Bypass adware-installers on sites like Sourceforge or Afterdawn automatically
Sites like Cnet's Download.com or Sourceforge began to implement wrappers on their services some time ago with the sole purpose of earning extra revenue from software downloads.
These wrappers are similar to installers that contain the adware right away, and the only difference to them is that the wrapper's only purpose is to display offers to the user.
When a user accepts an offer, or misses the decline or skip button, a third-party program is installed on the computer system and the site who maintains the wrapper gets paid for that.
Techniques like making it difficult to distinguish between the real program and the offer or setting the offer to accept so that it gets installed when the user clicks next and oversees the offer are implemented to increase revenue further.
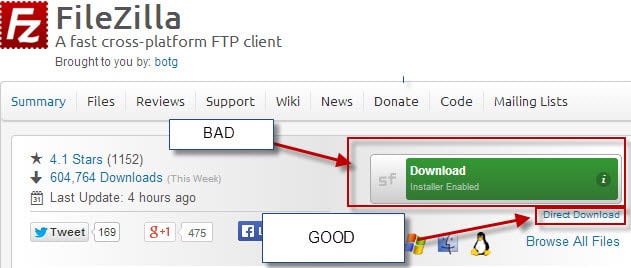
Most sites offer options to download the clean installer or program instead of the wrapper program. On Sourceforge for example, all you need to do is add ?nowrap to the address to download the clean installer of the program.
Here are two of examples on popular sites
As you can see, the wrapper link is displayed prominently on the download page while the direct download link is barely visible.
Automation
While you can get the direct download on most sites, some users who download often from a particular site or sites may want to automate the process.
The userscript Fake-Download Bypasser does that for the sites Sourceforge and Afterdawn. It has been designed for Download.com as well but that does not seem to work at the time of writing.
Once installed in the browser of choice, it will activate the correct download on the site even if you click on the wrong download button.
To install it in Firefox, you need to install the Greasemonkey add-on or compatible extensions before you can install the script directly in the browser. Once done, it works out of the box.
Chrome users on the other hand cannot install the userscript directly. It will download instead and when it does, needs to be dragged to the chrome://extensions/ page to display the installation prompt and add it to the browser.
The userscript Adware Atomizer offers a second option. It supports way more sites than Fake-Download Bypasser but has the same issue on Download.com than the other. Installation instructions are provided on the project page. The only difference is that Chrome users need to install the Tampermonkey extension before the script can be installed.
Verdict
The scripts work well on some of the sites but not on all of them. The core reason here is that they have not been updated since last year and that some of the sites must have changed how downloads are delivered.
Still, it is worth a shot if you download from at least one of the working sites regularly.
Cnet Download has been fixed in version v1.29.1 of AntiAdware.
If you find any other issue, feel free to report it here: https://github.com/HandyUserscripts/AntiAdware/issues
Also, if you like the script, do not hesitate to become a fan or leave a good review here!
https://greasyfork.org/en/scripts/4294-antiadware/feedback
Turn off the installer in your accout settings at Download.com to get a direct download link.
That works if you have an account at the site.
Thank you for the pointer! It really adds to this article.
Great article!
Could you list some popular Sits that are clean? Maybe list some that install the wrappers?
Use this as a pointer: https://www.ghacks.net/2014/07/08/download-software-programs-computer/
Certain filelockers trump legal software download portals in AntiAdware’s supported websites.
The authors of the userscripts mentioned in this article forgot to add support for SoftM8. Those userscripts do not support software download portals which do not offer alternate direct links to the software they publish, leaving only download links to adware installers as the only download links to be found.
Fake-Download Bypasser is apparently abandoned by its author.
No script or adblock will replace common sense and vigilance at the end. It comes down to the end user.
Are you sure it has issues with Download.com? I did not have any problems with downloading adware-free installers.
Just an idea, but why not use a site like FileHorse or Ninite that doesn’t bundle adware? e.g.
http://www.filehorse.com/search?q=filezilla
https://ninite.com/filezilla/ninite.exe
Using clean portals or the developer’s website directly is the best option, but sometimes that is not possible.
Another option is to avoid any site that uses wrappers. Always find a clean source for the file first, if you can. And consider letting sites which try to load adware via wrappers know how much you dislike their policy.
Some argue that sites like FileHippo and MajorGeeks need the revenue from adware vendors in order to survive. I prefer to support the developers of the software instead. Donate to the dev if you use it!
Since when did MajorGeeks start using a download wrapper or promoting adware? I think you may be off the mark with that one.
Unchecky and MalwareBytes constantly saves me from these “offers”, one disabling all checkboxes not related to the program to be installed and the other blocking these adwares before its installation.
The best thing is to pay attention at these download sites and don’t click anywhere. You must take control of your nervous fingers.
Thanks for the excellent article Martin!
I often download using the wrapper in sandboxie. Just to give the developer some support. Than I recover the software and close the sandbox with the installed adware wiped from the sands.
I think you are using an outdated version of Adaware Atomizer.
Now it is named Antiadaware and you can find it on
https://github.com/HandyUserscripts/AntiAdware#readme
It work wonderful with the examples you have given.
That looks good, thanks!
Thanks, I have replaced the link to reflect that.
I’m using this link instead : https://greasyfork.org/fr/scripts/4294-antiadware
which can automatically install the script ;-)
Have a good day all !
Nice advice Martin. Thanks.
You are fast ;)
Have you on feedly :)