Google releases security update for Chrome that is exploited actively
Google published a security update for its Chrome Stable web browser that addresses a security issues that is exploited in the wild. Other browser makers who use Chromium, the core that Chrome uses, have released security updates as well already, or will in the near future.
Google released the update to the Chrome Stable channel, the Chrome Extended Stable channel, and for Chrome for Android. Chrome Stable's version increases to 107.0.5304.121 for Mac and Linux and 107.0.5304.121/.122 for Windows, the Chrome Extended Stable version increases to 106.0.5249.199, and the Chrome for Android's version is 107.0.5304.141 after the update.
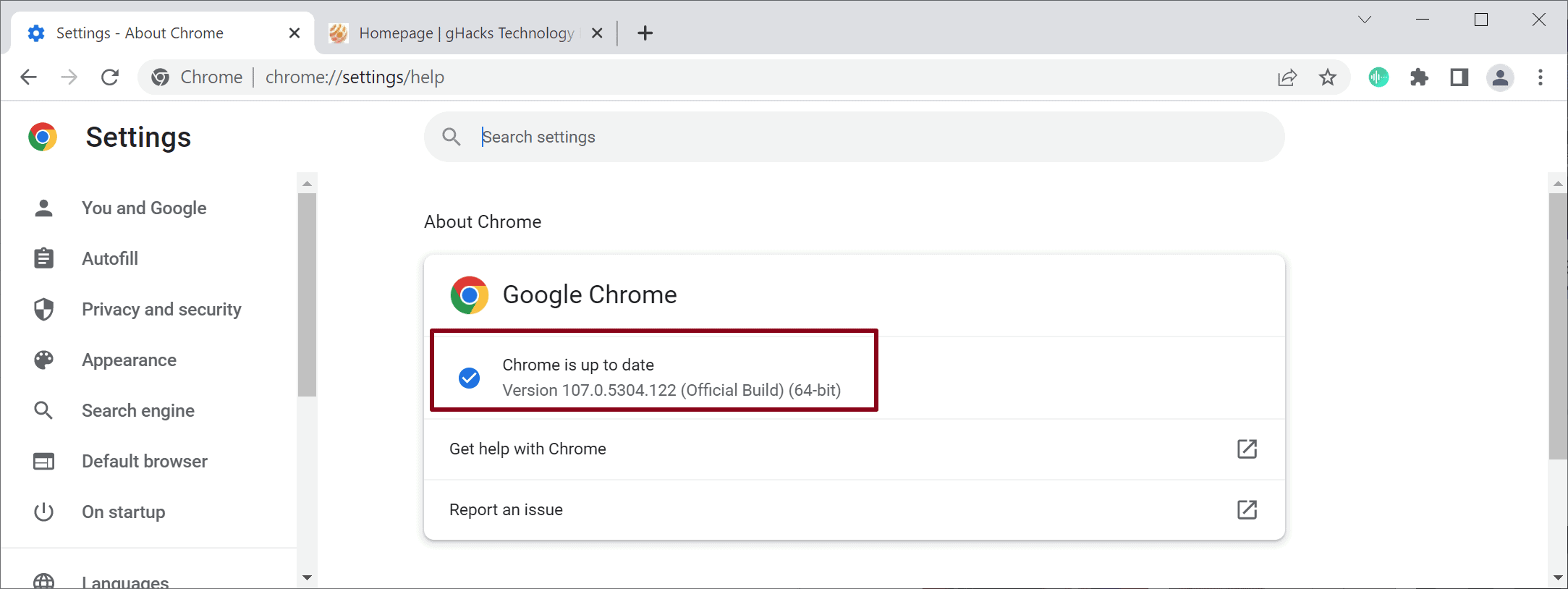
Desktop users of Chrome may run a manual check for updates to download the update immediately. All it takes is to load chrome://settings/help or select Chrome Menu > Help > About Google Chrome to do so. The page that opens displays the current version that is installed on the device and runs a check for updates. Any update that is found during the scan is downloaded and installed.
All updates address a single security issue in the browser. Google lists it as CVE-2022-4135: Heap buffer overflow in GPU, and assigned it a severity rating of high. High is second only to critical in the severity scale.
Google notes that the issue is exploited in the wild. Chrome users should update the browser immediately to protect the browser from potential attacks.
Google Chrome for Android updates automatically. There is no option to speed up the process, as Google Play lacks an option to run a manual scan for updates, similarly to how it is done on the desktop.
Google had patched 10 security issues in Chrome 107, which was released to the stable channel a few weeks ago. The search giant is testing a new security feature called Encrypted Client Hello (ECH) in Chrome Canary.
Brave updates as well
Brave Browser was one of the first third-party Chromium-based browsers to release an update that addresses the security issue. The release notes merely state that the browser has been updated to Chromium 107.0.5304.141, but the official Twitter account confirms that the update patches the security issue in the browser.
Brave desktop users may load brave://settings/help to display the installed version and run a check for updates.
Other browsers, including Microsoft Edge, Vivaldi or Opera, have no update available yet that addresses the security issue.
Now you: do you use a Chromium browser? Has it been updated yet?
I know that this is a bit off-subject, but: when I bought my new HP laptop and downloaded Chrome, it says ‘managed by your organization.’ But there is no organization. It’s a home computer. Never been used anywhere else or by anyone else. So, I can’t adjust some of the settings, like ‘use secure DNS.’
Apparently, this is a wide-spread problem. I’ve read all the threads, with all their ‘solutions,’ but none of them work. It’s a real annoyance.
