Emsisoft Emergency Kit is a free portable antivirus that you can use as a secondary scanner or to disinfect PCs
Emsisoft Emergency Kit has been around for a long time and ranks high in my troubleshooting arsenal. It has been a while since it was reviewed on gHacks.
So, let's take a tour of the latest version and I'll also tell you how it helped me with a problem I ran into recently.
First, the basics: the emergency kit is available for Windows 7 and Windows Server 2008 R2 or newer client and server versions including Windows 10 and Windows Server 2019. The download has a size of 326 Megabytes at the time of writing. The program comes as a self-extracting installer; it does not need to be installed but is extracted to a location when you execute it. You may then run the program from that location, even if it is on a USB drive.
Tip: any copy is set up to join the "Anti-Malware Network" automatically which includes "online processing of statistics on detected malware and program behavior". You can turn this off in the Settings under Privacy.
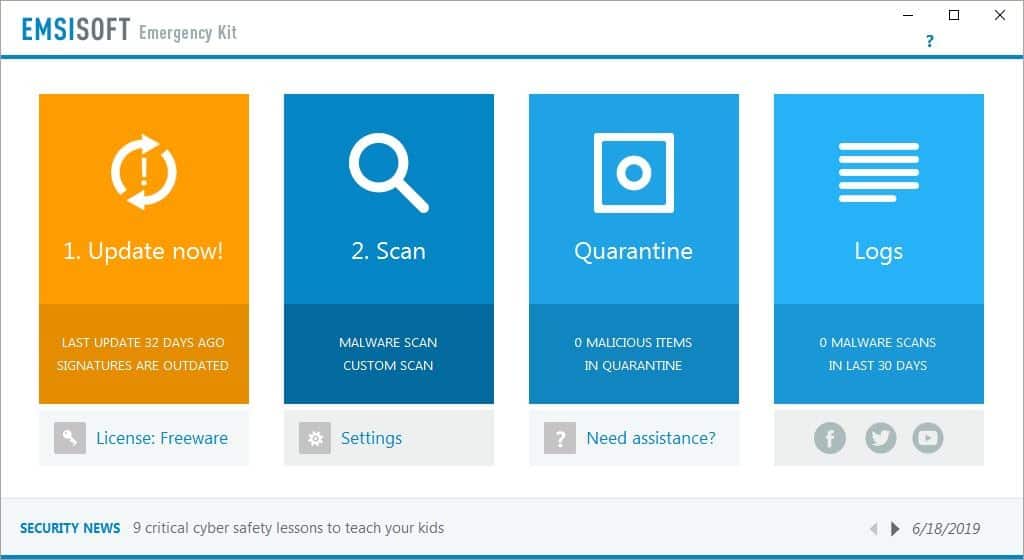
Emsisoft Emergency Kit - The Interface
The "Start Emergency Kit Scanner.exe" is for the GUI version, which we will discuss here. Optionally, you can use the command line scanner should you want to. The interface of Emergency Kit consists of four sections:
- Update
- Scan
- Quarantine
- Logs
The Update option allows you to keep Emsisoft Emergency Kit and its virus-definitions up-to-date. You can see the time-stamp when the last update was done on the banner and may want to run a check for updates on first start to make sure virus definitions and program modules are up to date.
The Scan option is the heart of the program. There are 3 types of scans that you can run using Emsisoft Emergency Kit.
- Quick Scan - This option scans all running programs for malicious activity.
- Malware Scan - This scan checks the normal places in Windows, that are normally targeted by malware.
- Custom Scan - This is the option you want to choose for scanning specific folders, partitions, and drives.
Select a scan to run it, and wait for the results screen to be displayed. The Settings menu in Emergency Kit can be accessed just below the Scan banner. You can set it to detect potentially unwanted programs, use more system resources for scanning, and set a post-scan option (report, quarantine, report + shutdown, quarantine + shutdown). The options may be simple, but the scanning and malware removal process is very efficient; it might save your otherwise unobtainable data.
The Quarantine is the malware vault, where the program isolates any threats that were detected. You can use it to analyze the malware, delete the contents, or restore files. You can manually quarantine suspicious files using the "Add files" option.
The Logs section keeps a record of all scans that were run (including the results), updates that were completed, etc. The License option can be used to convert the freeware license to a paid one, if you decide to buy the real-time version of the program. There is a news ticker on the bottom (or middle right) of the antivirus' interface which links to blog articles on the company's website. They can be turned off with a click on "don't show again".
