JavaScript Restrictor: improve privacy by limiting web browser APIs
JavaScript Restrictor is an open s0urce cross-browser extension designed to improved user privacy by limiting access to APIs of web browsers that websites may use when running JavaScript. The extension is developed by Libor Pol?ák and several contributors, including Giorgio Maone, who is known for the NoScript extension. Development is supported by the European Commission's Next Generation Internet program.
The main goal of the project is to give back some control to users of web browsers when it comes to web browser APIs that may be abused by sites for user tracking and other invasive activities. The extension may block access to APIs that it supports outright, or manipulate the data that is provided to sites.
Various websites collect information about users without their awareness. The collected information is used to track users. Malicious websites can fingerprint user browsers or computers. JavaScript Restrictor protects the user by restricting or modifying several web browser APIs used to create side-channels and identify the user, the browser or the computer. JavaScript Restrictor can block access to JavaScript objects, functions and properties or provide a less precise implementation of their functionality, for example, by modifying or spoofing values returned by the JS calls. The goal is to mislead websites by providing false data or no data at all.
The extension modifies and restricts access to web browser APIs. The list of supported APIs is available on the project's GitHub webpage. It includes HTMLCanvasElement, XMLHTTPRequest, ArrayBuffer, Geolocation API, WebWorker, window.name, navigator.sendBeacon, WebGLRenderingContext and others.
JavaScript Restrictor
JavaScript Restrictor is available for Mozilla Firefox, Google Chrome and Opera, and it works in other Chromium-based browsers such as Brave, Vivaldi or Microsoft Edge as well.
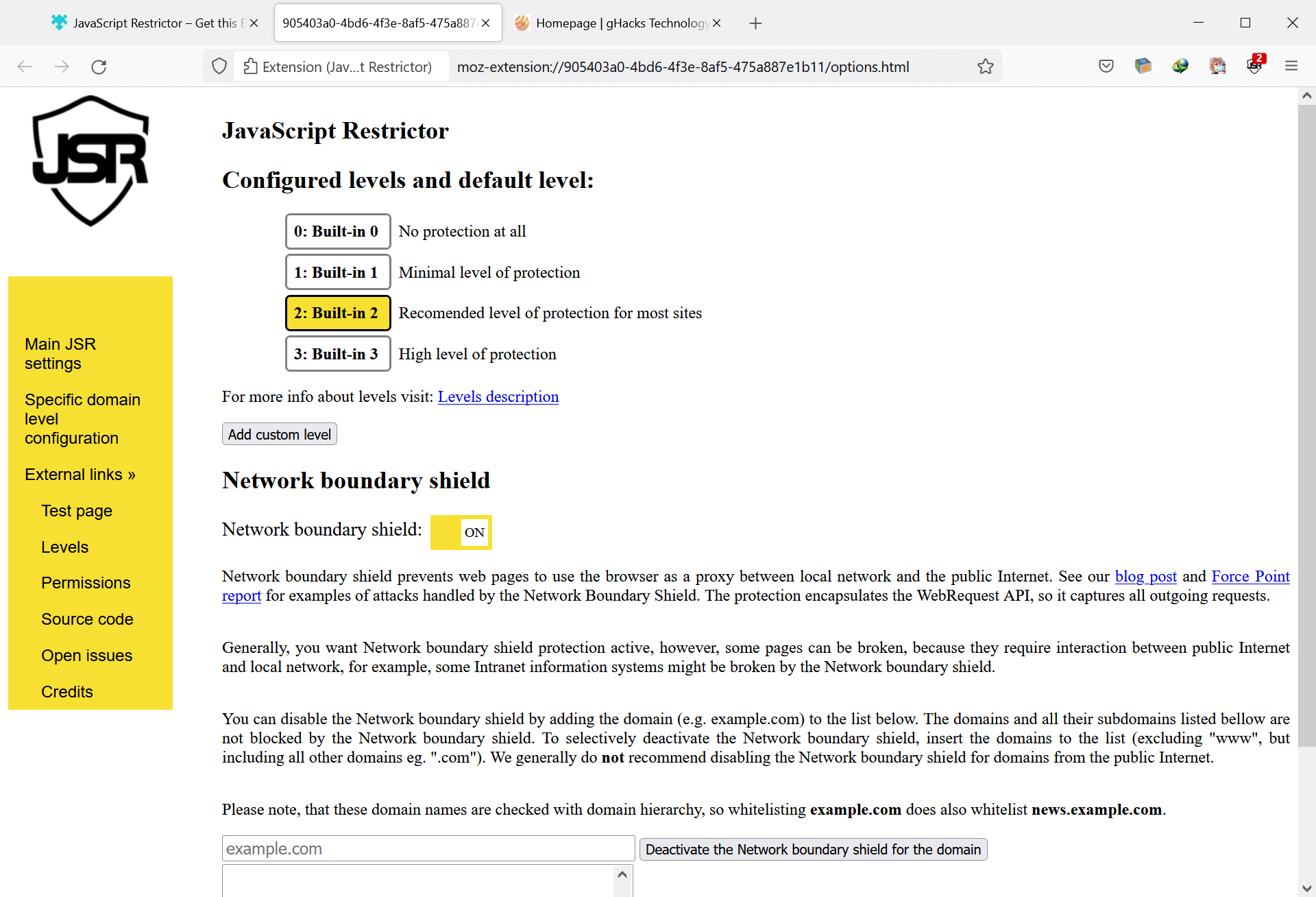
Protection is divided into different levels, with level 2 being the default option for all visited websites. Options to set different levels for sites are provided.
- Level 0 -- no protection
- Level 1 -- minimal protection. Only non-functionality breaking changes are applied
- Level 2 -- recommended protection. More protections are applied. Some sites may break.
- Level 3 -- high level of protection. Full protections are applied.
The full list of protections of the levels is found on the project's GitHub page. Network Boundary Shield is enabled by default. It prevents web pages from using the browser "as a proxy between local network and the public Internet".
The protection encapsulates the WebRequest API, so it captures all outgoing requests including all elements created by JavaScript.
The JavaScript Restrictor extension adds an icon the browser's main toolbar after installation. It displays the current level of protection on the site, and acts as a menu to change the level for that site on activation.
