Windows Defender vulnerability discovered and fixed
Microsoft published the Security Advisory 4022344 yesterday which informs customers about a security vulnerability in the Malware Protection Engine.
The Microsoft Malware Protection Engine is used by various Microsoft products, including Windows Defender and Microsoft Security Essentials on consumer PCs, and products such as Microsoft Endpoint Protection, Microsoft Forefront, Microsoft System Center Endpoint Protection, or Windows Intune Endpoint Protection on the business side.
All products are affected by a critical vulnerability that allows remote code executions if a program that uses the Microsoft Malware Protection Engine scans a crafted file. Attackers may execute arbitrary code on the system if the vulnerability is exploited successfully.
The update addresses a vulnerability that could allow remote code execution if the Microsoft Malware Protection Engine scans a specially crafted file. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system.
Windows Defender vulnerability discovered and fixed
Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich discovered what Tavis called the "worst Windows remote code exec in recent memory" on May 6th, 2017. The researchers notified Microsoft about the vulnerability, and kept information hidden from the public to give Microsoft 90 days to fix the vulnerability.
Microsoft managed to create a patch for the vulnerability, and has pushed out new versions of Windows Defender and other Microsoft products already to customers.
Windows customers who have any of the mentioned products installed on their devices need to make sure that it is up to date.
On Windows 10 for instance, you'd do that in the following way:
- Tap on the Windows-key on the computer keyboard, type Windows Defender, and hit the Enter-key to load the program.
- If you run Windows 10 Creators Update, you get the new Windows Defender Security Center.
- Click on the cogwheel icon in the lower left part of the interface.
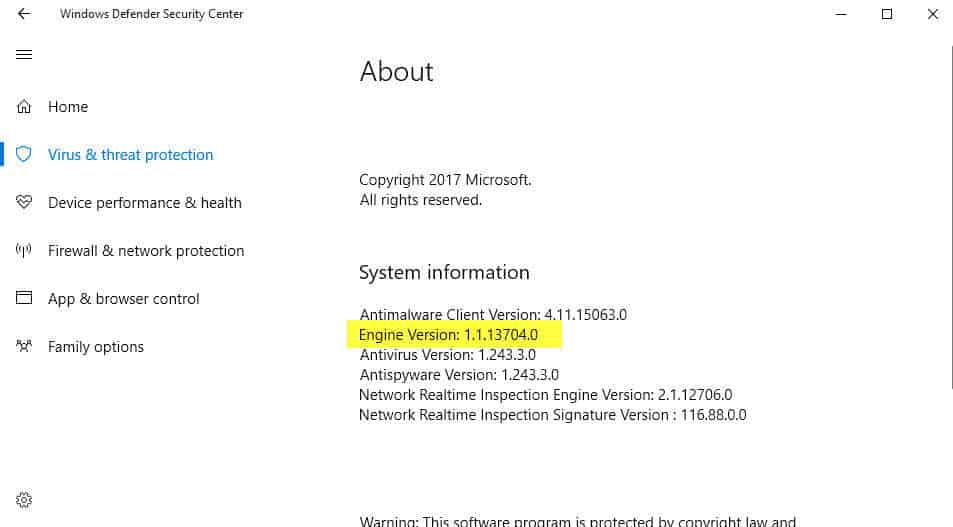
- Select About on the next page.
Check the "Engine Version" on the page, and make sure it is at the very least 1.1.13704.0.
Windows Defender updates are available through Windows Update, and Microsoft has published information on how to update the Microsoft Malware Protection Engine on various versions of Windows and in the various products affected by the vulnerability.
The Malware Protection Center on the Microsoft website offers information on updating Microsoft antimalware products manually.
More information on the vulnerability
Google released the vulnerability report on the Project Zero website. This makes it even more pressing to update the engine Microsoft's security programs use as attackers may use the information to craft attacks against computer systems that are still vulnerable.
Vulnerabilities in MsMpEng are among the most severe possible in Windows, due to the privilege, accessibility, and ubiquity of the service.
The core component of MsMpEng responsible for scanning and analysis is called mpengine. Mpengine is a vast and complex attack surface, comprising of handlers for dozens of esoteric archive formats, executable packers and cryptors, full system emulators and interpreters for various architectures and languages, and so on. All of this code is accessible to remote attackers.
NScript is the component of mpengine that evaluates any filesystem or network activity that looks like JavaScript. To be clear, this is an unsandboxed and highly privileged JavaScript interpreter that is used to evaluate untrusted code, by default on all modern Windows systems. This is as surprising as it sounds.
Now You: Which security software do you use on your system, and why?
I assume my old Windows 7 MSE is vunerable too, since the program it self was last updated in 2016 (product version 4.9… etc.)
I only use Enhanced Mitigation Experience Toolkit (EMET) 5.5 and my brain on WIn 7 x64
The main way to avoid infection is to minimize risk of your browsing. My copy of Pale Moon is locked down and I do not visit certain parts of the web. I have Superantispyware which I occasionally scan with for two reasons: an extra set of eyes and to rid me those pesky trackers. Spywareblaster is used to prevent me from accidentally exposing my computer to bad sites and avoid tracking cookies and active-X controls. I have Microsoft Security Essentials Prerelease which I do not turn on to monitor, but use it to run a scan occasionally for an extra set of eyes. My main security software is the paid version of Avast!, which is the only one I have on all the time.
