Virus scanning service VirusTotal releases VT4Browsers extension for Chrome and Firefox
VirusTotal is a useful online virus scanning service that Google acquired in 2012. The developers of the service have released VT4Browsers, an updated web browser extension for Firefox and Google Chrome.
VT4Browsers submits certain file downloads automatically to the virus scanning service for checking. Users may then click on a link displayed by the extension to open the scan results on the VirusTotal website.
The extension submits downloads with the exception of document file types by default. Users of the extension may change the default behavior in the settings.
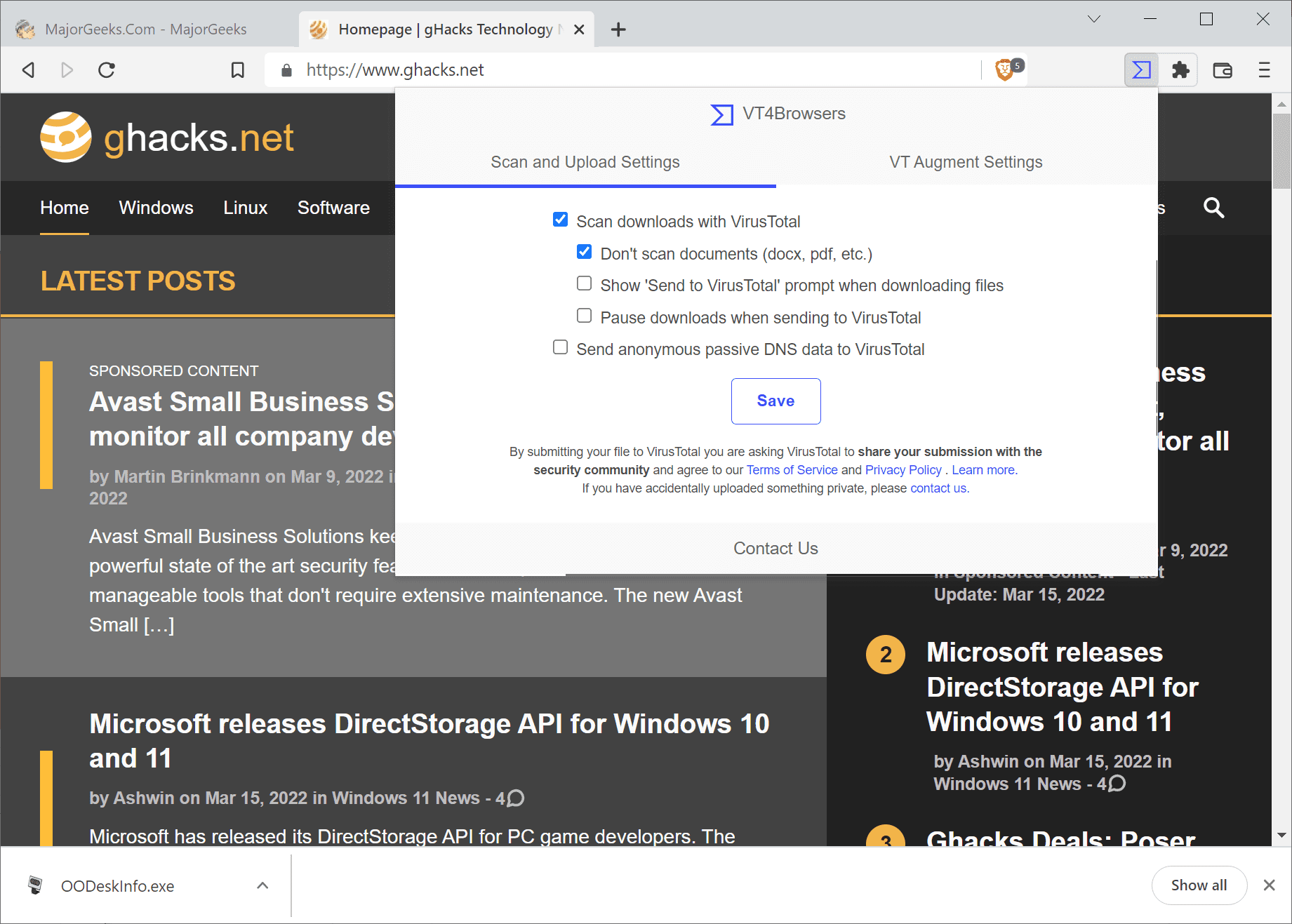
The settings are divided into a public part and a part that is reserved to users with an API key. The public part includes the following options:
- Scan downloads with VirusTotal-- this determines whether file downloads are submitted to the service.,
- Don't scan documents -- this determines whether document file types, e.g., pdf or docx, are submitted. These file types are not submitted by default.
- Show "Sent to VirusTotal" prompt when downloading files -- displays a prompt to the user to submit downloads on demand and not automatically.
- Pause downloads when sending to VirusTotal -- do not process downloads until files have been submitted to VirusTotal.
- Send anonymous passive DNS data to VirusTotal -- submits domain name to IP address mappings for DNS resolutions the browser performs to VirusTotal. Default set to on.