Just switch the level to another value to set a different protection level for the active site. The Network boundary shield may be disabled for the site as well using the action menu.
Closing words
JavaScript Restrictor works in most modern web browsers. It improves user privacy by limiting access to certain browser APIs, which may be abused by sites for tracking and other forms of attacks. Check out the project's website to find out more about it.
max3 hit the nail on the head… the only one thinking outside the box. Often the answer is simple. 100% unique with randomization. Mic drop, thread closed, keyboard warriors neutralized.
I don’t get what is wrong with being unique. It is impossible for my browser to look exactly the same as all the other browsers on the web. My operating system’s enabled font set alone gives me away every time. I would prefer to be 100% unique, BUT a different unique every time I start my browser. What browsers need to do is stop letting javascript analyse every last aspect of the user’s computer, monitor and operating system. Spoof those numbers differently every time I restart my browser and keep them the same until I exit the browser.
There’s a confusing amount of project names and outcome names here.
jshelter
JS Shield
Javascript Restrictor
For example, this:
https://i.imgur.com/FmeIwfq.png
… leads to:
https://i.imgur.com/AqkLf6z.png
Which is a dubious landing point because it dictactes the “cs” language whereas this link:
https://addons.mozilla.org/firefox/addon/javascript-restrictor/
…defaults to the user’s chosen language. For example, redirecting to:
https://addons.mozilla.org/en-US/firefox/addon/javascript-restrictor/
Brilliant project concept. That the internet is finally getting some regulated, election (at least, in theory!) accountable funding is extremely well overdue, but still underdone. The idea, from a decade or so ago, that governments are too slow and inept to keep tabs on, and be sheriff to the interwebnets lawless wild wild west nature is poppycock. Without democratic influence, look at the rampant spy network the web has become! Good on you, EU!
G. Manone and his NoScript has a confirmed bad track record. No wonder why such shady guy gets funding from EU.
This is so sad. Iron Heart again with its “anonymous” first comment and the nonsense that follows.
This should have been printed in bold red communist letters –
> Development is supported by the European Commission’s Next Generation Internet program.
@I hate brave so much (totally not a troll nick, yeah)
You too haven’t learn yet that I never post under any other pseudonym than “Iron Heart” here. I have no reason to. Seems like there are people who share my opinion out there, could be one of those other 40 million Brave users, you know.