Now THAT’s funny. I knew msoft software was generally poorly written, but their best security offering is even worse than an attachment-loaded email!
Folks, Ubuntu is not that hard to adapt to. Yes, the first two or so days are like trying to climb a 10-foot high brick wall, but once over the wall, life pretty much returns to normal. Well, “normal” without the constant barrage of the disgracefully repetitious security loop-loops.
> Now THAT’s funny. I knew msoft software was generally poorly written, but their best security offering is even worse than an attachment-loaded email!
Yeah, go figure. I’ve heard of lousy AV software before but this is utterly pathetic.
M$ does a sh!t job when it comes to the anti-virus game and they should get out of it. Running and developing an OS, they’ve got massive amounts of other problems to deal with. Let the security experts handle it instead of this amateurish band aid that even Enterprises (if they’re worth their salt) wouldn’t rely on.
I’m using Avira… when I look at the Defender About page, all these version numbers are simply “0.0.0.0”
Now how do I apply this update?
On windows 10 CU I use Defender which acknowledges I also run AVG Internet Security. I ran the Defender Update and AVG IS Update yesterday, and on a cold start today, AVG IS detected and removed a Trojan. I’m pleased with both products as I believe Defender is redesigned in CU, and AVG IS has demonstrated it is effective for me.
so they discovered this problem three days ago? and there already is a fix? sounds like the sky is falling again to me. or does anyone proofread articles anymore?
By the looks of it Windows 7 was unaffected by this. MsMpEng is nowhere to be found here as MSE is not installed. I strongly encourage not to use any antivirus. I find them all, save for Kaspersky, completely useless. They slow down the system for no reason and are extremely intrusive pieces of software. I quit using any a/v software few years ago and never had a problem since then. All I was doing before was constantly fighting against it due to false positives. Many a/v software flag even NirSoft programs as malicious, and I have many of these tiny programs for different tasks from other developers as well, also getting flagged.
Ever since I switched to Windows 10 – something I told myself I would never do, but it kind of happened on its own after I got a new AMD Ryzen system and didn’t want to bother with the USB driver issue on Win 7 installations – I have been happy to use the Microsoft on-board tools.
Prior to that I had been a long-time user of Avast for close to a decade, but it has been years since I was last truly happy with it. There are just too many decisions I didn’t like and too many issues and bugs to torture myself with it on this new device as well.
To be honest, I am quite happy with how Windows Defender performed so far. It has been surprisingly relaxing to go from an antivirus that kept bugging me with popups all the freaking time to a tool that stays in the background until it requires my attention. It is much like the difference between a young and hipster personal assistant (Avast) compared with an old-school butler (Microsoft). Most notably, I am happy to have gotten rid of the many false-positive malware claims Avast kept finding. I was never comfortable going into the settings and adding exceptions for certain executable filenames or even whole folder structures because that is invitation enough to be exploited, especially when they’re not located within the permissions-restricted folder structure on the system drive.
To make a long story short, I am tend to be a Microsoft skeptic, but I use their software anyway and this time it’s easy to admit, they have the superior offer. Since 90 percent of all infections happen because and not in spite of the person operating the system, I feel a dedicated antivirus/malware application is overkill for me. I still use VirusTotal for the more suspect files I receive or download and there’s always the nuclear option of using a VM if the case warrants it. Even that can be breached but hey, you shouldn’t use a computer connected to the Internet if you are terribly afraid of what may happen.
Windows Defender/Endpoint… software is the worse ever written software in the history of computers.
In every Anti-virus/malware benchmark Defender/Endpoint come the last with a warning for users/Enterprises.
Even Microsoft acknowledged that it is crap and advised users to use a proper anti-virus application when using Defender.
Your Windows PC may have been hijacked by trojan, botnet, virus… with Defender/Endpoint you will never know.
> It has been said that the best protection is found within the operating system. Defender inside Windows 10 meets this criteria.
I had Defender on a Win7 build for about a year and it was total crap. It didn’t detect anything at all. The only reason I used it was because I was too cheap to pay for another subscription.
After about a year of Malwarebytes and ComboFix detecting crap and having to do cleanups, I dumped Defender and subscribed to Bitdefender and have been happy ever since. Much fewer detections and cleanups.
Windoze Defender is junk for lazy M$ fanboys who think they’re invulnerable to malware. The “it won’t happen to me” attitude. Uh-huh…
In fact, it has come to light that many A/V software products are introducing vulnerabilities. What good is the ability to detect when the A/V software installation is creating attack vectors? Will it accuse itself?
It has been said that the best protection is found within the operating system. Defender inside Windows 10 meets this criteria.
Microsoft is selling ATP as a service and is succeeding at detecting and addressing patterns of attack. This research will flow to Windows 10 and Defender.
I’m using Defender, because it’s simple and it’s inside the OS. Free version of other AV show advertising banners in pop-ups.