Running Windows 7 or Server 2008? You will need this patch!
Microsoft plans to release an update early next year for the company's Windows 7 and Windows Server 2008 operating systems that add support for SHA-2 update handling to them.
Updates are delivered using SHA-1 and SHA-2 currently. SHA-1 is a hashing algorithm with known weaknesses and Microsoft plans to do away with SHA-1 support in April 2019 to use SHA-2, an improved hashing algorithm, exclusively going forward.
While that is no problem for Windows 8.1, Windows 10, or the server equivalents, it is one for devices running Windows 7 or Windows Server 2008. The reason is simple: SHA-2 is not supported by these operating systems when it comes to updates.
Any update that is delivered as SHA-2 exclusively, better, signed using SHA-2, can't be verified on Windows 7 or Windows Server 2008 devices. Means, these updates don't get installed on devices running these versions of Windows anymore unless the SHA-2 update patch is installed first.
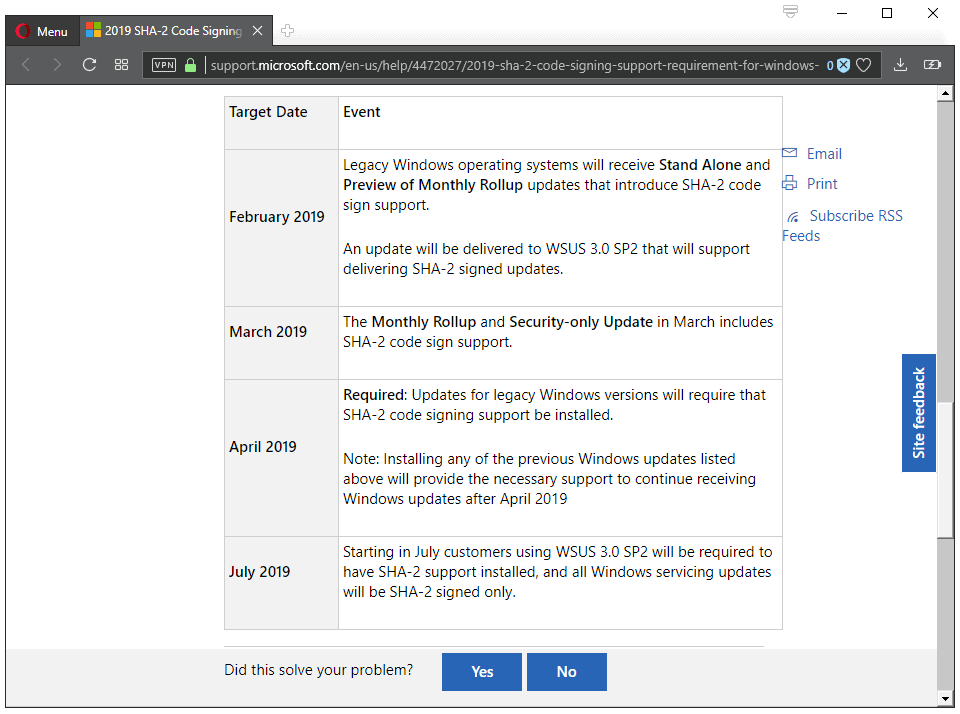
Microsoft published a timeline of events on a new support page:
- February 2019: The SHA-2 update is included in the Preview of Monthly Rollup updates and available as a standalone update as well.
- March 2019: The update is included in Monthly Rollup and Security-only updates for the operating systems.
- April 2019: Starting in April, updates released in April 2019 or later will be delivered using SHA-2 signing exclusively.
- July 2019: WSUS 3.0 SP2 will require that SHA-2 support is installed. All Windows servicing will be SHA-2 only.
Updates released prior to April 2019 will still be offered as SHA-1 signed versions as it would potentially lock systems out completely from receiving Windows Updates.
Devices that don't have the SHA-2 patch installed won't get new updates starting in April 2019 until the patch is installed on these devices.
To protect your security, Windows operating system updates are dual-signed using both the SHA-1 and SHA-2 hash algorithms to authenticate that updates come directly from Microsoft and were not tampered with during delivery. Due to weaknesses in the SHA-1 algorithm and to align to industry standards Microsoft will only sign Windows updates using the more secure SHA-2 algorithm exclusively.
As Woody Leonhard notes, it is critical that Microsoft gets the patch right the first time it is put out there in the open as there is little time to fix any issues that might come up.
Update: The patches are now available and distributed as security updates via Windows Update and other update management platforms. Check out the support article KB4472027 --Â 2019 SHA-2 Code Signing Support requirement for Windows and WSUS -- for additional information.
Simple answer is that I didn’t think to look beyond when I found it on archive.org. :-) Thanks for pointing it out.
This file is also still available on the Microsoft Catalog, so why get it from a third party at this time?:
https://www.catalog.update.microsoft.com/Search.aspx?q=KB3033929
I haven’t allowed WinUpdate since I can’t remember but it was prior to the KB’s that @AnorKnee Merce mentioned. I wanted to add these though and was able to track the files down and figured I’d put them up here in case anyone was interested.