I thought it was understood that extensions like these are not for blocking fingerprinting or tracking but for improving JS security and prevent websites from abusing JS.
But the big problem is that keeping track of and observing websites which break is hell.
More fingerprinting by using JavaScript Restrictor.
Interesting extension, the default protects against fingerprinting by timing, canvas, hardware. It also restricts geolocation accuracy and disables beacons.
The “network boundary shield”, if it’s what I think it is, preventing access to local network by sites, can be done in ublock origin too, by enabling the “Block access to LAN” filter list, that is included but not enabled by default.
About the Battery status API that they disable, I think that at least in Firefox it has been no longer exposed to the sites for some time already:
https://bugzilla.mozilla.org/show_bug.cgi?id=1313580
but one never really knows with Mozilla.
The window.name is cleared with each page load by the extension. Firefox 88+ had already if one believes them a counter for this being used as a tracking cookie:
https://blog.mozilla.org/security/2021/04/19/firefox-88-combats-window-name-privacy-abuses/
but this only confined the window.name supercookies to their own sites, meaning it could still be used as a first-party tracking cookie, which becomes more difficult with this extension. And Firefox was supposed to have done its site isolation of window.name already since version 82:
https://developer.mozilla.org/en-US/docs/Mozilla/Firefox/Releases/82#dom
their contradictory statements showing once again that their announcements can’t be trusted. Could this cross-site supercookie mechanism be used between versions 82 and 88, or not ?
The non-default level 3 seems to provide also security-related changes (“ArrayBuffer exploitation”, “SharedArrayBuffer exploitation”, “WebWorker exploitation”), this is reminiscent of NoScript bundling various security features, but like in Noscript I would like to know what those problems really are and if they’re not exaggerated. I am also skeptical about having to confirm every xhr request in that level 3.
I tried this addon a couple days ago, it breaks legit sites and doesn’t have any way to adjust what it blocks, nor does it tell you what it blocks and the only thing you can do is whitelist sites and change the blocking level. Very amateur addon severely lacking in features.
Which level of protection did you use it with it? Does level 1 also break sites?
Some here fail te realize that fingerprinting protection is not about just faking who you are, but constantly permutating those values. So, yes, you may be unique, but you’re less trackable.
What “Pigeonhole Web-Browsing” said.
Sometimes you want to be tracked, sometimes you don’t.
Me, I block all JS by default and then allow or more often, temporarily allow, what I need at that moment.
Jshelter anyone?
Instead of trying to become a digital locksmith, worrying every browser setting to obtain an ultimately private solution, I’ve found it far more effective to use multiple browsers with each their own separate profile directories. Add UblockO to each for aesthetics and usability.
I use ungoogled Chromium for YouTube and only for YouTube. Both are Google owned so there ain’t no hiding much from them in those instances.
Similarly, separate your total browsing into isolated pie wedges. One browser for this, one browser for that…
My IRL ID, financial/payments and related email address are only ever entered into one highly isolated browser. It’s used for shopping transactions and nothing else, ever.
Pigeonhole Web-Browsing
@JonSnow
> No matter what you do and what Browser you use you will be tracked.
I tend to agree, however, If that is the case, would it matter that you try and do something about it? Seeing as you’re unique anyway.
If you like wasting time and effort, go for it.
No matter what you do and what Browser you use you will be tracked. That’s the reality of Internet this days. The best you could to use a Ad-blocker like Ublock O to block ads and basic tracking extension or whatever way you protect yourself….other than that I do nothing else. I can live with that.
Correct. And what no one ever discusses is why it matters. 99.9999% of the population don’t care – or if they say they do, they’re lying because they don’t really do anything to prevent being tracked.
And 99.9999% of the population aren’t being tracked by any government agency other than the fact that everything they do online *is* captured by the NSA for perusal only when it matters to the NSA. Is this good? No. Can it be stopped? No. Not without dismantling the US government. Ed Snowden was educational but ultimately a waste of time.
99.9999% of companies are tracking you so they can show you relevant ads. Who gives a rat’s ass? Not that I want to see ads at all (which is why I use an ad-blocker). but if I did I’d *want* to see relevant ads. I wish I could convince Youtube to show me *really* relevant videos on my home page other than the crap in foreign languages they try to show me.
