Configure Controlled Folder Access in Windows 10
Controlled Folder Access is a new feature introduced in the Fall Creators Update for Windows 10 that is part of Windows Defender Exploit Guard.
The security feature protects files from being accessed by malicious code running on the Windows machine, and Microsoft advertises it specifically as a protection mechanism against ransomware.
The main idea behind Controlled Folder Access is to protect certain folders and the files they contain from unauthorized access. Think of it as a layer of protection against manipulation of files that are stored in protected folders.
The feature requires Windows Defender Antivirus and that real-time protection is enabled as well. Attack Surface Reduction, another security feature which I reviewed yesterday, has the same requirements.
The feature was introduced in Windows 10 version 1709, the Fall Creators Update, and is not part of older versions of Microsoft's operating system.
System administrators and users can manage Controlled Folder Access in several ways: through Group Policy and PowerShell, and the Windows Defender Security Center application.
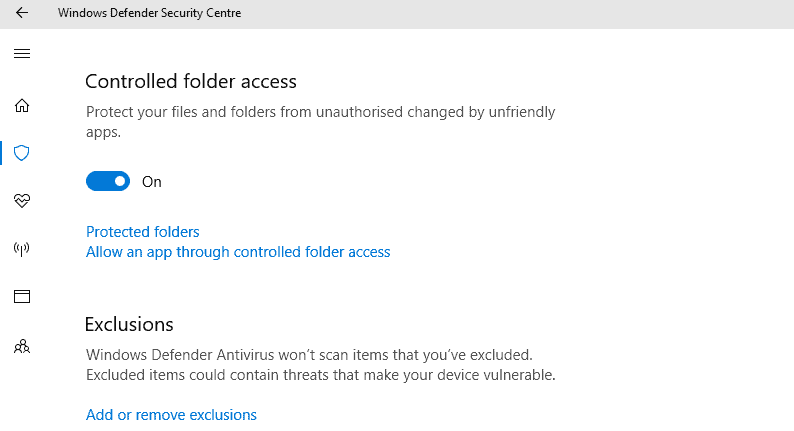
Controlled Folder Access
Microsoft describes the security functionality of Controlled Folder Access in the following way:
All apps (any executable file, including .exe, .scr, .dll files and others) are assessed by Windows Defender Antivirus, which then determines if the app is malicious or safe. If the app is determined to be malicious or suspicious, then it will not be allowed to make changes to any files in any protected folder.
This means that the functionality relies on Windows Defender to detect a process as malicious. If Windows Defender scans don't flag the process as malicious or suspicious, access to files an folders protected by Controlled Folder Access is granted.
This is different from other anti-ransomware tools like Hitman Pro Kickstart, Bitdefender Anti-Ransomware, or WinPatrolWar, which are usually more pro-active when it comes to protecting important files and folders.
Windows Defender Security Center application
Windows 10 users may enable and manage Controlled Folder Access using the Windows Defender Security Center application.
- Use Windows-I to open the Settings application.
- Select Update & Security > Windows Security
- Select Virus & threat protection when the Windows Security page opens.
- When Windows Security opens in a new window, select "manage settings" under Virus & threat protection settings.
- Make sure that real-time protection is enabled.
- Go back to the Windows Security Main page.
- Scroll down to the Ransomware Protection section and select Manage ransomware protection.
- Toggled "Controlled folder access" on the page to enable the feature.
- Accept the UAC prompt to make the change.
When you switch the security feature to on, two links are added underneath it.
Protected Folders
The list of folders that are protected by Controlled Folder Access is displayed when you click on the link. Windows Defender protects some folders automatically; these are:
- User: Documents, Pictures, Videos, Music, Desktop, Favorites
- Public: Documents, Pictures, Videos, Music, Desktop
You cannot remove these default folders, but you can add custom folder locations so that the added folders are protected by the security feature as well.
Click on "add a protected folder" to select a local folder and have it added to the protected folders listing.
Allow an app through controlled folder access
This option lets you whitelist applications so that these programs may interact with protected files and folders. Whitelisting is mostly useful for situations where applications are flagged incorrectly by Windows Defender (false positives).
Simply click on the "add an allowed app" option on the page, and select an executable file from the local system, so that it is allowed to access the protected files and folders.
Group Policy Configuration
You can manage the Controlled Folder Access feature using policies.
Note: The Group Policy is part of professional editions of Windows 10 only. Home users don't have access to it (the free program Policy Plus adds it to the system for the most part though).
- Tap on the Windows-key, type gpedit.msc, and select the item that is returned by Windows' built in search.
- Go to Computer configuration > Administrative templates > Windows components > Windows Defender Antivirus > Windows Defender Exploit Guard > Controlled folder access.
- Select the "Configure Controlled folder access" policy with a double-click.
- Set the policy to enabled.
You can set the feature to the following values:
- Disable (Default) -- Same as not configured. Controlled Folder Access is not active.
- Enable -- Controlled Folder Access is active and protects folders and the files they contain.
- Audit Mode -- Events created by the feature are written to the Windows event log, but access is not blocked.
Two additional policies are available to customize the feature:
- Configure allowed applications -- Enable this policy to add programs to the whitelist.
- Configure protected folders -- Enable this policy to add custom folders that you want the security feature to include in its protection.
PowerShell commands
You may use the PowerShell to enable and configure Controlled Folder Access.