I found KB3033929 at archive.org
https://ia600200.us.archive.org/4/items/Windows6.1KB3033929X64/Windows6.1-KB3033929-x64.msu
and KB2921916 which is inside the hotfix 471834_intl_x64_zip.exe over at GitHub.
https://github.com/CNMan/MicrosoftHotfixesList/blob/master/win7_winsrv2008r2_with_sp1/Windows7-x64.xml
The actual link to the hotfix is
https://hotfixv4.trafficmanager.net/Windows%207/Windows%20Server2008%20R2%20SP1/sp2/Fix485407/7600/free/471834_intl_x64_zip.exe
@ AnorKnee Merce
I forgot to thank you for the links which you provided with reference KB 3033929.
@ Gary D,
You are welcome.
.
Further info about SHA-2 wrt updates for AV programs on Windows machines, …….
https://success.trendmicro.com/solution/1113199-trend-micro-products-and-microsoft-s-sha-1-deprecation-policy-for-code-signing – 2 Sep 2018
<<>>
https://www.cnet.com/news/comodohacker-i-can-issue-fake-windows-updates/ – September 12, 2011
.
https://security.stackexchange.com/questions/19979/are-windows-updates-susceptible-to-tampering-eg-using-a-mitm-attack – Sep 10 ’12
.
.
Since Windows Update is invulnerable, Win 7 has already been patched for SHA-2 support in 2015 and SHA-1 has been fully deprecated by M$ in 2017, why the need for this CRITICAL update for Win 7 in Feb 2019 from M$.?
None of the 60 or so Win 7 PCs in this office has had Windows Update for nearly 2 years now. This was because we did not agree to forced telemetry or Win 10 ‘upgrades’, with tiles, candy crush, more unstoppable telemetry. Recent update quality and still unstoppable telemetry gives us no pause to reconsider.
Who in their right mind runs Windows on servers
Martin, do you mean Server 2008 or Server 2008 R2?
Both. Microsoft lists Windows Server 2008 R2 SP1 and Windows Server 2008 SP2.
I stopped update my Windows 7 x64 mid 2016 when Microsoft started with its MONTHLY LOW QUALITY ROLLUPS.
@ AnorKnee Merce, Tom Hawack et al.
I have just checked the installed updates on my Win 7 laptop.
KB 3033929 was installed on 14/5/2015 so it looks like MS is doing something a bit suspicious with this SHA2 update.
Click on AnorKnee Merce’s links to confirm that SHA2 is ALREADY installed on your hardware. If it is, this information from MS is irrelevant.
I’ve had KB3033929 installed on 2016/07/04, Windows 7.
Darn.
Paid security support will continue for windows 7 till 2023 with the updates likely leaking to the interwebs.
This is a good thing, ofcourse, assuming they get it right. Backporting features to 7 is almost always good. And I say almost because the telemetry backport was not, and will never be welcome, but thankfuly with 7 the user is still in control of the OS and not Microsoft.
“the telemetry backport was not”
Agreed. If I had any Windows 7 machines, the release of that patch would have marked the day that I stopped accepting any patches for Win 7 at all.
https://docs.microsoft.com/en-us/security-updates/securityadvisories/2015/3033929 – Availability of SHA-2 Code Signing Support for Windows 7 and Windows Server 2008 R2 – Published: March 10, 2015
.
https://charismathics.zendesk.com/hc/en-us/articles/231993568-How-to-enable-SHA2-Support-on-Windows-7 – Nov 4, 2016
.
.
According to M$’s own documentation above, Win 7 had already been patched(= KB3033929) for SHA-2 support since March 2015. What gives.?
Is M$ trying to sneak in another GWX KB3035583 and/or KB2952664 or something else.? Bear in mind that by Feb 2019, EOL for Win 7 will be just around the corner = may be M$’s last chance to hood-wink the still-remaining millions of Win 7 users into upgrading to Win 10.
.
https://www.csoonline.com/article/2879073/encryption/all-you-need-to-know-about-the-move-from-sha1-to-sha2-encryption.html
Interesting, I don’t have this update on a machine updated up to december 2017: imgur.com/CMNxhi9
For anyone who wants to check, the powershell command is: get-hotfix -id KB3033929
@ Yuliya
Windows Update in Win 7/8.1 can be set to manual, unlike Win 10’s forced auto-updates. So, you likely had Windows Update set to manual(eg “notify me but let me choose when to download and install updates”) and chose to not install KB3033929 when it was offered to your Win 7 computer in 2015.
___ Those with Windows Update set to the default of Automatic would have gotten KB3033929 in 2015 = have support for SHA-2 in Win 7.
Similarly, that was how many Win 7 users manually avoided the install of GWX KB3035583 and KB2952664 in 2015 and 2016.
I don’t update Windows 7 since two years now so I won’t have to go through this : installing an update to allow further Windows Updates with SHA-2 handled by Windows 7. Generally speaking Microsoft updates are all calibrated on Windows 10 aka “The Nightmare” and consequently previous versions have to swim or sink. Let mine sink, meanwhile it swims.
“As Woody Leonhard notes, it is critical that Microsoft gets the patch right the first time it is put out there in the open as there is little time to fix any issues that might come up.”
I think I should start an office betting pool on whether or not this update will be borked.
I don’t get it
Why would MS introduce SHA-2 support in “Legacy Windows OSs” when the end of life (January 14, 2020) for these OSs is just a few months away?
Yup, you guessed it right ;-)
14 months is a bit more than a “few months away”. If Microsoft didn’t do this, that would be over a year of security updates that would be missed!
Any bets that Microsoft will screw things up before the patch becomes available making it impossible to install?
Count me in. Not to mention that a bet can always be lost if a miracle arises.