Emsisoft Emergency Kit - Usage
Emsisoft Emergency Kit is a portable antivirus, you don't have to install it on your computer. It can be used even if you have another antivirus installed on the computer, and the applications won't conflict because Emergency Kit does not have a real-time protection feature.
By default, the program's self-extractor places the content in the C:\EEK folder. You can run the program to scan your PC for malware and disinfect it for free. You can copy this folder to a USB drive and use it to disinfect other computers as well. The best part of course, is that Emsisoft Emergency Kit is free.
Emissoft Emergency Kit displays a prompt when it finds suspicious files that suggests to install one of its core products that extends the functionality of the emergency kit on the device. The prompt makes no mention of the fact that agreeing to the installation installs a trial product, Emisoft Anti-Malware Home, that is available for a 30-day trial only; it needs to be uninstalled or purchased after that period. Emsisoft needs to make this clearer.
Note that you get that prompt each time you run a scan and anything is found. You will also get an exit-prompt when you close the application.
My personal experience with Emsisoft Emergency Kit
About a year ago, an elderly friend of mine asked me for assistance with his laptop. This was a Dell laptop which he brought from the USÂ and it had Windows 10 Home pre-installed. I don't remember the model number but it had a touch screen.
He told me that sometimes he gets ads on the computer, even when the browser is not running. He didn't want to wipe the drive, because it had a lot of important data. I told him to format the drive later, as a precaution. The first thing I noticed, is that he hadn't been using any antivirus on the laptop.
Note: Windows Defender is good for most users, but you need at least one extra tool to be safe, an ad-blocker. You'll see why I say this.
This is how I approached the issue:
- Disabled the Wi-Fi on the laptop.
- Connected the charger and let the laptop sit for a while.
- After a while, I saw a pop-up screen.
I don't have any photos or a screenshot of the malware, because I was more worried about helping him than to take pictures. But I distinctly remember the name of the malware, ReImagePlus. It is in fact, a rogue application. The laptop was painfully slow, and I was quite certain this was because of the malware. I had seen enough so I kept the laptop aside and copied the Emsisoft Emergency Kit folder from my PC to a USB Flash drive and transferred it to the laptop.
Surprisingly, I was able to uninstall the malicious program from the Control Panel. I checked the browser (Google Chrome) and found that the bookmarks bar on the top had multiple links to the rogue app so the browser had been hijacked as well. I didn't have to guess how this happened, because I could see there was no ad-blocker installed.
I ran a malware scan using Emsisoft Emergency Kit: the program detected some remnants and disinfected them in the first scan. But when I ran a complete scan the antivirus discovered several copies of an EXE (all of which were named ReImage) in the downloads folder. I quarantined all the findings.
Now that the malware had been disinfected, I connected it to my Wi-Fi to download uBlock Origin and Malwarebytes. The browser redirected me to ReImagePlus, which wasn't surprising considering it was hijacked. With my friend's permission, I reset Chrome deleting all its data, installed uBlock Origin, and Malwarebytes Anti-Malware. Further scans indicated the laptop was clean and it seemed to be faster as well. I advised him to run a scan using Emsisoft Emergency Kit and Malwarebytes once a month or so.
Another instance
I recommended Emsisoft Emergency Kit to another friend recently. Actually, he had just disinfected the laptop using Hitman Pro (also my recommendation) a few minutes ago. This malware (can't find the name of it in the chat history)Â had accessed his webcam.
He had noticed the light was on when the camera was not being used and we rushed to disinfect it. But I advised him to run scans using Emsisoft Emergency Kit and Malwarebytes Anti-Malware anyway.
This friend formatted the drive after disinfecting it and reinstalled Windows.
While we are on that topic, some malware persist after a Windows reinstall (though I have personally seen that happen over a decade ago), a full format on the other hand should wipe the infection, along with all the data on the drive. But, it is still better to tackle the malware head on, and disinfect the drive first, and try to recover some of your important data. Once done, you can (and in my opinion should) reinstall Windows after formatting the drive.
Now you: Which secondary scanner do you use?
With their latest update, Emsisoft have ended support for Windows 7, 8, and 8.1.
I made a Custom Scan since, and it went through normally. This is strange, since the Custom Scan I set was broader than the Malware Scan, the latter is the default scan and it stalled midway.
I just made a similar scan with the free (and old) version of Malwarebytes. Nothing of the sort happened. The scan proceeded smoothly, with a clean bill of health.