- Tap on the Windows-key, type PowerShell, hold down the Ctrl-key and the Shift-key, and select the PowerShell search result. This opens an elevated PowerShell command prompt.
To change the status of the feature, run the command: Set-MpPreference -EnableControlledFolderAccess Enabled
This enables Controlled Folder Access using PowerShell. You can set the status to enabled, disabled, or AuditMode.
To add folders to the list of protected folders, run the command: Add-MpPreference -ControlledFolderAccessProtectedFolders "<the folder to be protected>"
This adds the selected folder to the list of protected folders.
To whitelist an application, run the following command: Add-MpPreference -ControlledFolderAccessAllowedApplications "<the app that should be whitelisted, including the path>"
This adds the selected program to the list of allowed processes so that it won't be blocked by the security feature when it tries to access folders that are protected by it.
Controlled Folder Access events
Windows creates events when settings change, and in the audit and blocked modes when events fire.
- Download the Exploit Guard Evaluation Package from Microsoft, and extract it to the local system.
- Tap on the Windows-key, type Event Viewer, and select the Windows Event Viewer in the search results.
- Select Action > Import custom view when the Event Viewer window opens.
- Select the extracted file cfa-events-xml to add it as a custom view.
- Click ok on the next screen.
The following events are displayed by the custom view:
- Event 1123 -- blocked events.
- Event 1124 -- audit mode events.
- Event 5007 -- setting changes events.
Resources
- Protect important folders with Controlled folder access
- Enable Controlled folder access
- Customize Controlled folder access
- Evaluate Controlled folder access
- Windows Defender Exploit Guard
- Set-MpPreference documentation
- Add-MpPreference documentation
- Get-MpPreference documentation
I wish I had known that it doesn’t work for windows 10 home edition, as well. I am ready to throw out windows 10 or windows defender. Nothing works for me. I am not an IT.
Doesn’t work for Windows 10 Home edition. Would have been nice to have that at the beginning of the article.
I tried to save a file edited in Audacity, I could not. the error message? “That file name does not exist.”
So, I decided to overwrite the file and it ‘appeared’ to save, but I never saw the progress bar Audacity puts up while a file is being saved. Sure enough, the original file was intact.
So I am wondering how many of my 200+ programs and apps I am going to have to whitelist. Programs aren’t tooooooooo bad, just go to Programs Files + Program Files (x86)–but I’ve been a tech for over 30 years and know my way around an OS. None of my siblings or kids (save my son) or their spouses or kids know that ‘trick’.
Microsoft needs to make it user-friendly for the masses/consumers, not just the IT staff.
When I turned Controlled Folder Access on, I kept getting a notification that said “Controlled Folder Access blocked C:\Windows…\rundll32.exe from making changes to the folder %userprofile%\Favorites”.
I cannot eliminate the problem because a) the message does not identify the program that triggered the warning (it wasn’t rundll32.exe), and b) I’m not allowed to turn off protection on my Favorites folder since it is on the list of protected items.
If you create a new Custom View in the Event Viewer, you can see the full path from the notification. Use the following XML code to create the appropriate filter (I had to edit the XML code I pasted, replace the {} with angle brackets):
{QueryList}
{Query Id=”0″ Path=”Microsoft-Windows-Windows Defender/Operational”}
{Select Path=”Microsoft-Windows-Windows Defender/Operational”}*[System[(EventID=1123 or EventID=1124 or EventID=5007)]]{/Select}
{Select Path=”Microsoft-Windows-Windows Defender/WHC”}*[System[(EventID=1123 or EventID=1124 or EventID=5007)]]{/Select}
{/Query}
{/QueryList}
We shouldn’t need to make workarounds like this though, the full path should be in the notification instead of being abbreviated.
Thanks for the XML code. I’ll put it to good use!
Controlled Folder Access blocks all my apps from writing in my user folders even Outlook 2016 stopped working so I turned it off, after doing that all apps work fine again.
Good idea very badly implemented. Can ‘t remove folder once added. As mentioned above, no option to “allow” from the popup so it’s difficult to figure out what to allow. Could be so much better.
I agree with RossN – in its current guise, along with Action Centre’s arbitrary abreviations, it is very user-unfriendly and thus hamstrung. Many users will switch it back off shortly after turning it on.
I have my OS and my data on separate partitions. I move and map my Office templates folders to the data partition, saved in a folder where I keep software files. I added these folders to Controlled Folder Access. The next time I opened Outlook, it was blocked from making changes to the Office Templates folders. Outlook!? I suspect Windows’ list of allowed programs for CFA only applies to the folders protected by default.
Its part of windows defender which means if windows defender goes down for reasons, 3rd party antivirus, malware corrupts it, user disables windows defender, etc. controlled folder access will stop working.
It functions whether you use a third party AV or not. Same with the EMET replacement that has been integrated in Defender. Neither of those functions get disabled even with a third party AV.
You get a pop-up. But you don’t get the option to allow. You have to go deep into Windows Defender and add the application. It isn’t always obvious which app to add. Today c:\windows\…\dllhost.exe was blocked. I have several of those, so had to guess which one to add to the allowed apps.
Thank you very much Martin !
Here is an open source alternative which is compatible with previous Windows versions : https://iwrconsultancy.co.uk/softwarepolicy.htm
Do you get a popup to allow or deny an action is it’s automatically blocked without notification?
It notifies. If you are an admin, you can add an app to whitelist.