Users may want to disable the sending of anonymous passive DNS data and enable the "sent to VirusTotal" prompt to be in control of the sending. The extension does not reveal all document file types that it blocks from sending, and most users may want to be in control when it comes to the sending of files to the service.
The main change that the new VirusTotal browser extension introduces is support for the VT Augment widget. It allows users to link an API key in the extension to use advanced functionality.
The functionality consumes API lookups whenever it is used. It allows users to "highlight or enrich ioCs (hashes, domains, IPs, URLs) automatically.
The difference between highlighting and enrichment is the following:
The highlight feature identifies IoCs and adds a VirusTotal icon next to each IoC. When the icon is clicked an API call is performed to embed the IoC detection ratio and display the VT AUGMENT widget as a side panel. API quota is only consumed when you click on an IoC icon.
For each IoC identified in a site, the enrichment feature automatically queries the VT API and embeds the IoC’s security vendors detection ratio/score next to the IoC. Clicking on the VirusTotal icon or detection ratio next to each IoC will then display the VT AUGMENT widget as a side panel. This setting can generate API lookup spikes and is only recommended for premium API keys.
A support article on the VirusTotal website provides additional information on the new options.
VT4Browsers is available for Chrome and Firefox officially. Most Chromium-based browsers should install the extension without any issues. A quick test in Brave and Vivaldi was successful in that regard.
Now You: do you use Virustotal or other virus scanning services?
Here is what it blocks from the source code:
this.IGNORED_FILE_TYPES = [
’eml’,
‘pdf’,
‘docx’,
‘doc’,
‘xlsx’,
‘xls’,
‘txt’,
‘ppt’,
‘pptx’,
‘csv’,
];
And here is more telling it to check the IGNORED_FILE_TYPES list:
// If the settings to send doc files are not enabled,
// check the file is not a document
if (this.settings[‘excludefilesdocs’]) {
let fileExtension = filename.split(‘.’);
fileExtension = fileExtension[fileExtension.length – 1];
for (let i = 0; i < this.IGNORED_FILE_TYPES.length; i++) {
if (fileExtension.toUpperCase() ==
this.IGNORED_FILE_TYPES[i].toUpperCase()) {
this.sendMessage(tabId, 'error', null, {
message: 'File type not sent per user settings',
downloadId: download.id
});
return;
And can verify here:
https://crxcavator.io/source/efbjojhplkelaegfbieplglfidafgoka/4.0.4?file=src%2Fbackground.js&platform=Chrome
And there ya go! Hope this helps you determine what it is and is not scanning with the docs scanning turned off :)
VT Hash Check is better:
https://github.com/charonn0/VT-Hash
adds to right-click menu to scan any file in explorer
program pings VT with the hash first to see if its the database, if it is a popup box shows the results, if it isnt it allows you to upload the file.
you only have to waste time with the browser if you need to scan a large file or if you want to rescan one that hasn’t been scanned in years
requires a free API key from VirusTotal though
If you read the VirusTotal, Terms of Service, it explains any sample you submit can be shared. Personally, I wouldn’t send sensitive data like files containing passwords or personal information you didn’t want to be made available to other entities.
By submitting data, you are agreeing to their Terms of Service and Privacy Policy, and to the sharing of your Sample submission with the security community. Please do not submit any personal information; VirusTotal is not responsible for the contents of your submission.
A virus scanning service run by a company that is itself a virus on humanity.
Oh, the irony :)
No thank you. Third plugins may listen my communications.
Don’t send your personal files (for example passwords…) to Virus total, if I am not wrong, some individuals (with access) can download it
@A
« Don’t send your personal files (for example passwords…) to Virus total »
Access? Do you have the source of this info?
@Martin P.
Well their Privacy Policy basically says they own what you upload but go ahead and upload your passwords. I’m sure it’ll be fine.
‘Jotti’s malware scan’ [https://virusscan.jotti.org/] “is a free service that lets you scan suspicious files with several anti-virus programs.”. Not sure VirusTotal and its myriad of detection engines (some of which look more like starlets than stars) provides much more security reliability. Manual file(s) submission only, which anyway is my choice.
Jotti has always been excellent, but this is several tads more convenient.
Terribly outdated service. The software hasn’t been updated for many years.
It’s terribly outdated though.
@Tom Hawack: thank you.
I’ve been using a right-click tool (every file)
https://github.com/Genbox/VirusTotalContextMenu
Sometimes it fails to open in VT results in the browser and there is a limit on the size (large ones you need to navigate to VT then choose the upload option).
I like the lazy option. Provided it works for every file every time the switch becomes permanent. The other issue is rescanning. During the CCleaner infection I learnt results don’t update in VT automatically as vendors discover malware. VT needs to rescan to get updated results from vendors.
I’m using this one and add it to the right click “send to”:
https://github.com/SamuelTulach/VirusTotalUploader
You can also “drag & drop” files on the open program
It fails sometimes too to open in VT results…
vt extension asked whether I wanted a file checked today. I said yes. The file downloaded. No VT check performed.
