it will not give me details I need (see my last sentence in Dch48 answer, regarding services that actually need to connect). And to be honest, I don’t know if I’m right assuming it would work as I expect it to….
I also can not find any “release notes” anywhere that list any services. Neither in the program folder itself nor on the website.
The readme.txt file is what I’m talking about :-)
Regarding your previous assumption, it’s pretty wrong, but you could not guess: in fact the first service detection logic I implemented was based on some heuristics for services WFN could not properly detect, and during the beta tests, it proved to be not that reliable, even if you may have thought it was :-/
Believe me, when I decide to reimplement something, it means that it is actually better than what I previously achieved (stupid bugs apart ;-) ), simply because I hate losing my time.
Where you see worse results, I see better reliability, and this is what users are all expecting :-)
Khan
I discovered a rather interesting “bug” in v1.6.2. If I enable services detection and disable my blanket svchost rule, Windows Time is detected and a rule is made for that specific service. However, if the default rule for Windows Update is deleted and you try to use it, you get an alert for svchost with the services box grayed out but with a bunch of services listed like AeLookup, BITS, EapHost, iphelper and probably more since it runs out of space at that point. If you click on allow you get a blanket rule for svchost created.
I really hate to say this but I have reached the conclusion that all this stuff with services detection has been a complete waste of time and effort. Nobody else does it and I think we now know why. as I have said, v1.3.2 was fine and probably all we ever needed. It was a fine little utility and didn’t need all the paranoia based stuff added to it. Service detection is once again disabled for me and will remain so.
Also, if you block any part of Avast from connecting, you are probably defeating the purpose of improving detection rates by having samples and events automatically sent to their servers and giving them faster response times to new malware. I prefer to contribute to improving the product.
This is not a bug. Windows Update can not be detected since connections are not living long enough (and are using random local ports). BITS or CryptSvc can’t either, and this is the reason why default rules came in in the first place.
If you read the release notes, you’ll see that it indeed shows many services names (prefixed by a star) when the connection owner can not be resolved: this is exactly the case that fits the description you made…
This is not “paranoia stuff”, everything remain optional and believe me, according to the mails I’m receiving every day, people needed those features.
You think that 1.3.2 was a great version, it was not, as said again and again, code has been improved a lot – and I’m not speaking of service detection here.
Khan
I’m sorry but the first part of what you said is wrong because when you first implemented the service detection, Windows Update was recognized correctly and a rule was created for that specific service. Since the default rules have come, it appears that it is no longer the case and without the default rule, it isn’t detected correctly. Cryptservice and BITS were also originally detected correctly with a specific rule created for them. You changed something somewhere that is causing the different behavior.
Khan,
Is this code similar to what you are using?
What would really help is if a WFN event popup is shown, each service associated with the PID at time of block/accept action would be shown in a separate screen popup.
——————————————————————————————–
In order to detect whether a program is being run as a windows service or a console app,
Idea1: Use the WMI class Win32_Service to list the services belonging to the process. If the list result is empty, it means that the process is not run as a service. The following sample code illustrates the meaning.
using System;
using System.Management;
using System.Windows.Forms;
namespace WMISample
{
public class MyWMIQuery
{
public static void Main()
{
try
{
// Get current process ID
int pid = Process.GetCurrentProcess().Id;
ManagementObjectSearcher searcher =
new ManagementObjectSearcher(“root\\CIMV2”,
“SELECT * FROM Win32_Service WHERE ProcessID='” + pid.ToString() + “‘”);
foreach (ManagementObject queryObj in searcher.Get())
{
Console.WriteLine(“———————————–“);
Console.WriteLine(“Win32_Service instance”);
Console.WriteLine(“———————————–“);
Console.WriteLine(“Name: {0}”, queryObj[“Name”]);
}
}
catch (ManagementException e)
{
MessageBox.Show(“An error occurred while querying for WMI data: ” + e.Message);
}
}
}
}
Hi Don,
I’m not fond of WMI querying (probably because it looks old fashioned and reminds me of VBScript tools I wrote years ago…), so I don’t use that one.
I perfectly know how to retrieve the services for a given process (that’s what WFN does), and I perfectly know how to retrieve the real service behind a connection as well, the only problem here is that some connections do not last long enough for WFN to check what their actual owner is (they’re closed right before)… That’s why services list can come back empty, and why service detection can fail. Using another detection routine would not change a thing, and WMI would return an empty result as well if the corresponding service is not running anymore….
I’m afraid that as long as WFN is an event based notifier, it will NOT be possible to fix that issue.
Khan
I wondered why you thought service detection was failing, so I retested 1.6.1, and, indeed, it does not work at all (even with Windows Time service, which was detected before…). As written in the release notes: shame on me.
I updated to 1.6.2.
Stupid code mistake, I do apologize.
Khan
More on Avast per Gizmo’s Best Freeware web site, http://www.techsupportalert.com/best-free-windows7-vista-64-bit-software.htm. This might also explain the constant starting and stopping of the Application Experience service that is recorded in my event log. Application Experience service is used for “program compatibility’ support in Vista and WIN 7.
“Many of the protection mechanisms used by Avast rely on interactive Windows services. Support in Windows 7 and Vista 64 for interactive services is intended for use by legacy applications. This places restrictions on the information that can be sent to the user.”
Well, last nights first boot was interesting with the new 1.6.1 ver.
If I can trust WFN on the popups, it told me both Multimedia Scheduling and Application Experience where attempting to dial-out. The verdict is still out of those two.
I am still receiving generic svchost.exe WFN popups while browsing. With few exceptions it to Alkami and MS IP address. I am starting to stronglt suspect Avast! as the culprit. What I have observed appears to be IP redirect activity. I have blocked avastui.exe, the user interface, program to outbound access. I have suspected avastui.exe for some time of less that desirable activity.
Time will tell if Avast UI is the issue.
Khan,
I downloaded ver. 1.6.1 last night. I didn’t have a lot of time to play with it but there appears to be issues. I received one WFN popup about svchost.exe with no service specified. From the IP address shown, appears this popup was Lanmnaworkstation service related and WFN is not recognizing my existing firewall rule to allow that service. My ISP appears to use a lot of backbone servers and using SMB to connect to them.
Anyway I am sticking with ver. 1.6.0b that I had no problems w/Lanmanworkstation and didn’t give me me any popups for unrecognized services.
One idea I have is if you could display the process id(PID) on the WFN popup, then I should be able to find the service in use. It would require that I use the SC xxxx command from a command window prompt to convert each svchost.exe process w/multiple services into individual processes – one for each service in use.
Yesterday I read that WIN 7 has over 150 system services. The firewall GUI only shows 50 or so that are definable in that GUI. I have a feeling that there might be services that will have to be allowed through the firewall using criteria other than service name.
To date I have been unable to find a document anywhere that shows which WIN 7 services require Internet access and which ports and protocols are used. Only available are firewall exception definitions for individual applications. I also saw a couple of choice comments to the effect that Microsoft has been intentionallly vague on WIN firewall specifics because they want you to purchase their One Care product.
I saw a little bug that went through all tests that have been done, I had to update to 1.6.1 (official, no beta for that one since it was not a really good thing).
The bug: service detection was indeed failing, but instead of showing the host process, nothing was shown.
@Don: Unfortunately, it means that the behavior you were talking about was indeed buggy, and you should get more alerts with 1.6.1… Sorry about that, but I had to fix it!
Teredo is not just for P2P and was not developed for that reason at all. It was developed to allow the reception of IPv6 content where it would be otherwise unavailable.
Simply put, it converts IPv6 material into the IPv4 format.
Teredo is just a formalized protocol for peer-to-peer activity. There are a dozen or so public Teredo servers spread around world.
Teredo is dangerous since anything running on a Vista or WIN 7 box can use it. Once the tunnel connection is establish, any I/O activity bypasses existing firewall including router firewalls or NAT processing. This means “pinholes” or router firewall exceptions do not have to be defined.
Vista and WIN 7 use Teredo to tranfer encrypted certificate info at boot and at other intervals.
The “bot” implications here are obvious.
“Regarding the service detection, if you disable it, you will still get
notifications, but for the corresponding host. If not, it’s a bug…”
The blocks are shown in my event log as originating from svchost.exe. At first they appeared to occur once an hour. Later observation shows that is not true; can be longer in duration. They mostly occur when I am using the Internet but not always. The destination IPs are always Microsoft or Alkami related. The activity persists for approximately 5 minutes and then goes dormat. My gut tells me this is “application experience” phoning home related but WIN 7 is not using that service but using what appears to be a hidden .dll. Like I previously mentioned, It has been shown that WIN 7 does this data uploading regardless of the Application Experience participation setting.
In any case, the fact that WFN in the latest ver.is not alerting me is great since I can now running it w/o being bothered by constant alerts.
Quote–Teredo is a transition technology that gives full IPv6 connectivity for IPv6-capable hosts which are on the IPv4 Internet but which have no direct native connection to an IPv6 network. Compared to other similar protocols its distinguishing feature is that it is able to perform its function even from behind network address translation (NAT) devices such as home routers.
To me that says that Teredo has very much, actually everything, to do with IPv6.
Ok, so you instantly proved I was right saying I had no knowledge about Teredo ;-)
Thanks, I’ll definitely take some time to read about it, and sorry for the obviously wrong assumption!!!
