Microsoft Patch Day November 2011 Overview
Today Microsoft has released security updates exclusively for Microsoft Windows operating systems. Of the four bulletins released today, one has received the maximum severity rating of critical while the other three have received one of important. Maximum severity means that at least one Microsoft operating system has received the critical vulnerability rating.
In this case, the critical rating applies to all operating systems that Microsoft supplies with security patches. This includes the client operating systems Windows XP, Vista and Windows 7 as well as the server operating systems Windows Server 2008 and 2008 R2.
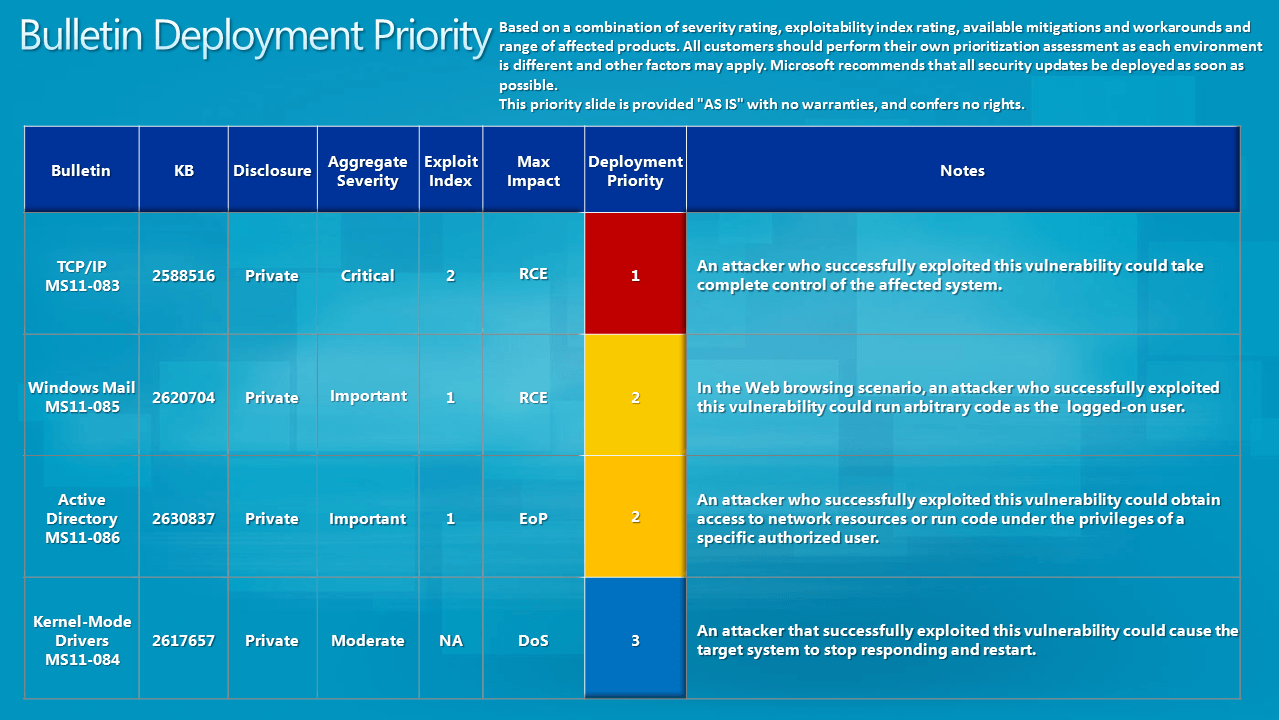
Here are two graphs visualizing the severity and exploitability index and the bulletin deployment priority.
Here is the list of security bulletins released in November 2011 by Microsoft.
- MS11-083 - Vulnerability in TCP/IP Could Allow Remote Code Execution (2588516) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker sends a continuous flow of specially crafted UDP packets to a closed port on a target system.
- MS11-085 - Vulnerability in Windows Mail and Windows Meeting Space Could Allow Remote Code Execution (2620704) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a legitimate file (such as an .eml or .wcinv file) that is located in the same network directory as a specially crafted dynamic link library (DLL) file. Then, while opening the legitimate file, Windows Mail or Windows Meeting Space could attempt to load the DLL file and execute any code it contained. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a legitimate file (such as an .eml or .wcinv file) from this location that is then loaded by a vulnerable application.
- MS11-086 - Vulnerability in Active Directory Could Allow Elevation of Privilege (2630837) - This security update resolves a privately reported vulnerability in Active Directory, Active Directory Application Mode (ADAM), and Active Directory Lightweight Directory Service (AD LDS). The vulnerability could allow elevation of privilege if Active Directory is configured to use LDAP over SSL (LDAPS) and an attacker acquires a revoked certificate that is associated with a valid domain account and then uses that revoked certificate to authenticate to the Active Directory domain. By default, Active Directory is not configured to use LDAP over SSL.
- MS11-084 - Vulnerability in Windows Kernel-Mode Drivers Could Allow Denial of Service (2617657) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow denial of service if a user opens a specially crafted TrueType font file as an e-mail attachment or navigates to a network share or WebDAV location containing a specially crafted TrueType font file. For an attack to be successful, a user must visit the untrusted remote file system location or WebDAV share containing the specially crafted TrueType font file, or open the file as an e-mail attachment. In all cases, however, an attacker would have no way to force users to perform these actions. Instead, an attacker would have to persuade users to do so, typically by getting them to click a link in an e-mail message or Instant Messenger message.
Microsoft has published a video in which Jerry Bryant discusses this month's bulletins (Silverlight required).
Additional information about this month's security bulletins are available on the Technet Blog page and the Microsoft Security bulletin Summary for November 2011.
The updates are already available on Windows Update. Users who have started their computer earlier today may need to run a manual update check in Windows Update.
The updates will also be available shortly at Microsoft's Download center.
Advertisement
Hoi Martin, A bit late (this because I needed to install main win-7 after 7 mounts hard using again) but thanks again for this great story.