People need to understand: You can haz better security. You can haz worse security. But you cannot haz “security”. There is no security. Deal. And that applies to privacy.
The more you do to become private, the more unique you become. In order for a request you make (that’s how browsing works, you request information) to be fulfilled, a site has to know to whom the data is to be sent.
If you block ads and trackers, regardless of method, if you don’t go overboard, browsing will definitely be much smoother and faster but you won’t gain much privacy. You will be harassed far less, though, that’s all I go for.
After playing with a lot of extensions similar to this one, the brute force, one size fits all approaches such as brave or system level adguard, that are maintained well seem to work the best. The more you try to customize any browser with extensions, the slower it gets and the more likely a scorched earth reinstall will be in your future.
This utility may look good at first glance; the default setting should definitely prove it’s doing something. How long will it take before you’re down to level 0?
I tried it yesterday. So far I have no impressions. But it is not clear how to test it and on which sites for reliability.
> The protection encapsulates the WebRequest API, so it captures all outgoing requests including all elements created by JavaScript.
Will die with the release (complete transition) to Manifest v3 by Chrome and browsers based on Chromium.
@Honorius
Who cares? Never ever should you employ such extensions to fight fingerprinting, read my reply to @Anonymous to understand why.
There are Chromium-based browsers with native protections against Canvas fingerprinting, such as Brave or Bromite. They were never in need of an extension that doesn’t solve the problem anyway.
wonder if and how it interferes with canvasblocker and/or ublock?
@Anonymous
> canvasblocker
Eww, please no. This extension generates vastly different output compared to the built-in protections of the browser. The output of this extension is unique to the extension, and you are thus within the (small) pool of users of the extension, for all to see. And protecting Canvas alone is pointless anyway as there are many other values that can be checked just as well.
> And protecting Canvas alone is pointless anyway
Rubbish. It fools naive scripts
@Anonymous
Good luck then. Many scripts check for more than just Canvas.
> Many scripts check for more than just Canvas
But they still check for canvas which is the point because it’s randomized and fools naive scripts
Brave doesn’t protect fonts or timezone or any of another hundred things. By your logic Brave doesn’t work against naive scripts either then
thx for the exlanation! (wasnt me answering above)
highly fingerprintable, leaks like a sieve, doesn’t cover enough anywhere near enough to prevent high entropy, breaks legit JS left right and center, lacks enough hooks into APIs to do the job properly
leave it to built-in browser solutions like Brave’s token randomizing or Tor Browser’s comprehensive mitigations
Please back up your allegations with evidence.
@Gerard
The guy above is correct. Read this comment by security researcher Daniel Micay:
“Providing the offer to disable features to reduce attack surface can be useful. Doing it to prevent fingerprinting is utter nonsense since by changing any settings that sites can detect you have made yourself far more easily fingerprinted. Disabling WebRTC and WebGL would make you far easier to fingerprint, not harder. These sites encouraging things like that is a problem.”
source: https://old.reddit.com/r/GrapheneOS/comments/ciizae/vanadium_and_bromium_privacy/ev6m2ot/
Here, Whonix developer madaidan on the matter:
“Configuring / “Hardening” the Browser
You cannot configure your browser to prevent tracking either. Everyone will configure their browser differently so when you change a bunch of about:config settings, such as privacy.resistFingerprinting, and pile on browser extensions like Privacy Badger, you’re making yourself stand out and are effectively reducing privacy.
Additionally, just disabling JavaScript, while preventing large vectors for fingerprinting, does not prevent fingerprinting entirely. Fingerprinting can be done with only CSS and HTML. One example is using @media rules to figure out your browser resolution.
You also cannot substantially improve security by configuring the browser. Changing a few settings will not fix deep architectural security issues. You can at most reduce some attack surface by disabling things, but most people don’t do this to an extent where it actually matters.”
source: https://madaidans-insecurities.github.io/browser-tracking.html#configuring-the-browser
Also, read this thread very carefully:
https://old.reddit.com/r/privacytoolsIO/comments/iepjwh/wont_reducing_your_browser_fingerprint_have_the/
The only people who believe that you can “fix” browser fingerprinting via extensions or alternatively user.js files doing similar shit are the self-important maintainers of these non-fixes. The only way not to stand out is for browsers to behave the same while protecting these values, like the Tor Browser Bundle or Brave attempt to do. Installing Firefox or any other browser, with everyone modifying it here and there does not reduce your uniqueness, it is utter bullshit.