Hi Kan,
“As far as I know, Teredo as nothing to do with IPV6.”
Yes, that is correct. So I guess I am wondering why am I getting the alert from WFN for Teredo activity in the 1.6.0 versions whereas I never received it in prior versions?
I guess you are getting those “new” alerts because Seven and Vista use hybrid IP stack, and the API targetting IPV4 connections can not retrieve the wrapped ones (so almost all stuff developped with IPV6 in mind).
In 1.6, I’m using both IPV4 (for legacy applications) and IPV6 APIs (for both native IPV6 and IPV4 on IPV6 applications).
Regarding the service detection, if you disable it, you will still get notifications, but for the corresponding host. If not, it’s a bug…
Khan
I looked at the rule again that WFN generated for Teredo. It has this strange short name, ç´ïƒ¯. That sure looks like some kind of Chinese symbol to me – does it not?
Now I am wondering if I have been hacked?
BTW – if you have service notification alerts off, you are not going to see any alerts related to services.
No, it only means that WFN may be reading memory pages it should not (probably because of pointer targetting freed memory zone). Since I stay in the WFN memory pages, it won’t hurt, anyway, but sounds like a little bug to me…
I am not getting any alerts for Teredo. Is that because I have no IPv6 service? Or is it due to me disabling services detection?
As far as I know, Teredo as nothing to do with IPV6. And as said (or almost) by Don, since Vista the IP stack is a hybrid one, meaning that IPV4 connections are encapsulated in IPV6 ones (easier to manage), so even if your ISP is not IPV6 compliant, your system is :-)
Khan,
I did update to the latest 1.6.0b ver. Interestingly, I am no longer getting popups from the unknown svchost.exe services that have been giving me problems. However, the events are still being logged in the WIN 7 firewall log? Did this latest ver. check the profile and ignore outbound traffic for undefined profiles for that rule?
Prior to the IPv6 vers. of WFN, I received no WFN alerts on Teredo activity i.e. TCP/UDP port 3544. Starting with the IPv6 vers., I starting getting alerts for TCP/UDP port 3544. If I did not allow those connections, the crypto operations WIN 7 performs via Teredo would fail. What I am saying is WFN should ignore that activity. The WIN 7 core rule will dymanically open and close any ports required. You don’t want permanent rules for Teredo since it’s a security risk. Nor do I want to prompted by WFN everytime MS performs crypto operations via Teredo. However I do see some value with being alerted that the tunnel is being opened by an outbound process. Key here that remote IP for the connection be 65.55.158.118 – MS’s Teredo server. Don’t know how the novices will be ever be able to keep this straight …………………
Note that Teredo is 6to4 IP address tunneling.
V1.6.0 is officially out!
I’ll probably release minor updates depending on user’s feedback, but I really wanted to release that one before next week…
Khan
Khan,
Ver. 1.6 a bit too agressive when it comes to Teredo. It will alert on TCP/UDP port 3544 at boot. Win 7 has a core outbound rule to cover Teredo outbound for IPHelper service. I would eliminate your checks for that since you don’t want people allowing unrestricted access to the Teredo tunnel w/o specify a specific Tereodo server.
DCH – you don’t need IPv6 ISP support to use ver 1.6. All WIN 7 internal communication is via IPv6.
I am now not sure about BITS w/WIN 7. I know Win Updates doesn’t need it but other services appear to be using it. So I let it in for the time being.
I am still getting svchost.exe alerts from WFN w/o service specified. Always to Alkami or MS servers. So I allowed Application Experience and Media Scheduling services again. So far no alerts from WFN.
Thanks for your feedback.
I have absolutely no knowledge regarding Teredo; you wrote that Win7 has a core default rule for it, so it should not raise any notification, except if really needed. So I guess this is where the problem lies: if WFN notifies about an outgoing (expected) Teredo connection, the user will be able to create a global rule while it should target a specific server, is that what you mean? If so, what about a forced IP selection for the related rule to ease a proper rule creation?
I’m about to release 1.6, so I can do that right before.
Regarding the missing services, is the “service” checkbox grayed out, or is it empty? If so, did you update to the latest 1.6.0b when I posted here (https://www.ghacks.net/2011/07/28/windows-firewall-notifier/comment-page-4/#comment-1377865)?
If they remain undetected, I will add default rules for them too, so that the average user won’t have to bother about those ones.
Thank
Khan
I updated 1.6.0b (same link), fixed a bug regarding the service name not being shown in the notification, and tweaked the automatic rules creation since it was always creating the same rules when reactivated (creating useless duplicates…).
It will probably be a public release if I’ve positive feedback.
@Don: I’m really glad you do love that version! Thanks!
Khan
I allow the Google updater to run once a day to keep the Chrome browser up to date even though it’s not my default browser, IE9 is on this machine. Chrome is the default on my XP laptop. I don’t see anything evil in it at all. Like I said before, I don’t care if things “phone home” since many times the data collected is used to improve the product which only benefits everyone. Of course it’s also done for advertising purposes but hey things we use for free still have to be paid for somehow and like I said, I don’t even block ads when I surf.
I can not test the IPv6 feature in the latest version since my ISP does not support it yet. In my connection properties under IPv6 it always says “No Network Access”.
WAT now connects in a different way than what you posted . It now uses a file called WatAdminSvc.exe which is located in c:\ Windows\system32\wat
Khan,
I do love the new version! Especially the TCPView like connection display that shows the connections with the big plus of showing the individual services running.
As far as your question as to Windows Defender and WAT neither WFN or the WIN 7 firewall showed those programs being blocked. Interesting is it not?
Also I am still seeing blocked connections in the firewall logs for which I am not receiving alerts from WFN. I am hoping these are the result of the block rules I created for Application Experience and Multimedia Scheduler. I am fairly certain those two services are being used by WIN 7 to constantly dial home to Microsoft.
BTW – BITS is needed by Vista for WIN Updates to work. WIN 7 uses triggers to activate BITS on demand when needed. I verified that yesterday.
Hi Khan,
If you use Google Updater, then I don’t know what to say. I consider it spyware to the ninth degree. Was mysteriously installed on my Win 7 OS and was an absolute bear to get rid of.
Yes, my WIN 7 setup is doing Win Updates w/o BITS firewall rule with no issue. WIN 7 creates a rundll32.exe task that has to be allowed through the firewall that does the periodic update checking.
I stopped the Appication Experience WIN 7 firewall log entries by creating a block rule for it for all profiles. I have also created a block rule for the Multimedia Scheduler service for the Domain and Public profiles to stop those from showing up in the logs. Appears both the above services do a broadcast to all profiles. Appears to be a WIN 7 bug to me.
To allow Windows Defender to connect outbound you need to:
1. Create a program rule for:
C:\Program Files\WindowsDefender\msacui.exe.
2.Allow Windows Defender service TCP ports 80, 443.
To allow Windows Activation to connect outbound you need to:
1. Create a program rule for Windows Activation:
%Windows%\System32\slui.exe
I certainly do not use Google updater, it’s on my system since I reinstalled Google Earth, I guess, and I’ve left it there to check if WFN was working properly, since many people use the said updater.
Regarding WAT, it should raise a WFN notification ; same for Defender. Am I wrong assuming they both do?
Khan
Hi,
As far as I know, BITS is used by Google Update as well, I hadn’t the required time to check if it was through a svchost instance or not…
Are you sure Windows Update is working properly as a background task when BITS is not allowed through svchost ? If so, I may consider removing that default rule.
Last but not least, v1.6.0b is out, adding only one but still important thing (hence the new version) : IPV6 support for the connections list. Sould be an alpha release, but it seems to be perfectly working. Let me now if it does not!
As you guessed, it’s right here : http://wokhan.online.fr/progs/WFN_1.6.0b.zip
Khan
Hi Khan,
I have made a lot of progress this week.
I found after a lot of web searching, two required outbound rules for both win 7 activation and windows defender. Neither of which will show in the event logs if not present. I will post those tomorrow.
I have everything nailed down except for Appication Experience. Did a lot of research and found win 7 will still attempt to dial-out even if you disable that option in the GUI. For some reason even though I have a svchost.exe rule for it, it is still failing. Also appears that the associated DNS request for it is failing on a RARP; my router IP address is malformed. Strange indeed.
As far as your default rules go, you only need BITS for MSE. If you don’t use MSE, BITS works just fine w/o a separate svchost.exe rule for it. There is a lot of community sentiment that says BITS should be harnessed since a lot of malware has been known to use it.
I personally, have kept my blanket svchost rule and deleted the ones that were automatically produced since they were redundant. For those who want to use the services detection however, I feel there need to be a few more default rules. Three I can think of off hand are W32Time, LanManWorkstation, and probably the RPC service as well.
One thing I really like in the latest beta is the connection monitoring. That could prove very useful in the event of a problem.
Hi there,
WFN 1.5.5b is out (still beta, not finalized, but I’m a little bit tired working on it ;-) ).
For the improvements… well, check the included read-me.
Two important points:
– WFN needs to be enabled (again) for its first-time launch in this version, so hit OK when it asks if you want it to be activated.
– it automatically creates three rules :
– Windows update service (remote ports 80/443)
– BITS service (same ports)
– CryptSvc (port 80)
I will probably change that, at least for cryptsvc as I know at least one of you does not like that one (hi Don ;-) ), but as of now it seems to be the best option for most users.