The old 2.x version of Malwarebytes is less sufficient on detecting new threats due to the old engine and the differnces in the database syntax.
https://forums.malwarebytes.com/topic/211141-prospects-for-continued-database-updates-for-mbam-2/?tab=comments#comment-1165937
Thanks for the warning. However, I was under the impression that the new Malwarebytes had some big drawbacks (can’t remember what). One of the cases where an upgrade is really a downgrade. Does it ring a bell ?
So-called Malware Scan (recommended) stalls midway, with a message that it’s “preparing for scanning files” after having scanned a bunch of others.
Nothings happens. No progress indicator. Program uses 25 % of CPU. Ten minutes later, it’s still there. Stopped it. Worthless.
Oh, and creates 117 registry items, even though it’s supposed to be “portable”. I hate programs which do that.
Too big to be scanned by Virus Total.
Loads malware signatures every single time it is launched, even if this has been done a minute ago. After this, will ask if you want to “update”, even though you have just downloaded the freaking program. Update what ?
Not high DPI-aware. Either blurry, or tiny UI.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\epp]
“Type”=dword:00000002
“Start”=dword:00000001
…\bin64\epp.sys
@mustafa
What is your point … no explanation ‘
A one line explanation might be helpful, even 2 or more might be better
@Ashwin, “[Emsisoft] Emergency Kit displays a prompt when it finds suspicious files that suggests to install one of its core products that extends the functionality of the emergency kit on the device.”
If I understand correctly this ‘Emsisoft Emergency Kit’ only analyzes a system’s health but should it detect anything bad the user will have to download & install the component required to disinfect the OS. If so this is comparable to the HitmanPro application which analyses for free as well but requires a paid registration to carry on the disinfection.
In other words free to know if the OS is clean but prepare cash if it’s dirty. That’s fair but I wonder if it wouldn’t be more rational to directly buy the subscription. Do notice that I use myself HitmanPro without the license, scan regularly and never encounter a problem.
A bit like driving without a license, to avoid having to pay to clean the OS one might be extra cautious as to keep it out of trouble to start with :=)
Hi, Tom! I agree that the way that part of the article is written, one could mistakenly assume that, but as the screenshots show [Quarantine/Delete] and other parts of the article say: “You can run the program to scan your PC for malware and disinfect it for free.â€
More information can be found via the landing page link given above in the article summary.
HitmanPro, which I use once in a blue moon as a third-opinion scanner, is the only anti-malware program I can think of at the moment which detects, but won’t remove unless you pay. Emsisoft (both versions: EEK and EAM), Malwarebytes, and every other free AV I’ve ever used all detect and remove for free.
Hope you survived the heatwave well! I still cannot believe those temperatures…
@Hy, Hi! (always makes me laugh!) quoting Emisoft’s Emergency Kit homepage : “You can run the program to scan your PC for malware and disinfect it for free.â€. You’re darn right, I should have checked rather than rely on an article I obviously didn’t understand correctly.
HitmanPro indeed as I had noted it as well (though mistaking when comparing it with Emergency Kit which is free all the way) requires a paid registration (or a 30-day free trial) to disinfect. I’ve had 2 subscriptions in the past but never had to disinfect (PC is cleaner than my bachelor’s flat!) and HitmanPro’s subscription has increased exaggeratedly IMO so as you I run it once in a while for my soul’s tranquility (though many other matters interfere!).
My comment here and now testifies I survived, the heat that is. A big fan (I’m a fan fan) and much of Gazpacho (spanish cold soup), ice-cold coffee, cool jazz helped a lot :=)
Read you later!
Hitman Pro Free Version DOES remove Malware it detects.
It only requires a email to verify your 30 day Trial.
@BobK: You’re right–during the 30-day free trial HitmanPro will remove what it detects. After that, payment is required for removal.
The problem with Emsisoft Emergency Kit is that it includes both the 32bit and 64bit versions, and both versions use their own separate language files and malware signatures.
So the 64bit version has a folder with 278MB of signatures and the 32bit version has the same.
If I delete the 32bit version, It saves me 330MB of space and the 64bit version still works.
But when I update the signatures database, the 32bit version and it’s signatures are downloaded again.
This is a bad design and waste users storage space and time, especially when making backups.
Hello Ashwin and subscribers!
Last week I loaded some portable anti-malware software onto my USB flash drive.
I obtained these from http://www.portableapps.com including the highly recommended, EEK!
(a worthy site whose products are Free to use . . . and the Donation you give to this website is so appreciated by its Founder and Lead Developer, Mr. John T. Haller.)
This particular USB device is dedicated to anti-malware protection that can be used on my family and friends’ computer.
