Microsoft, Adobe Ready Security Updates
It is the second Tuesday of the month again and this means security patch day at Microsoft and Adobe. Adobe has just released a security bulletin for Adobe Reader and Acrobat that fix several critical vulnerabilities in versions of the pdf software.
Vulnerabilities affect Adobe Reader X and earlier versions for Windows and Macintosh, Adobe Reader 9.4.2 and earlier for Unix, and Adobe Acrobat 10.1 and earlier for Windows and Macintosh.
Adobe as usually recommends to update Adobe Reader to the new version released today. This is Adobe Reader 10.1.1 for Windows and Macintosh, and Adobe Raeder 9.4.5 for Unix, as well as Adobe Acrobat 10.1.1 for Windows and Macintosh.
The security bulletin offers vulnerability details and download links for all Adobe Reader and Acrobat updates.
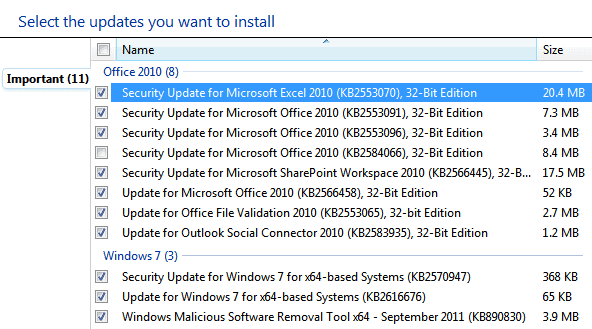
Microsoft today has released five security bulletins that affect Microsoft Windows, Microsoft Server Software and Microsoft Office. The maximum severity of all five bulletins is Important, the second highest rating available.
Windows Update is already picking up the updates online. Windows users can check for updates in their operating system to download and install the patches right now.
You find summaries for all five bulletins below. Follow the link for detailed descriptions of each security bulletin.
- MS11-070 - Vulnerability in WINS Could Allow Elevation of Privilege (2571621) - This security update resolves a privately reported vulnerability in the Windows Internet Name Service (WINS). The vulnerability could allow elevation of privilege if a user received a specially crafted WINS replication packet on an affected system running the WINS service. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
- MS11-071 - Vulnerability in Windows Components Could Allow Remote Code Execution (2570947) - This security update resolves a publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a legitimate rich text format file (.rtf), text file (.txt), or Word document (.doc) that is located in the same network directory as a specially crafted dynamic link library (DLL) file. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-072 - Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution (2587505) - This security update resolves five privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted Excel file. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. Installing and configuring Office File Validation (OFV) to prevent the opening of suspicious files blocks the attack vectors for exploiting the vulnerabilities described in CVE-2011-1986 and CVE-2011-1987.
- MS11-073 - Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (2587634) - This security update resolves two privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted Office file or if a user opens a legitimate Office file that is located in the same network directory as a specially crafted library file. An attacker who successfully exploited either of the vulnerabilities could gain the same user rights as the logged on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-074 - Vulnerabilities in Microsoft SharePoint Could Allow Elevation of Privilege (2451858) - This security update resolves five privately reported vulnerabilities and one publicly disclosed vulnerability in Microsoft SharePoint and Windows SharePoint Services. The most severe vulnerabilities could allow elevation of privilege if a user clicked on a specially crafted URL or visited a specially crafted Web site. For the most severe vulnerabilities, Internet Explorer 8 and Internet Explorer 9 users browsing to a SharePoint site in the Internet Zone are at a reduced risk because, by default, the XSS Filter in Internet Explorer 8 and Internet Explorer 9 helps to block the attacks in the Internet Zone. The XSS Filter in Internet Explorer 8 and Internet Explorer 9, however, is not enabled by default in the Intranet Zone.
You find deployment priority information and the severity index at the Technet blog.
Advertisement
re: Adobe Reader
it’s not the easiest thing to find the offline installers for Adobe Reader, but thanks to a ghacks story from last year I managed to get to a Adobe ftp page that leads to what might be all versions (past and present) of Adobe Reader. I thought it might be nice to share :-)
ftp://ftp.adobe.com/pub/adobe/reader/
So, if like me you want the (full/offline install) version of latest Adobe Reader X (10.1.1 , i think):
click on win
click on 10.x
click on 10.1.1
then click on the one with your language and (hopefully) you should be at a page with the full (offline) install.
ps: on the choose your language/version page, the link that is called ‘misc’ leads to the 10.1.1 update.
pps: do I want to know what a ftp page is, and why it’s different to http?
Thanks so much for posting those, this should help a lot of readers.
Thanks for the update links. I tell my firewalls to block all Adobe products as they have more wide open holes than a choirboy, so they don’t update automatically as a result.
Got all 12 Updates a few minutes ago! :)