Finally, the link : http://wokhan.online.fr/progs/WFN_1.5.5b.zip
Khan
What I am finding out is a lot of the svchost dial-outs are due to built-in Microsoft spyware. Win 7 installs Windows Defender by default. It also turns on it’s SpyNet reporting. So turning that off eliminated most of the “crypto” server dial-outs. I also turned off the Customer Experience baloney only to find out WIn 7 still attempts to dial-out.
Bottom line – WIN 7 is MS spyware in my opinion. I am allowing only the following outbound in addition to the provided WIN 7 core rules:
BITS – TCP Ports 80, 443
Network Location Awareness – TCP Port 80
Cryptographic – TCP Port 80
Windows Defender – TCP Ports 80, 443
Time Updates – UDP Port 123
Windows Update – TCP Ports 80, 443
Ignore any other svchost blocked activity..
I found this great web link: http://www.neosoft-tools.com/articles/10-things-about-windows-vista-service-hardening.htm that explains “Windows Hardening” Most of it applies to Win 7 with the addition of Win 7 service triigers.
Bottom line – service hardening provides a built-in “HIPS” capability in that it restricts internally what a service can modify. Note that it protects nothing protocol, port, or any other network access wise. MS’s stance is they provide default rules for the basic required services …….. Yeah – ICMP, DNS, and DHCP; that’s it. Further, WIN 7 introduces no standard service use e.g. using the dnscache service for P2P connections.
Your assumption is pretty wrong. I didn’t read the said page (kinda short of time), but WSH also provide some hidden default firewall rules.
The good news is: next version of WFN will include those rules on the “Rules” tab (one of the features I wanted to keep secret ;-) ).
Khan
Hi Khan,
Major revelation!
Don’t know if this relates to your “little secret” or not.
Appears some but not all services do a type of outbound broadcast to all three Win 7 profiles. Since I only have the private profile active, the firewall will block outbound connections to the other two profiles. Hence I suspect the constant WFN svchost.exe connection alerts?
I have set all my svchost.exe rules to private profile only and am monitoring. Will keep you posted on developments.
Hi there,
I prepared something you’ll probably all enjoy using. I’m still tweaking it, but I know people will like it.
No spoiler here, I’ll keep it secret til released ;-) Hopefully next saturday, maybe before.
Khan
Looks like WIN 7 uses RpcSs on those hourly dial-outs for Win Updates. That’s a bummer since RPC has know secuirty issues. I did restrict it to port 80 so lets see if that works. If not, I will just write a rule to block it since WIn 7 will still update once every 24 hours w/o it. With the block rule in place, I won’t get anymore alerts from WFN.
BTW – I make it a habit to create my own block rule although I know WFN will block it as an exception. I do that in case I want/need to run w/o WFN. I would like to see a “generate block rule for exception’ option capability in some future release.
I do know that Microsoft has made output firewall processing as difficult as possible as far as svchost is concerned. As I posted previously, one obvious reason is MS uses svchost for its own spyware purposes such as product activation, customer “experience” uploads, etc., etc.
A few things here. The gui looks exactly the same to me, I see no change. My existing rules were all checkmarked. I see no option to disable service detection except by manually editing the config file and changing the value to false.
Okay I found the option to disable service detection and I also noticed the uninstall button was moved to that same tab.] so disregard those two things. I do have a question though. I checked the box to disable service detection and it does work. I tested it with Windows Update and the services box is just greyed out. My question is this. Why does the config file still say this even with the box checked and service detection not running?
erSettings>
True
Geez, it didn’t paste in right. The config file says:
WindowsFirewallNotifier.Settings
setting name=”EnableServiceDetection” serializeAs=”String”
value True /value
Khan,
I really like the GUI of the new version. Looks very professional.
A few bugs I have found so far.
1. remote ports show in local ports column.
2. existing rules are not check marked.
Also I did get an alert from these MS dial-outs that are still causing me problems. Alert was for svchost – dsncache TCP port 80? I did allow it and am monitoring it since I did come across a discussion on the web on this stange behavior in WIN 7. No wonder no one has ever tried this before!
Thanks :-)
Regarding the two bugs: I fixed them locally but have not updated the beta, thanks for noticing.
For the service detection, you should not trust this version, there are some bugs and that’s why I’m rewriting the related code for something 100% reliable… Sorry about that…
Khan,
This is hillarious.
I found the culprit for the hourly svchost.exe dial-outs. It was the Network Store Interface Service. I also suspect that MS is hiding that connection hence WFN’s inability to detect it?
Anyway once I enabled that I received a block from a program in System32\WAT directory. Guess what the program was? Windows Activation!
So the Win 7 firewall didn’t even create a default outbound rule to allowing it’s own spyware! I just love Microsoft ………………..
It’s indeed funny ;-)
I found another way to detect services (a way more complex one, but clearly more reliable). It will thus totally supplement the previous one, I hope to be able to make it work today…
I’m confident it is the way to go, so I won’t stop until it’s done…
Sorry, I inverted the version numbers!!!
Correct URL is http://wokhan.online.fr/progs/WFN_1.5.0b.zip
Khan
http://wokhan.online.fr/progs/WFN_1.0.5b.zip
This link doesn’t work? I get some destination unreachable in French?
Oops. Sorry – didn’t notice you changes the link.
Khan,
This link no longer works for downloading the latest beta:
http://wokhan.online.fr/progs/WFN_1.4.0b.zip
New beta: http://wokhan.online.fr/progs/WFN_1.0.5b.zip
Services detection is still a problem (I had many alerts for connections to a Google server, while it was initiated by a svchost instance hosting MS services only, so I don’t get what’s happening). Still working on it.
@Dch48: this version introduces an option to completely disable service detection.
Khan
Ok, it was BITS. That’s rather weird since I allowed it for all and every IPs during my tests, and it is still blocked by Windows firewall.
By the way, I updated 1.5.0b (again, same link), an annoying bug was introduced regarding the icons management, sorry about that.
Khan
Hi Khan,
I am presently allowing BITS TCP port 80, 443.
I am playing with the idea of just using an “all services” rule. If I understand MS correctly, this will allow WIN 7 to use whatever service it needs in the firewall. I ran with this for a while and recieved zero outbound blocks. I am puzzeled as to why MS does not have outbound firewall rules to cover everything. I guess they want you to do that via Group Policy …………..
This is much better than allowing svchost.exe unresticted outbound access even if restricted to TCP port 80 and 443.
I have win 7 Home Premium and as such don’t have the Group Policy Editor which would allow me to restrict access by GP.
Khan,
I turned off WFN and have been debugging the svchost issue using the WIN 7 firewall log. I have pretty much working out all blocks for svchost except one.
Besides the core DNS, DHCP rules I added a rules for Windows Update, Time Updates, and Error Reporting, I also added rules for NLA, Cryptographic, Windows Defender, and LanmanWorkstation. These rules cover the majority of outbound connections from svchost..
I do know you don’t want to give BITS outbound access. Once you do that, I start getting suspect outbound TCP activity.
My main issue presently is that approx. once an hour, I get outbound svchost activity to Alkami and MS servers. I strongly suspect this is a check for Windows Updates that differs from the check made at cold boot time. That update uses the Windows Update service for sure. This hourly activity I have not been able to identify svchost service wise. Or,it is just data harvesting by Microcoft. In any case, the blocking activity does not appear to be causing any operational issues.
Hi,
Why don’t you want to let BITS do its job? I know that disabling it caused Windows Update to stop working properly (at least Security Essentials wasn’t able to update anymore, and do other softs as well).
I’ll give a try to the soft you were talking about, thanks for the info :-)
Khan
There is one , and only one, reason why I bother with outgoing filtering at all. It is to alert me in the highly unlikely case that a piece of malware has gotten through my defenses and is attempting to connect out to either download more malware or transmit some of my data. I’m not interested in knowing what safe applications are doing and even less interested in monitoring parts of the OS itself. I want the end result of setting my rules to be that if I do get an alert, and I haven’t installed anything new, I pretty much know the connection attempt should not be happening and should probably not be allowed. I say highly unlikely because I have been online since 1999 and have never been infected by anything. My AV at the time has always caught the attempts and there haven’t been that many, maybe 20 in 12 years. I was on dialup for the first 5 years and never used a firewall of any kind. That’s why I want the process to be as simple and unobtrusive as possible. Please make all this extra detection stuff optional and able to be switched off in the final release as you said you would like to.
More why you don’t want to give services unrestricted firewall access,
Whereas neither of these utilities are supported under WIN 7, there is nothing to prevent them from being used to create WIN 7 services.
What is Srvany?
Srvany is a utility developed by Microsoft that can start almost any regular, non-service application as a Windows Service.
Since a Windows Service must be specially constructed to interface with the operating system (to allow Windows to start, stop or pause it on demand), a regular application without this interface will not function properly as a Service. To solve the problem, Microsoft developed Srvany – an “adapter” (or “wrapper”) that can accept the Windows Service commands and translate those into actions that a regular executable can understand.
Like any good adapter, Srvany is installed in between Windows and the application and handles all interaction between them. For example, when Windows says “Start the service”, Srvany intercepts the request and starts the application as if you had double-clicked on it yourself.