I have been using Windows Defender and Malwarebytes (Premium) for Quite some time now and I never worry about protection for my laptop. These do an admirable job and in fact, this week MB blocked two rogue websites from said device.
i
I’m keeping a USB stick with c’t Desinfect for emergencies. It combines four commercial AV engines (ESET, Kaspersky, F-Secure, Sophos) in a portable Linux desktop.
Desinfect is an annual DVD by the german magazine c’t, but it’s largely unknown to international audiences.
c’t is known, however “annual” sounds like “ever-spoiled”
Nah, you can even make a stick with reiserfs and organize updates with snapshots in the new version.
“Which secondary scanner do you use?”
Honestly, none. I just use Windows Defender, or whatever they’re going to call it in the future. Using multiple AV programs can be a major resource hog. I would only ever use a secondary scanner in the event of a major emergency–which is pretty rare nowadays (usually, Malwarebytes is helpful in those cases, which I would just uninstall after it’s been taken care of). Otherwise, I’m not too concerned.
@Graham, the question was about a secondary scanner, not a second, installed A/V or “multiple AV programs”. So, your “resource hog” assertion is entirely irrelevant. Occasional, manual scans are never a “resource” burden.
+1. And I don’t even use Malwarebytes, I just recover system image from backup.
It’s guaranteed and most of the time faster, unlike other solutions.
since you are getting malwarebytes afterwards, why not just use malwarebytes in the first place? does it do something that malwarebytes doesn’t do or does it better?
It just reported me two traces of a PUP detected by MalwareBytes, but apparently neglected .
+1 :-)
>free
>portable
Now you’ve got my attenction :) I like portable software. And a portable a/v I could use just to scan something I’m unsure of or maybe even remediate after-the-fact issues. I’ll give this a try.
Now, I am of the opinion that a once-infected OS can never be trusted again, and must be re-installed, but whether or not you should proceed to this rather long and boring jurney, should firstly be investigated with an a/v. And most a/v software nowadays is borderline malware and it hooks into the OS so deeply to the point it’s almost impossible to completely remove it – in which case even if your OS was clean, now it is a hodge-podge due to said a/v.
with “portable” antivirus dilemma is the same: either it plugs into OS by installing ring0 drivers, bypassing most API layers in hope to bypass malware self-protection, or it will only find simple malware which does not really try to hide.
Remember Sony Rootkit?
> but you need at least one extra tool to be safe, an ad-blocker
I didn’t see, it’s not even implied.
Does it still display a pop up urging users to upgrade to full version on every database update or after a scan is finished?
Yes it displays prompts after scans and on exit. I don’t know if that happens everytime though.
It did for me last time I had it on my flash drive (1-2 years ago). Every update, every scan the obtrusive pop up appeared. Urged the developer to use ad banner, they don’t want to.
> malware persists OS reinstall?
Can you elaborate please? You mean if there are infected files, they will still be infected after the OS reinstall? That’s absolutely true, how the reinstall is even related I do not understand.
If you mean, after reinstall it will automatically boot with OS without user interaction, I doubt that a lot.
Except if it has written itself inside BIOS/EFI, but in that case I don’t see how formatting the drive can help.
It can infect the BIOS/UEFI. I think it’s more difficult with older BIOS computers, where the BIOS was a very simple interface. Nowadays this thing called UEFI became so complex (I think MSI went ahead and boundled an entire browser (Chromium) into their UEFI on certain boards), and generally speaking complexity and security are inversely proportional.
Nowadays you can flash the BIOS/UEFI straight from Windows, which in of itself is absolute madness. Such an attack would be very targeted, with a very small sample of victims, but certainly possible.
@Yuliya you don’t even imaging the vastness of trouble :)
Actually flashing wrong BIOS is much more difficult nowaways due to crypto signatures and different protection schemes, thus something like CIH can’t prevail nowadays. Also, security gets much more attention than in 90s.
However, there is certainly more attack surface than before. https://security.stackexchange.com/questions/44750/malware-that-can-survive-bios-re-flashing
Chromium in BIOS? Never heard of, and I doubt it’s real because of size. If it exists, I guess it’s running from separate block-level flash drive, not normal EFI EEPROM. Thus I count it as dual-boot, and infecting it is just hijacking one OS from another.
> Nowadays you can flash the BIOS/UEFI straight from Windows, which in of itself is absolute madness.
I don’t agree. Requirement to boot something else just to flash BIOS inhibits BIOS updates, which are already hard enough. I’d rather say BIOS updates should be made automatic, like OS updates (yes, I’m adept of UnattendedUpgrades), but BIOS restoration should be made easier too (Gigabyte DualBIOS Hooray!).