“The only way not to stand out is for browsers to behave the same while protecting these values, like the Tor Browser Bundle or Brave attempt to do.”
Can you explain Brave browser attempts properly? How many values it protects, and more important name of some values it protects?
I didn’t say the guy was wrong. He should thank you for doing what he failed to do.
Iron Heart didn’t even answer the question
Iron Heart’s fingerprinting knowledge is disgustingly abysmal, bordering on criminal. He doesn’t know how entropy, fingerprinting or linkability works
Here’s a tiny snippet of his lack of knowledge on the subject
– https://www.ghacks.net/2021/07/31/how-firefoxs-new-smartblock-feature-works/#comment-4501396
– https://www.ghacks.net/2021/07/31/how-firefoxs-new-smartblock-feature-works/#comment-4501361
Iron Heart just likes to link and quote non-fingerprinting experts out of context to make himself look smart
—
This is not about fingerprinting metrics (there is that) but the actual extension. Extension APIs are limited, and this makes it hard to plug all the leaks. Workers in particular are an issue which is why you find extensions killing them. And there can be timing, injection, and perf issues. And then there’s this little fact
reading
– https://palant.info/2020/12/10/how-anti-fingerprinting-extensions-tend-to-make-fingerprinting-easier/
– https://news.ycombinator.com/item?id=25374383
– https://abrahamjuliot.github.io/creepjs/tests/prototype.html
levels 2+3
– the version of creepjs prototype linked above is out of date. Newer versions of it are improved to evade evasion tactics used in a game of whack-a-mole (proxy lies), but not needed for JS redirector it seems. The test linked is a detailed scan. On level 3 it errors out. On level 2 it returns 194 lies detected in 50 of 2022 properties on Firefox
– the creepjs test can also be run in a less detailed mode, the important bit is the 50 properties (not necessary used to lie, but cannot be trusted): FYI: levels 2 + 3 are the same: 50 properties
– the order of navigator keys is uniquely altered when comparing a loop vs prototype
level 3
– 37 window properties moved after constructor: including a unique set of at least 13 not seen elsewhere
– other telltale signs such as errors like “Permission denied to access object”, or Date.split()
level 2
– 24 window properties moved after constructor: including a unique set of at least 6 not seen elsewhere
level 1
– not meaningful
and that’s just for starters
@Anonymous
> Iron Heart’s fingerprinting knowledge is disgustingly abysmal, bordering on criminal. He doesn’t know how entropy, fingerprinting or linkability works
But you do? I have not seen anything in regards to that, either.
And the links you’ve pointed to… Yeah, people, go ahead and read the entire thread then. I am discussing with a believer in snake oil like user.js files there. Fun read indeed.
> Iron Heart just likes to link and quote non-fingerprinting experts out of context to make himself look smart
How am I quoting them “out of context”? I am not a quote shortener, and the entire context, or indeed, the entirety of the posts I’ve quoted from (and linked to, for all to read) indicate that they are not fond of snake oil like user.js “templates”.
Yeah, I guess developers of f*cking Whonix and GrapheneOS have much less of an idea of fingerprinting than some self-important user.js author (with whom you have nothing to do, I am 1000% sure) who has never written a single line of code and only knows the defenses from the results of testing suites. Yes, I do believe that. /s
> developers of f*cking Whonix and GrapheneOS have much less of an idea of fingerprinting than some self-important user.js author (with whom you have nothing to do, I am 1000% sure) who has never written a single line of code and only knows the defenses from the results of testing suites.
LOL:) “f*cking Whonix” is a joke and only code they write is comments in scripts. Dont know much about Sir Micay, but he seems to be more hysterical than productive and tends to invent problems out of thin air, just like uneducated whonix “devs” and our dear Iron Heart.
@Developers Developers Developers
These guys are still much more knowledgeable than any irrelevant author of a “change 1001 settings in Firefox and everything will be alright” bandaid script. Deal with it.