Srvany was developed in the late 1990’s for Windows NT and remains mostly unchanged to this day. It is available as part of the Windows Server 2003 Resource Kit Tools package.
What is Instsrv?
Instsrv is a Microsoft-developed utility used to install a Srvany Service. It does not participate in the actual running of an application as a service – it just helps with the installation.
Khan,
Are you aware of this free MS sponsored service trigger utility for WIN 7? Might help in service execution due to dynamic port opening and closing.
http://www.coretechnologies.com/products/ServiceTriggerEditor/
Hi Khan,
I am really starting to make some progress on the Svchost.exe services.
As I somewhat suspected a while back, you have to create a Win 7 firewall rule for pretty much every service that is dependent on RPC.
From what I have observed the similarities btw Vista and Win 7 firewall are almost non-existant. The key to understand Win 7 firewall is by default, Microsoft appears to do be doing most of its web crypto stuff using the Teredo tunnel. As I observed the crypto activiity which btw are the connections to msecn.net and Alkami, I would see 224.0.0.253 openning and closing – a sure sign of Teredo tunnel activity.
The key service for stopping the majority of WFN blocks for me was BFE i.e. Base Filtering Engine. Note that I had previously enabled many other RPC dependant servives such as IKEEXT, Protected Storage for lsass.exe activity and the like. BTW – I obvserved activity from these services when I was running the WIN 7 allowing all outbound activity.
At present, the only web page giivng me trouble is AOL’s home page where I am getting those previous crypto related service blocks from WFN. I am inclined to attribute this to the suspect behavior of AOL and the assumption that the site is interfering w/ the WIN 7 firewall tunnelling activity. One could assume that when such a site is encountered it would be prudent to exit that web page.
I still beleive this by service approach is the way to go. When I allow all outbound activity, I observe way to many connections of suspect web servers associated with Google.
[q]As far as creating a “global†svchost generic rule, it defeats the whole purpose of creating rules by service.[/q] Yes it does and I have decided that I don’t need to do it since no other firewall I know of has that capability, I don’t think it’s needed. To me it’s like about 95% of what the paranoid geeks at Wilders recommend, simply not necessary. I returned my svchost rule to allowing all, deleted all the service specific rules, and everything works like it should, including Windows Update and Time. I’m getting no more alerts like the ones Don mentions which I really couldn’t deal with. It was worse than having a HIPS application which I also have rejected after using a couple of firewalls that had the functionality.
I was happy with v1.3.2 of WFN and I actually might go back to using just that with it’s simpler interface.
Your point of view is shared by many people (including me, I added services detection for those asking for it), but you can stick to 1.5.0 (when out!) and still define global rules. Interface changes are not the only tweaks I have been working on, as said, the code has been way improved. I will probably add an option to completely disable service detection, since it adds a little overhead, as you probably guessed.
Khan,
“I guess there is a bug behind that: svchost should always be followed by a specific service in WFN, if not, it’s a bug. ”
I am not so sure of this. I keep getting connection attempts to MS or it’s proxies(Alkami, etc.) about once an hour or so. These are to IPs like MSNet and the like. Also these show no related service. The connections always seem to occur while I am browsing or shortly after I log off.
I am beginning to believe MS is using svchost with perhaps a hidden service to “dial home” browser statistics minimally and at worse, site tracking info.
Another possibility is that I have read that WIN 7 checks for updates quite frequently. I also read that it does not use the WIN Updates service for this. I have created a firewall rule for the Scheduler service and it did not help. Again this might be might be a “hidden” service.
Note that not all services are shown in the WIN 7 firewall. I don’t know if it only shows those that have a SID(security indentifier) or what.
As far as creating a “global” svchost generic rule, it defeats the whole purpose of creating rules by service. Also limiting by IP seems an effort in futility for the MS dial-outs since the IPs and/or servers keep changing.
I suggest perhaps the SID concept be explored. From the MS doc. I have read, these are the legit services according to MS. WFN could check for the existance of a SID and if one exists, allow the svchost transaction. WFN would only alert when SID is not present. Sure beats trying to figure out if a svchost service rule needs to be added.
I got fed up with alerts for svchost wanting to connect to a new set of IP’s on almost every website I went to (mostly certificate issuing authorities) so I just made my miscellaneous svchost rule (for connections not specifying a particular service) allow all connections on port 80. I subsequently had to add port 5357 to allow communication to the other machines in my home network. I still get an occasional one from system concerning connections to my router. One more alert and the blanket rule for svchost goes back in effect and there will be a similar one for system. It’s either that or no outgoing filtering at all and a return to the default Win7 firewall.
I guess there is a bug behind that: svchost should always be followed by a specific service in WFN, if not, it’s a bug. I’ve to handle Windows Update and BITS apart since they both connect from random local ports to remote port 80 or 443, and connections originating from them both only last a few ms, so I can’t catch them “the usual way”. I guess the same occurs for cryptography or alike.
Remember it is still a beta and I’ve a real job / real life out there, I can’t test all and every cases ;-)
Thanks
I now suspect that some of the connections have to do with the web shield of Avast which sends all connections through a proxy to be evaluated before actually establishing the connection. It’s already been determined that allowing the web shield to scan all traffic and not only that from a browser conflicts with Windows Firewall outgoing rules and actually bypasses them in some cases. If it comes down to choosing between Avast and WFN, I’m sorry to say that Avast will win out.
I did not set specific IP’s for the rules that did specify which service they were for. I did it for the ones that didn’t specify one and subsequently allow all services. I figured that allowing all IP’s through port 80 for example wouldn’t be that much different than just having the blanket rule. It’s not the alerts that do specify a service that I find to be a hassle, it’s the ones that don’t and are connections to mostly Microsoft or certificate issuing parties. I suspect that those connections are tied in to IE9’s enhanced SmartScreen filtering.
Also, Don mentions v1.5. What I have from the current download is v1.4.5. Am I missing something?
You are not missing anything, 1.4.0.5 is the beta version that will be turned into a 1.5.0 when publicly released :-)
IMHO, as long as you trust a program, you trust it fully and should not have to restrain the IPs it communicates with… Just my 2 cents.
I forgot to answer your previous post about your MS “System” rule. You wrote: “Now I’m getting tempted to just disable WFN and go back to just the default Win 7 Firewall.”
I don’t get it, remember WFN only creates rules you are asking for, you still can tweak those ones if you want to or manually create others. The primary aim of WFN still is to notify you of blocked outgoing connections, it’s here to help.
I’ll give a try to IE9 smartscreen filtering (not using it as of now, since I’m an Opera user), to see if I get other notifications or not.
Khan,
New version still not showing all services. I was still getting constant popups w/o service name for what appeared to be crypto releated IPs. Looking at service dependances for cryptographic service saw DCOM Server. ??? So I set at svchost.exe rule for that and bingo – all the alerts disappeared.
Also for some strange reason, I am not getting a popup at boot time for that ICMPv6 type 143 rule I mentioned previously. WFN is blocking it OK but does not create an exception for it? Note: that an exception existed in the old version but disappeared when I installed the new 1.5.0 ver.
Also when I installed ver. 1.5.0, I saw a block entry for .Net 2.0 dw20.exe file. Hasn’t reappeared on subsequent boots. Must be an install fluke or something?
Okay, I think I solved the problem with the Microsoft sites changing at reboot. I just allowed the full range of MS Hosting IP’s and so far, so good. I was getting an alert for a different IP being connected to by svchost or system every time I restarted.
Good choice, except that the full MS range you are talking about can change (and thus is not that full, in fact). MS uses some other servers, not only theirs, and IP range can vary. It should work for some time, anyway, so you can keep the rule you created – but do not wonder why it asks again one day or another :-)
I just got another one, “Custom Rule – Microsoft Windows NT 6.1.7601 Service Pack 1 [T:207.46.11.135] [R:137]” . It’s for a Microsoft server in California and again the associated program is “system”. Now I’m getting tempted to just disable WFN and go back to just the default Win 7 Firewall.
1. It works
2. Do I like it?–not sure
I did away with my blanket rule for svchost and so far this is what I have gotten.
FOR SERVICES:
Windows Update
Windows Time
Cryptographic Services
Network Location Awareness
LanManWorkstation
MISCELLANEOUS FOR ALL SERVICES (NONE SPECIFIED):
Verisign
Akamai
Allstream.net or entrust.net
startssl.com
Microsoft Hosting
I also got an alert for rundll32.exe connecting to a Microsoft site described as Microsoft Hosting and a strange one for what is called “Custom Rule – Microsoft Windows NT 6.1.7601 Service Pack 1 [T:192.168.2.1]” which of course is the IP of my router. In that rule the program associated is simply System.
I have to say that I’m very tempted to just return to the blanket svchost approach and I think all these alerts are the reason why all third party firewalls deal with it in that way. It’s just too much of a hassle to keep up with, especially when you consider that the Microsoft IP’s are constantly changing for security reasons and is why you can’t specify one for Windows Update. I have gotten 3 different ones so far for “Microsoft Hosting”.
I don’t get why you consider that approach as being problematic, you only have to define your services rules once. If you still want a global svchost rule, untick the box in front of the service name, it’s that simple…
I offer the option to create IP specific rules for people who want to deal with it (I personnally don’t, dealing with the local / remote port should be enough).