Martin, can you, or one of your readers, offer a solution that works?
Thank you,
Rand
What a surprise. A month ending in Y, H, L, E, T, or R with a Chrome zero-day exploit.
What we need now is more blog posts from Google-funded security “experts” to tell us “Ak-shually, Chrome is the most secure browser ever made”.
@Andy Prough
Firefox has weaker exploit mitigations but is hacked less at the same time since it’s more or less irrelevant.
Not that hard to understand.
@Iron HEart:
Notice that has needed to be re-explained once every two weeks to Andy? Yet he cites how much more secure Pale Moon is – which would be GREAT if it worked on all common web sites.
@Jody Thornton
These geniuses have done the same thing in the more recent Chromium-related article. Totally not obvious that it’s shilling. :D
If brother Iron Heart says Chrome is more secure than Firefox, then do not ask why, do not ask for proof. Accept his and brother Madaidan’s word as truth. This is because they know the truth, just like they know the sky is blue and water is wet. Google is infallible, all who are wise and pious accept this.
@Hitomi
> Yeah yeah madaidan and twitter posts from 2014. Sure relevant today with a Rust based fox!
Reality-based fox:
> Last edited: March 19th, 2022
> Firefox does have some parts written in Rust, a memory safe language, but the majority of the browser is still written in memory unsafe languages, and the parts that are memory safe do not include important attack surfaces, so this isn’t anything substantial, and Chromium is working on switching to memory safe languages too.
From the source that the r/firefox crew hates the most: _https://madaidans-insecurities.github.io/firefox-chromium.html_
@Brotherhood of Google Fanboys
You see, that is the beauty of open source, if you will. Both Chromium and Firefox are open source. What does that mean? It means you can go look at the code yourself and verify whether or not the things Whonix developer madaidan says are true. If you find his statements to be false, you can write a counter-analysis, providing your own evidence based on the code. No faith or piety or higher wisdom required, it’s all there for you to check. I am eagerly waiting for your counter-analysis, and have been waiting for years.
Listen, I know that you are here to evangelize for Firefox, and I know that this article is a thorn in your side. But making false claims or ridiculous assertions in response is not helping your cause. You would be far more credible if you had an analysis of your own, some fact-based statement to make. But you don’t, you only have bullshit retorts to offer sadly.
A speedy recovery!
> A speedy recovery!
Will probably need it considering the sheer amount of bullshit here, including yours.
You, “Iron Heart”, is THE absolute Master of said bullshit.
“Firefox has weaker exploit mitigations but is hacked less at the same time since it’s more or less irrelevant.”
Firefox seems to be VERY fu<king relevant to you.
> Firefox seems to be VERY fu<king relevant to you.
LOL, I did not bring it up here, did I? It was the usual Firefox evangelists. I just responded to the usual drivel.
I guess the state of your comment is what you end up with if there is no argument to be made here.
>”LOL, I did not bring it up here, did I? It was the usual Firefox evangelists.”
The timestamps clearly show that the first one to bring it up on this entire page was you. It was not mentioned at all in either the article or any comments before your first comment.
It would appear that SameSh*t may have a valid point.
@Andy Prough
You are massively shilling for Firefox or Firefox-based projects here on gHacks any chance you get and when you purposefully come here, under a completely unrelated article, to voice your pseudo-complaints about a product you don’t use, it is abundantly clear which direction the wind is blowing from, not least because FF is the only multiplatform alternative to Chromium or Chrome anyway.
“But, but… I didn’t explicitly mention Firefox here! See! You did! My motives are pure, and the other fanboy supporting me is right!” – Not sure gHacks readers are stupid enough to buy into this. Maybe they are, maybe they aren’t. It’s a gamble, are we as silly as you are or can we see right through you? Hm, which is it, “Andy”?
That seems to be a common theme here, when there is an article on something Google related try to divert attention away from it to something else.
Nice try to give it a spin to make Chrome appear more safe. Yeah yeah madaidan and twitter posts from 2014. Sure relevant today with a Rust based fox!
:^)
What do you mean that Google Play lacks an option to scan for updates?? There are at least two methods in the menu structure for updates scanning.
There is no option to definitely get an update for an app, if it is released, as far as I know.
And that is the case indeed, MartinB.
Three differente ways to update apps (Chrome) in Android:
1) go to Play Store, apps, seek for updates, read the list and update one by one or all at once.
2) go to settings, apps, touch in one, go to bottom (details of app at store), touch it and just see if it appears the button “update” in the app description, do finish touching it to proceed the installation of the update.
3) open Chrome, go to options, more, seek the button “update”. If there is no button, there is no update available.
“Other browsers, including Microsoft Edge, Vivaldi or Opera, have no update available yet that addresses the security issue.”
Vivaldi had released updates to desktop stable and android BEFORE you even posted this article.
Have these updates of Vivaldi fixed the security issue related to this article?
I just checked, no, it hasn’t.
https://vivaldi.com/blog/desktop/minor-update-five-5-5/
The following improvements were made since the fourth 5.5 minor update:
[Chromium] Upgraded to 106.0.5249.203 (CVE-2022-4135)
Well, according to release notes, it fixes exactly CVE-2022-4135 which is the one mentioned in the article.
Additionally, chromium version in the new Vivaldi 5.5, namely 106.0.5249.203, is further than Chrome’s extended stable version 106.0.5249.199.
Not sure, but I guess this is the fix, no?
I use Edge Chromium as secondary browser, it’s the most complete of them all. Thanks for the article! :]