CryptSync: upload only encrypted files to online storage services
Several cloud storage services use encryption to protect data of user accounts from being accessed by third parties. While this may be reassuring for many users, some prefer to add encryption of their own to important files on top of that. Why? The core reason is to prevent access to the files even if someone gained access to the account. Say, someone managed to steal your account password for your Dropbox, SkyDrive, Google Drive or whatever-online-storage-service-you-are-using account. This is enough to gain access to all files. With added encryption, the attacker would not only have to steal the username and password, and maybe even intercept a two-factor authentication code, but also the password the files are encrypted with.
You have several options to encrypt files before they are uploaded to a remote server. One of the easiest options available is CryptSync, a free program for Windows. The program keeps pairs of folders in sync on systems it is executed on. One of the folders is encrypted during the sync process, making it an ideal program to encrypt data before it gets uploaded.
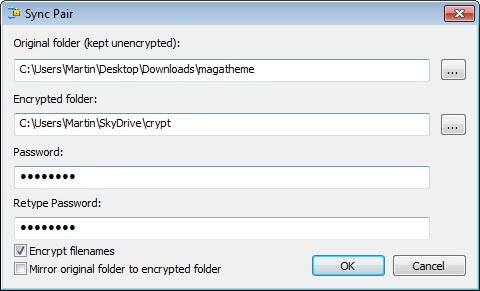
The basic idea is the following here. You select a folder with data that you want to host online as the originating folder, and pick a local cloud drive folder as the destination folder. CryptSync encrypts the files during the synchronization using a password you specify.
To create a new folder pair click on the new pair button in the program interface. Here you need to specify the original folder and encrypted folder, as well as the password that you want to use to protect the data.
You can furthermore enable the encryption of file names so that it is not possible to guess a files contents or type from that. The mirror original folder to encrypted folder option enables one-way syncing instead of two-way syncing.
You can then sync the files once and exit the program, or set it to run in the background all the time. The latter option checks the original folder for new files and folders regularly to encrypt and upload them to the destination folder in the process.
The files and folders that get synced with the destination folder and the online storage look like this if you have enabled file name encryption as well.
You can run the program from the command line as well which can be useful for the creation of batch files or programs that allow you to run third party programs (like backup software).
The downside of using CryptSync is that you will have two folders locally that store the data. One of them is the original folder, the other the encrypted folder which some may see as redundant. Still, if you are looking for an automated way to protect files that you store at online storage providers then CryptSync is definitely one of the programs to do just that.
Advertisement
It seems cloudfogger is shut down. I did a test 5-6 years ago and found cloudfogger puts the file in the cloud _before_ encrypting, so anyone with access to file history in DB would be able to retrieve unencrypted versions of the files. I’d use something else. I thought cryptsync looked promising until I read the issues on github. I’ll wait on that one for a while as well. (@dan)
“The mirror original folder to encrypted folder option enables one-way syncing instead of two-way syncing”
It doesn’t work if you select MIRROR or NOT it is the same is a two-ways !
So if you delete a file on the original folder it is deleted on the DROPBOX encrypted folder !
CRYPTSYNC 1.1.3.235
I use an iPhone which backs up to Cloud, so would the process be the same if I’m updating or do I even need to worry about this?
Check out Cloudfogger: accomplishes the same thing without the need for dual folders.
You have to uncheck ‘Preserve modification time stamp of file containers’ in the Truecrypt preferences for Dropbox not to upload the whole container file.
An alternative to CryptSync is Boxcryptor. I use both, depending on further usage of the encrypted files.
Encrypting cloud data is mandatory. Microsoft revealed last week that it has surrendered customers data to US authorities.
Microsoft is not the only company, read today that US authorities may get realtime access to Gmail and every other US based service.
It’s not really a question of access per say. US Government (Law enforcement) already has said access. And sadly, so does many criminals.
It’s really a question of being able to use said access to enforce laws publicly (taking the “bad guys” to court) and using evidence obtained via said access.
Don’t be fooled. Everything we do online is already scanned, documented, and inventoried. It’s just a matter of being able to use the information legally.
I think the advantage of this is that individual files are encrypted and uploaded as they are changed.
With TrueCrypt from what I understand is that it uploads the whole container than the changed files.
I have been using AxCrypt, but I think this might be even more convenient than individually decrypting a file.
Though I can see that if you access your files from another location where CryptSync is not installed you will not know which file is what due to the random naming scheme.
From what I understand and my experience, Dropbox only needs to upload the portions of the container file that have changed. Avantages of using TC is that you decrypt all the files in one go and you don’t have 2 copies on your hard drive.
Spideroak have a zero knowledge policy – their USP is that they don’t have access to your files at all
> Dropbox only needs to upload the portions of the container file that have changed
My last test on this was more than a year ago, but that was my experience with Dropbox + TrueCrypt: it doesn’t re-upload the entire volume.
Right. But you do not need to encrypt the file names, that is just an option.
I currently do something similar using Truecrypt – I keep my encrypted container in my Dropbox and have a batchfile I run on Windows startup that loads the container as a drive so I can access the files.