By the way, service hardening does not mean you have to target specific IPs, only that services should only communicate on ports they have been designed to, for the purpose they have been designed for.
I don’t get why you consider that approach as being problematic, you only have to define your services rules once. If you still want a global svchost, untick the box in front of the service name, it’s that simple…
And creating IP specific rules is not a good idea, I offer the option for people who want to deal with it (I personnally don’t, dealing with the local / remote port should be enough).
Service hardening does not mean you have to target specific IPs, only that services should only communicate on ports they have been designed to, for the purpose they have been designed for.
So it’s
Hi Khan,
I will download and try out the new version shortly.
I have finally got my WIN 7 outbound svchost.exe rules established. Key was RPC and RPC Endpoint Mapper. Those have to allowed outbound access. Vista appears not to require them but Win 7 definitely does. Also BITS needs unrestricted access since at boot it appears to call many other services. Finally, if running Windows Defender in real time, its service must be allowed. Otherwise you will be nagged by constant WFN alerts to Microsoft or its proxy servers.
One thing that concerns me is the allow rules WFN generates. For example I received an alert for ICMPv6 type 143. The allow rule that WFN created was to allow System. No ref. to protocol(58) etc. Not good.
Rules creation has been improved with the last beta, but still works the lazy way regarding the protocol (= the protocol is considered only if you specify a remote port, only for UDP & TCP, not for ICMP).
Fixed and updated!
Khan
Hi there,
Here we go, 1.4.0b evolved into what is going to be WFN 1.5.0, meaning it has been deeply modified.
The design changed as well, and now allows to create complex rules for those who want to (as for Don ;-) ), while still allowing to create simple rules for the others (as for Dch48 ;-) )…
Still the same URL for the beta : http://wokhan.online.fr/progs/WFN_1.4.0b.zip
How does it work ? Simply tick the checkbox in front of the items you want to create a rule with. If you want a port-specific rule, check this, if you want a target-specific rule, check that.
I really hope all of you will enjoy this beta.
As usual, feel free to contact me!
Khan
I updated the beta, a minor bug was reintroduced in the one I published yesterday: when a new connection was blocked, the corresponding notification was displayed in place of the previous one, which was kinda annoying.
Thanks to Cyrus for telling :-)
Khan
And I’ll update it again soon for another little bug: both the “service” and the “target” fields are sometimes blank.
Hard to work on it while watching the game :-)
Khan
Khan,
I found out what my problem was with svchost! I am so embaressed.
When I set up most of my initial svchost.exe rules, I only allowed TCP for most of them. Then I compounded the error by only allowing TCP on the allow “all services” rule I created. Smack, smack ………
Appears the Cryptograghic service definitely requires both TCP and UDP. Microsoft “camps out” for extended periods of time on a high valued UDP port. This very well could be Windows Messenger activity which off course is enabled by default in WIN 7. But it also could be to facilitate certificate checking which I what I really thing it is.
So for the services I feel I need, I have left them all undefined except for Windows Time which I know definitely uses UDP port 123 in and out.
One question. Does WFN require that .Net 2.0 be installed for full functionality? By default .Net 2.0 is not installed on WIN 7. MS states that that later .Net releases support prior .Net applications but there have been well know documented exceptions to that statement.
Your assumptions are right, WFN checks the exceptions list for all blocked outgoing connections. In fact I guess that the “block” option should be called “ignore” since this is what it really does… I’ll change that.
By the way you were right about the bug with blocking rules: a popup was shown even if the connection was set to be blocked in the windows firewall. This is a non-sense and I fixed it (still not released,though).
Regarding .Net, WFN uses version 3.5, not 2.0. For my own knowledge, what exceptions are you referring to with v2.0?
Thanks
Khan,
Pertaining to my .Net 2.0 comment, I just noted that there is exisiting Net 2.0 developed software that will only work with the .Net 2.0 framework. This type software will not run right on .Net 3.5.
Also, I wonder if WFN can show blocked UDP connections – at least for system containers like svchost.exe? This would have saved me a lot of time in diagnosing my problem.
KHan,
Just want to verify WFN operation.
If I get an alert from WFN, it implies that it has encountered the default action for the inbound/outbound firewall. For both inbound and outbound that action would be block. This is why all you have to do is close the WFN popup window and the action is automatically blocked w/o having to click on the “Block” button.
Now when I click on the “Block” button, WFN blocks the executuion and adds the event to WFN exclusion list..
In my instance of svchost.exe, I have a Win 7 firewall rule to allow all registered services. I get a WFN popup implying something has bypassd that rule. If I now select the WFN block “button”, WFN will add svchost.exe to the WFN exclusion list.
My question is the next time svchost.exe is executed and that event causes no exisiting Win 7 firewall rule for it to be satisfied, no popup will be received from WFN since WFN found an instance of the program on the exclusion list. Is this correct?
In other works, adding a program to the WFN exclusion list does not override any existing firewall rule that was manually added for the program?
I’m getting concerned that WFN is evolving into a firewall of it’s own with these added detection routines. I thought it was just supposed to be a simplified interface to the Windows Firewall that made the management of outgoing filtering easier. I just hope that these changes don’t wind up ruining what was a fine and simple little utility.
Don’t worry, I’m aware of your needs and I understand your point of view, and that’s why I added an option yesterday allowing to create either application or service rule (exactly what you’re talking about :-) ). Furthermore, service “detection” (which is more an identification routine) will be optional, since of course it uses some resources when WFN is run (not that much, anyway!).
I won’t be able to work on it before Friday, sorry it takes so much time but be sure 1.4.0 is more than a little update, I’m improving some internal stuff which should make it more reliable. Still not stable enough to be another beta, though…
All of that further validates (in my opinion) having a rule for svchost that allows all outgoing. Who wants to keep dealing with a bunch of alerts? I read what Microsoft has to say about it and I really had to laugh. They say one thing and talk about serious security risks but then they default their firewall to allow all outgoing by everything.
Don, I know you were asked this in the Avast forums but I have to ask again. Why are you using IE8 when IE9 is so much better in every way?
Khan,
Yes, after allowing what was most certainly a certificate store update, I did not receive a further popups from WFN pertaining to svchost.exe the remainder of last night.
I suspect the issue with WFN might be in it’s handling of the Distributed Transaction Service(DTS). Scroll to the last posting on this Wilder’s forum page: http://www.wilderssecurity.com/showthread.php?t=239750&page=17. Appears DTS initiates the connection, then the Wins Update service, and finally the Cryptographic service.
Hi Don,
Thanks for your investigations, I’ll double check WFN behavior based on what you observed, which will help a lot!
As of now, service detection works way better (I didn’t update the beta since the last one is not stable enough), but I still have some issues with the said services (CryptSvc and DTS, and some others). Still working on it…
Khan,
I have run into an issue with ver. 1.3.2.
In keeping with Mcrosoft’s guidelines with firewall rules for containers, I created a rule that allowed all my services w/o specifying svchost.exe. In theory that should allow everything and I should not get any blocks from WFN. Well, I kept getting popups about svchost.exe? So I traced the IPs and they all related to Cert. Auth. sites like GoDaddy etc. So I allowed one connection and traced the connection. Sure enough it was related to the cryptographic service.
Most of the popups occur when I am surfing with IE8. IE8 with default settings checks for certs. validity. My theory is IE8 must be calling the crypto. service and something is getting hosed in WFN and it is ignoring the WIN 7 firewall already in place?
Hi Khan, thanks for the excellent software. I’m trying now your beta, i’ll let you know.
Can i suggest you to open a thread in the Wilders Security forum? It’s full of security nerd, and you can find plenty of beta testers…
Hi Svarius,
Thanks for your support! I previously wrote that I should indeed go to Wilders, and I still do, when I finally find the time to :-)
Khan
BTW – my full AV scan yesterday found a Trojan. First infection I every had on this WIN 7 OS in sometime. Now I could have done it to myself since I have been reconfiguring many outbound firewall rules. However, I am a bit suspicious of 1.4.0b release since I have been running with it for the last week.
Don, I guess from what you are writing that you are misunderstanding the way WFN works. It is NOT a firewall, it does not directly allow or deny connections: its aim is to ease the creation of outgoing connections rules. The user always makes the choice of either allowing or blocking the connection. I’m sorry to tell, but the trojan was probably here because of something you did…
Regarding your other post about services, I’m still working on it, it takes some time since I have less free time than expected…
Khan
As far as Microsoft’s stance on svchost.exe and for that matter all service containers e.g. svchost.exe, dllhost.exe, etc. or programs that host services e.g. avastsvc.exe. mbamservice.exe, etc., they should never be added stand alone to any firewall rules list. They should only be added in reference to a particular service – period.
Ref: http://technet.microsoft.com/en-us/library/cc730951(WS.10).aspx
BTW – this is a major “secuirty hole” in all non-Eneterprise firewalls today hence my return to the WIN 7 firewall.
Khan,
Came across this on the web. Supposed access path for svchost.exe service identification.
Services Display Name Path
BFE Base Filtering Engine C:\windows\System32\bfe.dll
DPS Diagnostic Policy Service C:\windows\system32\dps.dll
MpsSvc Windows Firewall C:\windows\system32\mpssvc.dll
Here’s what I did in regards to ver 1.4.0.