The extension is old. Not in the way of outdated, but first released. I’ve been using it since at least 2016.
Suggestions please about how to scan files above 650mb? VirusTotal does not take those…
You don’t need to scan 650MB. Just send the HASH to VirusTotal.
Didn’t they should scan the file automatically after downloaded without to send it? :[
I use VirusTotal manually, though I would like to use another, non-Google way. Any suggestions?
I would try https://virusscan.jotti.org/
@Leland: thank you.
Leland / Klass – Have you read the privacy policy of https://virusscan.jotti.org/? It’s horrendous.
“We store files you send in for scanning and share these with anti-malware companies”, “…we log information that your web browser provides us with, such as your current IP address, operating system, and possibly the URL of the website you came from”.
And “Our advertisers place cookies and collect information you provide them with, such as your IP address, browser, visits to other websites”.
You should read the privacy policies of these web sites before sending any information to them to know what information they are collecting about you and sending onto third parties.
If, however, you are fine with them collecting this information on you, then fair enough.
@Anonymous, Blacklight’s results for [virusscan.jotti.org] :
—
3 Ad trackers found on this site. This is less than half the average of seven that we found on popular sites.
1 Third-party cookie found. This is less than half the average of three that we found on popular sites.
Tracking that evades cookie blockers wasn’t found.
Session recording services not found on this website.
We did not find this website capturing keystrokes.
Facebook Pixel not found on this website.
Google Analytics’ “remarketing audiences” feature not found.
—
A perfect illustration of how a site which is clear, transparent about what it stores of its visitors’ data can initiate over-reactions when in fact it is relatively respectful compared to many sites which track and store far more without ever stating it clearly : be honest about your business affairs and you’ll be crucified, hide them and you’ll be glorified. It is because too many of us react as you do, focusing on the top of the iceberg, that dishonesty continues to be considered as the way to go for business.
@Tom Hawack
Fair comments Tom, and I respect Blacklight’s results as well, as Blacklight is a member of the privacyguides.org team.
I, and other privacy users, just want to make people aware of, despite web sites privacy policies being transparent and clear, of what some web sites do collect and store about those who use the web site and its products, like IP addresses, location and user agents. If the users after knowing this is alright with it, then fair enough. That’s their choice.
Others like to be more private and try to avoid giving this information, or as much of it as possible, to avoid things like targeted advertising.
It all comes down to what each individual user is comfortable with.
@Anonymous, I understand your point.
Blacklight focuses on trackers, mainly cookies.
You mentioned in your first comment the privacy policy stating “we [the site] log information that your web browser provides us with, such as your current IP address, operating system, and possibly the URL of the website you came from”.
They site has the honesty to make it clear because we all know that practically all sites log such users’ data as well as the referer (referrer) and seldom mention it clearly. This practice is so widely adopted that dedicated tools exist (user-agent switchers, referer managers…).
So what I meant and mean is that emphasizing on the transparency of a website’s privacy policy (be it questionable) may mislead to the value of this site. Of course we’d all like zero logs, zero tracking (there are such sites!) but, call it tolerance, call it distinguishing the bad from the worst may lead to a better definition of a site’s honesty. That’s all.
Remains that we agree with many others that privacy and security are essential.
@Tom Hawack Fair comments Tom, and I respect Blacklight’s results as well, as he/she is part of the privacyguides.org team.
I, as do other privacy experts, just want people to be aware of what the privacy policies of some web sites do contain and the information they will be collecting on people who use their web sites / products. If people are fine with privacy policies, even if they are transparent, in saying they will store information like IP addresses and user agents of the user, then no problems. It’s their choice.
Others like to withhold that information from web sites if possible to avoid things like targeted advertising.
It’s all down to the user themselves and what they are comfortable with.
@anonymous: many thanks for the heads up. You are totally right, of course, reading the privacy policy is the 1st basic requirement.
I have not used Jotti yet, so milk spilled, fortunately.
Which service do you use, if I may ask?
@Klaas No Problem Klaas. It’s something simple that more users should do before using any website or downloading anything.
All I use is my anti-virus to scan an item that I download onto a spare memory stick first, so that nothing on my computer, or back up memory sticks, are at risk. Then, if all is clean, I move them to where I want.
As for checking websites, I just let Ublock Origin (along with other privacy extensions) and its various lists try to keep me safe and warn me if any websites are dodgy or contain anything.
Hope this helps!
@Anonymous: I have been using uBO for years in all of the major browsers that I use(d).
I have been on a Mac for nigh on 3 years without an anti-virus program and have never had any hassles. I have been using VirusTotal, but would like to move to a non-Google site.
Anyway, thanks for your help, esp. the heads-up.
I use VT manually (HashMyFiles has a nice right-click Windows Explorer option) and will continue to do it manually. The fact that this is all Google goodies gives me the willies and I’ll keep it off my browser – even if its privacy is fine on paper which I’m not sure, maybe it is but probably not.
What are you downloading? Aside from malware scanning ,…Google/gov wants to know this too.