I downloaded it and unzipped it in to it’s own folder. I uninstalled ver 1.3.2. Part of that process asks if you want to keep existing settings and I said yes to all.
I then fired up ver. 1.4.0. I didn’t delete anything. No crashes so far.
As I posted previously I did have a .Net crash with the exisiting 1.3.2. ver. that appeared to be related to the WFN log file.
Also, I have Windows Defender too of course, but it has been disabled from the time I first bought this machine. It came with Norton Internet Security pre-installed (and don’t give me the same old tired nonsense about Norton being bad. I used it for over ten years and never had a single complaint, performance issue, or infection. They make an excellent product, I just didn’t want to pay the subscription fee any more.) Norton was completely and fully removed and then the free version of Avast was installed and also has not experienced any problems other than the new webshield interfering with and overriding some of the outgoing rules of WFN if you have it set to scan all traffic and not just what comes through your browser.
I guess I would describe myself as a minimalist when it comes to security apps. I do extensive PC gaming and I can’t be bothered with allowing this and blocking that all the time or alerts freezing my game or crashing it to the desktop. I may even just go back to using the default state of the Win 7 firewall. I think about doing that often.
Please do not reply and tell me to search for remnants of Norton. There are none.
I have a folder called Windows Firewall Notifier in C:\Program Files. What I did was run the uninstallation routine then delete all of the files in that folder. I then extracted v1.4.0b and copied and pasted all of those files into the folder in Program Files. Then I ran the install.On first access of something without an outgoing rule, V1.4 crashes itself or at least says it does even though sometimes the rules are successfully created. I go through the same process of uninstall, deletion of files, extraction and pasting in of v1.3.2 and everything works as it should again.
What I’m thinking is that there is a .NET problem with v1.4 that doesn’t exist with 1.3.2. Like I said, I’m really not interested in separate service detections , and therefore different rules for each one cluttering things up so at this point I’m leaning strongly towards staying with 1.3.2.
Don and I have different approaches to what is needed for security. To me, a lot of what he wants is overkill and totally unnecessary. Why would you have a rule blocking the Avast UI from connecting for example? For svchost, every firewall I have tried, Comodo, PCTools, Outpost, Online Armor, Windows 7 Firewall Control, will create a rule for svchost allowing all outgoing connections. The default state of the Windows Firewall will allow the same behavior. That’s good enough for me.
Khan,
One bug I also found with the beta version was it appears to be ignoring my existing Win 7 firewall outbound block rules and creating a WFN block rule. I doubled checked the avastui.exe WIN 7 rule and it should have blocked the connection based on the existing rules; i.e. TCP port 443.
Windows Defender is installed and runs real-time by default in Win 7. So far it has not conflicted with of my other real-time anti-malware software so I just left it in place.
BTW – I am running WIN 7. It’s services are similiar but expanded from Vista’s. Also my alerts are back for svchost.exe. I am allowing BITS, Win Update, RPC, Time, Cryptography, Software Protection, and Windows Defender but still getting svchost.exe alerts from WFN.
Most include MS IPs so it must be OS related but darn if I can find out what service it is. It is always for TCP port 80. I might try allowing the Profile service again. I suspect MS might be using it to log on and dial-out periodically.
@Don : Ok, I think I found a bug for the services, still working on it, but since I’m late I won’t be able to fix it before tonight.
Do not bother trying the newly published beta version, services detection is still not fully working, I’ll keep you informed.
Khan
Thanks Don, I guess Windows Defender uses the same logic than Windows Update. May I ask why are you still using Defender and not MS Security Essentials?
It seems that “service detection” isn’t working anymore for me as well (always showing up svchost) :-/
@Dch48: did you redownload using the same link?
If it still fails while not producing any errors.log file in the WFN folder, can you please try removing the “WindowsFirewallNotifierTask” task from the task scheduler, and launch the install process again?
If it doesn’t work any better, could you please tell me where you extracted the files and what file you have in the WFN folder?
Thanks!
Khan
Well, I think I found the service that was causing all my alerts from svchost.exe – Windows Defender! I always forget I have that running in real time mode. You definitely need an outbound svchost.exe rule for Windows Defender service if you are filtering services like I am.
So far so good with this lastest vers. – no hangups etc.
I wish I could use 1.4.0b but unfortunately, I can’t. It crashes.
I am now running ver. 1.4.0b. Stable so far.
I thought you modified it to show what svchost.exe service was issuing an alert? This ver. is the same as 1.3.2 in that all it shows is svchost.exe. That is it.
Yes, I did, and it worked (at least with the task scheduler and some other services), I would not have written that it did otherwise.
Unfortunately it fails for the most important service (Windows Update), I did not notice that behavior since I allowed it manually. I’ll think about another solution ; but believe me when I say that this version is better, the svchost modification was not the only one.
Khan
Just tried the new beta and the same problem exists. Try to connect to Ventrilo and up pops “Windows Firewall Notifier has stopped working”. This time however after a bit , a popup showed that .NET error reporting also could not connect so maybe it’s a .NET problem. I also can not find any file called errors.log. It doesn’t exist.
Okay I’m going to reveal something here that I know will horrify Don. I use P2P software, in particular,µTorrent. For that program you have to have unrestricted access, both incoming and outgoing for at least the TCP and UDP protocols. I did not want to allow IPv6 connections and there is no way in the program to do that. I tried making rules to block them and I kept getting a slew of alerts telling me that the blocks had occurred and asking what I wanted to do. That was unacceptable. What I did was this. The next time an alert for an IPv6 connection came up, I clicked on block and there were no further alerts and µTorrent continued functioning under TCP and UDP. I discovered later that µTorrent had been added to the exclusions list in WFN which blocks things without producing alerts but surprisingly was only blocking IPv6 and allowing the other protocols.
I really do not see any reason to make custom blocking rules with WFN and more than that, I personally don’t see a reason to change the rules that WFN creates by default. I really don’t care about this service detection stuff for svchost. Just give it full outgoing rights because, hey, that’s what every other firewall out there does by defaul when they create rules for it. .I’m happy with the way 1.3.2 works and for me, 1.4 so far is unusable because it doesn’t work without crashing itself.
I can’t let you say that ;-)
1.4.0 is way better than the previous version, and I still have to figure out why it works perfectly on my computer (and others) while it does crash everytime on yours…
Don’t forget it’s still a beta, your help is valuable to get it fully stable and I hope you’ll give 1.4.0 another try.
I have updated the beta with minor changes, if you can redownload it (same URL)… I’d be glad if you could send me the error report (errors.log) that gets created when crashing…
Thanks!!!
Khan
As I said directly to Dch48: no need to save anything. WFN is non intrusive, just uninstall, your rules will stay in place even if you choose to reallow outgoing connections while uninstalling (they won’t be used, that’s all).
Second point: regarding the bug of remaining “blocking rules”… it’s not a bug, it’s a feature: WFN does NOT create any blocking rule, because it could be too restrictive for a standard user. That’s why I’m talking about “exceptions”, they only target items that will be ignored when blocked by default by the Windows firewall :-)
Khan
I think you can export your firewall rules in the WIN 7 Firewall GUI? If so, then you could import rules after cleanup.
BTW – I have had ver. 1.3.2 lockup on me with .NET 2.0 log file errors. I tried everything short of a total wipe out that you are proposing to fix the problem. Let PC sit over night and rebooted – and problem magically disappeared.
Also ver. 1.3.2 is buggy. When I change rules in WIN 7 GUI some are not reflected in WFN GUI. Primarily when I delete a rule from the WIN7 firewall GUI, it is not deleted from the WFN GUI block area.
Hi Steve,
Glad you like WFN! But as for Don, I can’t guess your email address ;-)
@Everybody
To make it easier, here is a download link: http://wokhan.online.fr/progs/WFN_1.4.0b.zip
Please do NOT distribute this version, even if it’s close to a final one. It’s stable, it’s working, but I don’t want a beta to fly around out of control ;-)
To specialized freeware websites: please do not use the link above for the same reason.
To “install” it: as usual, extract the archive in a dedicated folder and launch the exe. If you already enabled a previous version, please use the “Uninstall…” button in the main window (either with this exe or the previous one, doesn’t matter) and then relaunch the application to reinstall 1.4.0b.
Please read the provided readme.txt file if you’re not familiar with WFN (it contains a small changelog as well).
If you have any trouble and can’t uninstall using the exe, launch DisableWFN.cmd.
If you have any feedback, please send me an email (as said, using the form on my website, I’ll answer asap), to prevent this page to become a forum ^_^
Thanks
Khan
Okay, I have some bad news. I ran the uninstaller for 1.3.2 but at the second part, I left the outgoing on so I wouldn’t lose the rules I had. Then I enabled 1.4 and disabled both the blanket svchost rule and the rule for Windows Update. I tried to run Windows Update and after a bit, it said it couldn’t connect and gave the error that means no connection to the server. There was no alert from WFN at all .The same thing happened with Windows Time.
More bad news. I ran the uninstall fully this time, rebooted and then turned WFN back on after deleting the rule for Ventrilo (a voice chat program) . I attempted to run Ventrilo and got a popup saying that WFN had stopped working and it would be shut down. I probably need to uninstall WFN again and completely delete it’s folder and most likely set Windows Firewall back to the default settings wiping out all my custom rules before trying the new WFN again. I really don’t want to do that.
Khan,
Hi. Love your program. Would like it very much if you could email me the “private” beta v1.4.0. as I anxious to test it out.
Thanks in advance.
Steve
@Don: I sure will, but I might need your email address ;-)
@Dch48 : can you please try again? You can also send me a mail directly, since my email address is almost the same than my website one (just replace the first dot with a “@”).
If you can’t, I’ll post a link here, the beta is not “that” private ^_^
Khan
HI Khan,
Yes, please email me a zipped ver. of the new release. Also instructions on install and uninstall if I have problems with the new ver.
Hi,
For those interested in the next version, I can send you the “private” beta of v1.4.0: feel free to ask through the message form on my website (at the bottom).
@Don & Dch48: I’d be glad if you want to give it a try since I made this version following your posts here :-) I’m really busy at the moment and can’t test as much as I wanted to…
Thanks!
Khan
I would be interested in trying out the new version but I tried to leave a message from your website and it said something about spam being detected and the mail not being sent so I don’t know if it went through or not.
I got tired of multiple alerts for svchost so, for the time being, I have returned to allowing it to connect whenever and however it pleases. This is the default behavior of the Firewall and is actually the way other 3rd party Firewalls create default rules for it. I’ve never had a problem with allowing it that way.
I’m not getting any alerts for it except for the occasional mysterious one when coming out of standby that says that it’s trying to connect to another computer in my network on port 0 even though I have a rule that is supposed to allow all connections on all ports within the ip range of my network and even once it tried to connect to IP 0.0.0.0 on port 6. I still don’t know what that one was about. I just tell it to accept for that attempt only and then to close the connection.
Fantastic! I can’t wait for the new release. Svchost.exe is still giving me fits in the area of identifying services requesting firewall access in WIN 7.
Hi,
@Don & Dch48
Thank you for investigating. I’m currently really busy but I read everything you’re posting here, and I will improve the svchost / services management logic as soon as possible.
I’ve been considering something similar to Don’s method, but hoped that there were better ways (using Windows APIs or alike). It doesn’t seem to, so I’ll give it a try, hopefully before mid-october!
Of course I’ll post a comment here when it’s done :)
Have a nice day
Khan
Hi,
I started working on a “service identification routine” one hour ago, it works as expected. WFN services support has thus been way improved and svchost is no longer considered as a standard application.
I’m still tweaking the code, but I should be able to release a private beta today (or maybe tomorrow, since I’ll be mostly away today), meaning that a new version should come next week (except if I feel confident enough to reduce the beta testing period ;-) ).
Stay tuned !
Khan
I have also seen that some of the default svchost rules are for ports other than 80 and 443 and not always through TCP. Windows Time uses UDP and port 123.
I have found a somewhat “brute force” method of determining what svchost service is executing when a popup alert is generated by WFN. This works for WIN 7 x64 SP1. I also assume it will work for XP and Vista.
1. Keep the WFN popup visible on the desktop and note the IP address and port shown.
2. open a command prompt window as admin.
3. Enter the following minus the quotes after the command prompt – “netstat -anob”. Do not press the enter key yet.
4. Click on the Allow button on the WFN popup for svchost.exe. Immediately thereafter press the keyboard Enter key to execute the netstat command that was previously entered.
5. Scroll up in the command prompt window searching for the original blocked IP address. Once found, you will observe to left on the same line the short name of service that svchost requested.
Note that netstat command will most likely display the program name that called svchost.exe. Therefore you will not see the service short name listed under svchost.exe but under the calling program name..
6. Open up Task Manger and click on the Services tab and search for the full service name associated with the short name that was displayed as a result of the netstat command.
7. Delete the global allow firewall rule for svchost.exe that WFN generated.
8. Create a new WIN 7 firewall custom outbound rule for svchost.exe selecting the above appropriate service. For protocol I always use TCP and for destination/receiving ports I always use 80 and 443.
Note; Before adding any firewall rule for a svchost.exe service, determine that the service is a valid Windows or application generated service. Also remember that the service might be valid but intrusive e.g. Google update service, etc.
I have hardened my rules for svchost. I have a rule for Windows Update and another one for Time. I then started getting alerts for connections to the other elements of my home network so I made a rule allowing connections to all ports but only for the IP range of my network and it seems to be working fine so far. Those are the only alerts for svchost that I have gotten. If you run the notifier exe file again and look at the outbound rules, you will find many default outgoing rules for svchost where it is allowed to connect. The mystery to me is why Update and Time are NOT allowed by default when you enable the outgoing protection.
Oh forgot to mention this.
The allow outbound rule that WFN generates for svchost.exe is not just allow all services; it is a rule to allow all programs and services for svchost.exe. I don’t think that is very secure.
Congratulations on providing a much needed WIN 7 firewall add-on.
The problem I am having with svchost.exe is many popups for unknown services. I have coded outbound service rules for update, time , and for Network Awareness to handle the boot time dial-out to MS to check for network connectivity. I am still getting dial-outs from svchost.exe and it;s difficult to detemine which service is doing the outbound connection. I just added a rule for cryptograhic service since I read that can require Internet requests.
It is virtually impossible to find ref. data on which WIN 7 svchost.exe services require Internet access.
Hi “Dch48” (there was no “reply” link under your post, I guess there is a limit or something).
This version has been tested by some users before being publicly released, and none of them met this issue :-/
You may have another rule stating that System should be blocked (at least for some IP / ports), conflicting with the newly added rule; could you please check that point?
If not, could you please check if the rule has indeed been created (namely Custom rule – System)?
Thank you!
Khan
I deleted all but one of the rules for SYSTEM and so far there have been no further alerts. It did the same thing for svchost, trying to make another rule for Windows Time after the one for Windows Update was created. That rule was supposed to allow everything as well. I deleted the second rule and it hasn’t asked again.
People have been telling me that I shouldn’t have a rule for svchost that allows all protocols, ports, services, etc like the current rule does. Is there any real reason to have rules for it for every specific service and the ports that are accessed by that service? I always have allowed just a default allow all outgoing for svchost with any firewall I have used and of course the Windows Firewall in it’s default state would allow everything. These people are citing a feature in Win 7 called “hardening” that supposedly only allows specific connections and actions by system files and they claim that I am negating that by allowing all outgoing connections by any service through svchost.
Well, they are right: in a perfect world, svchost should never be allowed as a single whole, and settings should be set at a service-only level.
But you found the exact reason why I didn’t bother about that point: default Windows behavior is to allow all outgoing connections, so creating a single rule for all services should not hurt that much when changing that behavior…
If you’re an advanced user, you can set svchost to be always blocked (in WFN), and then only allow services you are currently using.
Anyway, I’m searching for a way to find out which service is trying to connect (one instance of svchost actually hosts many services, so it is not as easy as it could have been).
Khan
When you “fixed” the svchost problem ,it created a new one which caused Windows Update and other things like Windows Time not to work. I had to manually create an outgoing rule for svchost. There were also 2 other things that gave no alerts for connection and subsequently didn’t work. The game DiRT3 gave the incoming alert but nothing for outgoing and the Games For Windows Live framework would not work either because the client app and the LiveID file were being blocked with no alert. I only found the problem by looking in the blocked log.
Okay, I updated to v 1.3.2 and all the problems appear to be fixed. I tested it by deleting the rules I had manually created for svchost, DiRT3 and Ventrilo. It alerted to all 3 trying to connect and then created rules perfectly. Good job.
I am now getting alerts for outgoing connections by SYSTEM to other elements in my home network, namely the router and the other computer connected to it. I allowed the first one and it the rule says it should cover every connection type but I am getting additional alerts still for SYSTEM. I don’t need a bunch of rules accumulating for the same thing.
WFN 1.3.2 is officially out (available on my website, and soon on Major Geeks as well).
All blocked connections should now be detected properly, and 64bit related bugs have been fixed, along with many other little bugs and some code optimization.
As usual, your feedback is really valuable :-)
Khan
I’m using V1.3.0 on Win 7 Home Premium 64 bit and Windows Update is unable to connect and gives no notification. I also got no notification for the popular voice chat program Ventrilo and had to create an outgoing rule manually.
I had to remove the program once and the .exe didn’t work so I just deleted the task and then set the Win7 firewall back to defaults. I then reenabled the notifier and it worked. The first install completely cut off all internet access.
Hi,
WFN 1.3.0 has some known issues with 64bit systems, which have been solved in a newer version (coming either today or tomorrow, still being tested !).
Setting your firewall back to its defaults must have reallowed some system process (maybe IPV6 or alike), which wasn’t detected properly by WFN, this is why it failed the first time.
Khan
Hello,
Can I please have access to the latest version. For some reason this really messed up my computer and I can’t even run System Restore successfully to remove it. Clicking the exe again doesn’t work either. Need help. Thanks.
Hi Mike,
Sorry to ear that. What do you mean by “it messed up my computer” ?
To remove WFN without using the provided exe (since it indeed fails on some computers with v1.3.0), please use the following file by extracting it on your computer, then right-click on DisableWFN.cmd and choose “Run as administrator”:
http://wokhan.online.fr/progs/DisableWFN.zip
It will remove the scheduled task WFN is based on, will reallow all outgoing connections, and will disable back firewall logging for all blocked outgoing connections.
I’m sorry not to send you the latest version (still a private beta), it will soon be publicly released.
Khan
Yeah there´s 2 threads already at Wilders security about Windows Firewall Notifier.
http://www.wilderssecurity.com/showthread.php?t=307871
http://www.wilderssecurity.com/showthread.php?t=304278
Khan, I suggest you get involved there with the conversation to get even more publicity for you software. :)
Thanks for telling, I’ll subscribe to the forum.
I’m currently working with some friendly users on v1.3.2 (1.3.1 already finalized, but not improved enough for a public release).
I want next version to be working perfectly for everyone, sorry for those encountering problems with the current one…
I can’t give any release date as of now since I’m busy with other stuff, but it should be soon :-)
Thanks to all of you supporting me !
Khan
This is e-x-a-c-t-l-y what I was looking for! I’m fine with using the Windows built-in GUI for the firewall, but lack of notifications for outbound traffic was a serious oversight.
The solutions from Sphinx and Binisoft in their free versions have nothing over what is offered here, and they are both an additional layer over built-in interface, the settings not being visible by either layer – WFN recognises the already present config of the built-in tool without a problem. The option of allowing only the port the communication was detected on is an insanely cool bonus.
Thanks for the effort Khan!
Hi Barthazar,
Thank you for your nice message ! I’m working on some fixes to improve the user experience (including a fix for the bug encountered by JML above) and version 1.3.1 should be released soon.
@Martin: I hope you don’t mind if my comments make that page look like a little forum :-) Some other blogs do too, I guess I’ll have to think about a real forum !
Khan
Hey Khan,
I like your useful app :) but i have same problem as JML although im not using Vista 32bit but Win 7 32bit. I just get the windows firewall notifier has stopped working. I hope you have it fixed on your upcoming version :)
Btw, why not create topic into wilderssecurity forum? It has firewall section :) some fellas there are quite interested about you app :)
Thanks a lot for these new updates.
The exclusion of svchost is working like a charm.
I have a little modification to ask you about the windows displaying the exclusion list. Could make it resizable for resolution beginning at 1024×600 (My Viliv N5 will appreciate :-)
Merci encore …
I have these in my installed programs:
Microsoft .NET Framework 3.5 SP1
Microsoft .NET Framework 4 Client Profile
I created folder to “c:\Program Files\WindowsFirewallNotifier\”
Thank you for your answer.
Could you please check which version(s) of the .Net framework you got installed?
Thanks
^ meants to say “WindowsFirewallNotifier has stopped working”
Hi JML,
You’re the second one having this problem, I don’t know why. I’ll find a Vista box to check if it’s a problem with the new version or not, I apologize for any inconvenience…
Where did you extract the files? Local folder, network, your documents folder?
Thanks !
Khan
Doesn´t work for me. I just get “WindowsFirewall has stopped working” when I try to launch it in Vista32bit, yes with admin rights. I can see it created the Task in task manager, but that´s about it.
Version 1.3.0 is out and clearly improved… No more balloon notification, but an easier to use “permanent” dialog (still event-based, I have not added a systray icon as of now).
@Mike: I think you will appreciate some modifications I made, feel free to contact me about those ones.
I will not keep developing that fast, have to go back to work tomorrow, so no new version should come before some time.
Khan
The best tool to create rules and to control Windows Firewall that I was using until now, is “Windows Firewall Control” from binisoft.org.
Khan: I tried using Windows Firewall Notifier for a few days at the end of July and frankly couldn’t cope with the endless messages, especially regarding svchost. It was worse than anything I’d ever experienced before, even from older incarnations of Comodo Firewall. Nevertheless, the changes you’ve made in your last 2 updates are intriguing so I’ll give it a try again next week. Thanks for your continued development of the software.
Hi Mike,
Thank you for being frank (!), and for your feedback. I don’t know why you got so many notifications, maybe your system has many more services than mine (or the average user’s one) does, explaining why svchost kept trying to connect :-/
Thank you for trying again, please feel free to contact me through my website (link at the bottom) so that I can answer directly by mail.
WFN has been downloaded approx 3500 times during the last two months; I didn’t get much feedback (less than 20 persons, either by mail or on some forums / blogs), two were really negative (including yours). My goal is to only have positive reviews ;-)
Khan
So… It’s done, v1.2.0 is out, and has been improved a lot (see readme).
Khan
Hi,
I’m the author of Windows Firewall Notifier, and am glad to see you are using it (and enjoying it, by the way) !
I published an update yesterday (1.1.0), with the following modifications:
– the outgoing connection dialog has been slightly modified (now creates a rule by default, except if asked not to, so that only two buttons have to be shown).
– when directly launched through the exe, WFN shows a new screen with exceptions list, and the 500 last entries of the Windows firewall log (so that you can create rules from there using the contextual menu), along with a “uninstall” button.
Regarding the svchost problem, it should be fixed as well in this version.
For Windows Update / MSE related problems, I’ll check what’s happening asap. It seems some x64 processes are not detected properly, I don’t really know why as of now.
Feel free to contact me using the dedicated page on my website (link at the bottom).
Thanks for your feedback !
Khan
Khan, thanks for posting about the update. Keep up the good work,.
You’re welcome.
By the way, I’m already working on another version with major improvements some people are waiting for, I’ll post here when it’s done.
Khan
One problem I have found is that windows firewall notifier keeps asking me about svchost.exe… It can’t seem to create a rule to always allow the service host process, and I can’t seem to manually create this rule either.
Does anybody have any idea how to fix it? It’s driving me insane – sometimes it pops up 10 times in one minute!
Thanks a lot, it was a very good tool.
I have the same issue with the svchost.exe process. Do you have a workaround to not process the events concerning the svchost.exe process ?
windows firewall rules, gah i wish someone would explain these in detail,, which are needed , which not ,, such as “core networking – router solicitation” and the rest,, i am not a techie, but i disable all the remote access related rules ,, but i still see so many active rules incoming and outgoing,, oneday someone will hopefully put a decent explanation of what is and isnt needed for basic internet connectivity, hope you can martin! :D
War mir neu und finde ich gut. Der Blog ist scht eine gute Quelle für alles über Firewall. Danke, Bianca.
this notifier blocks MSE updates and regular win updates in win764bit,,bummer :(
How come that Microsoft, which by it own words, invest much in security, has 2 security apps with the lowest quality in the market : Windows Firewall and Microsoft Security Essentials (MSE) ?
Slightly left of field but interesting: http://arstechnica.com/microsoft/news/2011/07/internet-explorer-9-utterly-dominates-malware-blocking-stats.ars?utm_source=rss&utm_medium=rss&utm_campaign=rss
yep, microsoft made that! (Disclaimer: I am far from a microsoft fanboy – I despise IE from a usability and speed standpoint. I just hate it when people bag other people or companies based on nothing but a reputation from a decade ago…)
I wouldn’t call MSE one of the worst pieces of security software.. Far from it – both AV-comparatives.org and Vb100 gave it very decent ratings (when running under windows 7, and I think anybody who cares about security would always do best to run the lates OS). You’ll find the links to those comparatives here: http://mobile.pcmag.com/device2/article.php?section_name=&CALL_URL=http://www.pcmag.com/article2/0,2817,2376220,00.asp
I wouldn’t call it the best, but it’s far from the worst. And if you look at the average pc user who asks on yahoo q&a about security programs and has no idea (and all the mindless drones who keep recommending avg although it has underperformed for a long time) it becomes clear that providing a trustworthy, easy to use and at least relatively decent AV for the masses can only be a good thing. I myself prefer Avira, but I know a lot of my non- techsavvy friends would be confused by the notifications and couldn’t filter out the occasional false positive (which is a very important point when talking about people who don’t know how to deal with malware).
Now as for the windows firewall – I personally think that for the average, non-techy home user it is just fine, when coupled with a hardware firewall with SPI enabled, and with a decent AV and regular spyware scans.
I have a friend who well-meaningly installed zonealarm on another friends pc. The guy had no idea what all the pop-ups were and just allowed everything, meaning that any extra protection that zonealarm could offer was lost anyway. Yet he was lulled into a false sense of security which is more dangerous than anything else.
Anyway, my rant ends here ;)
hmmm I got an email notification that there was a reply, but now it’s nowhere to be seen… what happened??
Martin: Thanks for an interesting find … at first glance, this appears to be a lot like Windows 7 Firewall Control from Sphinx Software, which offers similar simple functionality in its free version, but without the graphical interface … another option is Windows Firewall Control from BiniSoft.org; it seems to offer a lot more control options – and correspondingly more complexity – than either of the other two applications … looking forward to trying out Windows Firewall Notifier to see how it stacks up to the other two.
that sounds great, I’ll give it a try.. will post a follow up comment once I can say if it works without problems..
thanks Martin, this could be very useful for me if it works!
You are welcome. Would like to hear what you have to say about it.
So far it has been working quite well! It froze up on me once, but terminating the process and retrying the program which required internet access fixed that. My only gripe is that the little pop-up balloon which notifies you that a connection was blocked doesn’t stay visible for longer. It only stays for about 5 seconds, so sometimes I’m not quick enough to click on it..
Otherwise it’s great – I’ll definitely keep using this one!